Code Red Everywhere
Security teams are beset with alerts on the best of days. This simple truth stems from two issues melding together:
- Product proliferation: With the average SOC using more than 10 discrete security products, staying on top of event data from each product becomes a taxing exercise mired with duplication.
- Setting the right product sensitivity: It’s always a challenge to deciding the level of sensitivity a security product should have for its alert detection. If it’s not sensitive enough, dangerous incidents might slip through the cracks and result in real organizational harm. If it’s too sensitive, analysts end up receiving false positives that take up huge chunks of their time and decrease work satisfaction.
Both these challenges can be met with the help of security orchestration. A playbook that executes actions across products to assign severity to incoming incidents will not only save analyst time by removing this redundant task from their daily lives, but also improve the accuracy of incident assignment by coordinating automatically across product-sets.
The Severity Scoring Playbook
Let’s look at the flow of a playbook that assigns incident severity:
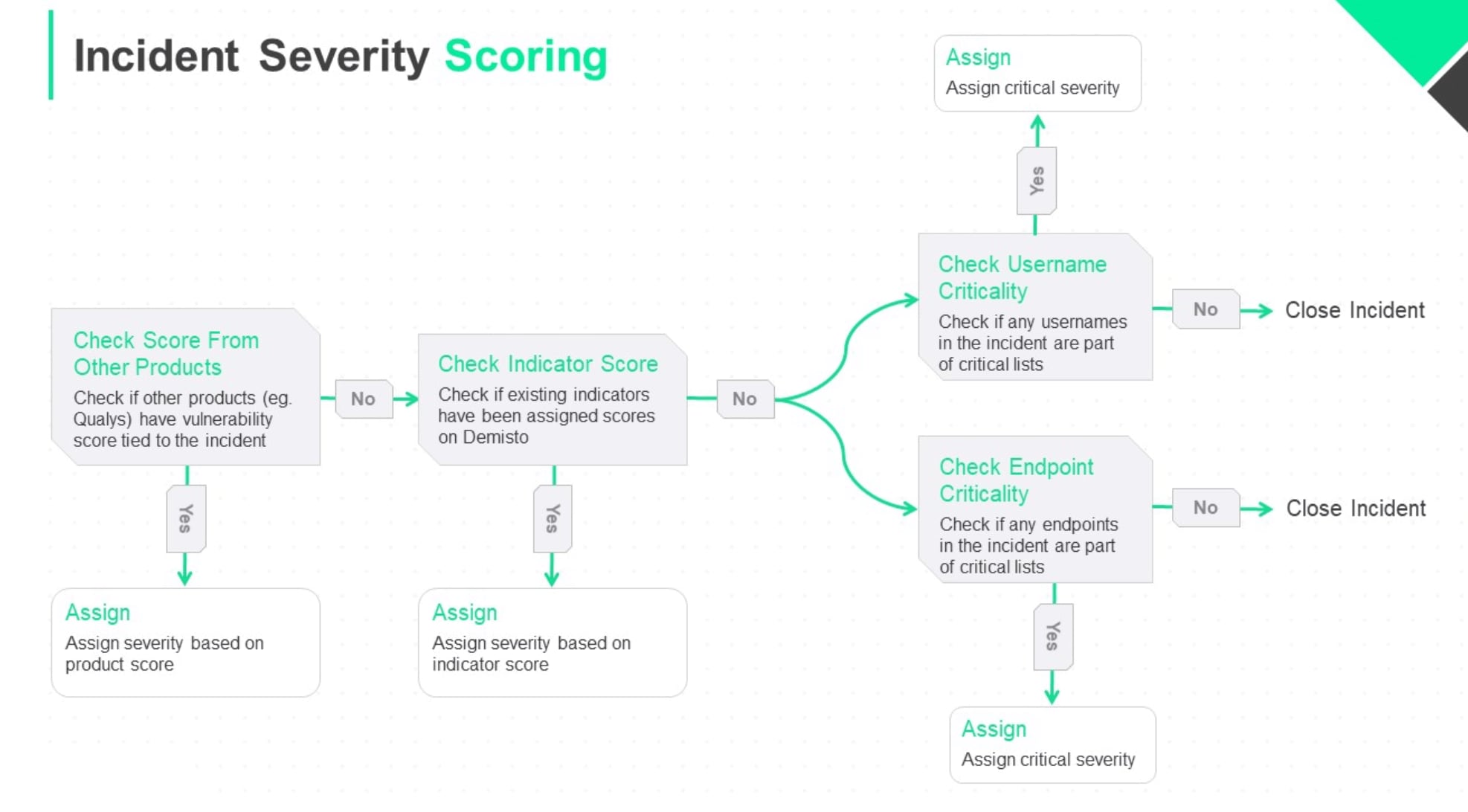
Step 1: Check External Product Scores
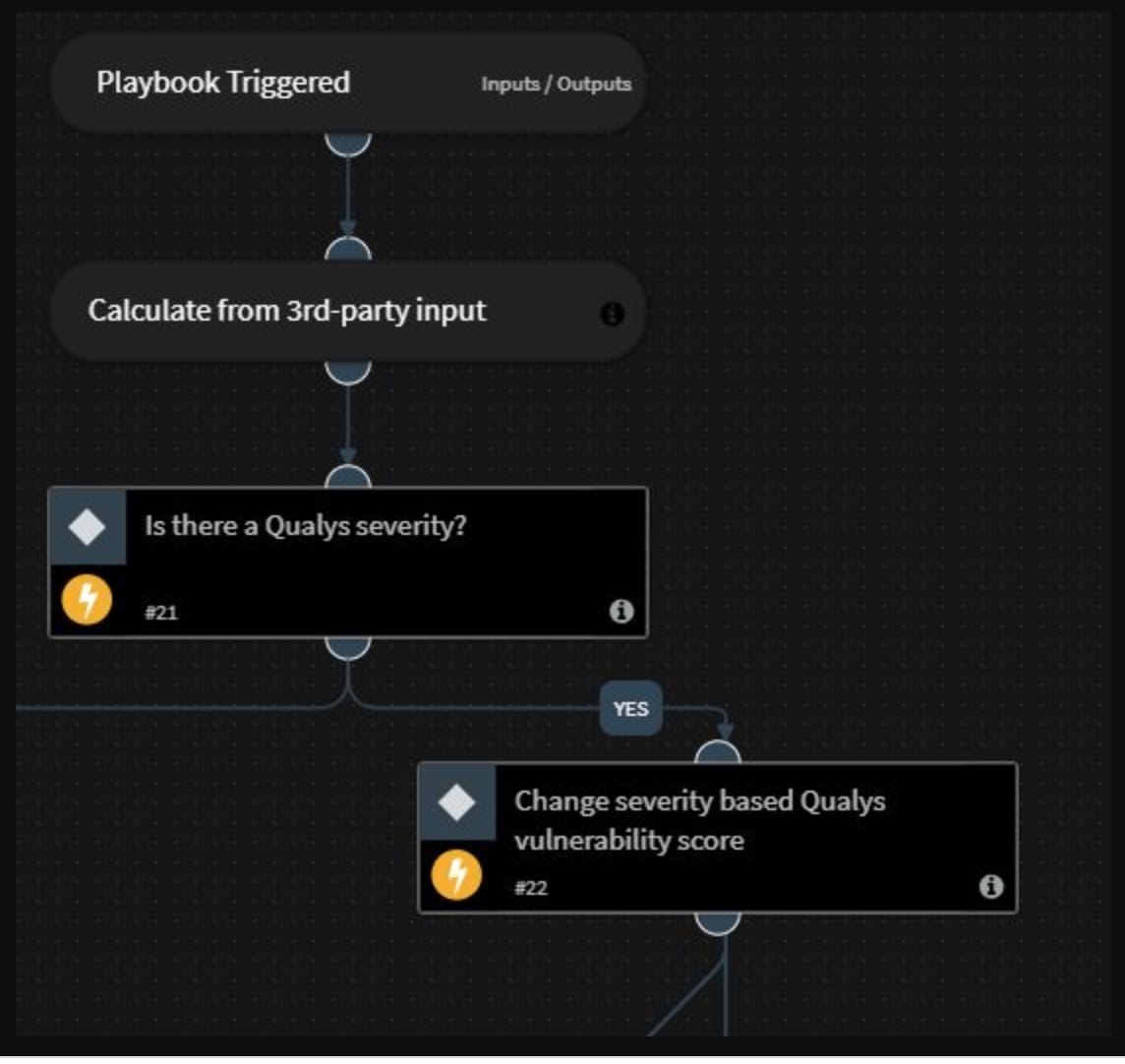
The playbook first validates whether any external vulnerability management products have recorded a severity level for the incident at hand. In the screenshot below, for example, the playbook executes a query to Qualys to check if there’s a recorded incident severity and assigns the same severity to the incident within Cortex XSOAR.
These actions ensure that teams utilize the strengths of their security products without having multiple tabs open at all times and manually performing low-level actions.
