What is Multifactor Authentication?
Multifactor authentication (MFA) is a method of authenticating users when they log into specific resources like applications, online accounts or VPNs. In addition to a username and password, users must utilize at least one additional verification method, if not more.
The goal of multifactor authentication is to make it difficult for unauthorized people to gain access to a system. It is becoming widely implemented in industries that understand the need for good cybersecurity practices — including finance and even popular gaming platforms — to require extra verification when someone is signing in. It’s widely agreed that MFA is a staple of good cybersecurity practices.
Why Is Multifactor Authentication Important?
Attack methods like credential harvesting and phishing are becoming more prevalent in the current threat landscape. When a threat actor gains access to a system through an employee’s credentials, they can deal immense damage by following up their initial attack with malware, such as ransomware or botnets. While encouraging good security hygiene and conducting mandatory training can decrease the odds of people in an organization falling for credential harvesting and phishing attacks, MFA is another crucial line of defense for keeping threat actors at bay.
Implementing MFA makes it more difficult for a threat actor to access a business’ environment and information systems, even if credentials like passwords or PINs have been compromised. This extra layer of protection notifies the SOC if an MFA attempt has failed, allowing the security team to identify gaps in their system before any damage is done. In addition to increasing protection, MFA is fairly straightforward and user-friendly.
How Does Multifactor Authentication Work?
When a user creates an account somewhere, they are required to provide several pieces of information to fulfill identification and authentication processes, including a username and password that represents their identity within the system. The service will then inform the user which additional verification methods (if any) are needed to finalize their account.
These additional methods typically consist of different factors:
- Something you know (e.g., a password, a personal identification number or PIN and/or security questions)
- Something you have (e.g., a mobile device, an email account, a physical security key or bankcard), and/or
- Something you are (e.g., a biometric identification like fingerprints or facial recognition)
