-
What Is a Cyber Attack?
- Threat Overview: Cyber Attacks
- Cyber Attack Types at a Glance
- Global Cyber Attack Trends
- Cyber Attack Taxonomy
- Threat-Actor Landscape
- Attack Lifecycle and Methodologies
- Technical Deep Dives
- Cyber Attack Case Studies
- Tools, Platforms, and Infrastructure
- The Effect of Cyber Attacks
- Detection, Response, and Intelligence
- Emerging Cyber Attack Trends
- Testing and Validation
- Metrics and Continuous Improvement
- Cyber Attack FAQs
-
What Is a Zero-Day Attack? Risks, Examples, and Prevention
- Zero-Day Attacks Explained
- Zero-Day Vulnerability vs. Zero-Day Attack vs. CVE
- How Zero-Day Exploits Work
- Common Zero-Day Attack Vectors
- Why Zero-Day Attacks Are So Effective and Their Consequences
- How to Prevent and Mitigate Zero-Day Attacks
- The Role of AI in Zero-Day Defense
- Real-World Examples of Zero-Day Attacks
- Zero-Day Attacks FAQs
-
What Is Lateral Movement?
- Why Attackers Use Lateral Movement
- How Do Lateral Movement Attacks Work?
- Stages of a Lateral Movement Attack
- Techniques Used in Lateral Movement
- Detection Strategies for Lateral Movement
- Tools to Prevent Lateral Movement
- Best Practices for Defense
- Recent Trends in Lateral Movement Attacks
- Industry-Specific Challenges
- Compliance and Regulatory Requirements
- Financial Impact and ROI Considerations
- Common Mistakes to Avoid
- Lateral Movement FAQs
- What is a Payload-Based Signature?
-
Dark Web Leak Sites: Key Insights for Security Decision Makers
- Dark Web Leak Sites Explained
- Evolving Extortion Tactics
- The Role of Leak Sites in Ransomware Double Extortion
- Critical Risks Exposed by Data Leak Sites
- Anatomy of a Dark Web Leak Site
- Proactive Defense: How Organizations Can Mitigate Dark Web Leaks
- Dark Web Leak Site FAQs
- What to Do If Your Organization Appears on a Dark Web Leak Site
-
What is Spyware?
- Cybercrime: The Underground Economy
-
What Is Cross-Site Scripting (XSS)?
- XSS Explained
- Evolution in Attack Complexity
- Anatomy of a Cross-Site Scripting Attack
- Integration in the Attack Lifecycle
- Widespread Exposure in the Wild
- Cross-Site Scripting Detection and Indicators
- Prevention and Mitigation
- Response and Recovery Post XSS Attack
- Strategic Cross-Site Scripting Risk Perspective
- Cross-Site Scripting FAQs
- What Is a Dictionary Attack?
- What Is a Credential-Based Attack?
-
What Is a Denial of Service (DoS) Attack?
- How Denial-of-Service Attacks Work
- Denial-of-Service in Adversary Campaigns
- Real-World Denial-of-Service Attacks
- Detection and Indicators of Denial-of-Service Attacks
- Prevention and Mitigation of Denial-of-Service Attacks
- Response and Recovery from Denial-of-Service Attacks
- Operationalizing Denial-of-Service Defense
- DoS Attack FAQs
- What Is Hacktivism?
- What Is a DDoS Attack?
-
What Is CSRF (Cross-Site Request Forgery)?
- CSRF Explained
- How Cross-Site Request Forgery Works
- Where CSRF Fits in the Broader Attack Lifecycle
- CSRF in Real-World Exploits
- Detecting CSRF Through Behavioral and Telemetry Signals
- Defending Against Cross-Site Request Forgery
- Responding to a CSRF Incident
- CSRF as a Strategic Business Risk
- Key Priorities for CSRF Defense and Resilience
- Cross-Site Request Forgery FAQs
- What Is Spear Phishing?
-
What Is Brute Force?
