The rapidly changing cyberthreat landscape is a significant challenge for many organizations. With new threats constantly emerging, it can be difficult for organizations to keep up and effectively protect themselves and their assets. This is especially true given the complexity and scale of many modern threats.
Indicator and artifact analysis is essential in cybersecurity investigations (e.g., URLs, files, etc.). Analyzing URLs and files helps determine whether they contain malware or other malicious content. This is important in the early stages of an investigation, as identifying and containing threats as quickly as possible can help to minimize damage.
In addition to identifying threats, URL and file analysis can help security professionals understand how threats are being delivered and how they operate. For example, security professionals can determine how the URL is being used to deliver malware or other threats. Similarly, by analyzing the content of a malicious file, security professionals can determine how the file is being used to compromise systems or steal sensitive data. URL and file analysis can also be used to track the source of threats, which can be helpful in tracking down and creating attributions.
Many organizations use VirusTotal online services to analyze and identify artifacts. The service leverages an extensive database of known malware and advanced analysis tools. VirusTotal inspects its roughly 3.6B samples with over 70 antivirus scanners, URL/domain blocklisting services, and a myriad of tools to extract signals from the studied content.
Unlocking the True Power of VirusTotal with Cortex XSOAR
Cortex XSOAR integrates with VirusTotal to automatically analyze suspicious hashes, URLs, domains, and IP addresses, enhancing threat detection and response capabilities. This enables you to check for an immediate verdict, detonate artifacts, and get extended context from VirusTotal without manual effort.