Step 2: Check Indicator Scores
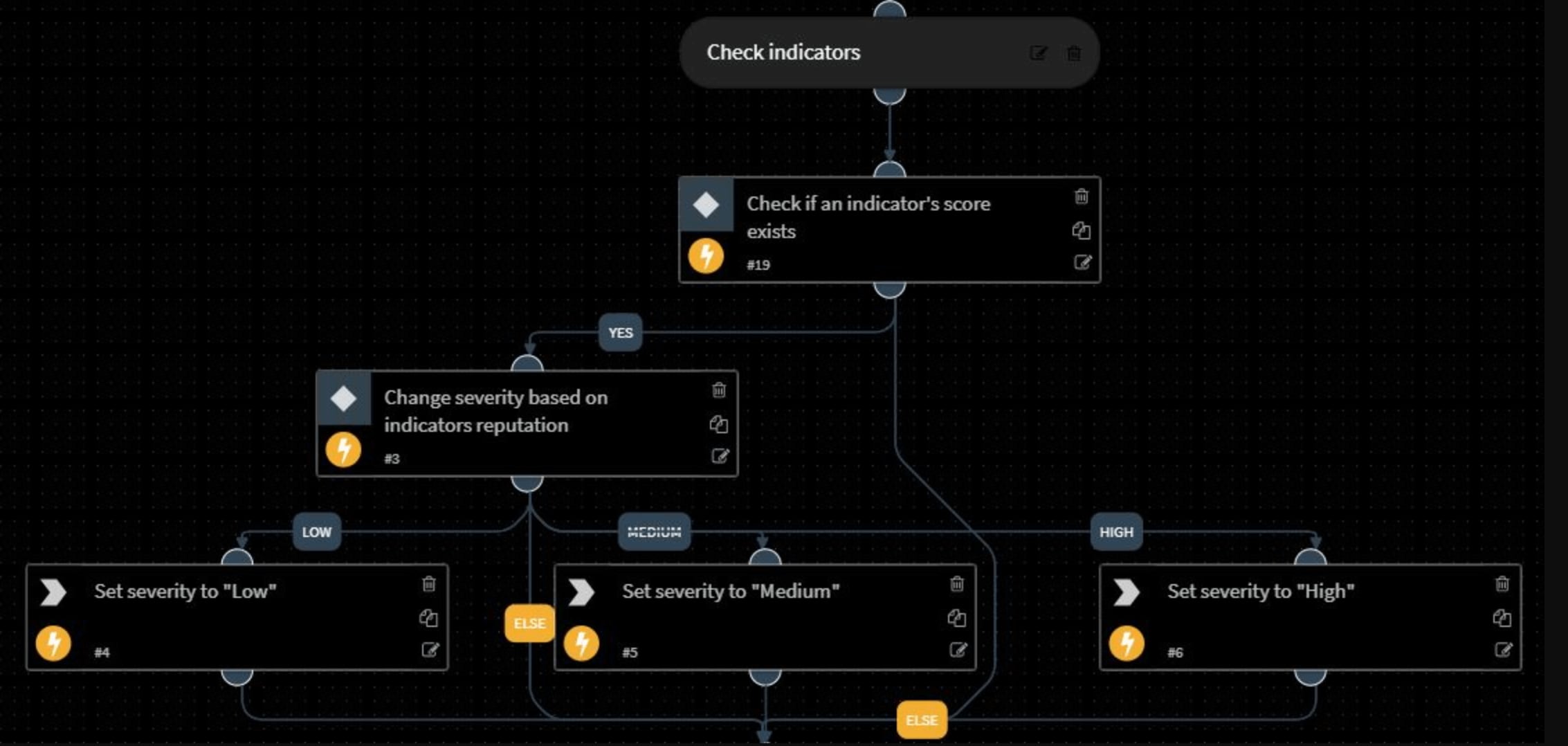
If there’s no third-party severity input, the playbook checks the indicators (IP addresses, URLs, file hashes) of the incident and validates whether there’s a score attached to any indicator. After Cortex XSOAR automatically records all indicators within the platform, each indicator is assigned a ‘Reputation’ based on an amalgamation of scores from other threat intelligence platforms that a user integrates with.
If there’s a score attached to any indicator, the playbook assigns a High, Medium, or Low severity accordingly. If a user integrates with multiple threat intelligence products, the indicator score is an ideal way to action the insights from each product through a combined reputation rating.