- How Brute Force Functions as a Threat
- How Brute Force Works in Practice
- Brute Force in Multistage Attack Campaigns
- Real-World Brute Force Campaigns and Outcomes
- Detection Patterns in Brute Force Attacks
- Practical Defense Against Brute Force Attacks
- Response and Recovery After a Brute Force Incident
- Brute Force Attack FAQs
- What is a Command and Control Attack?
- What Is an Advanced Persistent Threat?
- What is an Exploit Kit?
- What Is Credential Stuffing?
- What Is Smishing?
-
What is Social Engineering?
- The Role of Human Psychology in Social Engineering
- How Has Social Engineering Evolved?
- How Does Social Engineering Work?
- Phishing vs Social Engineering
- What is BEC (Business Email Compromise)?
- Notable Social Engineering Incidents
- Social Engineering Prevention
- Consequences of Social Engineering
- Social Engineering FAQs
-
What Is a Honeypot?
- Threat Overview: Honeypot
- Honeypot Exploitation and Manipulation Techniques
- Positioning Honeypots in the Adversary Kill Chain
- Honeypots in Practice: Breaches, Deception, and Blowback
- Detecting Honeypot Manipulation and Adversary Tactics
- Safeguards Against Honeypot Abuse and Exposure
- Responding to Honeypot Exploitation or Compromise
- Honeypot FAQs
- What Is Password Spraying?
- How to Break the Cyber Attack Lifecycle
-
What Is Phishing?
- Phishing Explained
- The Evolution of Phishing
- The Anatomy of a Phishing Attack
- Why Phishing Is Difficult to Detect
- Types of Phishing
- Phishing Adversaries and Motives
- The Psychology of Exploitation
- Lessons from Phishing Incidents
- Building a Modern Security Stack Against Phishing
- Building Organizational Immunity
- Phishing FAQ
- What Is a Rootkit?
- Browser Cryptocurrency Mining
- What Is Pretexting?
- What Is Cryptojacking?
What is a Botnet?
A botnet (short for “robot network”) is a network of compromised computers or devices, called bots, that are infected with malware and controlled remotely by a cybercriminal known as a bot herder. These bots work together to carry out large-scale malicious activities, including DDoS attacks, data theft, and spam distribution.
Key Takeaways:
- A bot is a single infected device, and a botnet is a group of infected devices.
- Botnets are controlled by command and control (C2) servers.
- They are used in DDoS attacks, data theft, and cryptocurrency mining.
- Due to their stealth and persistence, botnets are difficult to detect.
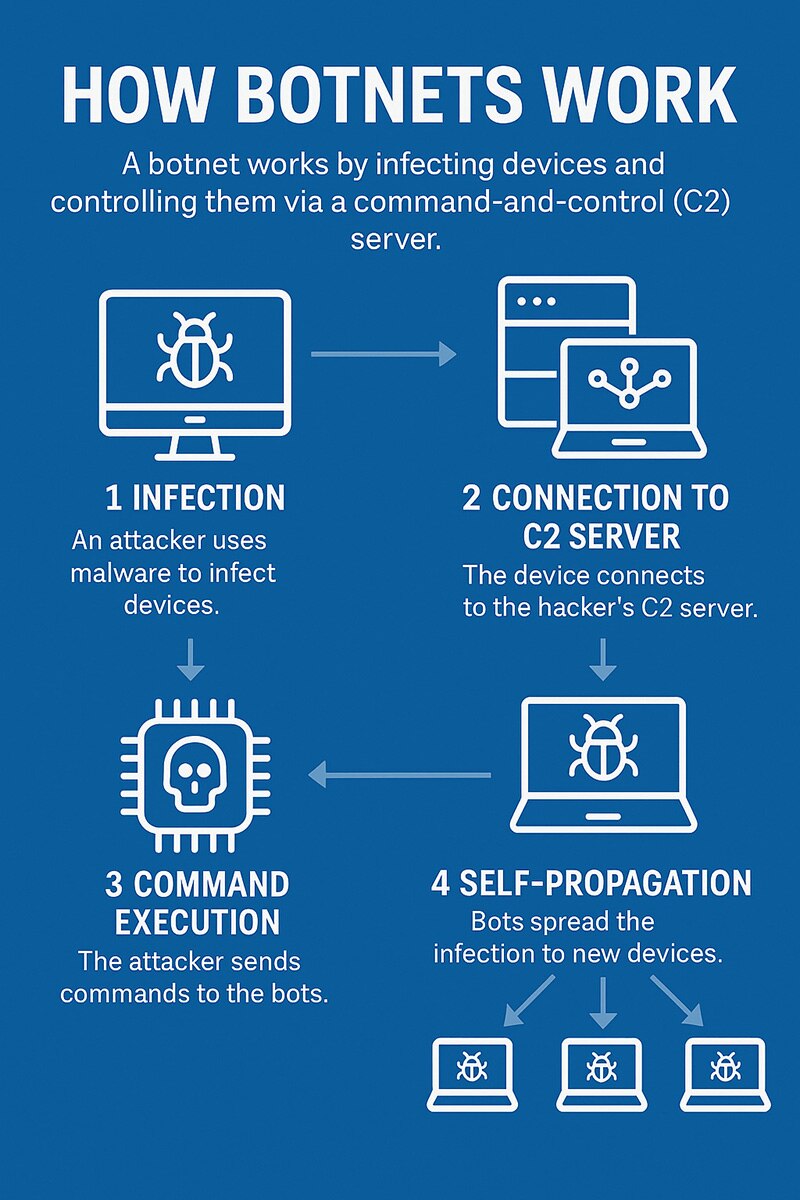
How Botnets Work
A botnet works by infecting multiple devices, such as computers, smartphones, and Internet of Things (IoT) devices, with malicious software that allows a hacker to remotely control them. Once infected, these devices become “bots” or “zombies” and operate under the command of a central authority known as a Command and Control (C2) server.
