The role of a security analyst has evolved significantly over the years, as the nature of cybersecurity threats have become increasingly sophisticated and complex. Today's security analysts are responsible for a wide range of tasks, including monitoring and analyzing network traffic, identifying potential security breaches, and developing strategies to mitigate cyberthreats.
With the new Joe Security sandbox security integration, analysts can easily submit URLs or automatically detonate files that are detected by the deployed EDR. The retrieved information allows the analyst to gain more insights on the alert from studying the full sandbox report or even doing a quick view of the extracted indicators of compromise (IOCs).
How Does Joe's Security Sandbox Work?
The Joe Security sandbox integration is utilized in the Malware Investigation and Response content pack as part of EDR alert investigation and response. The wizard aids security teams in configuring several integrations that together create full coverage for the Malware Investigation use case.
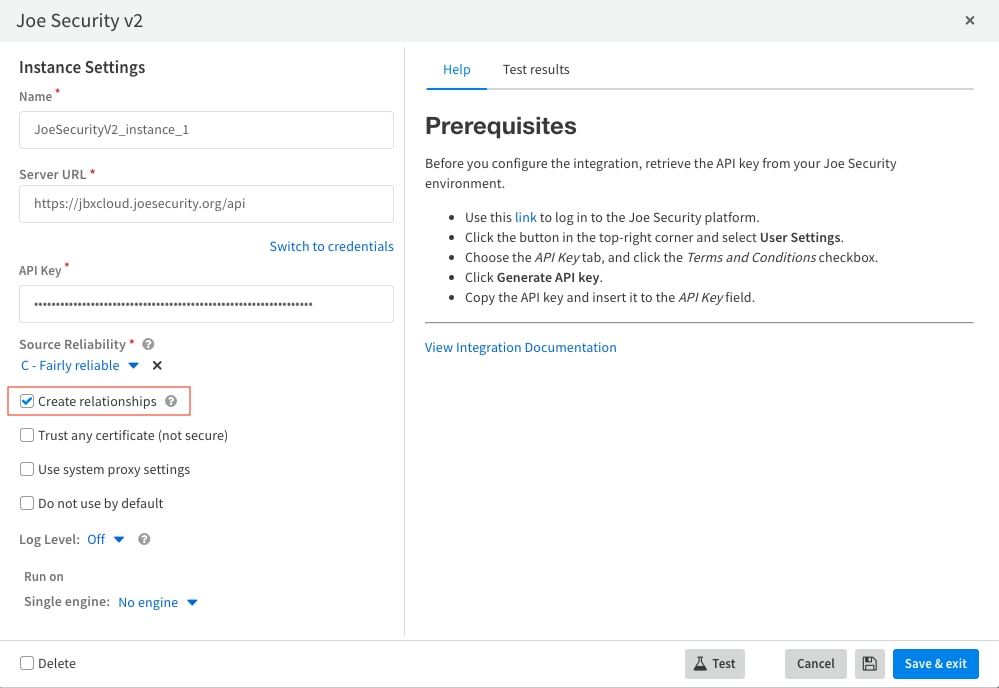
Configuring Joe Security Sandbox integration in XSOAR is a straightforward process that can be completed in just a few steps, all one needs are the server URL and API key. Also, there is an option to create relationships between IOCs enabling analysts to quickly identify patterns and connections between seemingly disparate security incidents. Don't forget to mark the “Create relationship” parameter to let XSOAR create the relationships between different indicators empowering the analyst's investigating techniques.