When someone signs into that service later on, the system will ask for whatever information they submitted when they signed up. They will only get access to the system when they’ve correctly verified through the necessary methods. Whether this process stops at credentials or requires multiple forms of authentication depends on the service.
Types of Authentication
While MFA is the general term for requiring multiple factors of verification, there are specific terms that are used to describe unique authentication technologies or scenarios, including the following:
- Single sign-on (SSO): Often used with identity management systems, SSO enables a user to log in to multiple platforms or services with one set of credentials.
- Two-factor authentication (2FA): Requires exactly two forms of authentication for a user to access a system.
- In-band authentication: A service or platform contains an authentication channel for users to sign in directly.
- Out-of-band authentication: A company uses a different communication channel to authenticate its users.
- Multifactor authentication: MFA requires three or more forms of authentication for a user to access a system.
- Adaptive multifactor authentication (AMFA): Risk-based authentication (RBA), AMFA verifies user identity by analyzing information like role, location, device and more.
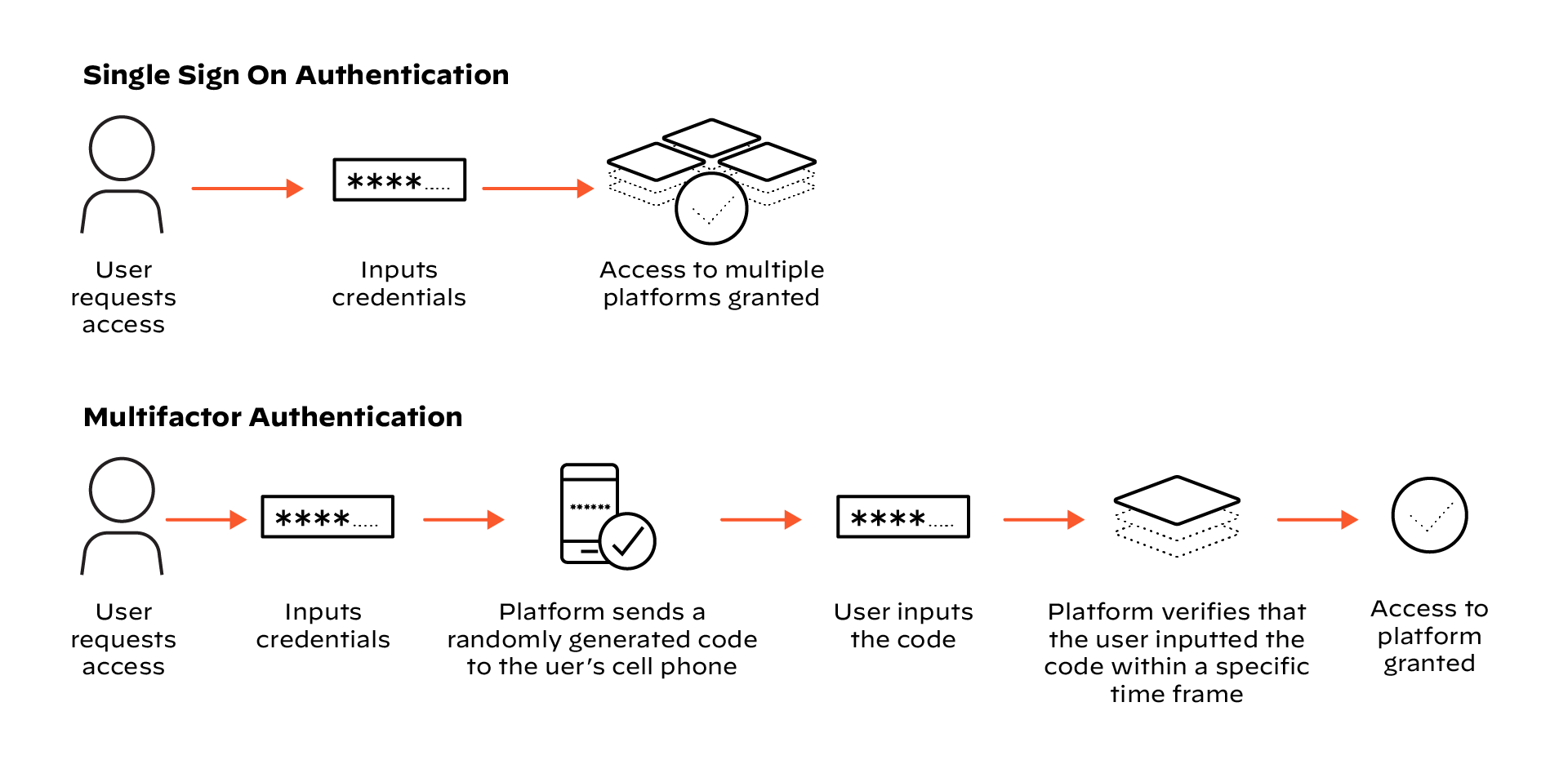
The platform or service that a user is accessing determines which type of authentication to use and which methods are enabled.
Verification Methods
There are many ways for users to verify their identity, and the list is growing. Some common formats include:
- PIN: A code between four and 10 digits created when the user signs up for the service or platform.
- Security questions: Users will choose and answer these questions when they create their account, then answer one or more of the questions when they log in.
- Verify personal information: Retyping or verifying the mobile phone number, email address or physical address associated with the account.
- Smart cards: A card with an embedded integrated circuit chip, like a debit/credit card.
- Token-based: A user must submit a random code that generates when they input their credentials. This code can be sent to their mobile device or email or generated on an authenticator app the user downloads or even a physical device that is sent to them.
- Biometrics: Methods like fingerprint scanning, facial recognition and more can help users verify their identity.
