A Day In the SOC…
When I worked at a managed security service provider (MSSP) a few years ago, I shadowed an L1 analyst who was in the middle of researching an endpoint detection and response (EDR) alert received from a client’s environment.
Interestingly, rather than being triggered against a signature of “known bad” malware, this alert was tied to an unknown process that was behaving suspiciously. I watched as the analyst attempted to determine what the process was and why the EDR alerted.
He jumped to a few threat intelligence providers and looked up the hash, but had no hits. He then started googling the process name to see if there was anything known about it. Again, no hits. At this point, he was stuck and escalated the alert to L2. At the MSSP, we eventually resolved the issue, but this experience stayed with me:
How can security analysts perform more effective investigations at scale?
Malware: Customer Conversations
To help scale and automate investigations like this, we at Cortex XSOAR built the Malware Investigation and Response pack. We wanted to better understand the challenges customers faced when managing their endpoint alerts, and throughout interviews with customers the following challenges came up consistently:
Challenge 1: Rudimentary Automation for Malware Investigation
Many customers had limited automation deployed regarding malware. They would integrate their EDR with XSOAR to operationally manage incidents with SLAs and dashboards and apply XSOAR Threat Intelligence Management (TIM) for indicator extraction and enrichment. But beyond TIM, there was no automation and analysts were on their own to investigate alerts or manually execute their security operating procedures.
Challenge 2: Investigations Still Largely Manual
Some customers were further along in their automation journey: They had Active Directory integrated to provide context on assets, and analysts could trigger response buttons through the layout. Analysts had access to malware analysis tools, but fetching the file and detonating it was manual.
These more mature customers had made some good automation investments, but we identified many repetitive activities that could still save their organization days per month in human effort.
Introducing the Malware Investigation and Response Pack
The Malware Investigation and Response pack accelerates the investigation process for endpoint malware incidents and alerts by collecting evidence of malicious behaviors, searching telemetry data available through EDRs, and processing malware analysis reports through sandboxes. Incident layouts also include buttons to quickly trigger containment activities.

Automated Investigation
The investigation process is the most time-intensive step when responding to malware alerts. Of course, an analyst must investigate whether a file or process is bad, but what are the detailed questions they should ask and what supporting evidence should they collect?
With this pack, evidence is collected automatically and mapped to the MITRE ATT&CK framework to answer questions such as:
- Is there evidence of persistence (scheduled job, registry entry, startup folder, new service, etc.)?
- Is there evidence of evasion or tampering (service stop, process kill, etc.)?
- Is there evidence of lateral movement (network connections, file share enumeration etc.)?
- Is there evidence of PowerShell or command-line abuse?
- Are the associated files digitally signed?
As an example, new commands were added to the Microsoft Defender for Endpoint (MDE) pack to check for different persistence techniques using Microsoft’s threat hunting query API. For this specific command, a search is performed against the MDE telemetry to determine if the process created a scheduled job.
