What is a Phishing Attack?
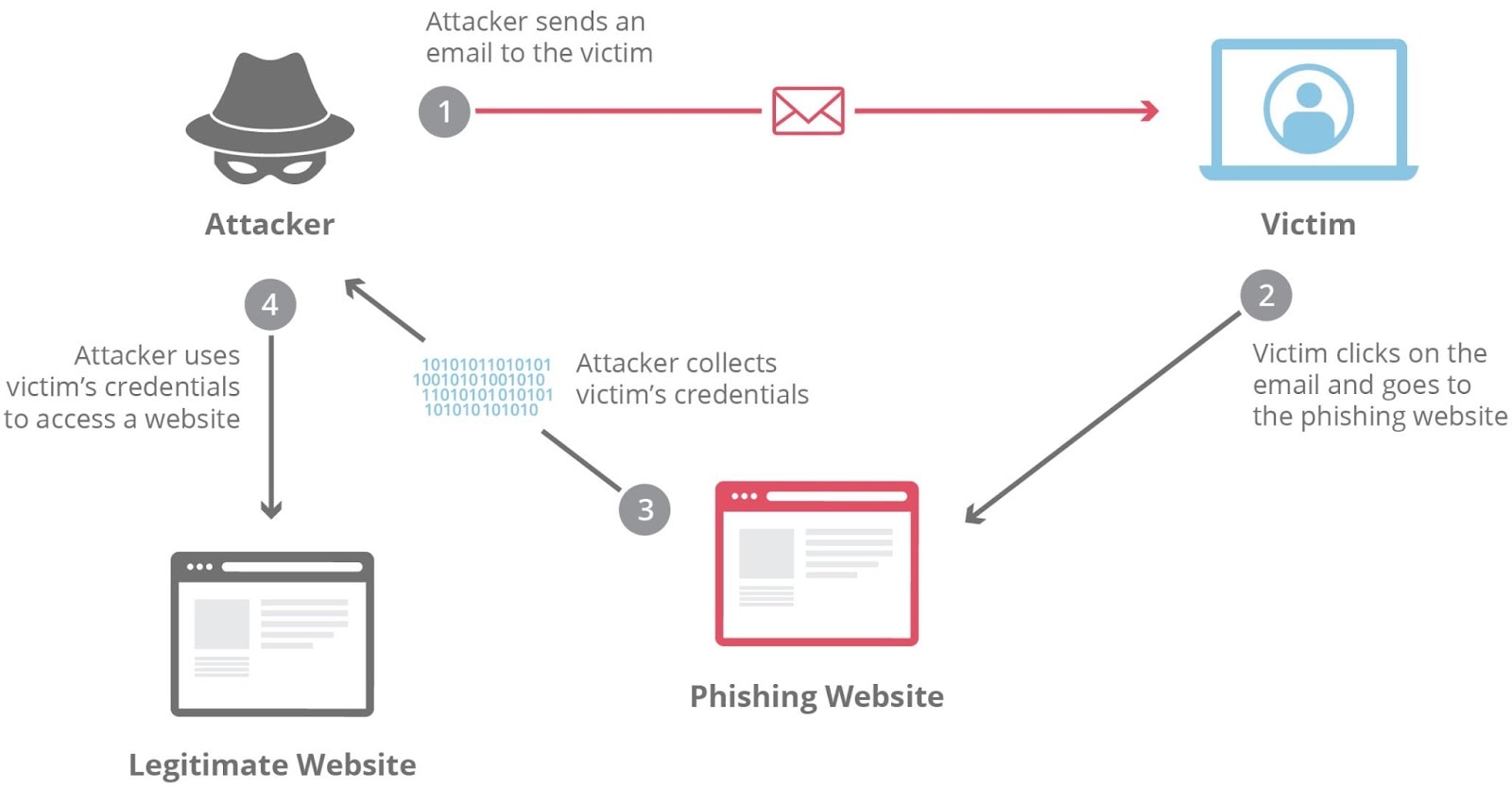
Phishing is a cybercrime where attackers disguise themselves as trusted organizations to trick people into giving up sensitive information like usernames, passwords, and credit card numbers. These scams usually occur through email but can also happen via phone calls, websites, and social media.
The main goal is identity theft, allowing attackers to access personal accounts or company systems, which can result in financial loss or reputation damage. Phishing exploits human trust and urgency. Despite advancements in cybersecurity, it remains a threat, so it's crucial to stay aware and cautious.