Step 3: Check Critical Entities
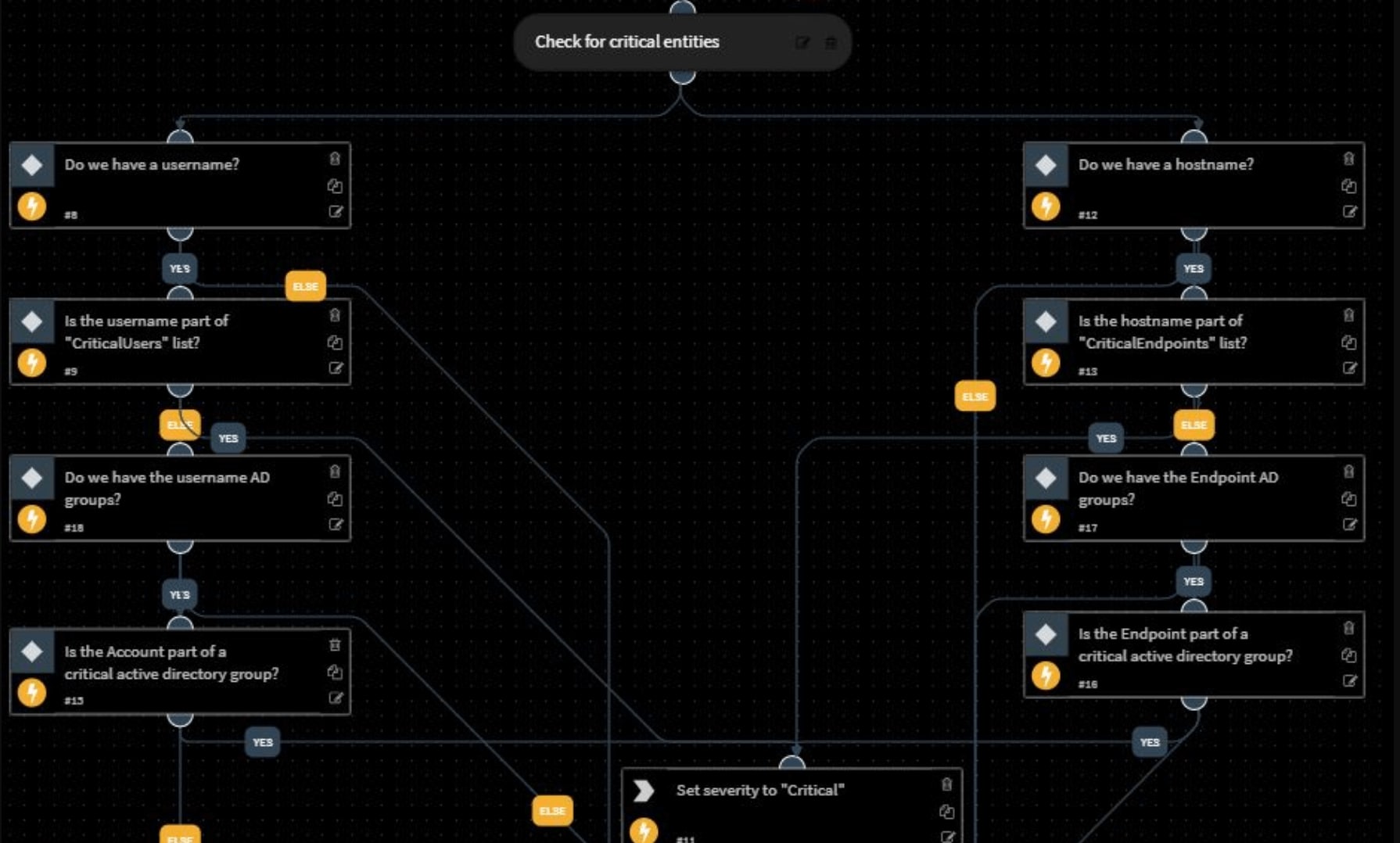
In addition to threat intelligence, this playbook also takes user identity and behavior into account while assigning incident severity. The playbook checks if there’s a username tied to the incident and whether the username is part of any critical user-lists. It performs these same checks with the hostname tied to the incident. If either the username or hostname merit additional agility in response, the incident severity is assigned as ‘Critical’.
The benefits of this incident severity scoring playbook are manifold:
- All these actions are performed automatically, freeing analyst time that can be used for more strategic problem-solving and decision-making.
- The playbook is modular and can be customized to organizational requirements. If you want to remove the third-party severity check and just focus on indicator scores and entity scores, a new playbook is a few clicks away.
- The playbook can handle complex logical flows to ensure that the right severity level is assigned to each incident and analysts eliminate the need to wade through false positives.
- The playbook coordinates actions across a range of products, ensuring a best-of-breed usage without time-sapping swivel-chair investigations.
We hope you found this severity assignment playbook useful. To explore other Cortex XSOAR features, download our Free Community Edition.