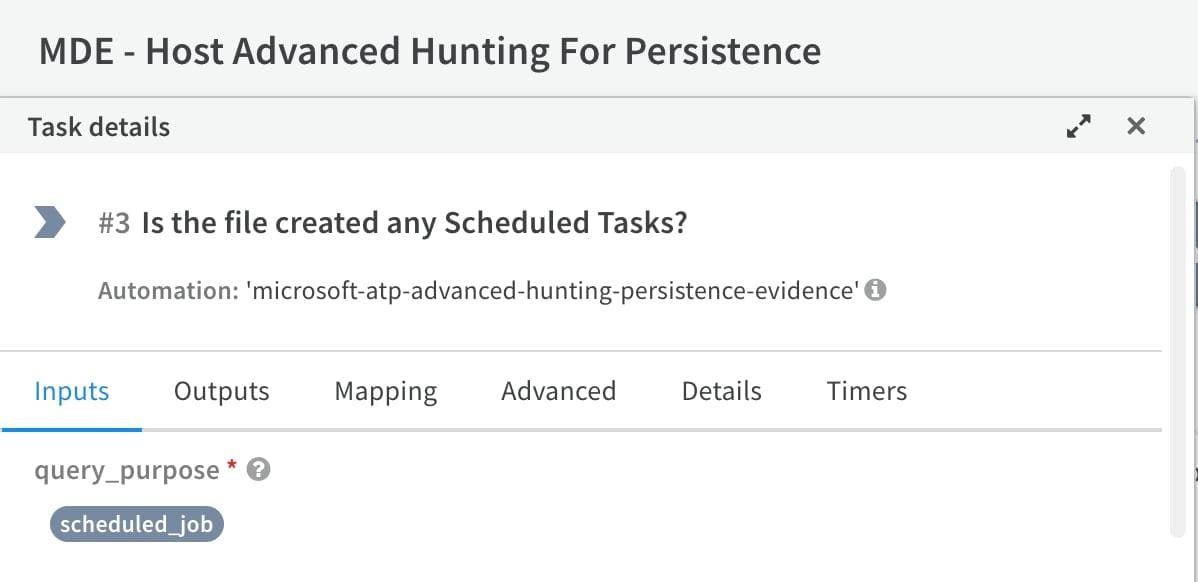
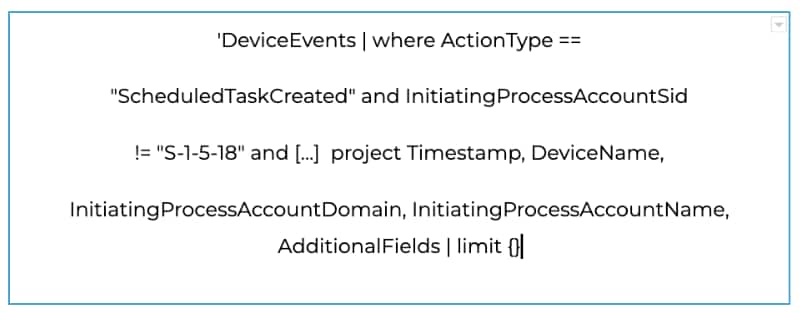
Malware Analysis
If you have a sandbox integrated with Cortex XSOAR for malware analysis, the playbooks included in this pack will automatically retrieve the malware report if it is available. If a report is not available, the suspicious file will be retrieved using EDR and passed to the sandbox for detonation. The pack supports most sandboxes in the market. The