Recently, MITRE Engenuity published the third round of the MITRE ATT&CK evaluations, which explored the tactics, techniques and procedures (TTPs) leveraged by the Carbanak and FIN7 threat groups. As you may have read, Cortex XDR achieved the best overall combined protection and detection in the evaluation.
Results of Cortex XDR Protecting Against Carbanak and FIN7
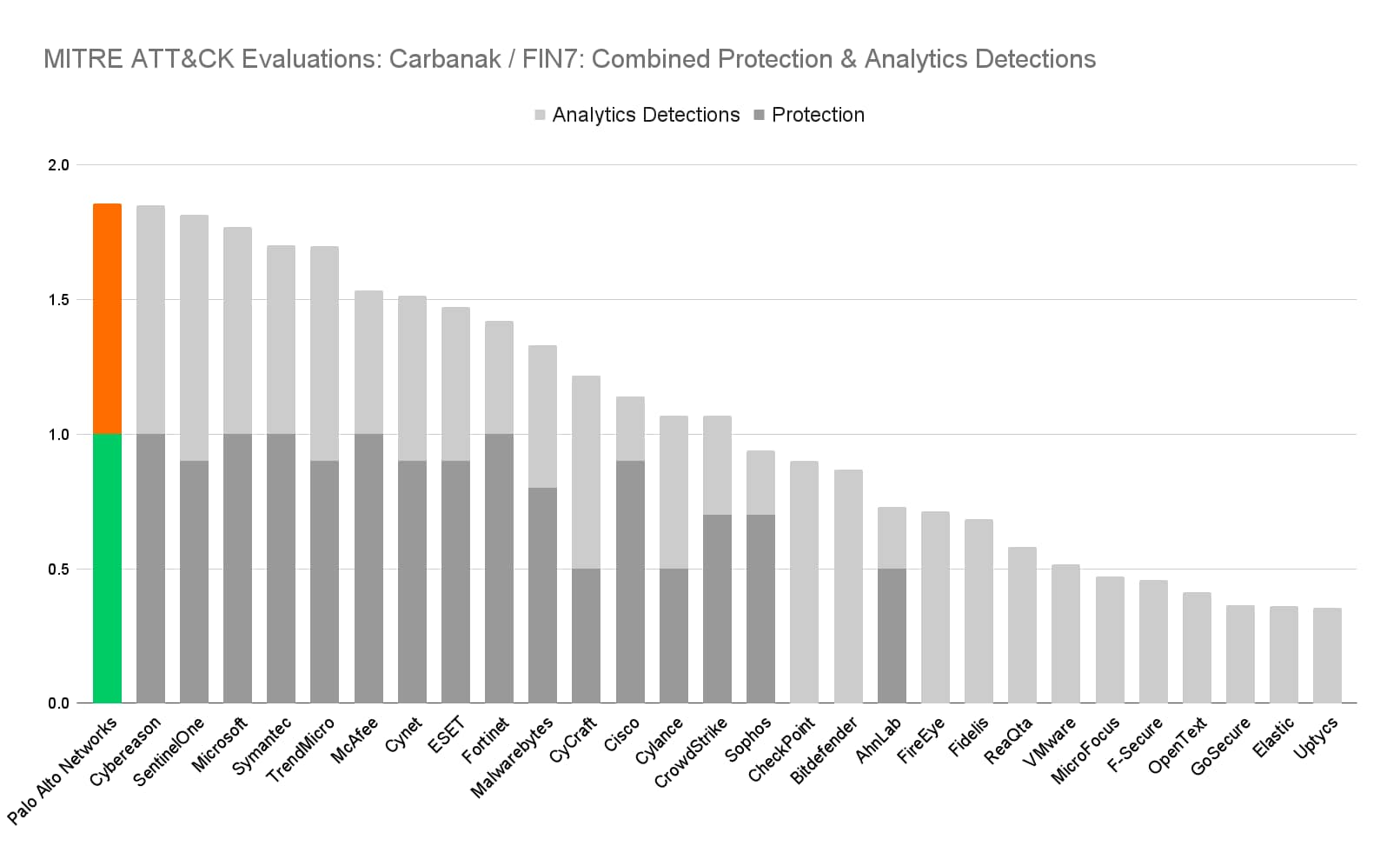
Figure 1. Cortex XDR had the highest combined protection and detection results in the evaluation.
*Note: Data and charts based on MITRE results minus detections with a “Configuration Change” modifier.