Step-by-Step Breakdown:
- Infection
The attacker uses malware, often spread via phishing emails, malicious downloads, or software vulnerabilities, to infect devices. - Connection to C2 Server
After the infection, the compromised device silently connects to the hacker’s C2 server, waiting for instructions. - Command Execution
The attacker sends commands to the bots to perform malicious actions such as launching DDoS attacks, stealing data, sending spam, or spreading malware. - Self-Propagation
Advanced botnets can scan for vulnerabilities and automatically spread to new devices, thereby growing the botnet. - Stealth and Persistence
Many botnets use obfuscation techniques to avoid detection and persist on the device by re-infecting it if security software removes the malware.
Why are Botnets Created?
The motivations for creating botnets are similar to those of most other malicious cyberthreats. Threat actors primarily create botnets for profit, but some use them for activism and to facilitate state-sponsored disruptions.
Several of the most common reasons botnets are created include:
- Cryptocurrency mining
- Theft of financial and sensitive information
- Sabotage (such as taking services or sites offline)
- Cyberattacks (such as phishing, ransomware, and distributed denial-of-service attacks)
- Selling access to other cybercriminals (i.e., botnet-as-a-service).
What are Botnets Used For?
Cybercriminals use botnets for various illegal purposes:
- DDoS Attacks: Overwhelm websites or servers by flooding them with traffic.
- Spam Campaigns: Send bulk phishing or advertising emails.
- Data Theft: Steal login credentials, credit card info, and personal data.
- Cryptomining: Secretly uses a victim's computing resources to mine cryptocurrency.
- Click Fraud: Generate fake clicks on ads to earn revenue.
- Malware Distribution: Deliver ransomware or spyware to other devices.
Types of Botnets
Botnets come in different forms based on their structure and control. Understanding these types helps you identify and mitigate threats more effectively.
- Centralized Botnets: These rely on a single command-and-control (C2) server. All infected devices (bots) connect to this central point for instructions.
- Pros for attackers: Simple to manage and deploy.
- Weakness: If the C2 server is taken down, the entire botnet can collapse.
- Decentralized (Peer-to-Peer) Botnets: Instead of a central server, bots communicate with each other in a peer-to-peer (P2P) fashion. Each bot can act as both a client and a server.
- Pros: More resilient to takedown attempts.
- Challenge for defenders: Harder to trace and shut down due to distributed control.
