With the recent news around the SolarWinds backdoor supply chain compromise, you are probably rushing to discover and understand which hosts on your network have SolarWinds installed, if they have been compromised by the SolarStorm SUNBURST malware and if there are other signs of malicious activity associated with this infection.
We can help.
Leverage the power of automation with Cortex XSOAR to help you speed discovery and remediation of compromised hosts within your network. Our Cortex XSOAR playbook helps you automatically:
- Collect indicators to aid in your threat hunting process
- Retrieve IOCs of SUNBURST (a trojanized version of the SolarWinds Orion plugin)
- Retrieve C2 domains and URLs associated with SolarStorm
- Discover IOCs of associated activity related to the infection
- Generate an indicator list to block indicators with SUNBURST tags
- Hunt for the SUNBURST backdoor
- Query firewall logs to detect network activity
- Search endpoint logs for Sunburst hashes to detect presence on hosts, vulnerable SolarWinds servers, and risky C2 traffic flows
- Search XDR incidents for suspicious SolarStorm behavior
- If compromised hosts are found then:
- Notify security team to review and trigger remediation response actions
- Fire off sub-playbooks to quarantine and/or block any vulnerable SolarWinds server IPs, and await further actions from the security team
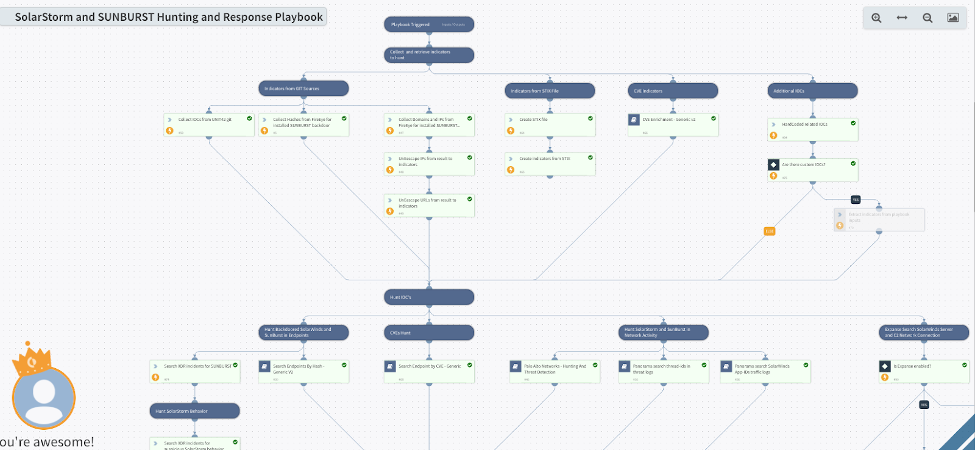
With the help of Cortex XSOAR playbook, your security team can save many hours of manual labor chasing down compromised hosts and trying to piece disparate sources of information together from multiple tools. Cortex XSOAR can automate the whole process of data enrichment and threat hunting by orchestrating across firewalls, endpoint security and threat intelligence sources so you can quickly shut down Sunburst and limit its impact on your network.
You can find the Rapid Breach Response content pack in our Cortex XSOAR Marketplace. Don’t have Cortex XSOAR yet? Try the free community edition today.