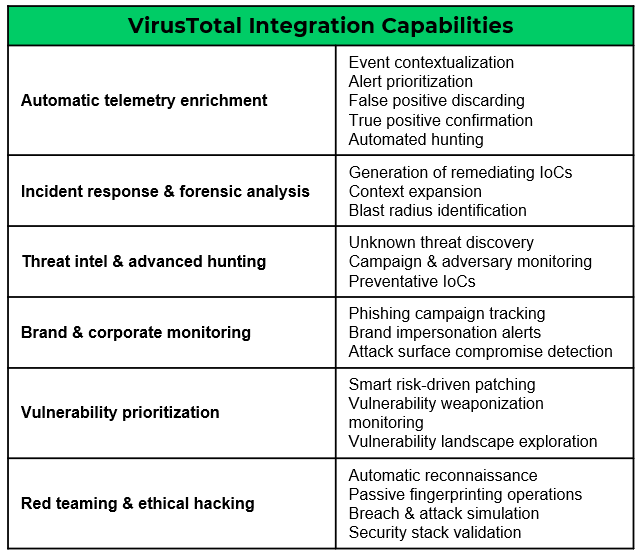
See It In Action
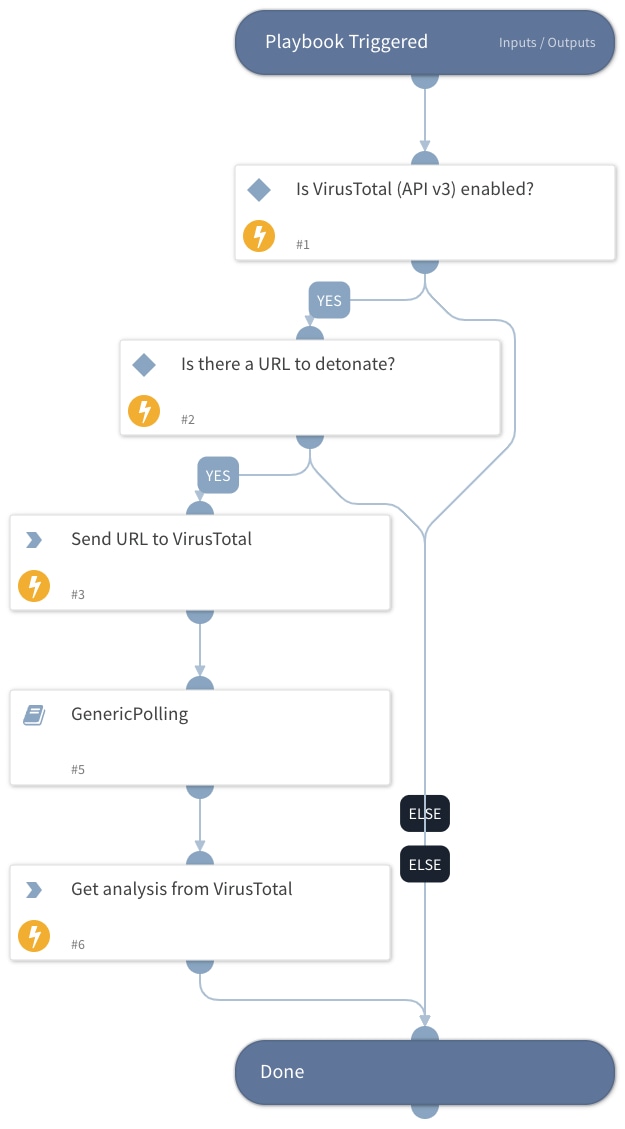
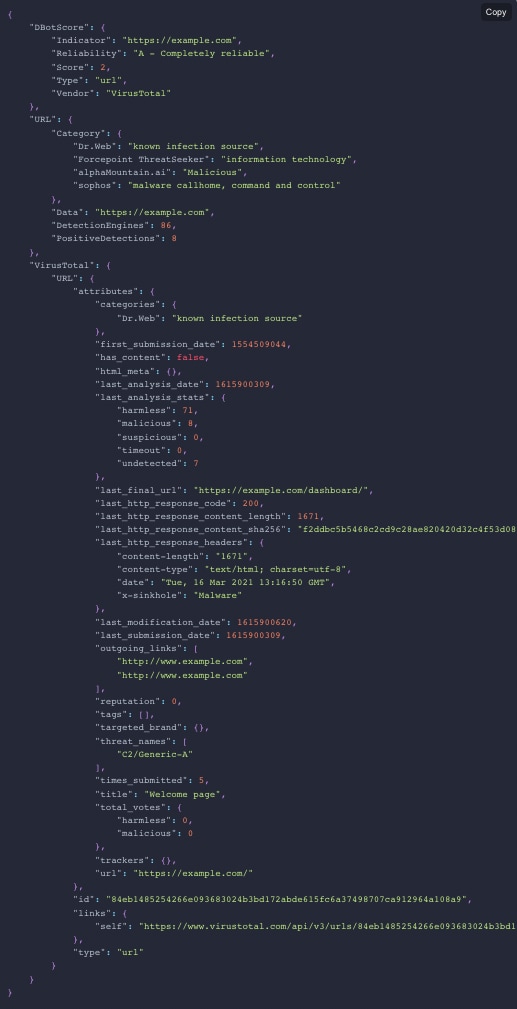
When using VirusTotal to run the URL detonation playbook, the response provided is very detailed, helping to address many actions that manual work may overlook or ignore if deemed irrelevant.
The Full Value of VirusTotal and XSOAR
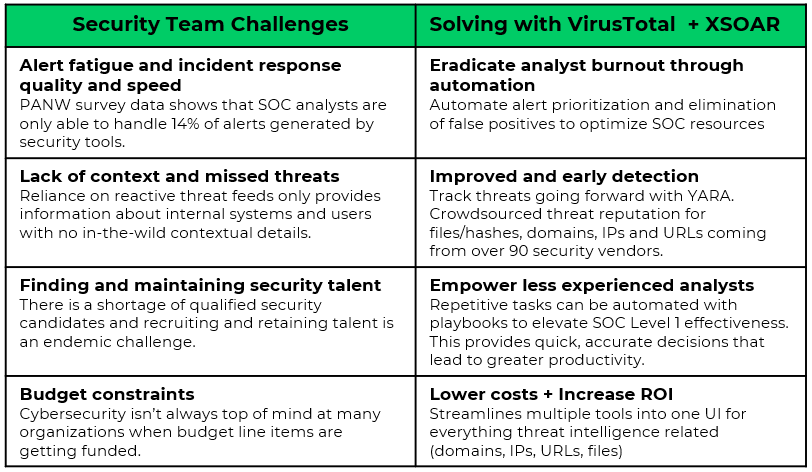
The VirusTotal integration includes an extensive list of supported commands that can be executed from Cortex XSOAR as part of an automation or in a playbook:
- ip - Checks the reputation of an IP address.
- url - Checks the reputation of a URL.
- domain - Checks the reputation of a domain.
- url-scan - Scans a specified URL. Use the vt-analysis-get command to get the scan results.
- vt-comments-add - Adds comments to files and URLs.
- vt-file-scan-upload-url - Premium API. Get a special URL for files larger than 32 MB.
- vt-comments-delete - Delete a comment.
- vt-comments-get - Retrieves comments for a given resource.
- vt-comments-get-by-id - Retrieves a comment by comment ID.
- vt-search - Search for an indicator in VirusTotal.
- vt-file-sandbox-report - Retrieves a behavioral relationship of the given file hash.
- vt-passive-dns-data - Returns passive DNS records by indicator.
- vt-analysis-get - Retrieves resolutions of the given IP.
- vt-file-sigma-analysis - Retrieves the result of the last Sigma analysis.
Conclusion
VirusTotal is a valuable tool that provides extensive malware analysis capabilities and helps organizations significantly improve their ability to identify and respond to threats. Using the integration with Cortex XSOAR helps reduce the time it takes to verify a threat, collect data for analysis, and act upon it. For more information on the VirusTotal content pack, refer to the pack documentation.
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.