Let’s look at security automation in three levels of maturity. The first level is the creation of helpful tools that humans use to optimize their vulnerability scanning. The second level is automatic threat detection without any human intervention. The third level is automatic threat resolution, where bugs are discovered and removed without asking for permission. Traditionally, the third level takes years of learning and engineering. What if we could jump straight to level three?
First, you need to grow your insights
There are many complex issues that underpin automatic threat resolution. Gathering information about your system is, alone, a difficult challenge. There are many disparate sources of information, with new services being updated, created, and removed on a daily basis. Keeping track of all of this is something that organizations have struggled with for years.
But how do you manage all of this data?
If you do manage to create a system that can scrape data from all of your services, you’re then encumbered with a new challenge. Where do you put all of this data? A solution to this only spawns further obstacles, leading to the questions: What is the most efficient format? How do you control costs? How do you keep queries fast?
There’s the long route to creating insights
You can begin with the implementation of a scalable logging solution. This means deploying, maintaining, patching, scanning, and monitoring your own infrastructure and all required software. This requires specialist knowledge and, most importantly, takes time. Security and operational procedures need to be reasoned, networking limitations need to be avoided, storage space needs to be optimized, and much more.
Building and running your own observability stack is a huge challenge. Even with expert development and specialist operational support, you’ll still be regularly maintaining and scaling your stack.
And then there’s the shortcut - Coralogix
Your logs contain a hidden wealth of operational insight. However, logs are naturally disordered. Coralogix specializes in this arena. Rather than building and deploying your own ELK stack, inheriting the burden that comes with this solution, Coralogix provides a managed ELK stack with integrations into all of your favorite tooling. You can immediately consume data from thousands of disparate sources and visualize them in a cost-effective, simple, flexible, and powerful user interface.
Now you have insights, how do you create action?
Coralogix can report on the data you have, but what you need now is action. This is where Cortex XSOAR steps in. Coralogix has a direct integration with Cortex XSOAR, so your data can be immediately utilized.