Studies like MITRE are valuable in shedding light into the deeper elements that make the difference in how successful we as Analysts are at effectively and rapidly addressing attacks.
Correlation, Curation and Completeness– How to Maximize the Outcome of Your Investigations
As Analysts it is imperative that we:
- Quickly recognize the nature of the attack
- Quickly and accurately identify the impact and scope of the attack
- Quickly and fully eliminate and remediate the threat
The quality of the data and corresponding detections we have pertaining to the attack is critical in achieving these goals.
MITRE Round 3: Carbanak + FIN7
MITRE round 3 presented an attack scenario based around the Carbanak (MITRE G0008) and FIN7 (MITRE G0046) APT groups, which primarily target US-based banking, retail, restaurant, and hospitality sectors. Initially active since at least 2015, these groups have traditionally utilized various point-of-sale (POS) oriented malware and the Carbanak attack toolkit. This evaluation focused on separate attack scenarios emulating Carbanak and FIN7 threat actors.There were a total of 174 attack substeps combined in these scenarios, each evaluated based on the quality of the detection.
Detection categories are evaluated as follows:
- None: The product did not collect any data relative to the expected attack step
- Telemetry: The product collected data relative to the attack step, but did not raise a distinct alert
- General: The product collected data and raised an alert, but was unable to provide specific contextual detail with regard to the tactic or Technique employed.
- Tactic: The Product raised an alert and provided context for what the attacker was doing, but was not able to contextualize how they were doing it
- Technique: The Product raised an alert, while providing contextual information regarding what the attacker was doing and how they were doing it.
The Importance of Correlated Data
While MITRE evaluates the attack sequences individually, the relationships between sequences, broader context, and characterization of the attack was beyond the scope of MITRE’s focus for this round.
In the real world, the value of your data is amplified as that data is correlated and given broader context, and this can improve the quality of our response. When we consider as an example attack sequence 5.B.1 – remote spawning of an attack process on a Linux host from a Windows host – we can see these concepts illustrated clearly.