report, when available, will be parsed, mapped to MITRE, and displayed in the incident layout.
Investigation Visualization
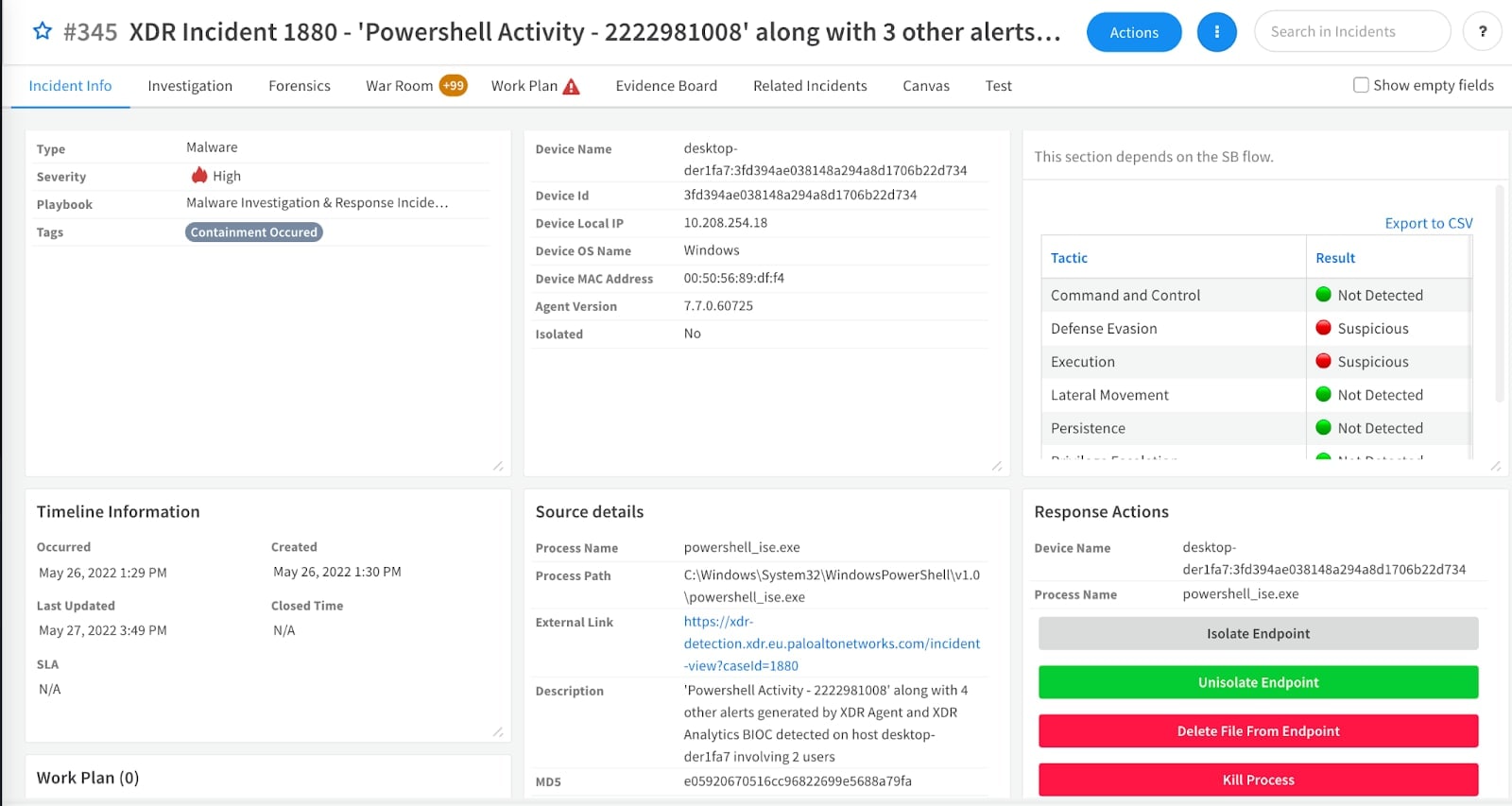
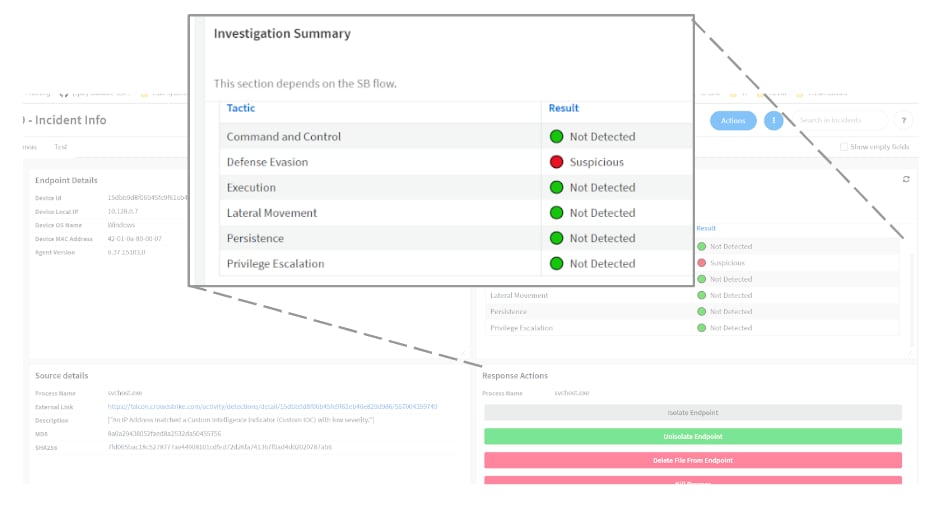
Once the automated investigation is complete, the results of the investigation are shown in the layout for the malware incident type. The investigation data is summarized in the primary incident layout to indicate whether specific tactics were detected.