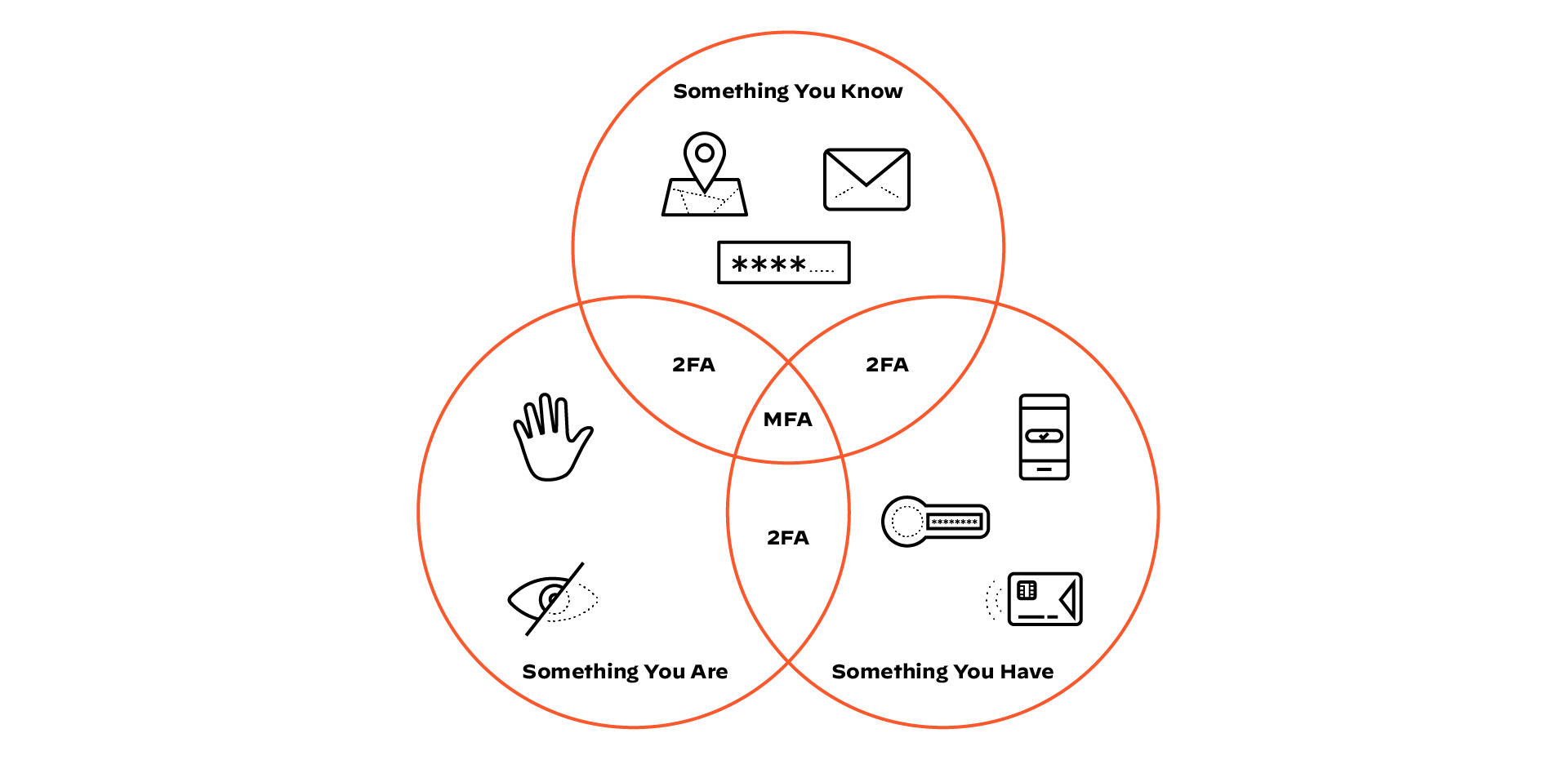
Many people can identify using these methods in their day-to-day lives, whether they’re focused on cybersecurity or not. MFA is becoming a more common — and more integral — part of society in many different ways.
Authentication Examples
Multifactor authentication has become very common; users from all types of platforms and industries have been using MFA without even knowing it!
