Precise detection
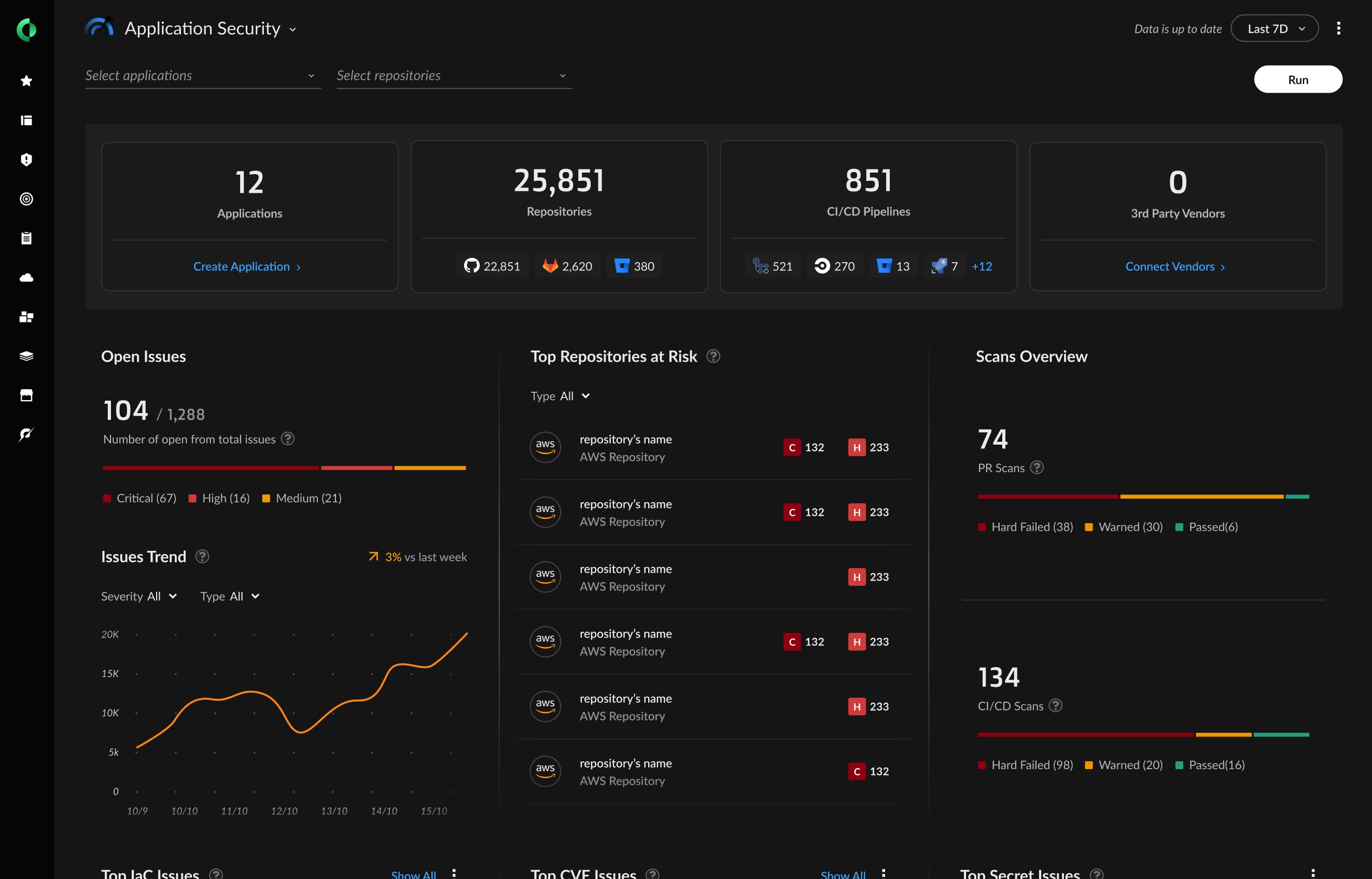
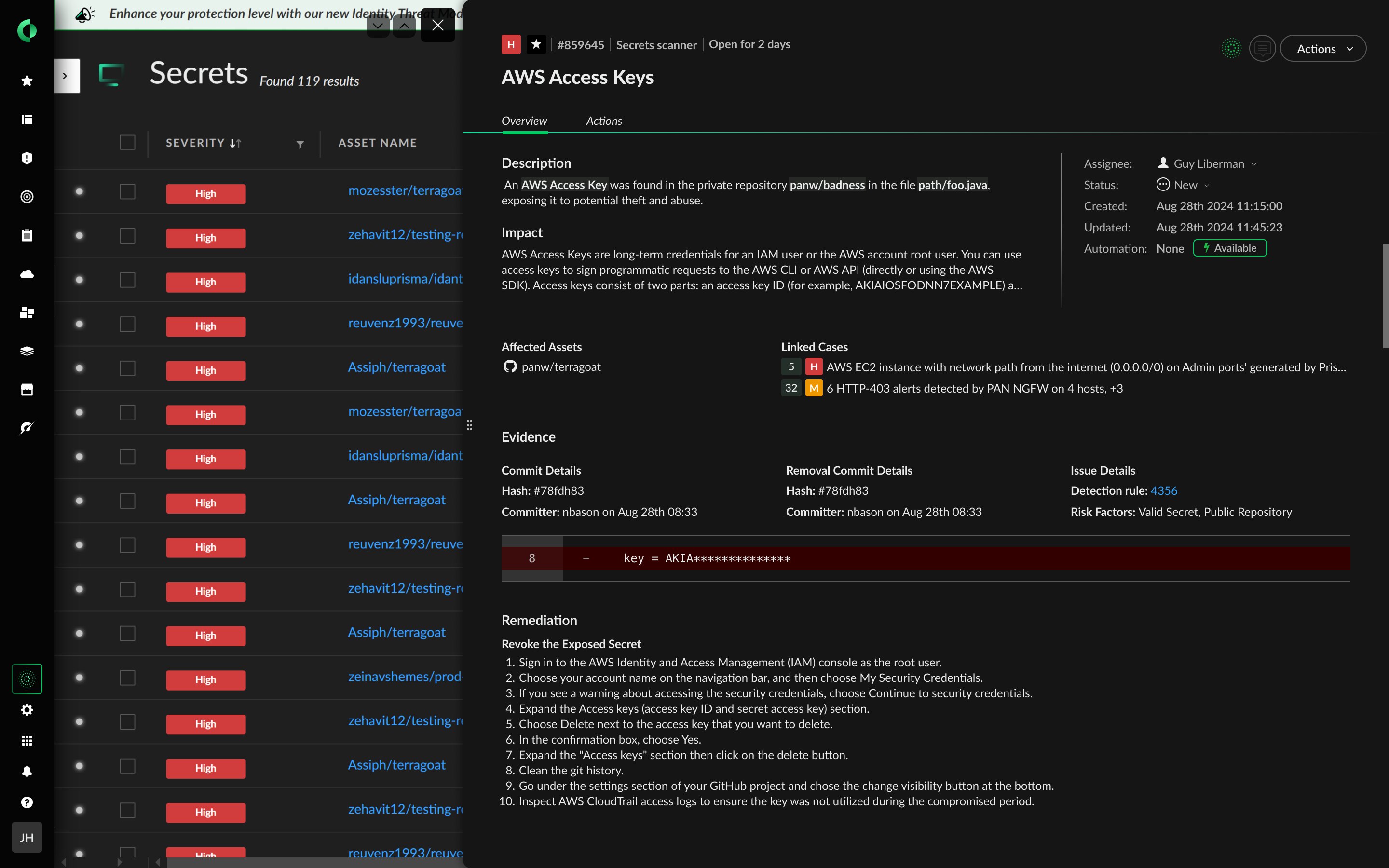
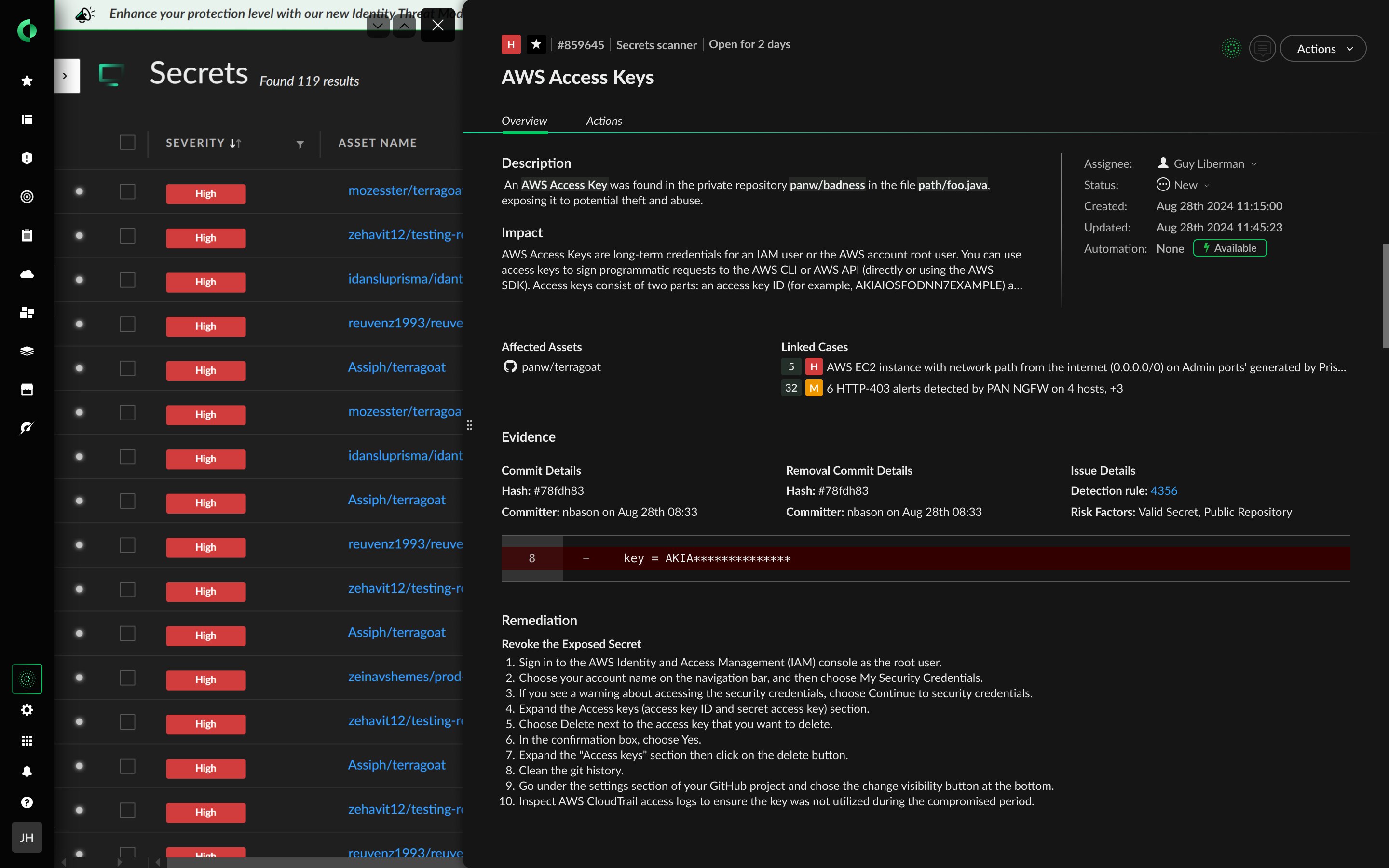
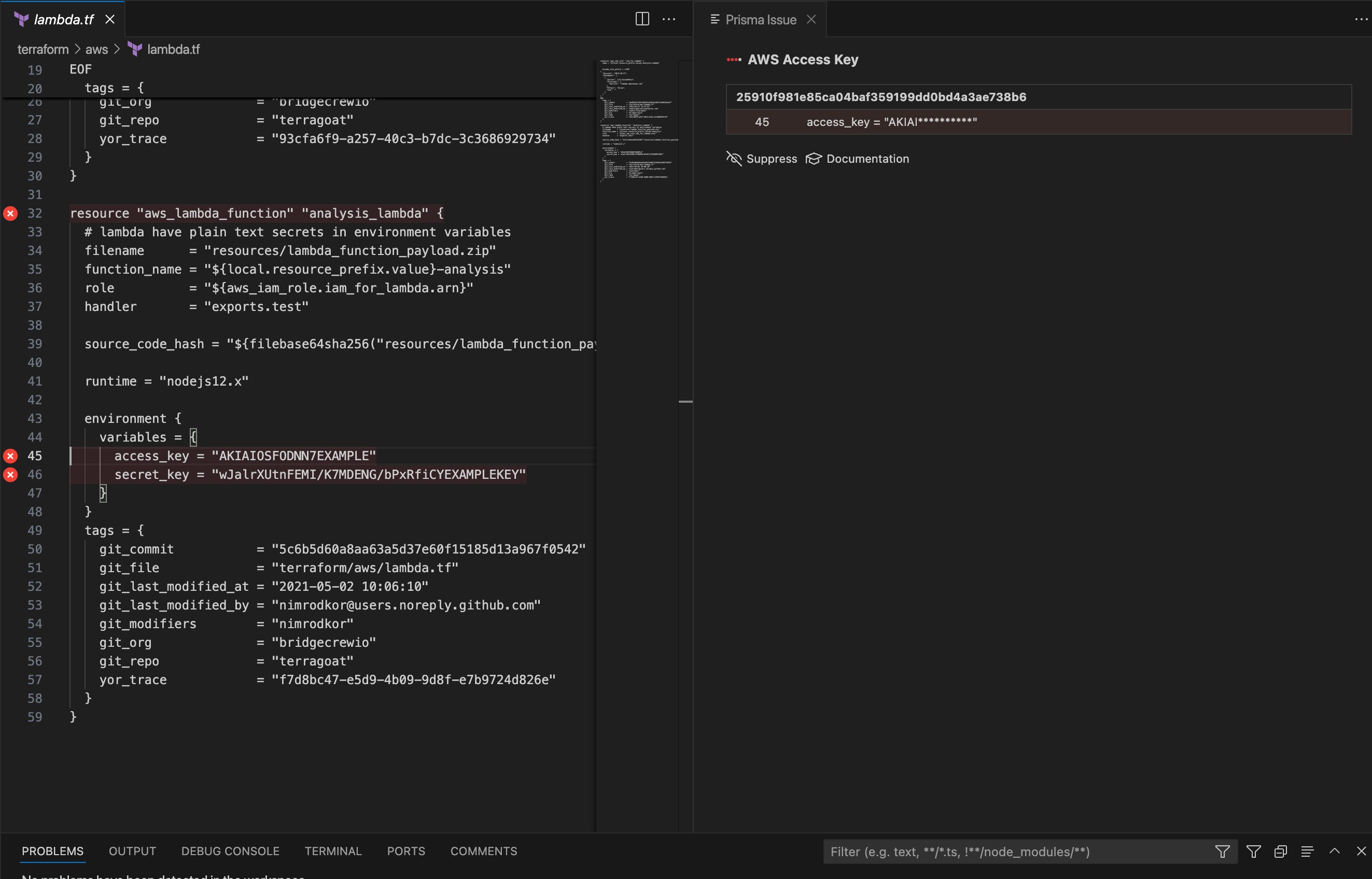
Secrets using regular expressions (access tokens, API keys, encryption keys, OAuth tokens, certificates, etc.) are the most commonly identified. Cortex Cloud leverages over 100 signatures to detect and alert on the wide array of secrets with known, predictable expressions.
Vast coverage
100+ domain-specific secret detectors ensure precise alerting in both build and runtime.
Broad and deep scanning
Scan for secrets in all files in your repositories and the version histories across your integrations.