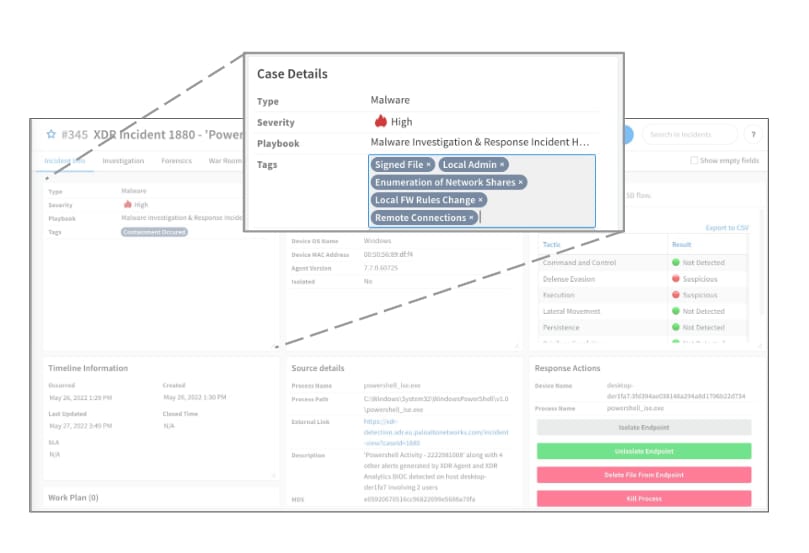
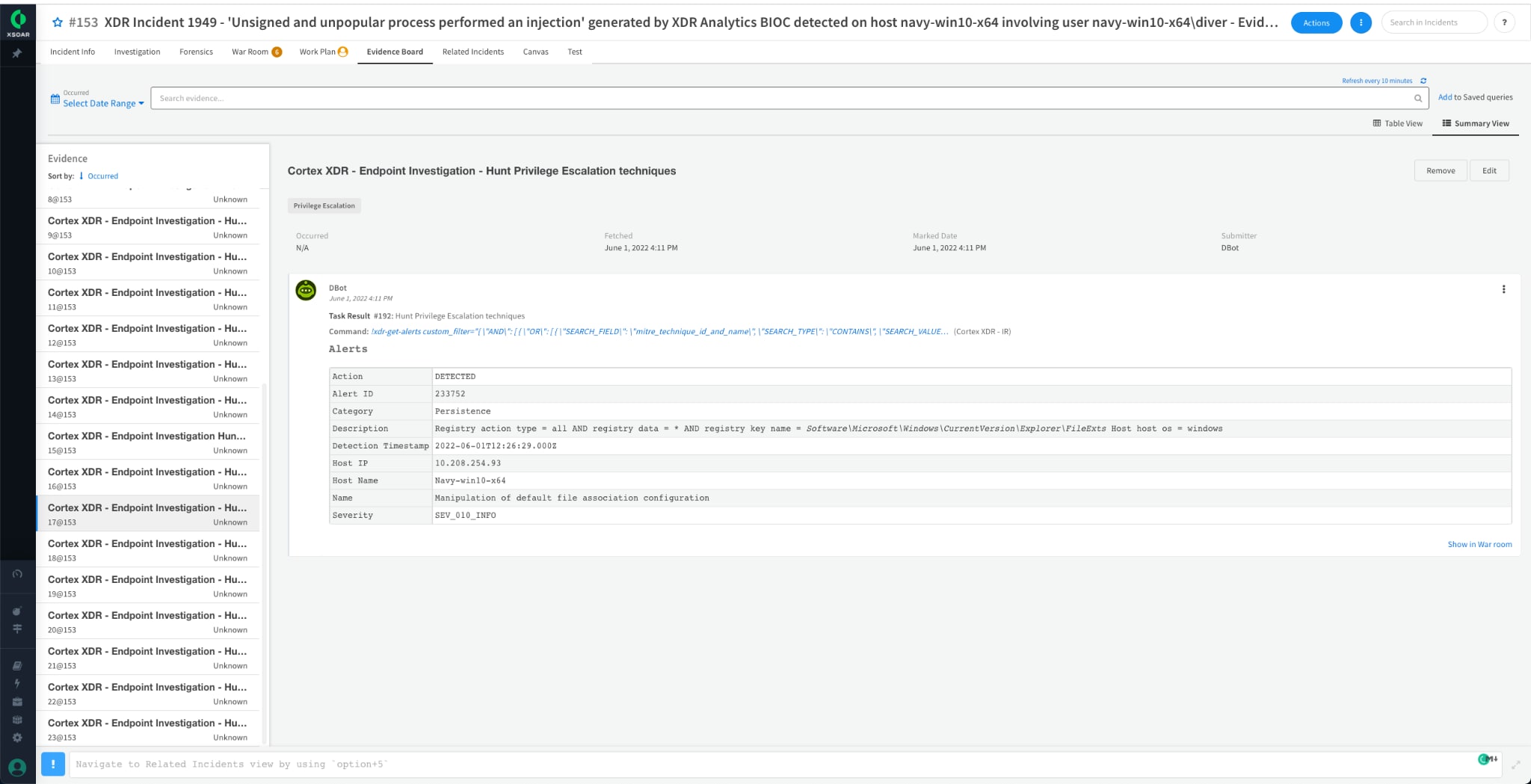
The specific evidence that is accumulated is then displayed on the evidence board. This allows the analyst to have an easy “yes” or “no” answer for specific tactics. They can easily review specific activity of potential malware, such as the exact registry keys that were modified.
Enrichment and Forensics