In attack sequence 5.B.1, the attacker, having already gained control of the HRMANAGER Windows host, now seeks to extend their footprint and control a Linux host that contains resources of value. The attacker has already identified this host from earlier reconnaissance activities, has staged a payload for movement to the Linux host, and is now ready to act. The sequence that unfolds consists of the following steps:
- On HRMANAGER, the attacker has successfully spawned a command shell (cmd.exe)
- From that command shell, the attack module plink.exe is spawned
- Plink.exe initiates a remote ssh connection to the target Linux host and attempts (successfully) to authenticate into the target using credentials that were harvested earlier in the attack
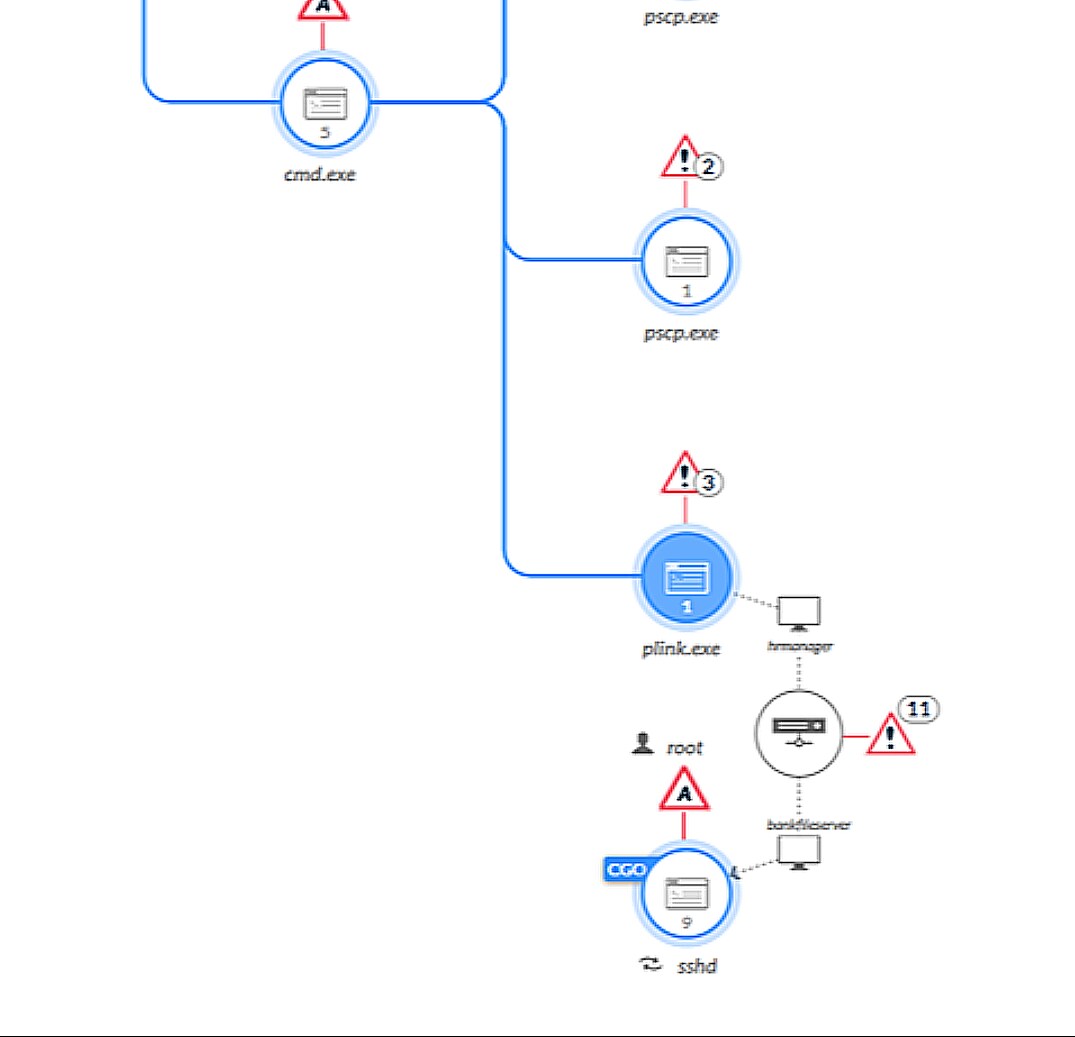
By providing strong correlation and context, the XDR platform enables the Analyst to quickly recognize the relationship between these events across multiple endpoints and regard them as contiguous elements of a single incident. This relationship allows the Analyst to regard any fruits of the activity (including system changes, file drops, or additional process spawns) as being directly attributable to this incident; the Analyst can then confidently collect and associate those subsequent elements to the incident and better orient their response.
We rely on our XDR platforms to provide us data, and the more data they can provide us, the greater our indictment of malicious activity becomes. Without automated stitching of correlated activity, an Analyst would be presented with two distinct data points in this example. The Analyst must then determine the degree to which these alerts are related. Meanwhile, time elapses and the attacker has a window to progress further with their attack.
Strong and effective correlation applied in real-time to these data points becomes a vital differentiating factor in enabling the Analyst to rapidly consume this information and respond with precision.
The Importance of Curated Data
Effective correlation is built on quality, and quality is developed through the methods and mechanisms data is obtained and refined; in short, the curation of the data. Curation refers to the development and enrichment of a data point in order to maximize its value. This starts by maximizing the number and facets of each data point, and delivering each point in the most complete presentation possible. Often, a given action generates multiple data points, each providing a unique view into the event taking place. Visibility that can be gained into each generated data point associated with a surfaced event helps strengthen that event, and enables the Analyst to act more quickly and decisively, with less time spent on enrichment.
