-
What Is Security Operations (SecOps)? Comprehensive Guide
- Security Operations (SecOps) Explained
- The Pillars of Modern SecOps: People, Process, and Technology
- Example Scenario: Incident Response to a Malware Alert
- Proactive Security Operations Examples
- Technology: Core Tools for the SOC
- Core Components and Functions of the SOC
- SecOps vs. DevOps vs. DevSecOps
- Security Operations FAQs
- What Is a Security Operations Center (SOC)?
-
How Do I Deploy SecOps Automation?
- Preparing for SecOps Automation
- Start Simple with High-Impact Tasks
- Automation Benefits for Organizations of All Sizes
- Peer Review and Approval
- Secure a Champion for Automation
- Defining Automation Use Cases
- Example Use Cases: Phishing and Malware
- Selecting the Right SOAR Platform
- SOAR Deployment and Use Cases FAQs
- Security Operations Center (SOC) Roles and Responsibilities
- How Do I Improve SOC Effectiveness?
-
How AI-Driven SOC Solutions Transform Cybersecurity: Cortex XSIAM
- How Cortex XSIAM 2.0 Revolutionizes Security Operations
- Cortex XSIAM Solutions and Advantages
- Addressing Critical Issues in Current SOC Solutions
- How Cortex XSIAM Transforms the SOC
- Distinctive Features of Cortex XSIAM
- Comprehensive SOC Solutions: Single Platform Delivery Highlights
- Integrated Capabilities: The XSIAM Solutions Delivery
- Ready to Transform Your Cybersecurity Landscape?
What is SOC as a Service (SOCaaS)?
Security operations center as a service (SOCaaS) is a cloud-based subscription model for managed threat detection and response that includes best-in-class SOC solutions and capabilities to help fill in gaps on existing security teams.
Which Cyber Threats are Monitored by SOCaaS?
Like a traditional, on-premises SOC, SOCaaS includes 24/7 monitoring, threat detection, prevention and analysis of your attack surface, including internet traffic, corporate networks, desktops, servers, endpoint devices, databases, applications, cloud infrastructure, firewalls, threat intelligence, intrusion prevention, and Security Information and Event Management (SIEM) systems.
Cyberthreats include ransomware, denial of service (DoS), distributed denial of service (DDoS), malware, phishing, smishing, insider threats, credential theft, zero days and more.
The Need Managed Security Services
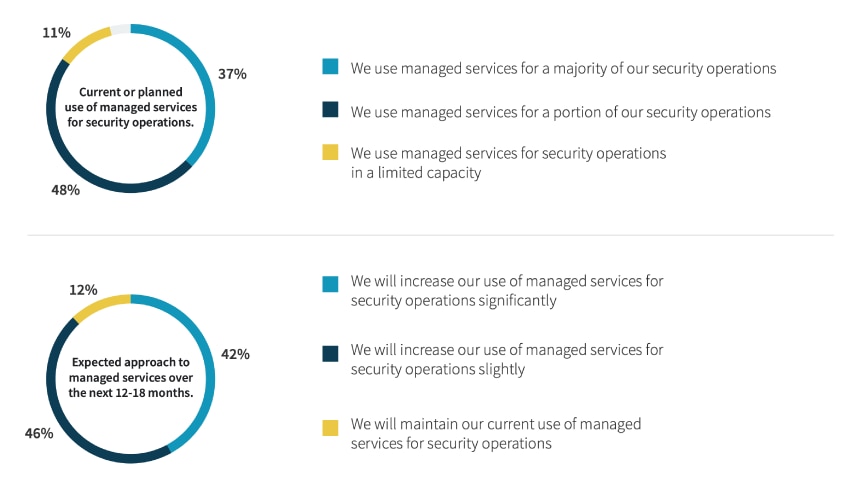
In their research report, SOC Modernization and the Role of XDR Enterprise Strategy Group found that more than half (55%) want security services so they can focus security personnel on strategic security initiatives. Others believe managed service providers can accomplish things that their organization simply cannot, with 52% believing service providers can provide better security operations than their organization can; 49% saying a managed service provider can augment their SOC team; and 42% admitting that their organization doesn’t have adequate skills for security operations

Source: SOC Modernization and the Role of XDR Enterprise Security Group (ESG)
What are the Benefits of SOC as a Service (SOCaaS)?