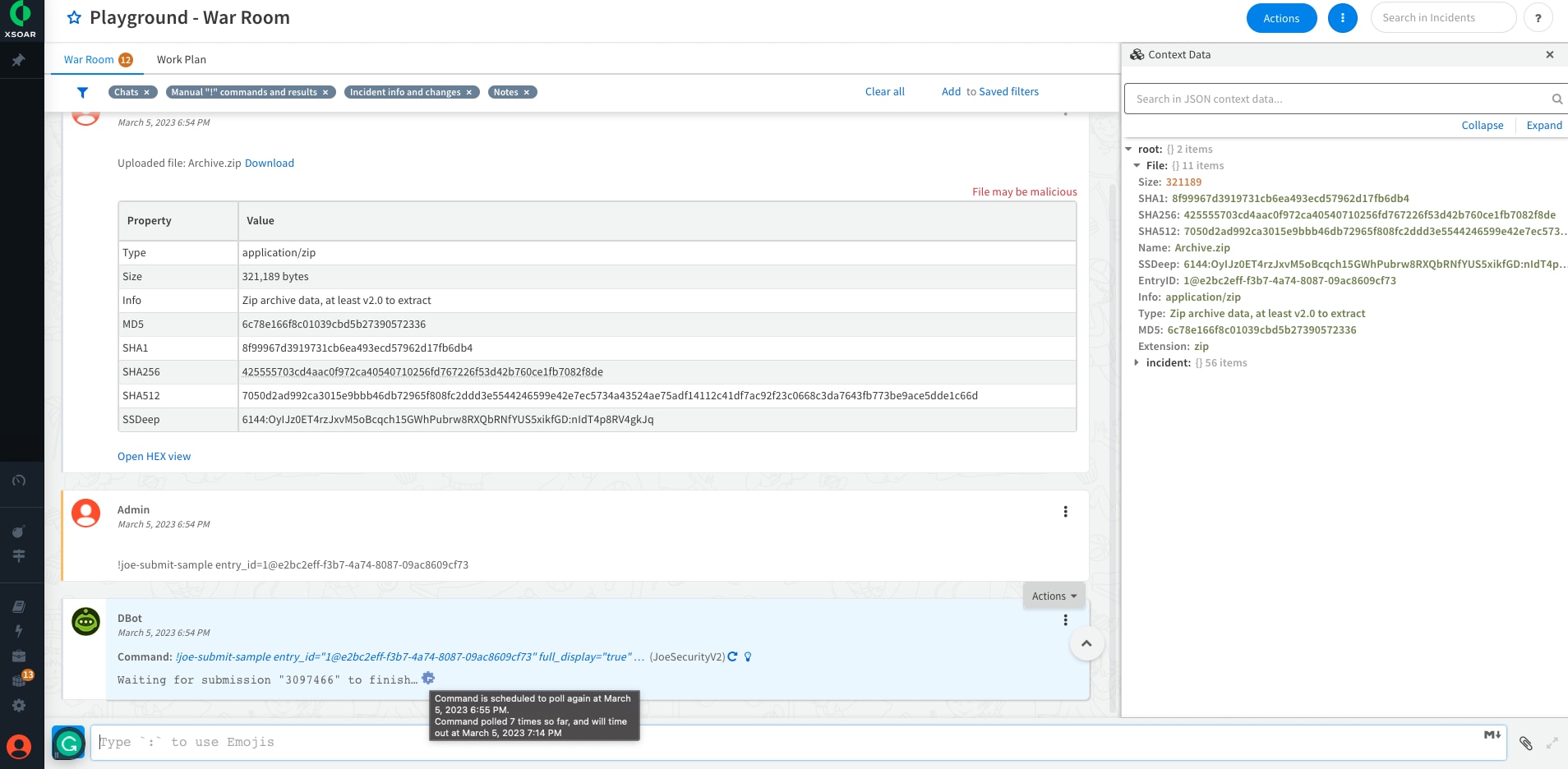
Users can submit potentially malicious URLs, single file or files (zip) for analysis and receive detailed reports on their behavior and potential threats. The integration new submission process is informative and easy to use, reducing the time and effort required to detect and respond to potential threats.