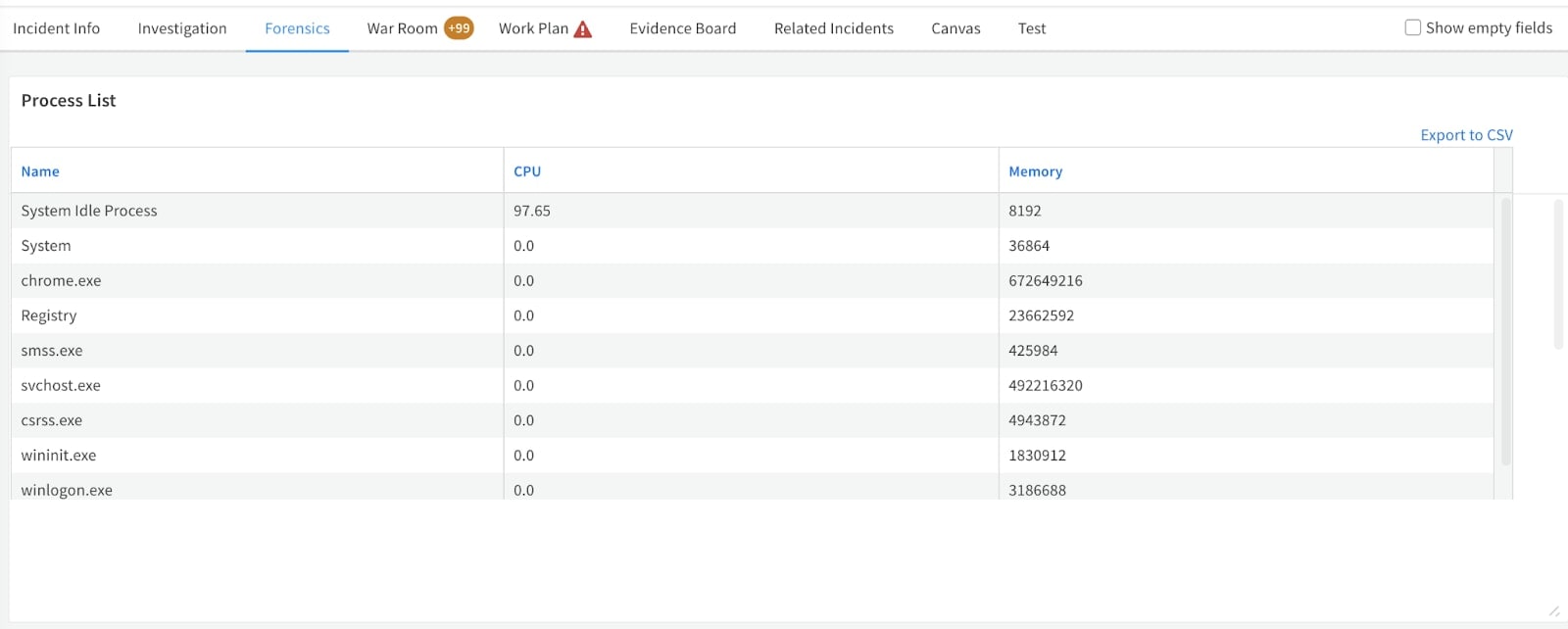
During an investigation, it is critical to understand what is happening on the endpoint at the time the alert is detected rather than at a later point during the investigation. Sometimes, it can be minutes or even hours before an analyst looks at a detected alert, at which point the state of the endpoint is likely different. This can make the investigation challenging.
