When responding to a security incident, triage, analysis, enrichment and remediation all can be time consuming and error prone processes, especially when responding and managing these attacks requires security teams to reconcile data from multiple sources. Often, by doing so, valuable time is lost shuttling between screens and executing repeatable tasks while an attack continues to manifest.
Today we’ll look at how SOC teams are able to utilize the best of both XDR’s extended endpoint threat detection and response with XSOAR’s workflow automation, orchestration and threat intelligence capabilities to become more effective using the Palo Alto Networks Cortex XDR — Investigation and Response content pack.
Automating XDR incident response
Cortex XDR is a detection and response platform that natively integrates network, endpoint, and cloud data to stop sophisticated attacks. By standardizing the XDR incident response and automating response with the Cortex XDR — Investigation and Response content pack, Cortex XSOAR decreases the mean time to detect by automating the collection of enrichment data, and providing centralized tracking. The pack includes out-of-the-box Cortex XDR incident type views with incident fields and layouts to aid analyst investigations, which are all easily customizable to suit the needs of each unique organization.
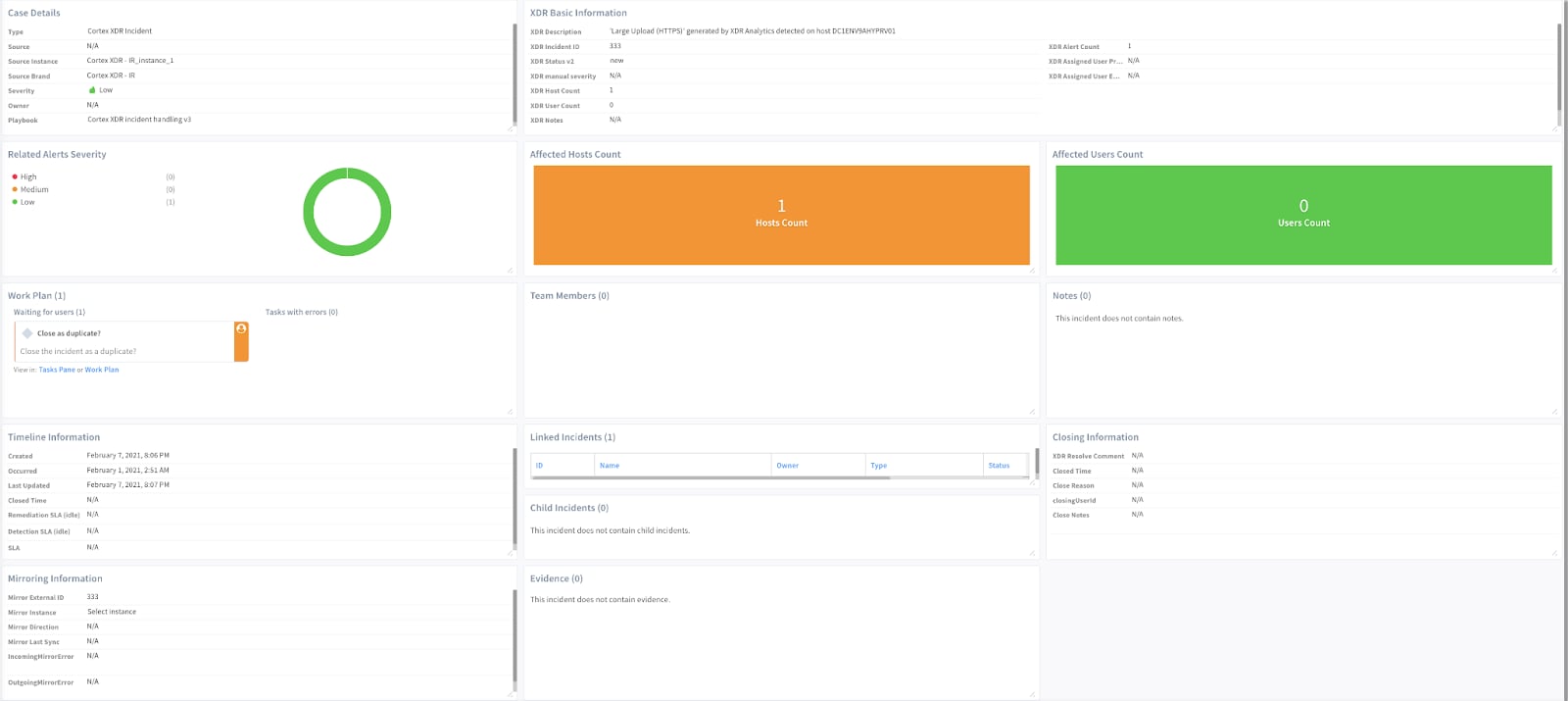
Image 1: Default Cortex XDR layout provided by the content pack
What does the Cortex XDR - Investigation and Response Content Pack do?
