A Deluge of Data
Like many of us in the world of cybersecurity, your SecOps team has likely been overwhelmed by the volume of alerts flooding your SIEM systems. We've all been there—sifting through endless alerts, trying to figure out which ones actually matter. This deluge not only tires you out but could make you miss real threats among the false alarms.
The kicker? A lot of these alerts are false positives—alerts that look scary but turn out to be benign activity—and they can quickly drain your resources and obscure your visibility. Addressing these false positives effectively is crucial to staying on top of genuine threats and keeping your security posture strong.
For organizations who leverage Splunk as their SIEM solution, integrating Cortex XSOAR® with Splunk isn't just an operational upgrade—it's a game changer for your daily workflow. By pairing XSOAR with Splunk, we create a powerful duo that turns the tide on false positives. XSOAR’s industry-leading automation, paired with Splunk’s deep data insights, paves the way for a more accurate and efficient workflow.
Alerts went from 10,000 per week to roughly 500—a staggering 95% reduction stemming largely from swift resolution of false positives and duplicate incidents, thanks to automated playbooks and historical cross-correlation.
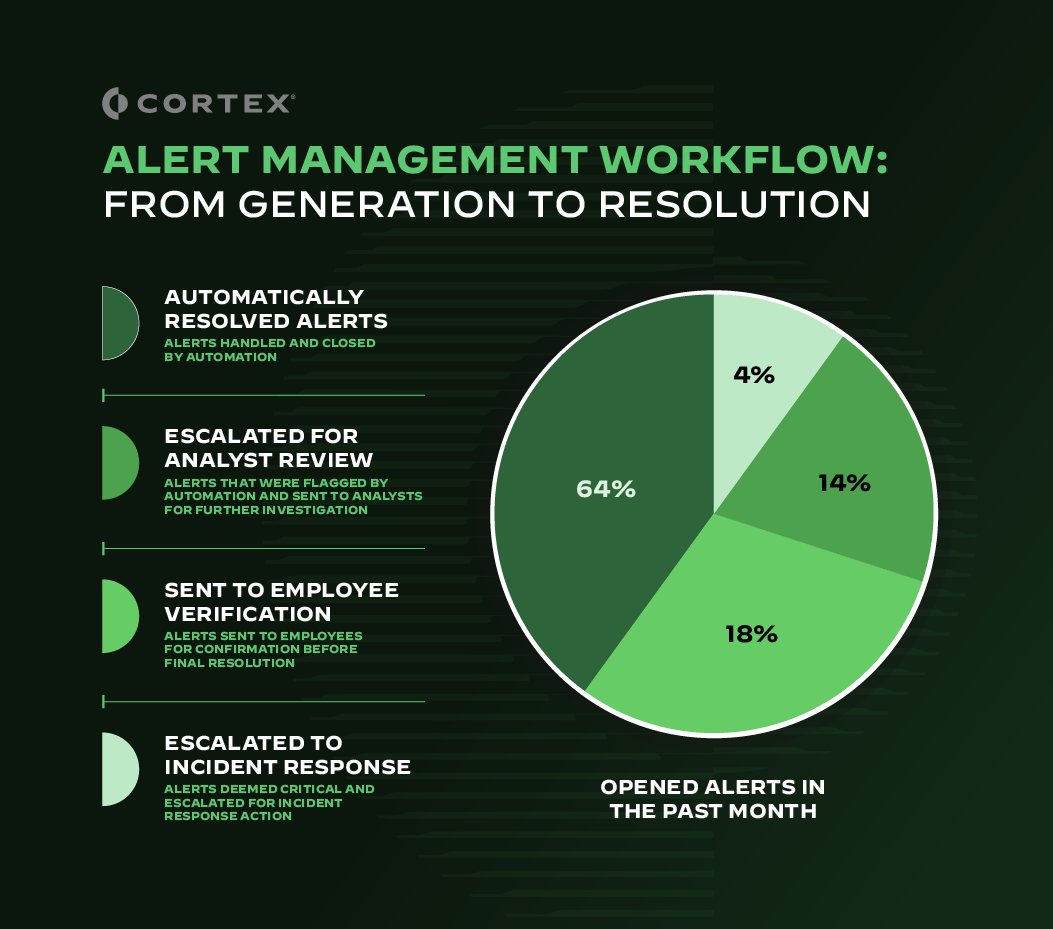
Let's dive into how this integration can cut through the noise, simplify your alert triage process, and bring measurable value to your organization.
Crafting Automated Workflows with Splunk and XSOAR
Let’s look at a common use case—excessive failed login attempts—and how XSOAR synergizes with Splunk to analyze potential threats.
Defining Alerts
Start by defining what events should trigger an alert in Splunk. In the case of excessive failed login attempts, an alert could mean several things:
- A threat actor could be attempting to brute force user credentials.
- An authorized user may have forgotten their password (false positive).
- An automated process may be configured with incorrect credentials.
Determining the root cause of the alert may require an analyst, but we can collect a lot of data now about the event and automate decision making to isolate high-risk situations.
Fetch and Enrich with XSOAR
Once Splunk raises the flag, the alert engages XSOAR, where a tailored playbook—your strategic plan for investigation—determines the risk level of the alert.