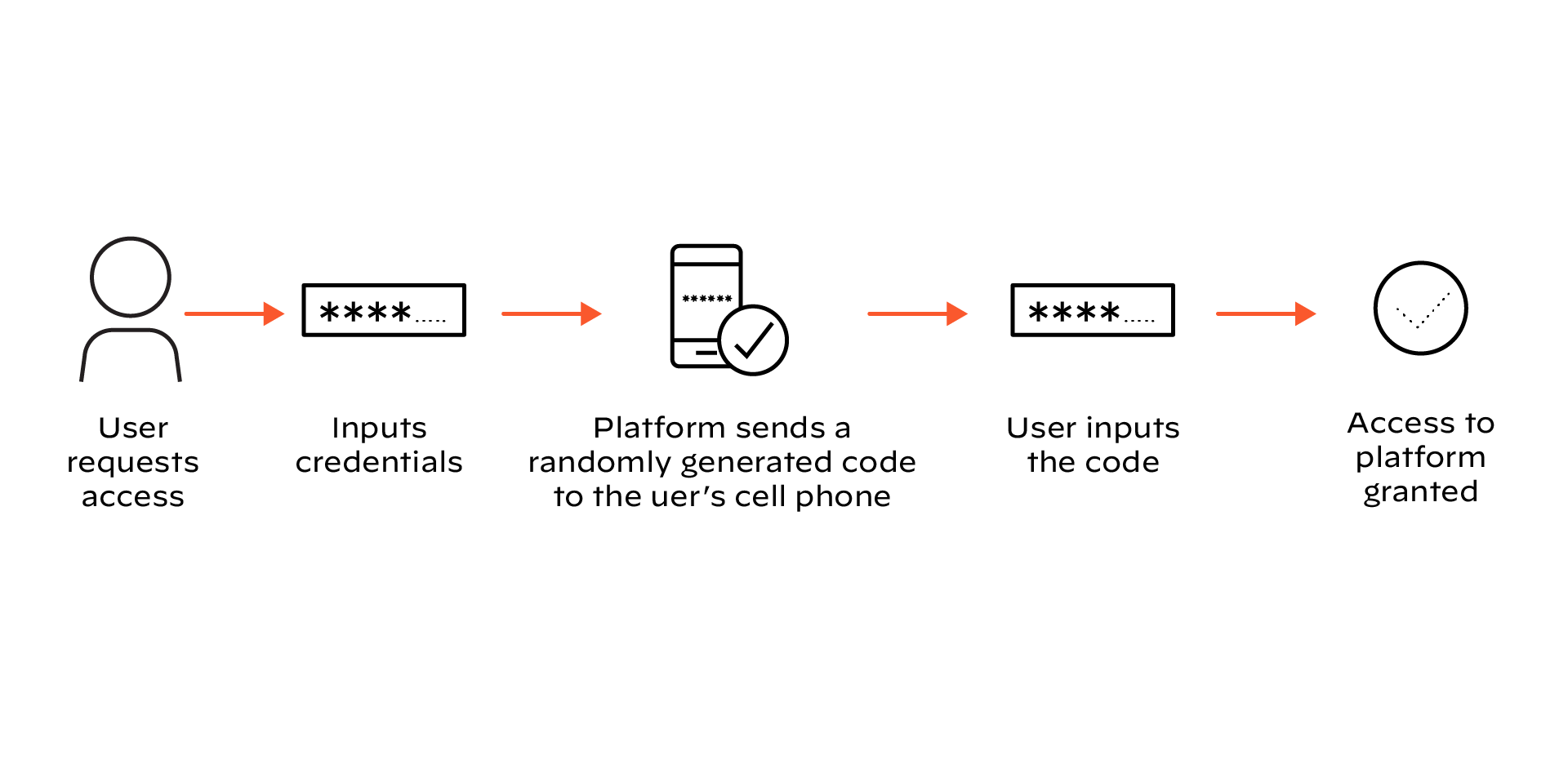
Many services use 2FA when someone logs into their online platform. After someone submits their login credentials, the platform will randomly generate a code sent to them via either a phone or email address identified when the user originally signed up. The user will then input that code into the platform for secure access.