With the Malware Investigation and Response pack, process and network connection data is fetched at the time the alert is created. Some EDRs also allow fetching a specific investigation package, which includes logs and other rich information.
Response: Containment and Remediation
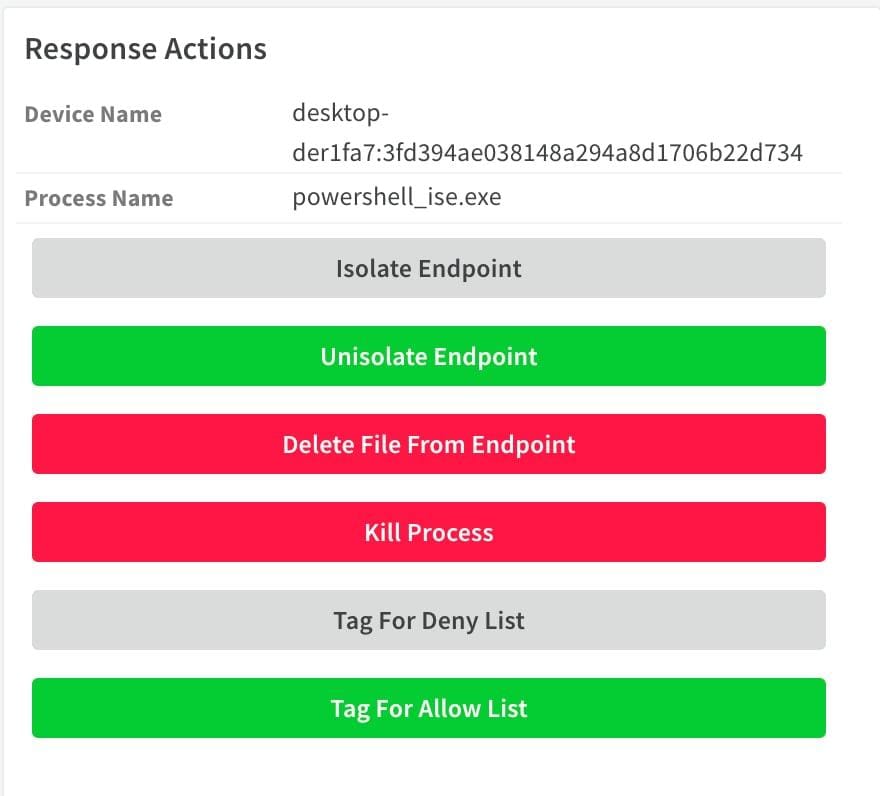
Once the investigation is complete, the analyst will need to take action based on the results of the investigation. If the alert is a true positive, then the analyst will want to take containment precautions to prevent the malware from spreading. The layout for the malware incident type includes buttons to easily trigger endpoint isolation, file deletion, and kill process commands.
The analyst can also apply a tag on the primary indicator. It allows your indicator management workflow to add the indicator to a deny list or allow list. For example, an EDR deny list or a firewall External Dynamic List (EDL) tag can be added to block access across the environment. If the file is benign or a false positive, the analyst can apply the allow list tag to avoid repeated alerting.