- Hybrid Botnets: Combining centralized and P2P structures. Attackers can push commands centrally, but they can also allow bots to share instructions across the network.
- Best of both worlds: Flexible control with added resilience.
- Mobile Botnets: Target smartphones and tablets using malware hidden in malicious apps or downloads. They can send premium SMS messages, steal data, or participate in DDoS attacks.
- Emerging threat: As mobile usage rises, these botnets are becoming more common.
- IoT Botnets: Infect IoT devices, such as smart TVs, cameras, and routers. Often used in massive DDoS attacks (e.g., Mirai botnet).
- Major vulnerability: Many IoT devices lack basic security features.
Signs Your Device May Be in a Botnet
Botnets operate silently in the background, making them difficult to detect. However, infected devices often show unusual behavior. Watch for these warning signs that your device may be compromised:
Slower-than-Normal Performance
Your device might become sluggish, take longer to open apps, or respond slowly to commands. This happens because the botnet is using system resources to perform tasks such as sending spam or participating in DDoS attacks.
Unexpected Crashes or Errors
Frequent system crashes, blue screens, or unexplained application errors could indicate that malware is interfering with your system’s normal operations.
Unusual or High Data Usage
A sudden spike in your data usage, especially when you're not actively using the internet, could be a red flag. Botnets often send and receive data in the background without your knowledge.
Device Running Hot While Idle
If your device feels hot even when it's not in use, it could be working overtime for a botnet. Tasks like cryptocurrency mining or spam delivery can strain your processor and battery, causing overheating.
Frequent Pop-Ups or Suspicious Background Activity
Unexpected pop-ups, unknown programs running in the background, or new processes appearing in your task manager may be signs of a malware infection. Botnets often install additional tools to maintain control or expand the infection.
Increased Network Activity
If your router lights are constantly blinking or you notice unusual outgoing traffic when you're not using the internet, a bot might be communicating with a command and control server.
Security Software Disabled or Not Working
Some botnets attempt to disable antivirus programs or prevent updates to keep themselves hidden. If your security software is malfunctioning or won’t launch, it could be a symptom of an infection.

How to Protect Against Botnets
Preventing botnet infections requires a combination of good cybersecurity hygiene, updated technology, and user awareness. Here are essential steps to safeguard your devices and networks:
Keep Software and Devices Updated
Organizations must regularly update their operating systems, applications, and firmware to patch known security vulnerabilities that botnets exploit. Enable automatic updates whenever possible for both desktop and mobile devices, as well as IoT equipment like routers and cameras.
Use Antivirus and Anti-Malware Tools
Use reputable antivirus and anti-malware tools to detect, quarantine, and remove threats. Modern solutions often include real-time protection, behavioral monitoring, and threat intelligence to identify botnet activity early.
Be Cautious with Emails and Links
Most botnets begin with a phishing email or a malicious download. Avoid clicking on suspicious links or attachments, especially if the sender is unknown. Watch for emails that urge immediate action or contain strange formatting and grammar.
Secure Your Internet of Things (IoT) Devices
IoT devices are a favorite target for botnets like Mirai due to their weak default security. To protect them:
- Change default usernames and passwords immediately after setup.
- Disable remote access features you don’t need.
- Regularly update device firmware.
- Place IoT devices on a separate network from critical systems, if possible.
Use a Firewall
Firewalls act as a barrier between your network and potential threats. Configure your firewall to monitor outbound traffic, which can help detect unusual activity, like a device contacting a known C2 server.
Educate Yourself and Others
Human error remains a major factor in successful botnet infections. Educate employees or family members on the signs of phishing, safe browsing habits, and how to recognize malicious files or websites.
Enable Multi-Factor Authentication (MFA)
Add an extra layer of protection to your accounts with MFA. Even if a botnet captures your password, it won’t be able to log in without the second authentication factor.
Perform Regular Security Audits
Conduct periodic security checks on your devices and network. Look for outdated software, weak passwords, or unusual access logs. Proactive audits can help you spot signs of compromise before severe damage occurs.