The Evolution of Phishing
Phishing attacks, a form of social engineering, have evolved significantly since their emergence in the mid-1990s, marked by increased targeting sophistication. Attackers conduct meticulous research to craft personalized messages tailored to their victims, a method known as spear phishing.
Originally, phishing scams were relatively unsophisticated and often involved mass-distributed emails intended to lure unsuspecting users into providing sensitive information, such as passwords or credit card details.
As internet use has increased, so too have the tactics of phishers, who now deploy more advanced techniques, utilizing email spoofing, voice phishing (vishing), and even SMS phishing (smishing). These methods deceive victims into believing they interact with legitimate and trusted sources.
This adaptation showcases the dynamic nature of cybercriminal activity, driven by technological advancements and the relentless pursuit of exploiting human vulnerabilities in digital communication.
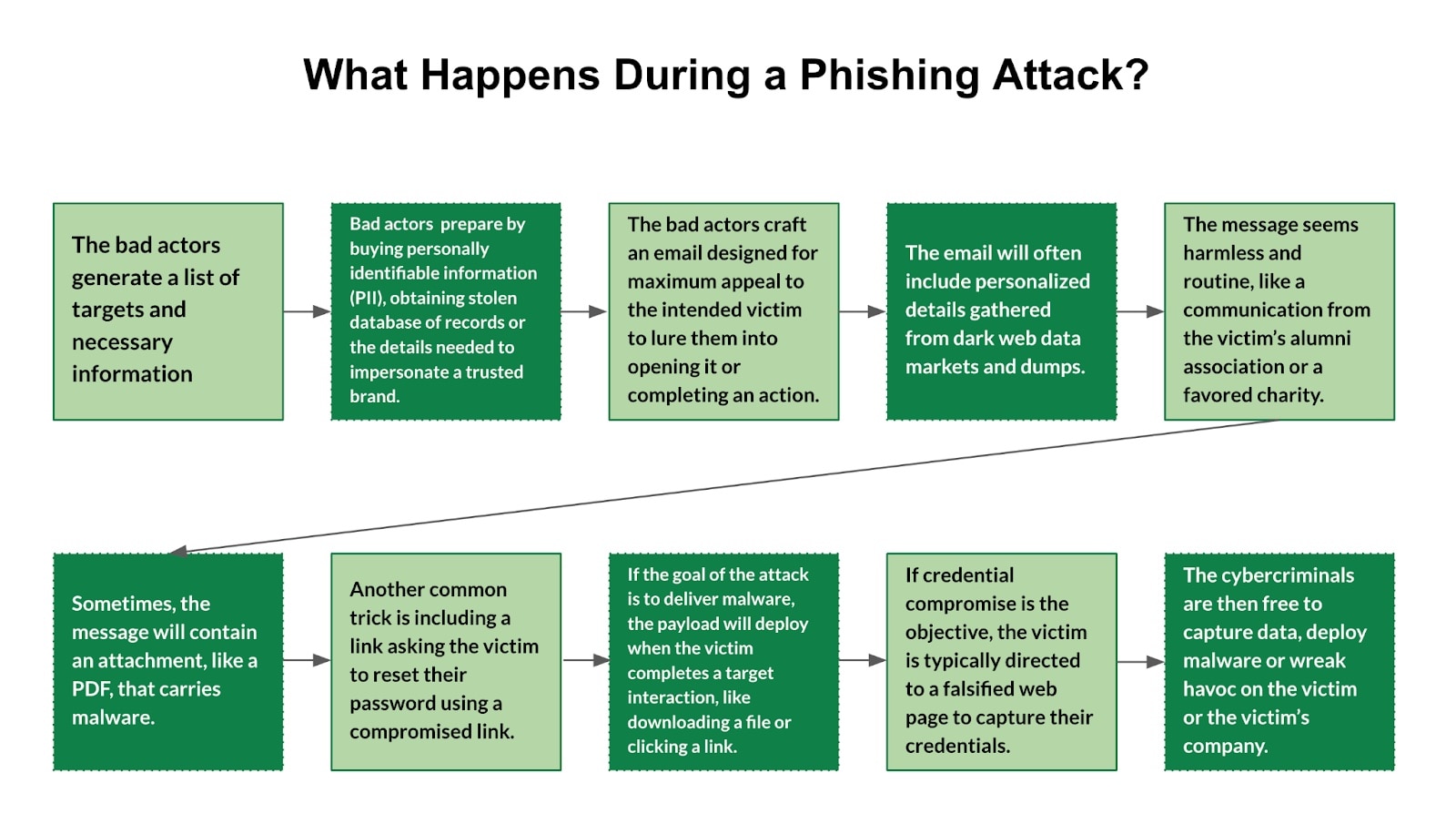
How Does Phishing Work?
