With digitization becoming a mainstream phenomenon, cyber hacking is fast evolving to resemble more like yesteryears organized crime. If there is a type of attack that has become more prevalent and hugely successful and profitable business for hackers, it has to be ransomware. Ransomware attacks can unfold in a classic Hollywood crime thriller movie style. There is a villain, a malicious perpetrator, a victim, suspense, use of threat and last but not the least, a hefty ransom that needs to be paid before it's too late! Emotions run high on all sides. The victim is left at the mercy of the perpetrator and is looking to the incident responder to come to the rescue.
To help incident responders combat this threat, Cortex XSOAR has just the toolkit to help incident responders be more effective in dealing with these nefarious actors.
Cortex XSOAR’s Ransomware content pack can immediately help incident response, threat intelligence, and SecOps teams to standardize and speed-up post-intrusion response processes. This content pack automates most of the ransomware response steps, allowing the incident response and SecOps teams to add their guidance and input. This pack can help incident responders better understand their position and exposure against threat actors by collecting the required information from your environment, executing the investigation steps, containing the incident, and visualizing the data with its custom post-intrusion ransomware layout.
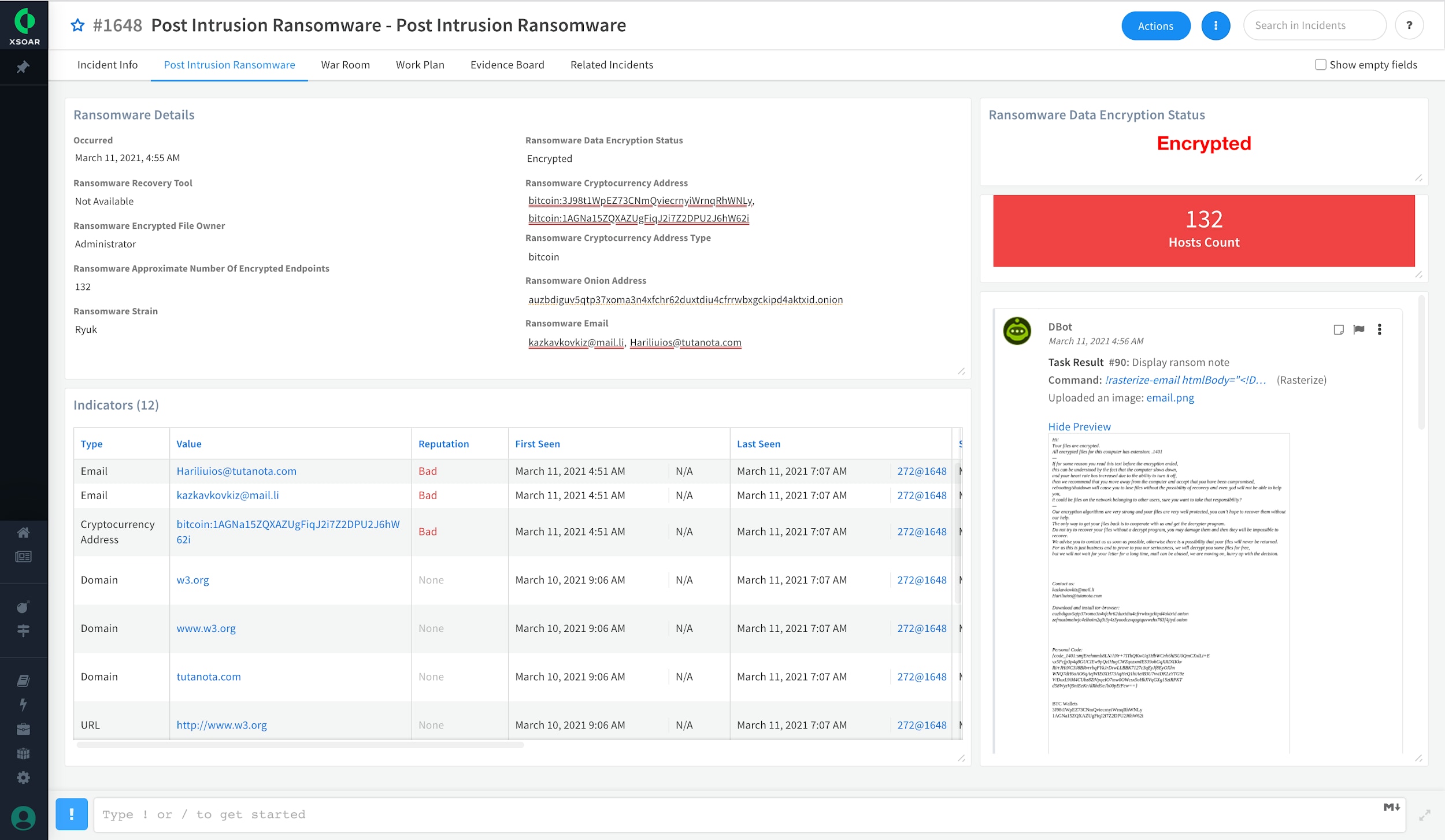
Ransomware dashboard that is a part of the content pack
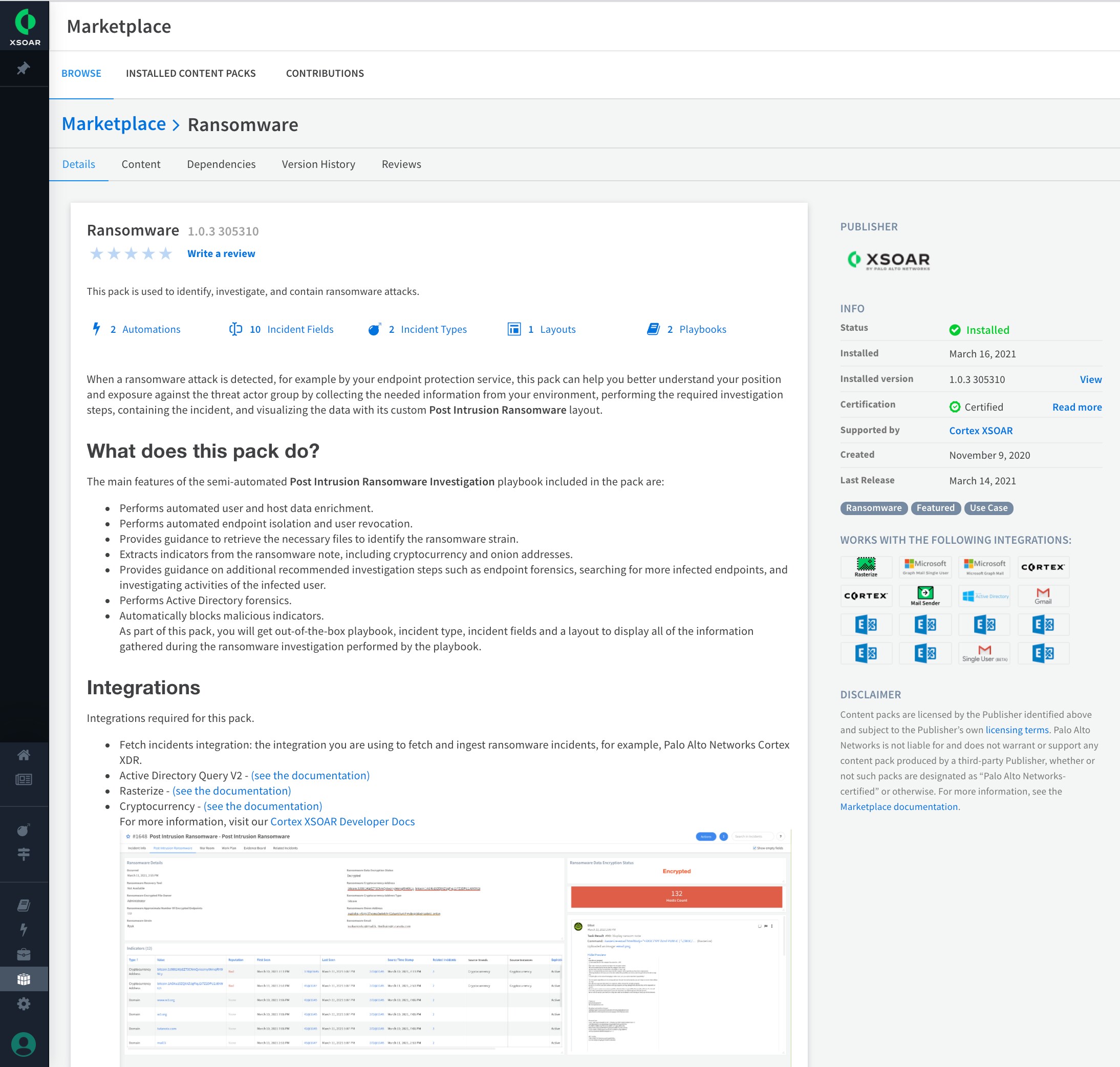
The Ransomware content pack is available for download from the Cortex XSOAR Marketplace
How does the Ransomware content pack work ?
When a ransomware attack is detected by one of several alert sources such as Cortex XDR, this pack automatically triggers the post-intrusion ransomware investigation and response playbook to identify, investigate, and contain the ransomware attack. The Ransomware content pack requires the ransom note and an example of an encrypted file to identify the ransomware variant and find the most appropriate recovery tool via the online database. All the relevant stakeholders are automatically notified of the attack. The playbook includes a manual task for determining the incident timeline that is essential part of the recovery process. Since the data encryption is the final step in the attack, prior attacker actions are investigated.