For remediation, the playbook has a parameter to open a JIRA ServiceDesk or ServiceNow ticket so that the IT team knows to reimage the compromised endpoint or use the appropriate IT workflow your company has in place.
Onboarding
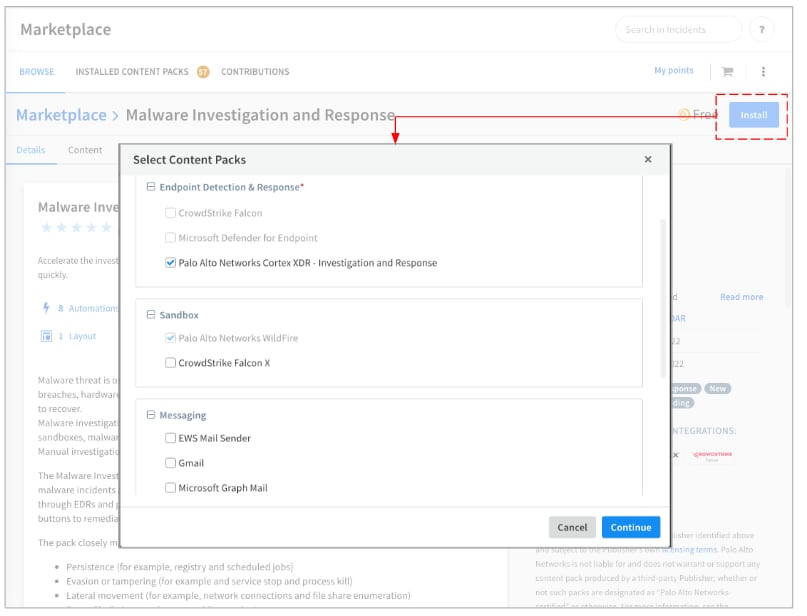
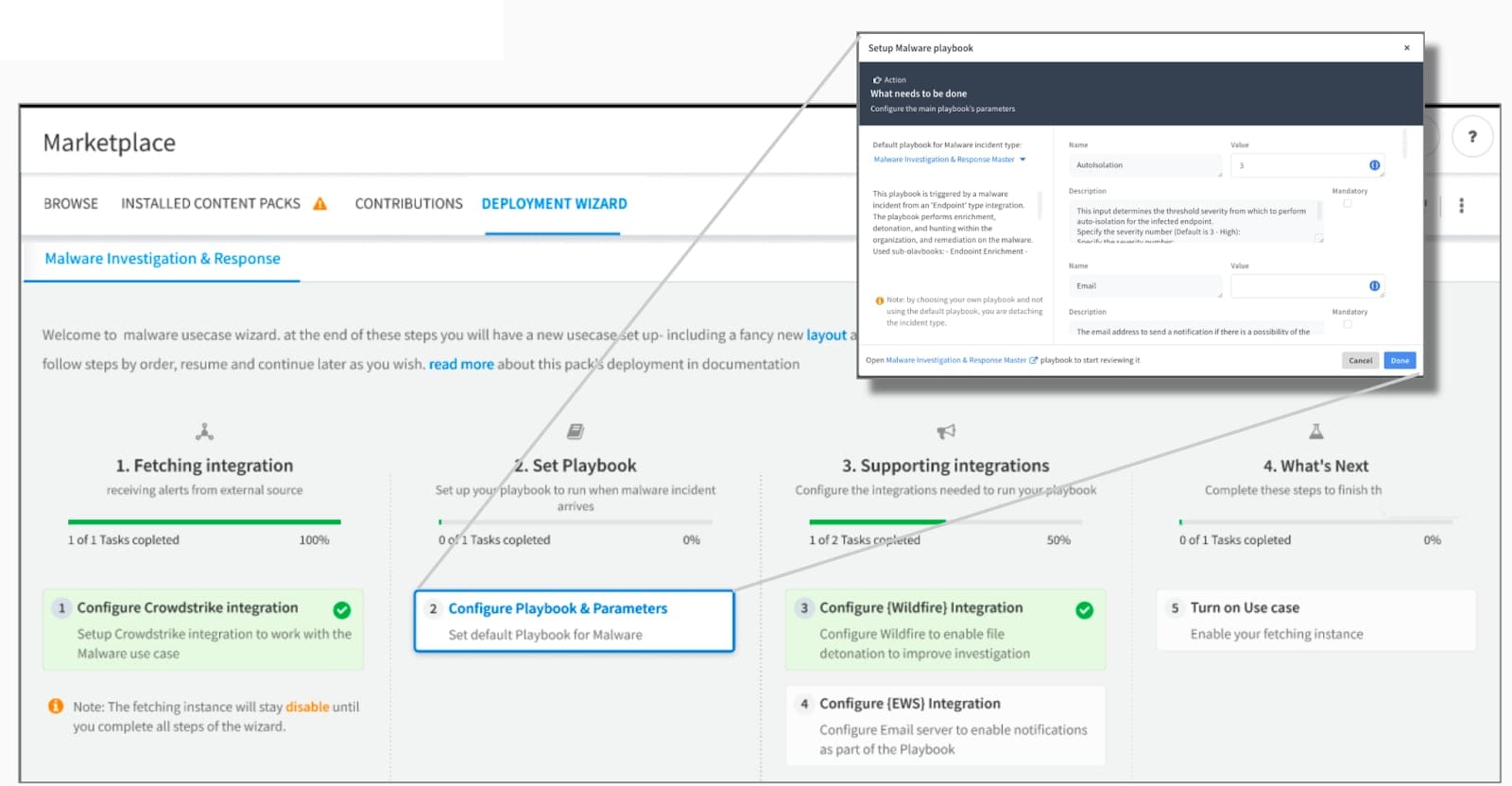
To guide you through the configuration, we introduced the deployment wizard in XSOAR 6.8, which streamlines the installation of the Malware Investigation and Response pack.
If you are on XSOAR 6.8 when the pack is installed, you will receive a prompt to select required dependencies. The deployment wizard will guide you through the setup process for configuring the EDR integration, selecting the primary playbook with parameters, supporting integrations, and ultimately enabling the integration once you’ve completed the configuration steps.
For XSOAR 6.8, the deployment wizard is only available for the Malware Investigation and Response pack, but we plan to support many more packs in the future.
I Like This, Now What?
If you are interested in this pack, and you are an existing customer, simply download it from the XSOAR Marketplace. The pack works with XSOAR v6.5 or higher, although the deployment wizard is only available starting with XSOAR v6.8.
If you are not currently a Cortex XSOAR customer, then download our free Community Edition trial. Join us for the webinar to learn more about this new content pack.
Supported EDR Tools
The Malware Investigation and Response pack integrates deeply with select EDR tools in order to perform queries and gather evidence aligned with MITRE ATT&CK. For this version, the pack supports the following endpoint solutions: Cortex XDR, Microsoft Defender for Endpoints, and Crowdstrike Falcon.