Phishing works by tricking victims into providing sensitive information such as usernames, passwords, credit card numbers, or other personal details. Attackers typically use deceptive emails, messages, or websites that appear legitimate.
Here's a step-by-step breakdown:
- Bait Creation: Attackers create a convincing message or website that mimics a trusted entity, such as a bank, social media site, or online service.
- Delivery: The phishing bait is delivered to potential victims via email, text messages, social media, or other communication channels.
- Deception: The message typically contains urgent or enticing content, prompting the recipient to click on a link, download an attachment, or provide personal information.
- Exploitation: If the victim takes the bait, they are directed to a fraudulent website or form where they enter their sensitive information.
- Data Harvesting: The attackers collect the submitted information and use it for malicious purposes, such as identity theft, financial fraud, or further cyberattacks.
Phishing attacks have become one of the most prevalent and effective methods of cybercrime due to their ability to avoid detection methods. Falling for these scams increases the risk of losing sensitive information and the possibility of identity theft, data loss, or malware infections.
The availability of low-cost phishing kits has added to their ease of deployment. These kits are collections of tools, such as website development software, coding, spamming software, and content, that can be utilized to collect data and create convincing websites and emails.
Adding more sophisticated and mysterious phishing techniques has enabled even novice threat actors to bypass traditional security defenses.

Business Email Compromise (BEC) vs. Phishing
Business Email Compromise (BEC) and phishing are deceptive email attacks that target different audiences and have distinct goals. BEC is targeted and financially motivated, while phishing casts a broader net for personal data.
BEC focuses on specific individuals within an organization, like executives or finance personnel, to manipulate business processes for financial gain. Attackers gather information to create convincing messages that can lead to unauthorized transactions or disclosures of sensitive information.
In contrast, phishing attacks aim to reach a broad audience to harvest personal information, such as passwords or credit card details. These emails are less personalized and try to trick many individuals at once, making phishing more about data collection than directly manipulating business operations.
Types of Phishing Attacks
While not a complete compilation, the following are the most common phishing techniques attackers employ. Understanding these techniques can help individuals and organizations better recognize and defend against phishing attacks.
Email Phishing
Attackers send fraudulent emails that appear to come from a reputable source. They ask recipients to click on a link, download an attachment, or provide sensitive information. Attackers use various tactics, including creating a sense of urgency or fear, to manipulate the recipient into complying with their requests. The links may redirect users to legitimate counterfeit websites, while attachments could contain malware that infects the recipient's device.
Spear Phishing
Spear phishing is a targeted form of cybercrime in which attackers use personal information to craft convincing messages for specific individuals or organizations. Unlike generic phishing, which targets many recipients, spear phishing is highly personalized.
Attackers gather details from sources like social media or company websites to make their messages appear legitimate and relevant. This increases the chances that the victim will engage with the content, disclose sensitive information, or click on malicious links, making spear phishing more effective than broader phishing strategies.
Case Study: FreeMilk Conversation Hijacking Spear Phishing Campaign
Whaling
Whaling is a form of phishing targeted at high-profile company executives. Whaling aims to gain access to highly confidential information through email communication. The message often appears urgent to convince the receiver to act quickly. In this case, the victim may click a malicious link without thinking beforehand, enabling the attacker to steal login credentials and sensitive data or download malware.
Smishing (SMS Phishing)
Smishing acts like other phishing attacks, but it comes as an SMS message. Often, the message will contain a fraudulent attachment or link, prompting the user to click from their mobile device.
Vishing (Voice Phishing)
Vishing, also called ‘voice phishing,’ is when an attacker targets victims over the phone to gain access to data. To appear legitimate, the attacker may pretend to be calling from the victim’s bank or a government agency.
Clone Phishing
Clone phishing is a sophisticated approach where attackers create a nearly identical copy of a legitimate email, replacing links or attachments with malicious ones. The cloned email appears to come from a trusted source, making it more likely that the victim will trust the message and follow the instructions.
Pharming
Instead of tricking individuals directly, attackers redirect legitimate website traffic to fraudulent websites without the user's knowledge, often through DNS poisoning. Many cybersecurity measures fail to notice this.
HTTPS Phishing
HTTPS phishing is an attack where attackers create fraudulent websites that use HTTPS, the protocol indicating a secure connection, to appear legitimate and trustworthy. By securing their malicious sites with HTTPS certificates, attackers deceive victims into believing the websites are safe and authentic.