What types of actions are we talking about?
The flexible nature of the integration between Coralogix and Cortex XSOAR opens up a new array of modern security capabilities.
Automated incident enrichment and response
By implementing a playbook in Cortex XSOAR, you can configure a series of behaviors. For example, if an IP address is already associated with a security incident, you may wish to block that IP address and raise an alert. This is simple.
Coralogix can notify Cortex XSOAR of a potential security issue and, by reading access logs, Cortex XSOAR can automatically detect activity from this new IP address. Cortex XSOAR can then block the IP address and send an alert.
Track changes as they happen
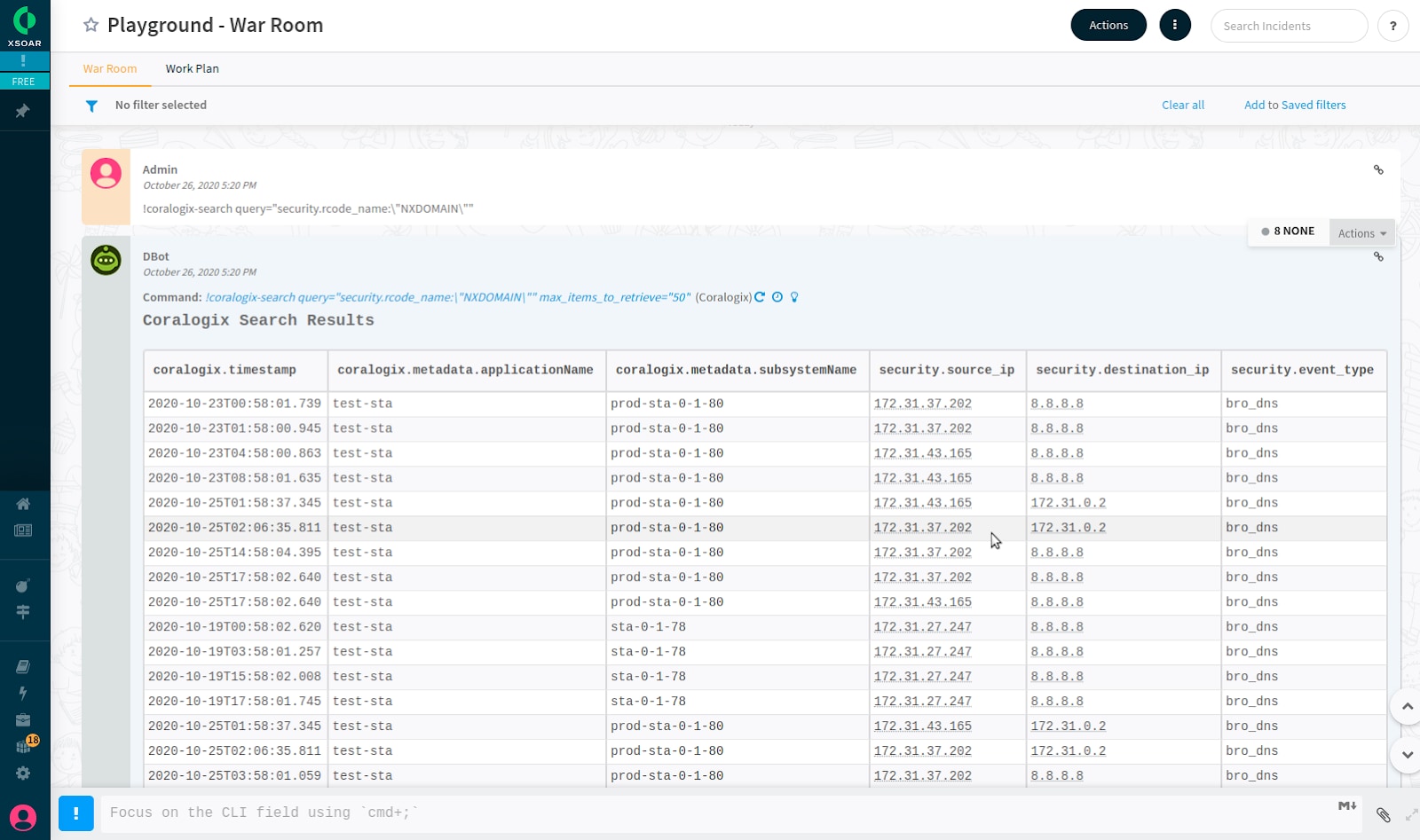
The most common question when a new vulnerability appears in a system is “when was the last deployment?” Without Coralogix and Cortex XSOAR working together, you’ll need to navigate disparate systems to piece together the current truth of the situation.
If Coralogix is integrated into your CI/CD pipeline, the data is easily accessible within Cortex XSOAR. Cortex XSOAR supports direct queries to Coralogix. No need to context switch away from Cortex XSOAR and waste precious time across multiple systems. Get the answers you need, right away.
Immediately surface relevant moments
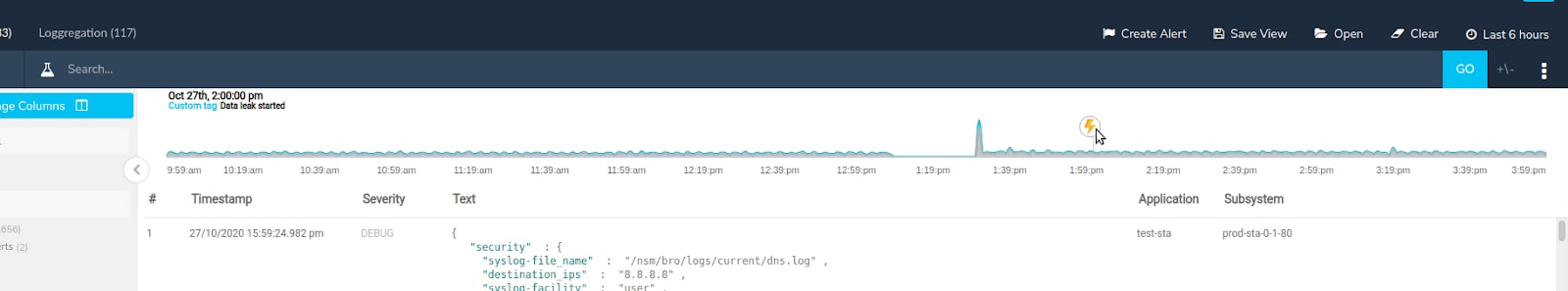
Coralogix supports tagging key moments in your timeline. This capability opens up a new avenue of collaboration between your security and operational teams. Rather than drawing up complex reports that detail each relevant moment, you can overlay this information directly in Cortex XSOAR.
This integration allows you to build an active, responsive map in real-time, that gives your security team total ownership of the information. This centralized approach to information gathering brings all of the knowledge into one place where it can be discussed and form the basis for a data-driven decision.
Conclusion
By bringing together the insights of Coralogix with the sophistication of Cortex XSOAR, you gain access to a pipeline of powerful data, fed directly into an intelligent engine that can directly solve security problems for you.
This level of automation creates a safety net for your engineers. Product iterations can proceed at pace, secure in the knowledge that if something does go wrong, Coralogix and Cortex XSOAR are on hand, to patch your vulnerabilities and deploy into production with confidence.
Visit our Cortex XSOAR Ecosystem to learn about other Cortex XSOAR integrations, or get started today with the free Cortex XSOAR Community Edition.