This content pack contains the Palo Alto Networks Cortex XDR Investigation and Response integration that enables direct execution of Cortex XDR actions within Cortex XSOAR. It also performs bidirectional incident updates between Cortex XDR and Cortex XSOAR. Plus, it enables the following workflows:
- Device Control Violations — Fetch device control violations and enrich data from XDR incidents and communicate with the user to determine the reason the device was connected.
- XDR Incident Handling — Compare similar incidents in Palo Alto Networks Cortex XDR and Cortex XSOAR, identify duplicate incidents, and update the incidents appropriately using the Cortex XDR Incident Handling v3 playbook (as seen in image 2 below).
- Threat Hunting And Detection — Extract IOCs from the investigation and run them across the organization to check if there are any other compromised accounts or endpoints with the same information that was detected in this alert.
- AWS User Access Investigation — Investigates and responds to Cortex XDR Cloud alerts where an AWS user's access key is used suspiciously to access the cloud environment.
- Enhanced Threat Detection with IOC Synchronization — Operationalize threat intelligence feeds and ensure the detection and response controls are leveraging the threat Intel feeds to push IOCs to XDR to enable better threat detection.
For more details on all the different playbooks options available within the XDR and XSOAR content pack, check out the blog “XDR + XSOAR: A Dynamic Duo”.
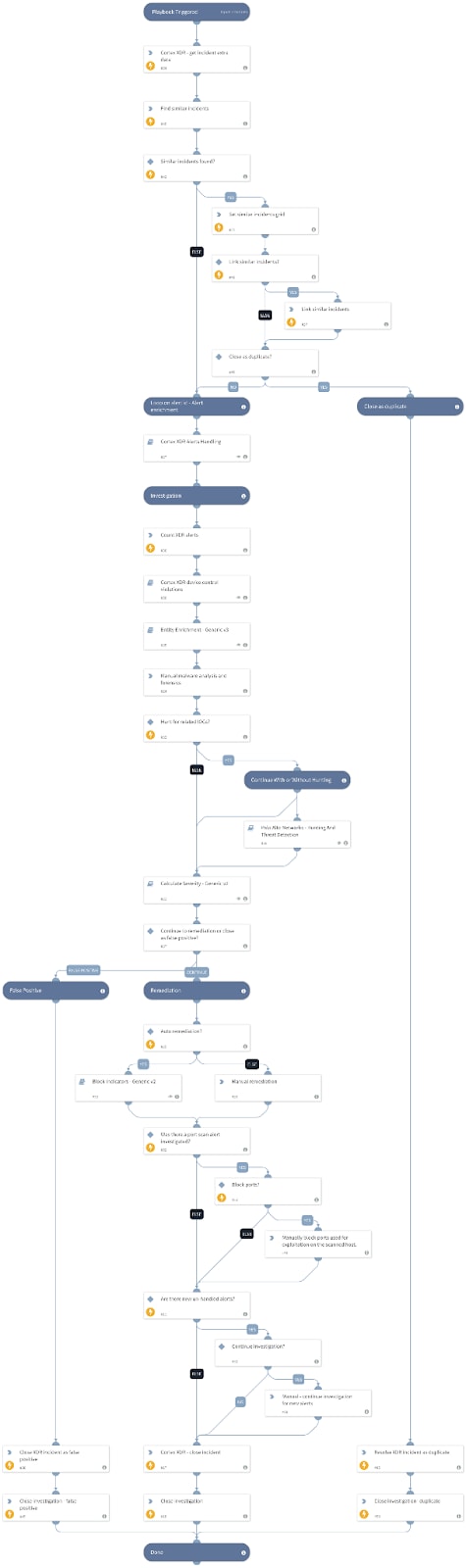
Image 2: Cortex XDR Incident Handling v3 playbook
The playbooks included in this pack help you save time and keep your incidents in sync. They also help automate repetitive tasks associated with Cortex XDR incidents, such as:
- Syncs and updates Cortex XDR incidents.
- Triggers a sub-playbook to handle each alert by type.
- Extracts and enriches all relevant indicators from the source alert.
- Hunts for related IOCs.
- Calculates the severity of the incident.
- Interacts with the analyst to choose a remediation path or close the incident as a false positive based on the gathered information and incident severity.
- Remediates the incident by blocking malicious indicators and isolating infected endpoints.
It is without a doubt that the Cortex portfolio of products is designed to make the life of a security analyst better, faster and more efficient when it comes to detecting and responding to today’s security threats. The beautiful thing about the Cortex family of products is the ability to use each platform in conjunction with one another for maximum results.
Watch the video below for a detailed overview of the XDR and XSOAR Integration. For more information on the Cortex XDR Content Pack, visit our Cortex XSOAR Developer Docs.
Automating XDR Incident Handling
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.
Please Suggest Other Ideas or Vote!
If you like these ideas or would like to suggest other ideas, please collaborate with us through the Cortex XSOAR Aha page: https://xsoar.ideas.aha.io/ideas.