Credential-Based Attacks
A credential-based attack uses stolen or compromised login credentials (usernames and passwords) to gain unauthorized access to systems, networks, or accounts. These attacks often involve tactics such as:
- Phishing: Deceptive emails or messages trick users into providing their login details.
- Keylogging: Malware that records keystrokes to capture credentials as they are typed.
- Credential Stuffing: Using lists of stolen credentials from one breach to gain access to other systems, exploiting the fact that people often reuse passwords across multiple sites.
- Brute Force Attacks: Systematically trying all possible combinations of usernames and passwords until the correct one is found.
- Man-in-the-Middle Attacks: Intercepting communication between the user and the system to capture credentials.
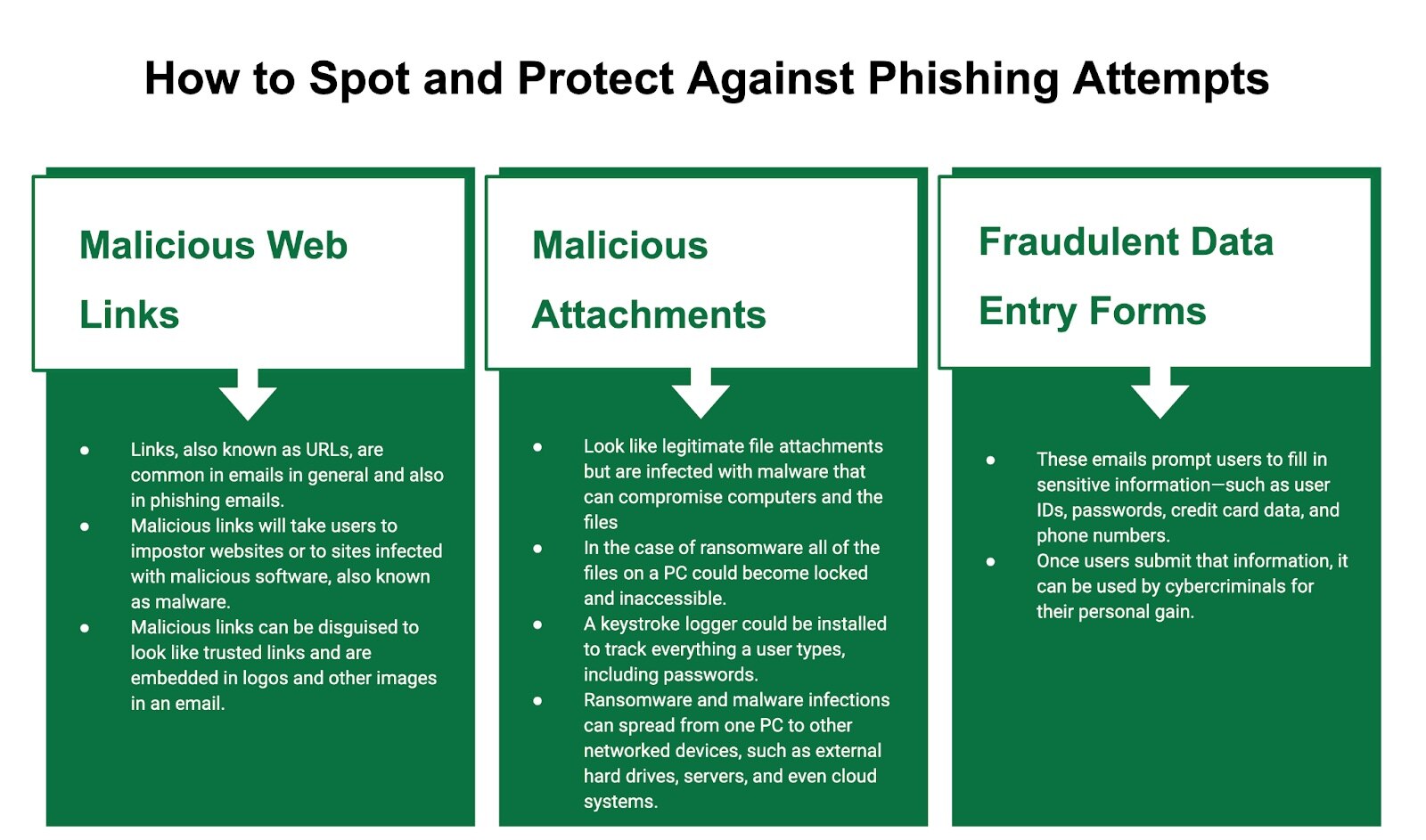
How to Recognize Phishing Techniques
Cybercriminals have evolved significantly over the years. They can produce fraudulent messages and attachments that can convince nearly anyone. Well-trained individuals following proper security protocols can often detect even sophisticated phishing attempts. Even the most seasoned cybersecurity professionals find these hard to detect. Potential targets can look for common signs to spot a phishing message.