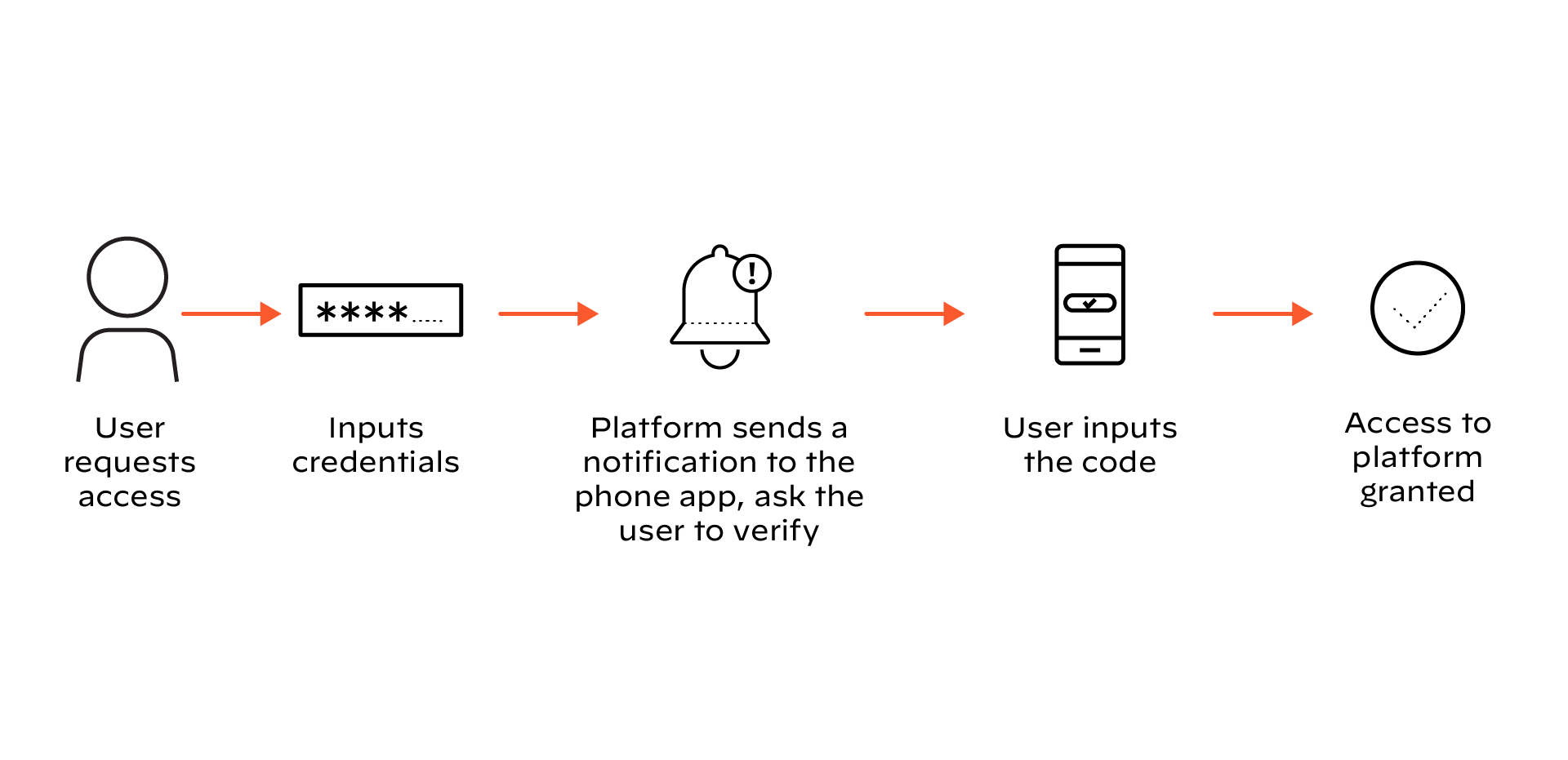
Another example of authentication comes from identity and access management (IAM) companies that provide B2B authentication methods. Users will be required to create an account with the third-party company and download a companion app to their mobile devices. Upon logging into the system, the platform sends a notification to the app and asks the user to verify that they are signing in. This example of out-of-band authentication is very common in the current working landscape.
One of the best methods of day-to-day protection is multifactor authentication, but that doesn’t mean it’s impenetrable.
Can MFA Be Hacked or Bypassed?
While MFA greatly reduces the likelihood of a successful attack, it can still be bypassed in various ways. It is possible through phishing, malware and meddler-in-the-middle attacks. Sometimes, it’s even user error — occasionally, users will enable authentication requests even if they don’t know their origin. They’ll simply assume the request is coming from a background process, or they forgot they had asked for access.
Even though MFA isn’t a concrete defense plan by itself, it should absolutely be implemented in a system. For additional protection, SOCs can look to endpoint protection solutions like Cortex XDR or SOAR solutions like Cortex XSOAR to identify potential breaches and automate responses.