Security teams have an important job: to protect the organization from an ever-evolving threat landscape
With growing amounts of data, ever-changing threats and the sheer volume of security alerts, this can feel overwhelming. But there’s a better way.

Cortex® XSIAM™ unites SOC capabilities that include XDR, SOAR, SIEM, ASM and others into a single SecOps platform.
It empowers security analysts with AI-driven outcomes and an automation-first approach to:
- Simplify SecOps and reduce operational complexity.
- Quickly and accurately stop threats at scale.
- Accelerate incident remediation and security outcomes.
Check out XSIAM in action.

You start your day in the XSIAM Command Center, where you see a complete overview of your security operations.
From here, you monitor ingested data sources, track security metrics and see how many alerts have resulted in security incidents.
You see how many incidents have been resolved automatically by XSIAM, and then you pivot to the incidents that need your attention.
Let’s dig deeper.

You open Cortex Copilot, your AI-powered SecOps assistant in XSIAM. This shows that you have a number of open incidents that you’ll need to investigate.

You ask Cortex Copilot which incident you should work first.
You see a Critical incident involving Potential Data Exfiltration, so you go into that incident view.

Data convergence and alert stitching
All the information you need to investigate and resolve this incident is provided in one place.
Based on the data sources you ingested, XSIAM’s AI-driven models have automatically stitched together disparate alerts into this single incident. You can see every alert and data source involved.

SmartScoring risk prioritization
The incident is Critical and has a risk score of 100. Here’s why …

The XSIAM SmartScore™ is an AI-driven engine that automatically calculates a risk score and fully explains the incident-specific factors behind it.
And with Critical classification and a 100 SmartScore, there’s no time to waste.

Before you even looked at this incident, XSIAM automatically ran playbooks to completion against several security alerts. It also ran some playbooks that require your review and input.
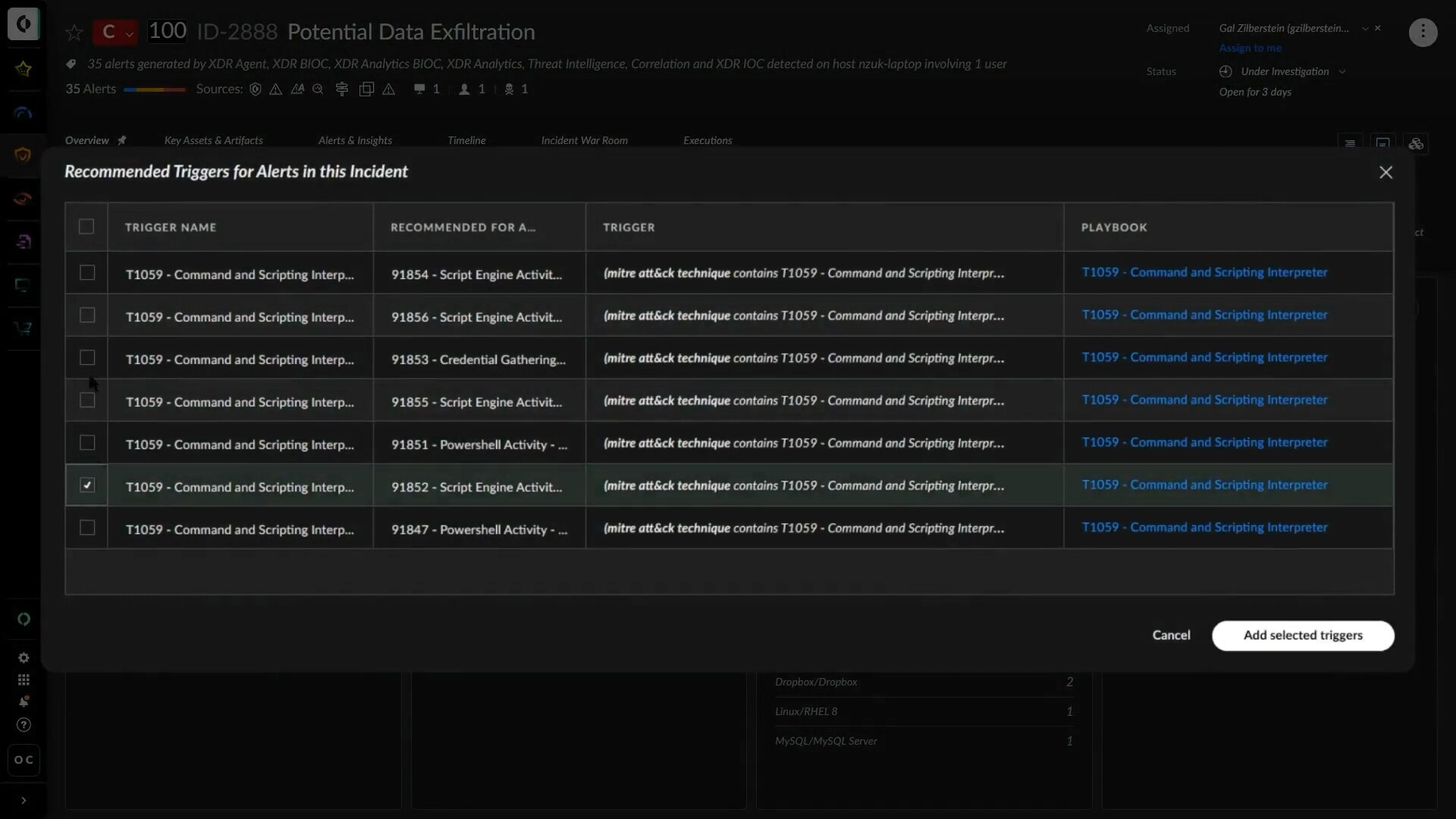
And based on other activity observed in this incident, XSIAM is intelligently recommending additional playbooks that you may want to run.