Common Signs of Phishing
The best protection against phishing attacks is understanding and identifying the common giveaways of a phishing email that may or may not look suspicious. The following are a few giveaways:
- Messages detailing problems with accounts, bank details, financial transactions, and shipments are prevalent during the holidays when most people are expecting a delivery.
- The language appears incorrect, and the message lacks fluency, which is typical of a native speaker. It features misspellings, poor grammar, and usage issues.
- The message looks like it is from a trusted brand, but it contains unfamiliar elements, such as not-quite-right colors, formats, or fonts.
- The message looks unprofessional, but it is presented as communication from an executive or other influential person.
- The sender is a U.S. federal government agency asking you to provide personally identifiable information (PII) via email or follow a link to a URL that does not end in .gov.
- The sender asks for your social security or tax identification number immediately.
- The sender's address, name, or email address looks strange.
- The message is from someone you don’t recognize asking for gift cards, money transfers, banking, or credit card information.
- The message contains a link to click or an attachment to download, but the address or filename seems unusual.
- Unexpected attachments or files with unusual or unfamiliar names are telltale signs they are malicious.

How to Protect Against Phishing Attacks
Phishing is a multifaceted threat that requires a comprehensive strategy to defeat. Overcoming the phishing challenge involves an integrated end-to-end process, ranging from proactive to reactive. If you have one and not the other, you’re unprepared to deal with the threat.
Phishing Security Stack
Recognizing that phishing isn’t just an email problem is vital. It’s essential to have a security stack that can address advanced phishing and invasive phishing attacks. Using a system based on URL databases and web crawlers isn’t going to work. Technologies like inline machine learning are needed to analyze the page content delivered to the end user to ensure no phishing risk and prevent patient zero.
Security Lifecycle Approach
Reducing the risk of phishing isn’t just about deploying any one technology; it’s about having a full lifecycle approach. That means the organization needs to have both proactive and reactive capabilities. No matter how much you deploy or invest in security, you must plan for something to get through. If an employee is phished and a credential is stolen, does the organization have the ability to detect malicious access and then respond to it?
Executive management must work with the organization’s teams to ensure that the technology, people, and processes are in place to help prevent as many inbound phishing attacks as possible.
Following are some additional phishing defense strategies:
- Employing spam filters and setting up email authentication protocols can significantly reduce the risk of phishing emails reaching users’ inboxes.
- Regularly updating software and systems with the latest patches helps close security gaps that cybercriminals often exploit.
- Implementing multifactor authentication adds an extra layer of security by requiring an additional verification form beyond passwords.
- Educating users about the nature of phishing threats is crucial. Regular training sessions and updates can help people recognize suspicious emails, links, or websites.
- Implementing resilient email filtering systems can significantly reduce the number of phishing emails reaching the inbox.
- Ensuring networks are secured with firewalls and up-to-date antivirus software to block potential phishing attacks is vital.
- Embracing anti-phishing tools and strategies, such as browser extensions and cybersecurity software, can offer real-time protection by alerting users to potential phishing sites and blocking malicious content before damage occurs.
Minimizing Risk with a Comprehensive Platform
A comprehensive security platform, like Cortex XSIAM, that focuses on people, processes, and technology can minimize successful phishing attacks.
In the case of technology, security tools like sandboxing analyze the unknown link or file and implement a policy to prevent access if it is malicious. Other processes, like URL filtering, block known malicious websites and unknown websites to prevent attacks early on. Access to a threat intelligence cloud provides the combined knowledge of the global community, enabling protections if a similar attack has been seen before.
Email gateway reputation-based solutions can catch and classify phishing emails based on the embedded URLs' known lousy reputation. However, well-crafted phishing messages with URLs from compromised legitimate websites will not have a bad reputation at the time of delivery and will be missed by these tools.
The most effective systems identify suspicious emails based on analytics, such as unusual traffic patterns. They then rewrite the embedded URL and constantly check it for in-page exploits and downloads.
These monitoring tools quarantine suspicious email messages so administrators can research ongoing phishing attacks. If many phishing emails are detected, administrators can alert employees and reduce the chance of a successful targeted phishing campaign.