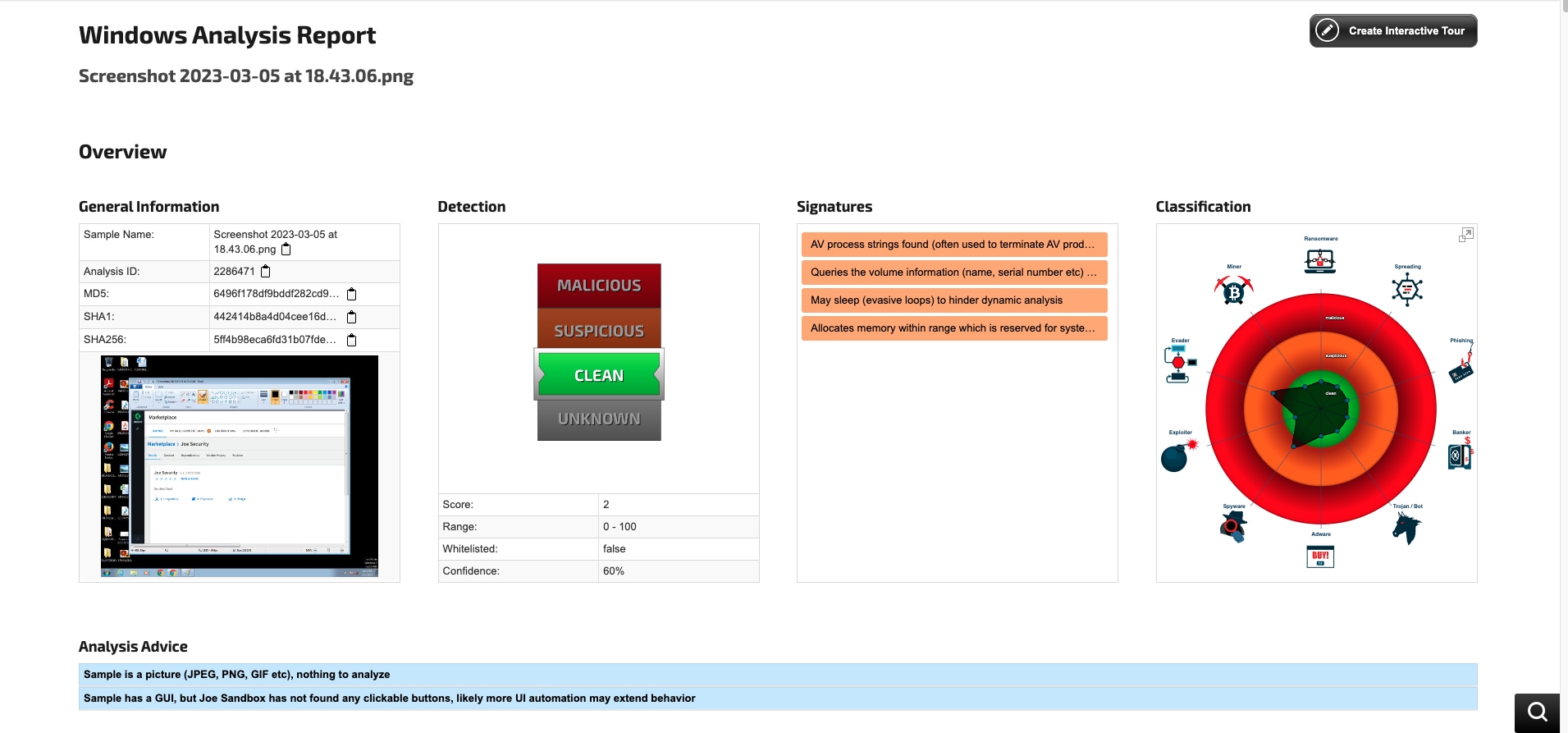
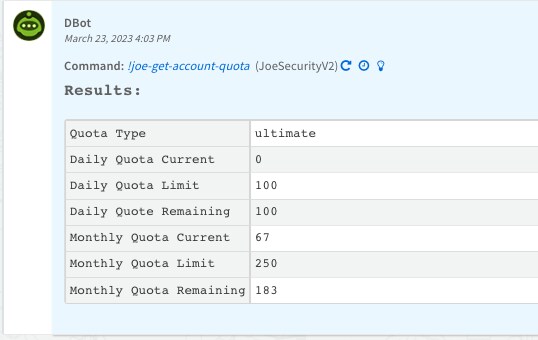
In addition, a new command called "joe-get-account-quota" has been introduced to retrieve the account API quota. The integration incorporates the API Metrics Board, which gives users a robust tool for monitoring and analyzing their API usage. This tool allows for more efficient resource management and identification of any possible issues. The board provides a range of widgets that allow users to keep an eye on important performance indicators like API requests, response times, and error rates.
Learn More
The Malware Investigation and Response pack accelerates the investigation process for cybersecurity analysts and makes containment activities push-button simple.
For more information on the Malware Investigation and Response Pack and other XSOAR packs and playbooks, visit our Cortex XSOAR Developer Docs reference page.
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.