Outsourcing security operations and information security management provides a handful of benefits, including the following:
- Cost reductions
- Faster detection and more efficient remediation to help streamline security events
- Access to best-of-breed security solutions
- Reducing the burden on internal SecOps teams
- Continuous monitoring
- Speeding up detection/response to deliver high-confidence alerts and reduce alert fatigue
- Minimizing turnover and reducing security analyst burnout; removing mundane tasks
- Reduced complexity
- Lower cyber risk
- Enhanced business scalability and agility
Conversely, issues from legacy SOC environments can include:
- Lack of visibility and context
- Increased complexity of investigations
- Lack of interoperability of systems
- Lack of automation and orchestration
- Inability to collect, process and contextualize threat intelligence data.
- Alert fatigue/noise from the high-volume, low-fidelity alerts of security controls
Further key benefits of SOCaaS are outlined as follows:
Continuous Protection
Security analysts can monitor for alerts, events and indicators of compromise (IoCs). Integrate high-fidelity threat intelligence and actionable threat and impact reports. Learn from analytics and threat detection across all data sources to generate high-fidelity leads for threat hunting.
Faster response times
Faster response times help to reduce dwell time and improve both mean time to investigate (MTTI) and mean time to remediate (MTTR).
Threat Prevention and Threat Hunting
SOCaaS allows teams to proactively examine environments for attacker tactics, techniques and procedures (TTPs) to help identify new vulnerabilities that may exist in your infrastructure.
Security Expertise and Coverage
While SOCs come in many incarnations, they can consist of roles and responsibilities to include a SOC lead, incident responder, and Tier 1-3 security analyst(s). Additional specialized roles may include security engineers, vulnerability managers, threat hunters, forensic investigators and compliance auditors.
Adherence to Compliance and Regulation Mandates
Key SOC monitoring capabilities are integral to enterprise compliance, especially following regulations that require particular security monitoring functions and mechanisms, such as GDPR and CCPA.
Sectors such as healthcare, financial and retail have their own sets of compliance to proactively manage risk and navigate regulatory changes. These include HIPAA, FINRA and PCI to safeguard the integrity of data and personal information from compromise.
Optimize Security Teams
Beyond investing in security solutions and tools, the most important factor in any successful SOC will remain the human element.
While machine learning and automation will undoubtedly improve overall outcomes like response times, accuracy and remediation — especially for low-level, repetitive tasks — attracting, training and retaining security personnel, including engineers, security analysts and architects, needs to be baked into any cohesive SOC transformation strategy.
Factors to Consider When Designing a SOC
There are numerous ways of designing and operating a SOC. In their paper, Security Operations Center: A Systematic Study and Open Challenges, Manfred Vielberth, Fabian Böh, Ines Fichtinger and Günther Pernul outline some factors that influence SOC operating models and various factors that can come into play when choosing to implement one.
- Company strategy: The overall business and IT strategy should be consulted to determine which operating model fits best. A SOC strategy should be defined before selecting the respective operating mode.
- Industry sector: The industry sector in which a company mainly operates largely influences the scope of the SOC required.
- Size: The size of a company also has an impact on the decision since a small company might not be able to set up and run a SOC on its own or might not even require a rigorously defined SOC.
- Cost: The costs of internally implementing and maintaining a SOC must be compared with the costs of outsourcing security operations. Initially, deploying an in-house SOC might be more expensive, but such an option might turn out to be more cost-effective in the long term. Costs of finding, hiring and training SOC staff constitute a significant factor, especially since they might increase due to growing skill shortages and increasing market demand.
- Time: It takes a considerable amount of time to set up a SOC. Therefore, alignment with organizational plans and timelines is necessary. Additionally, the time to set up a SOC should be compared to the time needed for outsourcing it.
- Regulations: Depending on the industry sector, different regulations must be considered. Some might enforce the implementation of an operational SOC; others might forbid the outsourcing of SOC operations altogether, or at least to specific providers who do not comply with the respective regulations.
- Privacy: Privacy also falls under regulation and must be respected whenever dealing with personal data.
- Availability: Availability requirements should be considered. Most of the time, the goal is to have a SOC operational 24/7, year-round.
- Management support: Management support is of crucial importance when setting up a dedicated SOC. If management is not committed, and the benefits of a SOC are not communicated to upper management, the team might not get the resources needed.
- Integration: The capabilities of an internal SOC need to be integrated with other IT departments, whereas, in an external SOC, the provider needs to be integrated to get all the data needed.
- Data loss concerns: The SOC is most often a central place where a substantial amount of sensitive data is processed. Internal SOCs need to be highly secured, while an external SOC requires a trusted provider who can ensure that the data is secured against intellectual property theft as well as accidental loss.
