The Attack Surface is Growing and Changing!
The network landscape is expanding at a crazy pace. There are new vulnerabilities released every day, and the number of applications and endpoints is continually growing. IT teams are burdened to identify and manage the full scope of IoT vulnerabilities. SecOps needs technologies that provide contextualized threat information on every device in their environment to find anomalies faster and better remediate risks.
Accelerate Incident Response by leveraging critical contextualized threat intelligence from WootCloud HyperContext®
WootCloud’s integration with Cortex™ XSOAR allows customers to append contextualized alerts with critical intelligence to SOAR workflows so users can build and automate workflows, simplify the incident response process, and reduce the amount of human intervention necessary to handle security incidents.
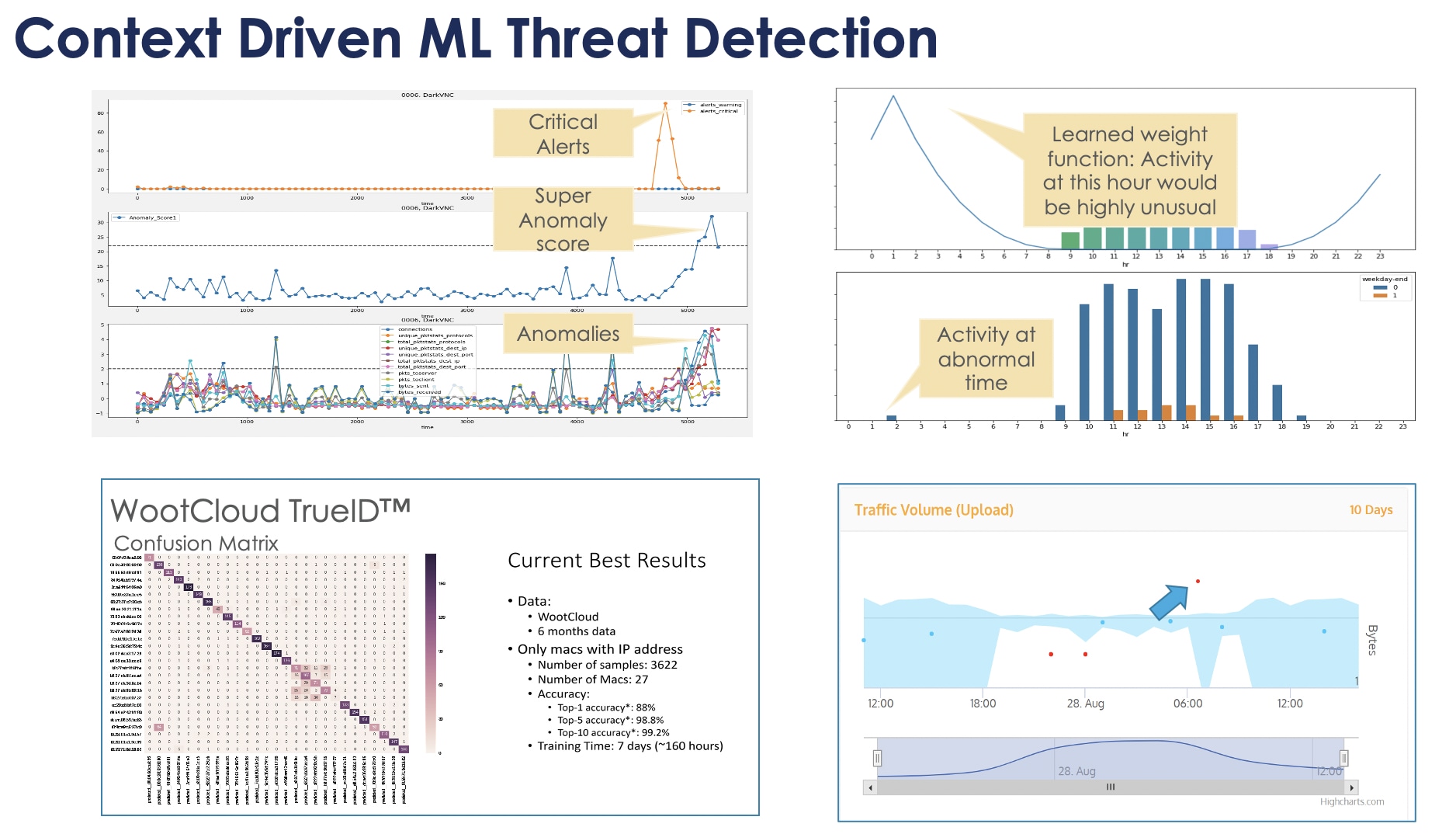
WootCloud analyzes and evaluates threats detected while adding deep device fingerprinting to each event, based on network/packet details as well as traffic from Bluetooth and BLE devices. WootCloud runs algorithms to correlate anomalies and events with detailed information, creating highly-curated super anomalies with relevant accurate information. This context-rich threat information helps SecOps build better response workflows, increasingly automate incident management, and response tasks within workflows and provide accurate formalized incident, workflow, and performance reports.
By automating time-intensive, manual processes and operational workflows, and delivering powerful, consolidated analytics, real-time dashboards, and reporting from across the security infrastructure, this integration maximizes the incident response capabilities of over-burdened and understaffed security operations.
Use Case: Boardroom video conferencing systems hacked
Scenario: Video conferencing equipment is commonly found installed in conference room and meeting rooms worldwide. These IoT devices are deployed inside the enterprise network and often have unrestricted access to other IoT devices.
Anomalies Detected: The WootCloud HyperContext engine deployed in a customer’s environment detected anomalous communication where a Polycom HDX device was questionably attempting login into other devices on the network using common usernames and passwords. The unusual login attempts highlighted an anomalous event because of the context of the Polycom device. There was no reason for the Polycom device to connect to other devices. Other Linux devices do attempt to use SSH for remote access and it’s hard to distinguish bad behavior unless necessary context is there. On investigation, WootCloud discovered 4 botnets.
Expertise Matters: The WootCloud’s engine is powered by machine learning and designed to detect for such anomalies in any given data set, from unusual patterns, uncommon network traffic or unexpected behavior. Most existing security solutions are not designed/built to catch these kinds of context driven threats and anomalies.
Facts Delivered Results: The company acted upon it immediately and was able to save their environment from rogue network activity and possible future data breach.
The WootCloud app is currently listed in the Cortex XSOAR Marketplace.