Cortex's Latest Innovative Releases: Amplifying Visibility and Fortifying Protection
At Palo Alto Networks, we're constantly pushing the boundaries of security, and our latest wave of innovations is no exception. With our newest feature release, I'm excited to announce that we're fortifying our leading Cortex security operations platform, providing our customers with expanded visibility and enhanced protection against the latest attack techniques.
This release features a number of new enhancements, such as advanced threat protection modules that stop malware before it is created and protect systems from being compromised at boot time. We’ve equipped Cortex XSIAM with cutting-edge capabilities, providing clear visibility into security and IT operations, amplifying security efficacy, and enhancing platform usability improvements. This is just the tip of the iceberg when it comes to the long list of innovations that our Cortex roadmap is committed to delivering to customers in our journey to revolutionize the SOC.
Learn more about the newest features now available across the Cortex Portfolio below and sign up for our newsletter to stay up to date on the latest innovations from Cortex.
Cortex XSIAM 2.1
Cortex XSIAM is one of the fastest-growing and innovative products in the history of cybersecurity, and the new features included in this release exemplify how we can enable you to be two steps ahead of your adversaries. The Cortex XSIAM 2.1 release introduces a host of capabilities, from enhanced visibility and security efficacy against the latest threats to platform usability improvements that help you keep up with the latest techniques in attack behavior. Let's delve deeper into each of these exciting additions.
- Enhanced XSIAM Command Center: Optimize your security operations with powerful new dashboards that provide instant visibility into your security operations center. You can now drill down to explore your data inventory and see a live feed of XSIAM activity.
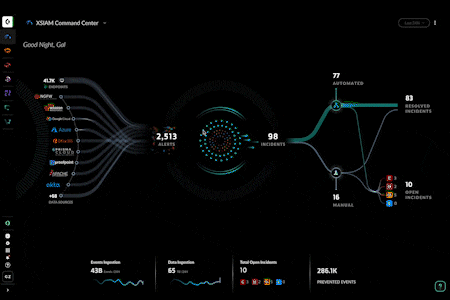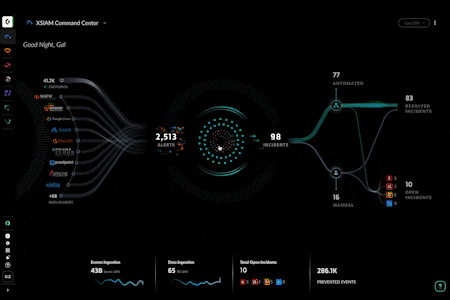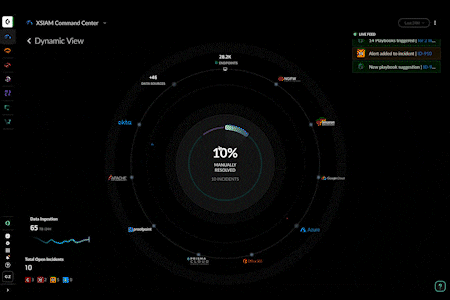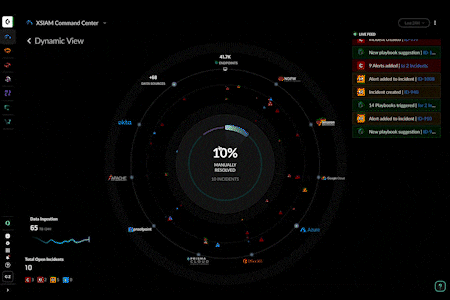
- Manual Incident Creation: Create incidents in XSIAM, expanding incident management capabilities to manage threats you discover, like insider threats, threat hunting exercises, and more.
- New User Risk Data: Improve user risk analysis with two new data sources in User Risk View: Common OSs displays frequently used operating systems, and Common Locations shows the top connection countries.
- Bring Your Own Keys (BYOK): Expand secret management capabilities to encrypt data in new Cortex XSIAM tenants using your own encryption keys.