Thinking of the Future, Here Are Some Enhancement Ideas
The Malware Investigation and Response pack accelerates the investigation process for cybersecurity analysts and makes containment activities push-button simple. Although this pack provides a ton of value for our customers, we are already thinking about what’s next.
Here are some of the things we are thinking about:
- Active Directory Enrichment and Response
Incorporating the capability to retrieve information about the active user on the endpoint will give the analyst context about the endpoint and possible risks to the organization. For example, insight into the active user’s department—are they in finance or engineering? We also want to enable the analyst to reset the end user’s password as needed.
- Enrich with Vulnerability Information
Having the ability to integrate with leading vulnerability management tools such as Qualys, Tenable, and Rapid7 will let the analyst access open vulnerabilities against the endpoint. This will inform the analyst if there is active malware that might try to exploit vulnerabilities on the endpoint.
- Send to IT
Add a new response button so the analyst can trigger the case creation for IT. In the current version, this is done through playbook parameters, but it would be convenient if analysts could trigger this on-demand.
- More EDRs
Expand support to other leading EDR tools such as SentinelOne, Cyberreason, Carbon Black, and others.
Please Suggest Other Ideas or Vote!
If you like these ideas or would like to suggest other ideas, please collaborate with us through the Cortex XSOAR Aha page:
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.