- Expertise: It takes time and money to build up expertise. The required skills for operating a SOC are not easy to find. Recruitment and retention of personnel is a crucial factor for internal SOCs. However, the necessary skills are already present for external SOC providers. Especially in the context of SOCs, having an insight into different companies might give SOC providers a knowledge advantage. However, companies should be aware that outsourcing reduces in-house knowledge.
Why a Managed SOC is Important
Similar to on-premises and hybrid SOCs, managed SOCs come in different types. Like their counterparts, they can monitor an organization’s threat landscape, including their IT network, devices, applications, endpoints (attack surface) and data for known and evolving vulnerabilities, threats and risks.
Managed SOC services typically come in two models:
- Managed Security Services Providers (MSSPs) that operate SOCs in the cloud and use automated processes
- Managed Detection and Response (MDR) that relies more on direct human involvement which exceeds basic prevention to enable proactive and advanced activities like threat hunting.
Choosing a managed SOC option can help reduce the complexity of managing and maintaining an internal SOC, especially for small-to-midsize enterprises.
The same is true for finding professional security staff to build and run a SOC that meets the ever-increasing IT security requirements and mandates. Hiring external security experts allows organizations to immediately scale their coverage and bolster their security posture with access to threat monitoring and research databases, which can result in a better return on investment (ROI) than a homegrown SOC.
With threat actors embracing their own forms of digital transformation and taking advantage of automation, organizations need security operations that can keep pace. Managed security providers can offer uninterrupted coverage and guaranteed service via service level agreements (SLAs) that define the scope and delivery of services, including required software updates and patches as they become available or countermeasures against a new threat are ready to implement.
Challenges of a Managed SOC
While outsourcing security operations has numerous benefits, challenges and limitations may exist, which is why it’s critical to conduct your due diligence when comparing services, solutions and SLAs.
Onboarding
Managed SOC providers typically rely on their own security stack. As such, these solutions must be configured and deployed within a customer’s environment before the provider can start providing services. The transition during the onboarding process can be time-consuming and may result in potential risk exposure during this vulnerable phase.
Sharing of Critical Data
An organization’s SOC-as-a-service provider needs access to gather insights into an organization’s network to identify and respond to potential threats. To achieve this, the organization needs to send large amounts of sensitive data and intelligence to its service provider. Yet, releasing control of potentially sensitive information can make enterprise data security and risk management more challenging, exposing vulnerabilities during this phase.
Storing data Outside the Organization
Storing sensitive threat data and analysis externally poses a potential risk of both data leaks and data loss if the SOC’s cyber defenses are compromised or if you part ways with the service provider. While you can usually keep track of threat alerts in-house, most of the data is processed outside the perimeter, which limits your ability to store and analyze extended historical data about detected threats and possible data breaches.
Cost of Log Delivery
SOC-as-a-service providers commonly operate their cybersecurity solutions on-site using data feeds and network taps from their customers’ networks. This means that log files and other alert data are generated and stored on the provider’s network and systems. Gaining access to full-log data from a managed SOC provider can be expensive for an organization.
No Dedicated IT Security Team
The roles, responsibilities and scope can differ between organizations, creating a disconnect if applying a one-size-fits-all approach vs. forming a team that is well-versed in the nuanced, unique environments and infrastructure of each client. An external SOC team may not offer customization of services as some may be shared among multiple customers, which can negatively impact efficiencies.
Limited Knowledge of the Organization’s Specific Business
In servicing multiple customers and sharing SOC resources, managed SOC providers may miss possible gaps in an environment, not fully understanding an organization's business processes and procedures to protect them properly.
Regulatory and Compliance Considerations
The regulatory landscape is rapidly growing more complex, and organizations need to put into place security controls and policies to achieve and demonstrate compliance. While a managed SOC provider may offer support for regulatory compliance, the use of a third-party provider may complicate compliance requirements, requiring trust in a service provider to fulfill their compliance-related duties.
Limited Options to Customize Services
An external SOC rarely offers complete customization of the services offered as they are shared among multiple customers. The limited customization options can result in reduced efficiency across the organization’s departments and the inability to properly protect certain endpoints, networks and other parts of the security infrastructure.
Overall, a dedicated SOC that provides organizations with multiple benefits, including continuous network monitoring, centralized visibility, reduced cybersecurity costs, and better collaboration means you can’t go wrong. Cybercriminals will never take a break, and neither should you.
For an overview of a Security Operation Center (SOC), read What is a SOC?