One of the most important steps an enterprise can take to control modern malware is to reduce infection vectors and eliminate the bots' ability to hide. Today, most infection vectors used by botnets are largely unchecked, and botnet traffic is typically small enough to blend seamlessly into regular network traffic.
By regaining complete visibility and control of strictly what traffic is allowed into the network and why, security teams can greatly satisfy both goals.
Why Botnets Lead to Long-Term Intrusions
Several unique functional traits of bots and botnets make them well-suited for long-term infiltration. The bot herder can update bots to modify their entire functionality based on their objectives and to adapt to changes and countermeasures by the target system.
Bots can also employ other infected computers on the botnet as communication channels, offering the bot herder a near-infinite number of communication paths to adjust to changing options and deliver updates. This underscores that infection is the most crucial step because functionality and communication methods can always be altered later as needed.
Since the remote bot herder controls infected computers, a botnet resembles having a malicious hacker inside your network, rather than merely having a malicious executable program.
How To Disable a Botnet
Once a botnet is discovered, the two widely used approaches for disabling it are to take down the control centers and remove the malware that controls the botnet. The best approach will depend on the botnet's architecture, scale, and the resources available to the organization.
Take Down Botnets Control Centers
If a botnet employs a client-server architecture, it can be disabled by shutting down the central server or servers that control it. Taking down a botnet control center usually requires the support of law enforcement.
Eliminate Botnet Malware on Infected Devices
Several approaches can be used to remove botnet malware from individual systems. The easiest is to use anti-virus tools. In cases where this does not work, the system needs to be wiped and reimaged. The malware can be removed from IoT devices by doing a factory reset, reformatting the device, or flashing the firmware.
Tools and Techniques for Botnet Defense
Several tools and techniques are available to defend against botnet threats. Some are specific to botnets, and others are part of an organization’s overall security program. The following are several tools and techniques that can be employed.
- Access controls
- Advanced anomaly detection
- Anti-virus software
- Behavioral analysis and machine learning
- Command-and-control (C2) server detection
- Device authentication
- Honeypots and decoys
- Installing updates and security patches
- Masking IP addresses
- Network segmentation
- Rate limiting
- Real-time monitoring
- Signature-based tools
- Strong password policies
- Threat intelligence
- User and entity behavior monitoring
- Using proxy servers
Real-World Examples of Botnets
Many botnet attacks are zero-day varieties. The following is a review of several real-world botnet attacks. While most of these have been disabled, a few are still active.
EarthLink Spammer (Disabled)
One of the first botnets to gain public attention was the EarthLink botnet, also known as the EarthLink Spammer. Launched in 2000, the botnet was used by its creator and other cyber criminals to send more than 1.25 million phishing emails over the EarthLink network.
This botnet software used Trojan horse malware to infect systems and remotely access users' information. Over a year, the EarthLink botnet affected approximately 12% of EarthLink's email traffic and resulted in an estimated $4.1 million in lost profits for the organization.
Cutwail (Disabled)
Discovered in 2007, the Curtwail botnet was sending more than 51 million emails per minute by 2009, accounting for over 45% of the world's spam. It is estimated that, at its peak, the Curwail botnet comprised 1.5 to 2 million infected computer systems sending 74 billion spam emails a day.
Cutwall targeted Windows systems with Trojan horse malware, which used infected computers as spambots. Cutwail was also used to spread well-known malware families and was used as a DDoS botnet for SSL attacks.
ZeuS (Disabled)
The ZeuS botnet, also known as Zbot, was believed to be the most widely used malware, infecting more than 13 million computers in 196 countries.
ZeuS used Trojan horse malware for several nefarious purposes, including spreading CryptoLocker ransomware and stealing credentials for users' accounts, such as social media, banking, FTP, and email accounts. Over 90% of all online bank fraud incidents were attributed to the ZeuS botnet.
Storm (Disabled)
Storm, also known as the Storm Worm Botnet, Dorf Botnet, and E-card Malware, was one of the first peer-to-peer botnets. This Trojan horse malware was available for rent on the dark web.