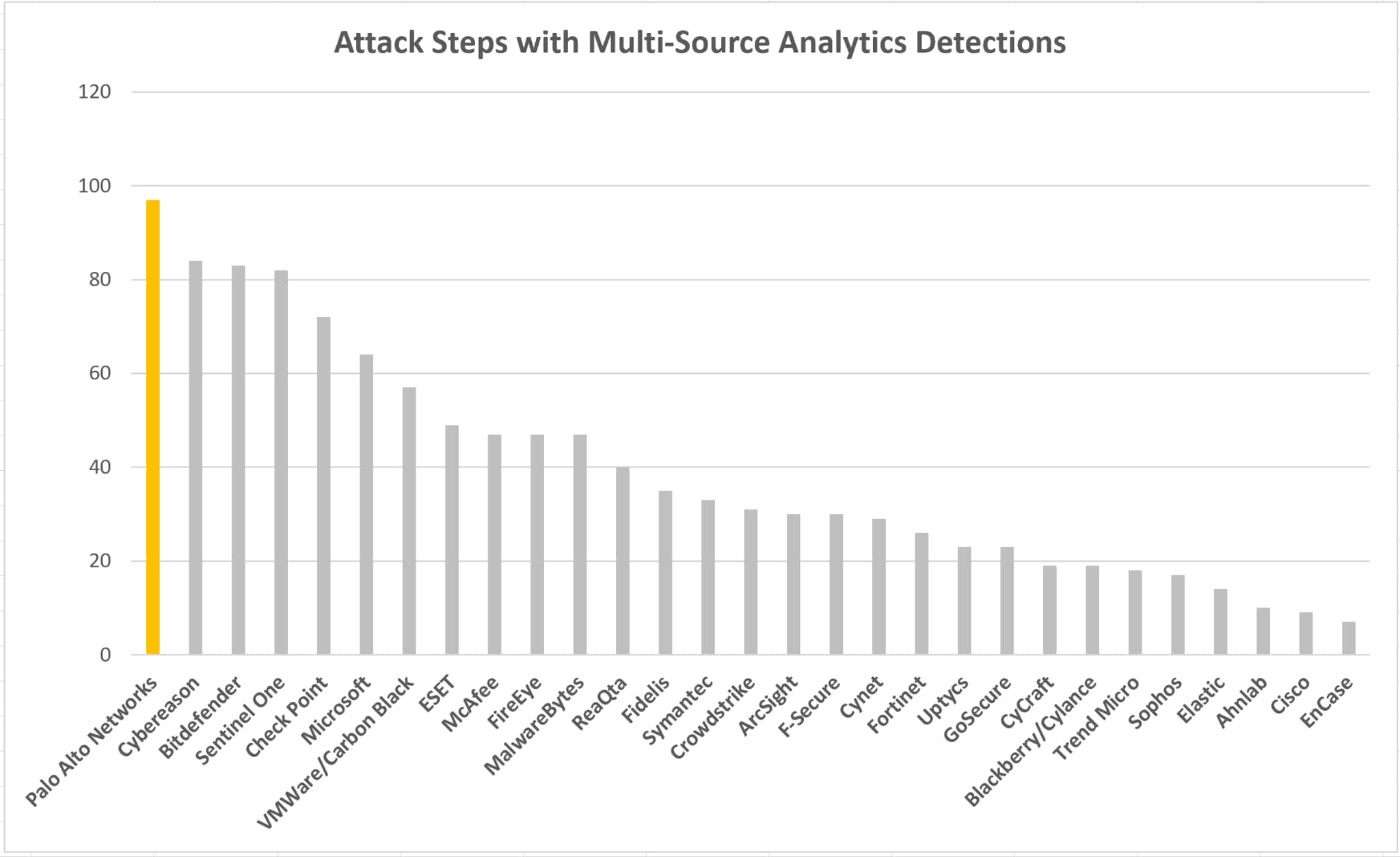
Criteria: Each step which had at least one analytics detection which contained 2 or more data sources within it was counted for each vendor *Note: Data and charts based on MITRE results minus detections with a “Configuration Change” or a “Delayed” modifier.
The Importance of Complete Data
A data point that is captured can be compared to the known elements for an attack stage and evaluated accordingly, however even data points that cannot be mapped to a known attack step contain potential future value, however when we face attacks in the field, this foreknowledge is never assured. Many organizations devote resources to cyber threat intelligence services in an effort to gain insight into emerging attacks in an effort to maximize the efficacy of their Analysts and EDR and XDR ecosystems. Intelligence is not a static entity; it evolves continuously. As our intelligence evolves, data collected previously gains new relevance. Therefore, an EDR or XDR cannot omit a data point at generation without negatively impacting the organization’s ability to leverage its intelligence services, or gauge the full extent and impact of an attack that has been surfaced.
Attack step 5.A.2 stages later activities by dropping a series of python scripts and several text file resources which are to be used later in the attack chain. The Cortex XDR telemetry for this is shown below:
There are a few things that are really important here from an Analyst perspective. First, we have the python scripts themselves, and their associated hashes:
However, there are also additional, non-executable files that were also dropped by this attacker as well, namely we see a text file that was an element of this attack (admin.txt) that was also written.
In the intelligence context, this presents a situation where an early stage attacker may find latitude to insert their attack elements before Threat Intelligence provides context raising them as an indicator since they may not have been collected before the indicator was provided. An investigator will subsequently have difficulty ascertaining whether or not (or to what extent) the attacker has infiltrated the environment since at this stage they would have relevance (the Intelligence indicator) but may not have the necessary data to apply it to. It is also a key reason why complete, and continuous collection of data points is vital to gauging the overall value of that solution and is an important advantage that CORTEX XDR customers currently enjoy.