Cortex XSIAM includes XDR and XSOAR integrated into it, so in addition to these new enhancements, XSIAM 2.1 will also inherit major upgrades included in both XDR 3.9 and XSOAR 8.5.
Cortex XDR 3.9 and Agent 8.3
Earlier in January 2024, we were named a leader in Gartner’s EPP Magic Quadrant, as well as a leader in the MITRE Engenuity ATT&CK Evaluation, IDC, and AV Comparatives, reinforcing Cortex XDR’s position as the industry’s most effective endpoint security solution and a force to be reckoned with in the market. Cortex XDR 3.9 solidifies this with several new capabilities that enhance its efficacy and enable you to stay ahead of the latest techniques in attack behavior.
We're introducing two enhanced threat protection modules in XDR 3.9: On-Write Protection and Pre-Boot (UEFI) Protection. The On-Write Protection functionality empowers users to stop malware on-write and defend against threats before they execute or move outside your visibility. This is done by using local machine learning and cloud-based WildFire analysis to stop malicious files during the on-write process, prior to execution.
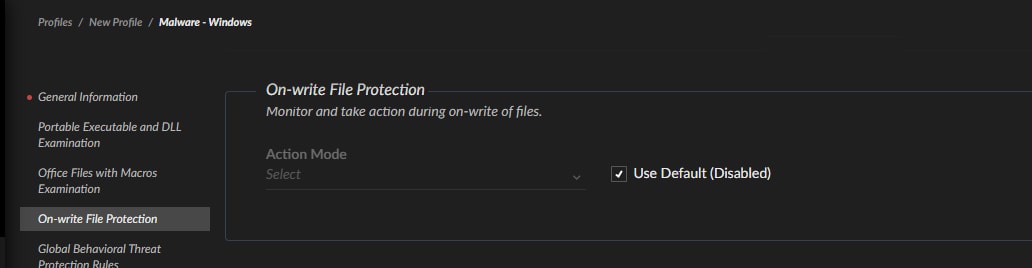
The new Pre-Boot (UEFI) Protection module uses behavioral analysis to detect suspicious changes to the UEFI image, then blocks these attacks proactively or can notify an analyst when an image was tampered with. This allows analysts to stop threats targeting the UEFI image that attempt to compromise the host’s boot process, prior to the OS loading.
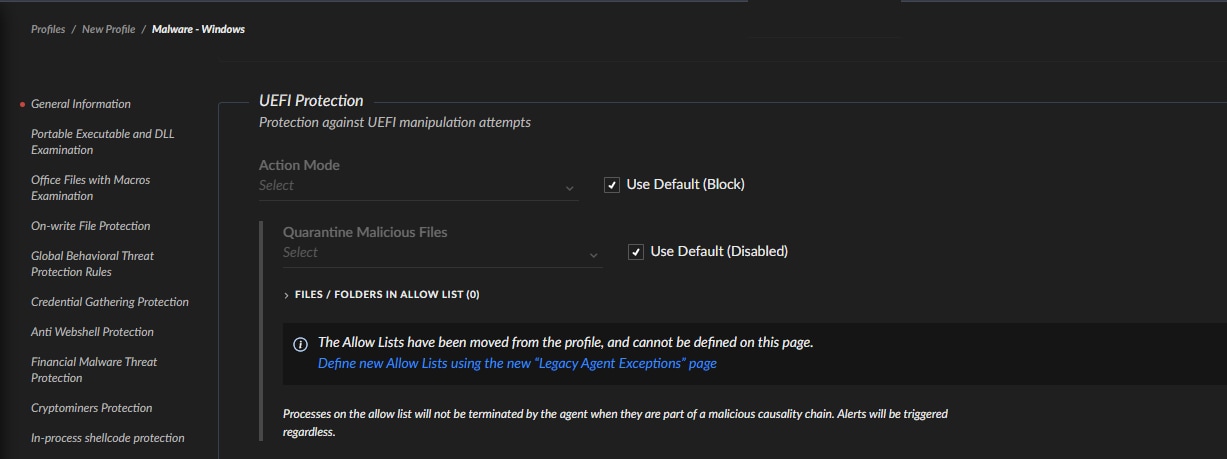
Several other enhancements to the Cortex platform include:
- XDR Platform Access Management Enhancements: Customers using the Cortex XDR API can now limit access to the API to a specific IP address or IP range, improving access control and the security of third-party integrations.