Playbooks are at the heart of the Cortex XSOAR system. They enable you to automate many of your security processes including, but not limited to, handling your investigations and managing your alerts.
Your playbook will further enrich the alert by asking additional questions about the dataset and looking for contextual clues about the event. Enrichments include:
- IP Origin/Reputation
- User Context (account activity, permission level, etc.)
- Device Security Status
For our use case, we’ve used four out-of-the-box (OOTB) playbooks and merged them to a single master playbook, which allows us to rapidly assemble a solution to a common problem. These are the OOTB playbooks we chose:
- IP Enrichment - Generic
- Account Enrichment - Generic
- Active Directory - Get User Manager Details
- Access Investigation - Generic
These playbooks will query external threat intelligence databases to assess the reputation of the IP involved. They’ll also retrieve user and endpoint data and examine them for details like the user’s last successful login attempt or whether the endpoint has a security agent installed.
We check for the latter using EDR, SIEM, and other tool integrations to ensure we get a comprehensive view of user and endpoint activity, providing a detailed picture of potential risks and the overall security posture.
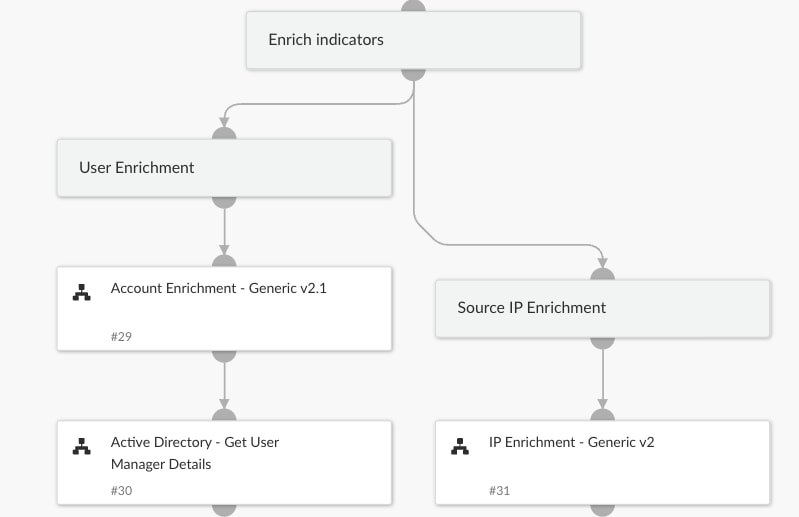
Automating Informed Decisions
The goal of our playbook is to measure the risk associated with the event. For this use case, we want to filter as many false positives as we can, so our analysts aren’t distracted by red herrings. We quantify the acceptable risk level of an event through an exoneration score.
The exoneration score is at the heart of our playbook and plays a pivotal role in distinguishing the real threats from false positives. This can be tailored to accommodate your risk appetite, enabling you to mold these OOTB solutions for your specific needs. For our use case, we wanted to know the following information about the event:
- Last successful login attempt? Attackers often target old but still active user accounts to pivot undetected. Long periods of inactivity could indicate malicious activity.
- Any other relevant events? Perhaps there are other alerts that may have been generated relevant to the same user, system, or IP address.
- Is this a service account? Some accounts exist only to execute processes. When passwords change but processes aren’t updated, these systems repeatedly attempt to connect until they lock themselves out of the network.
- Can the user provide confirmation? Playbooks can contact the implicated user through alternate channels to verify the attempt, such as via email or multifactor authentication (MFA).
Based on the enriched data, user feedback, and conditional checks, we can apply a playbook customized to our risk appetite to generate the exoneration score, which will either categorize the alert as a false positive or escalate it to an analyst for further review.
If the alert is determined to be a false positive and closed in XSOAR, this status is mirrored back to Splunk, automatically closing the corresponding alert in Splunk as well. This ensures consistency across both platforms and reduces the need for maintenance.

The Clear Value of Automation
Most organizations have the same goal related to cybersecurity: minimize risk at the lowest possible cost.
XSOAR doesn’t just automate decision-making, it provides a clearer picture of the organization’s attack surface. XSOAR provides efficiency, accuracy, and optimization by separating the deluge of benign data from real indicators of attack.
XSOAR also easily integrates with many different systems and provides unrivaled out-of-the-box workflows for automating alerts. XSOAR can leverage communication apps like Slack or Microsoft Teams to generate real-time communication with employees and admins, and it can integrate with Active Directory and MFA solutions for advanced analytics and faster response actions.
Beyond these integrations, XSOAR offers tons of pre-written playbooks and other content types that streamline various security processes. These resources are designed for immediate deployment and can be effortlessly customized to meet the specific needs of any organization.
Take Automation for a Test Drive
Ready to filter out false positives and start hunting for legitimate threats? Check out our Splunk integration guide or contact our team for a demo of the awesome synergy between XSOAR and your SIEM solution.
And if you are ready to move beyond automation, many organizations address these challenges by adopting Cortex XSIAM®, an autonomous SOC platform that unifies XDR, SOAR, ASM, and SIEM capabilities in one solution. XSIAM streamlines alert management by aggregating numerous alerts into actionable incidents, while using playbooks to automate and accelerate the remediation process.
Click here to learn more about Cortex’s automation capabilities.