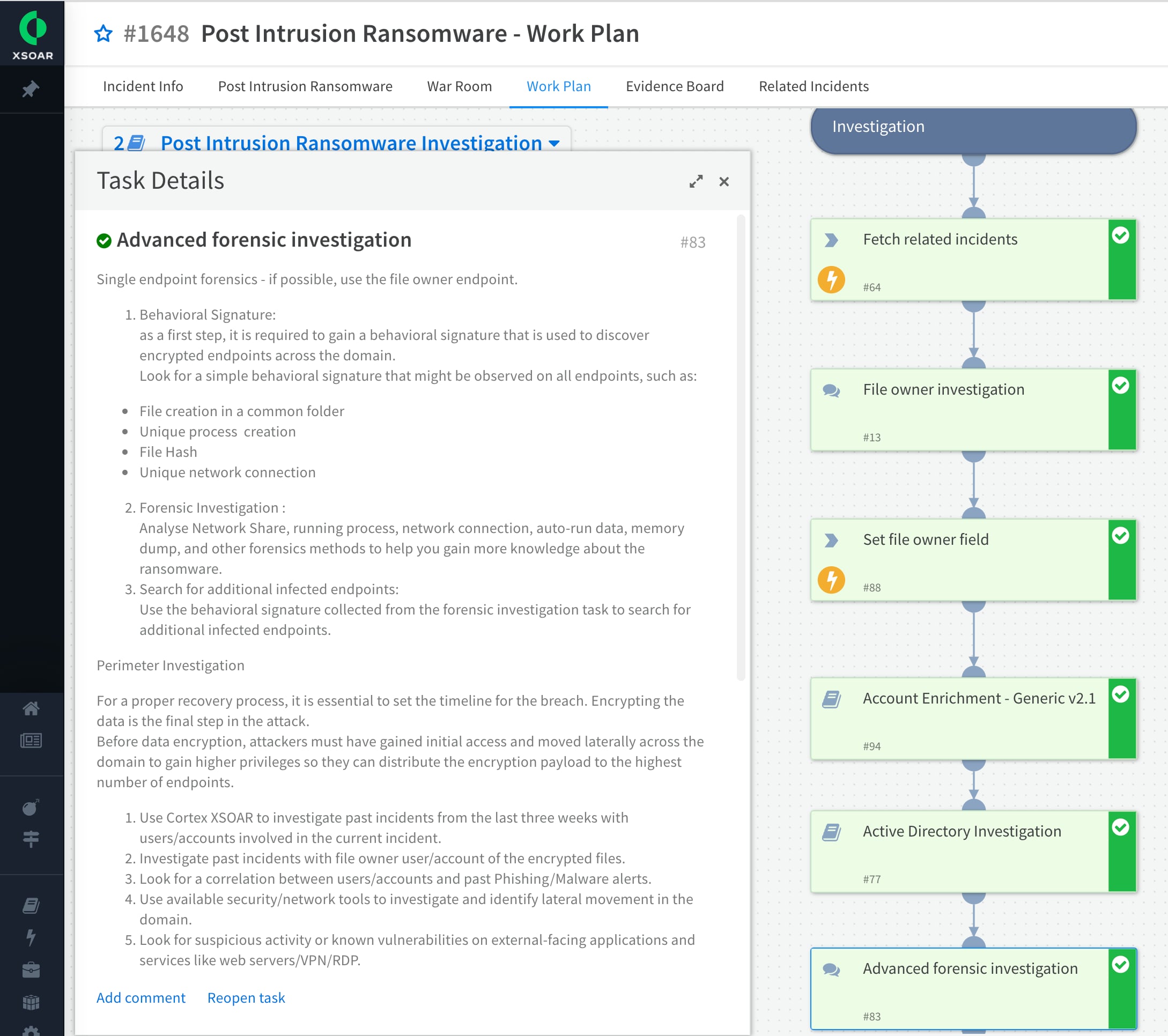
Expanded view of the advanced forensics investigation task of the playbook
The playbook includes options to further investigate the activity of the user whose files were encrypted, and identify additional endpoints that experienced the attack. If auto-remediation is approved, the malicious indicators from the ransom note are automatically blocked. Alternatively, the containment can be done manually as well.
To learn more about the associated integrations, playbooks, scripts, commands, and automations please refer to the playbook documentation section.
Conclusion
With the help of the Ransomware content pack and Cortex XSOAR core capabilities and integrations, incident response, SecOps, and threat intel teams can save many hours of manual labor trying to piece disparate sources of information together from multiple tools. Cortex XSOAR can automate the whole process of user investigation, endpoint isolation, notifications, enrichment, and threat hunting by orchestrating across SIEM, firewalls, endpoint security, and threat intelligence sources so that response teams can quickly shut down the ransomware, minimize the risk of losing data, limit the financial impact of ransom demands and its impact on the enterprise.
Don’t have Cortex XSOAR yet? Try the free Community Edition today.