Believed to have infected up to 2 million computers, Storm was used for various criminal activities, including identity theft, bank fraud, and distributed denial-of-service (DDoS) attacks. This was one of the most virulent botnets, as it had defensive capabilities that thwarted attempts to track and deactivate it.
Kraken (Disabled)
The Kraken botnet was a massive spyware botnet. It was estimated to have infected 10% of all Fortune 500 companies, but each of the almost 500,000 bots in the network could send about 600,000 emails a day. In addition to its size, the Kraken botnet is believed to have been one of the first to employ evasion techniques to evade detection by anti-malware tools.
Grum (Disabled)
Specializing in targeting the pharmaceutical industry with spam, the Grum botnet could send nearly 40 billion emails daily, accounting for around 20% of the world's spam. At its peak, the Grum botnet included more than 100,000 computers.
A notable feature of the Grum botnet was that it used two types of control servers, one for infecting systems and one for sending commands. Additionally, the control servers were located in Panama, Russia, and Ukraine, which provided resiliency and allowed the system to stay operational even when one control server was disabled.
Mariposa (Disabled)
The Mariposa botnet, comprising more than 12 million computers, used worm malware that propagated itself through malicious digital ads, also known as malvertising. This botnet was used to steal sensitive data from over 800,000 users, including credentials for financial services sites and credit card numbers. It was also used to launch online scams and DDoS attacks.
GameOver Zeus (Disabled)
After the client-server ZeuS botnet was disabled, GameOver Zeus (GOZ) emerged with a peer-to-peer architecture, making it harder to disrupt. Before it was disrupted, GameOver Zeus had infected over 250,000 computers and caused an estimated $100 million in monetary losses.
Dridex (Active as of May 2024)
Dridex, also known as Bugat and Cridex, is a Trojan horse malware that mainly spreads through phishing campaigns. It is delivered as a Word or Excel document attachment with a malicious macro that downloads and executes malware.
Distributed through a malware-as-a-service model, this infostealer botnet is used to perform various malicious actions, including stealing users' information by capturing screenshots, keylogging, and launching ransomware attacks.
ZeroAccess (Disabled)
Built to target Microsoft Windows operating systems, ZeroAccess is a peer-to-peer botnet that uses Trojan horse malware. The ZeroAccess botnet was particularly difficult to disable because it evaded detection by using a trick to disable anti-virus software running on infected systems. Growing to more than 9 million computers, the ZeroAccess botnet was used for cryptocurrency mining and spamming malware.
3ve (Disabled)
3ve was the head of three interconnected sub-botnets used for ad fraud. The botnet was used to create more than 5,000 fake websites, spoofing the domains of high-ranking and prestigious publishers and selling their "premium" traffic to advertisers.
3ve was believed to have generated 3-12 billion ad bid requests daily using the more than 1.7 million computers under its control. By using an anti-forensics evasion tactic, 3ve is estimated to have collected around $30 million before it was disabled.
Emotet (Active as of August 2024)
Emotet, also known as Heodo and Geodo, is considered one of the most dangerous botnets because it is polymorphic, changing its code each time it is called up. It uses Trojan horse malware to spread and distribute other malware and ransomware. Threat actors use Emotet to commit financial fraud, espionage, and political sabotage with malicious spam.
Mirai (Active as of August 2024)
The Mirai botnet is known for targeting and weaponizing IoT devices. It is believed to have infected over 600,000 devices, which it uses to launch DDoS attacks. In 2016, it ran a 1TB/second DDoS. The Mirai source code is publicly available and has been used to create hundreds more botnets. Mirai is considered to be the largest IoT botnet.
Botnet FAQs
The simple answer as to what botnets can do is anything. Botnets are used to automate and scale many malicious cyber activities. The following examples demonstrate the variety of actions that botnets can be directed to execute on behalf of cybercriminals.
These functions are made possible because once botnet malware is installed, it enables the botmaster to send commands such as:
- Exfiltrating files and other data
- Gathering data from the device
- Installing and running applications on the device (e.g., spyware)
- Monitoring the user’s activities
- Reading and writing system data
- Searching for vulnerabilities in other devices