You drill down and learn about one of the recommended playbooks.
You can run the recommended playbook right away. Or, you can preview the playbook actions before running it.

Under the Executions Tab, you get a full overview of everything that happened during this incident.
The causality view connects the alerts and provides a visual of incident-related events.
Here, you have the full story of what happened across various data and alert sources.

From here, you drill into specific events for more context and details.
In this incident, PowerShell was used to execute several suspicious subprocesses.

And if you want a detailed view of all the threat actor's actions, you can see them mapped back to MITRE ATT&CK® tactics and techniques.

After you've investigated this incident and taken recommended remediation actions, you resolve the incident.

…And add your input.

But things don't stop there. XSIAM helps you become more secure and efficient every day.
XSIAM will learn from the actions you took in this incident and recommend future tasks that will trigger automatically the next time an incident like this happens in your environment.

So, the manual actions you took here will be handled by XSIAM in the future, improving your security every day and allowing you to resolve more incidents in less time.

All of this is enabled by a new approach to security operations.
XSIAM's platform convergence, AI-driven outcomes and automation-first approach transform the capabilities of the SOC.

Data ingested in XSIAM is optimized to detect anomalous or malicious activity

Broad integration support and simplified data onboarding reduce engineering and infrastructure complexities and allow SOCs to easily ingest more data sources.
Bringing in new data sources is as simple as a few clicks …
Good analytics require good data. Continuous data collection, stitching and the normalization of raw data enable superior security analytics in XSIAM.
In this case, you want to add a new Dropbox data source to XSIAM.

You can see and control exactly what's being imported. This is data and automation onboarding made easy.
In addition to onboarding the data, you can quickly import existing automation content packs associated with Dropbox, including playbooks, dashboards and more.

You + Cortex XSIAM
Whatever threats are making waves in the headlines, Cortex XSIAM gives you the AI assistance, automation and transparency to rise above — and stay on top of — the incidents that keep you from doing the important things, at work and in life.
Transform your SOC with Cortex XSIAM.
Speak to an expert today