Cortex XSOAR 8.5
The latest Cortex XSOAR 8.5 release delivers new features and updated automations to improve your XSOAR user experience, optimize SOC efficiency, and facilitate cross-team collaboration. The enhancements included in this release deliver immediate value out-of-the-box and simplify automation workflows. Some of the new additions include:
- Multi-tenant Bilateral Communication (MSSP): Easily invite users from main and child tenants to incident investigations (including tasks, CLI, and War Room), as well as share investigation links with end customers via email, Slack, or Microsoft Teams.
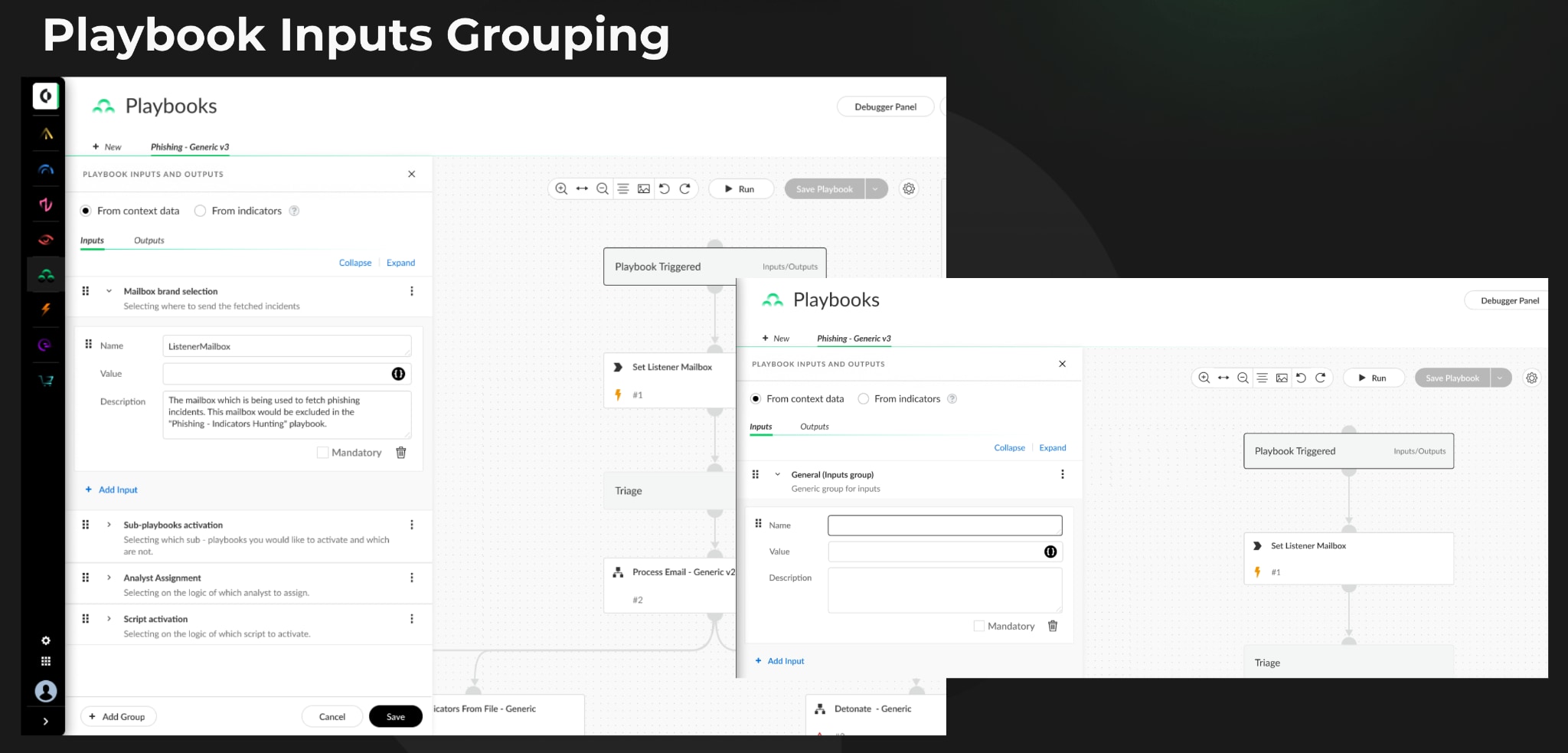
- Playbook Inputs Grouping: Group playbook inputs and outputs, making it easier to manage and understand the inputs required for different stages of the playbook.
- New Authentication Controls
- Passwordless Authentication: Option to require non-password credentials for SSO authentication.
- Force Authentication: Option to require users to reauthenticate access to the Cortex XSOAR tenant.
- Content Repository Enhancement: Easier configuration and management of content repository in the Cortex Gateway and Cortex XSOAR, enabling you to develop and maintain Cortex XSOAR content that is aligned with your development process.
- Improved Incident Navigation & Search
- For SOC analysts working on multiple incidents, next/previous navigation buttons provide the ability to navigate between incidents without returning to the Incidents’ page, saving time and facilitating analyst workflow efficiency.
- You can now do searches on War Room notes using the Incidents’ search bar. This new search option enables SOC analysts to query historical incident data for improved incident response and knowledge sharing.
- User and Roles: Administrators can now add phone numbers for users on the User Preferences page, which enables playbooks and scripts to trigger direct analyst communication, ensuring seamless collaboration during security incidents.
- System Email Customization: Customize a wide range of system emails sent to users, including notifications when a user is mentioned, a task is assigned or completed, and more. Customized emails give you the flexibility to include specific details about incidents, relevant data, and other information needed for prompt incident response.
- Authenticated Docker Image Repository: Use a custom container registry with your authentication credentials to apply custom images created on a private machine. Using your registry enables you to manage access permissions, ensuring that only authorized users can pull and use these custom images.
- XSOAR Content Packs and Integrations: Eleven brand-new content packs, playbooks, integrations, and automation use cases were added for easier out-of-the-box deployment.
Cortex Xpanse 2.4
In the newest advancement of Cortex Xpanse, our industry-leading attack surface management solution, the Expander 2.4 release introduces several enhancements. These include improvements to IP range management, filters to help you map your attack surface rules to align with the MITRE ATT&CK framework, improved reporting capabilities, and further enhancements to the Active Response module. Key highlights in Expander 2.4 include:
- MITRE ATT&CK context to exposures: You can now map your Attack Surface Rules to MITRE ATT&CK Framework to better understand the threats posed by your exposures.
- Active Response improvements, including:
- Enhanced configurability of playbooks to modify aspects of automation behavior such as ticketing and notifications.
- Gain additional incident details from Active Directory and Venafi with Active Response's new access capabilities.
- Quickly identify users who may have modified an instance with the expanded Prisma Cloud enrichment.
- Save time by onboarding Azure accounts directly through the top-level organization instead of individual tenants.
- New Attack Surface Rules: 40+ new and updated rules, including for critical risks such as SSH Terrapin Attack, Ivanti Connect Secure, Jenkins, and more.
- User-defined IP ranges: Users now have more granular control over the specific IP they want to be tagged, allowing more flexible asset management.
- PDF Support for Incident and Alert exports: You can now export individual incidents and alerts in PDF format for custom reporting.
If you’d like to learn more about these Cortex products, check out some great resources at paloaltonetworks.com/cortex.