Getting your threat intel management (TIM) program up and running might seem like a daunting task. Picking the right feeds and enrichers can be challenging as there are many different options and flavors to choose from, and these subscriptions sometimes come with a hefty price tag.
So, we have made it easier for our Cortex XSOAR customers to find and install integrations that do not require a subscription and in some cases might not even require registration upfront. We have known and used most of these feeds for a long time now and we have found them as a good stepping stone to get any TIM going.
To make it easier for you to discover and take advantage of these free feeds and enrichers, we’ve added four new tags to our out-of-the-box feed integrations in the Cortex Marketplace:
1. Plug & Fetch - This tag was created for feeds that are free and which do not require any credentials or registration. As using a Plug & Fetch integration does not require any registration or credentials all you need to do is set up an instance for it in Cortex XSOAR TIM and let the pack run. A good example of such a feed is LOLBAS, which does not require any credentials whatsoever.
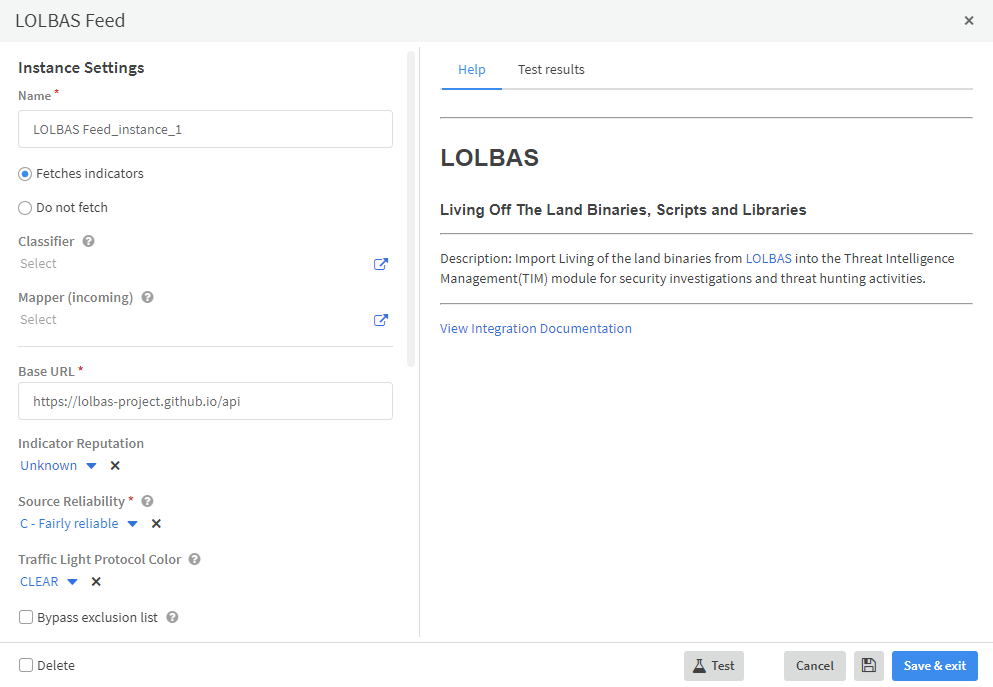
To find all of the Plug & Fetch feeds available for XSOAR you can simply use the “Plug & Fetch” tag in the Cortex Marketplace search filters:
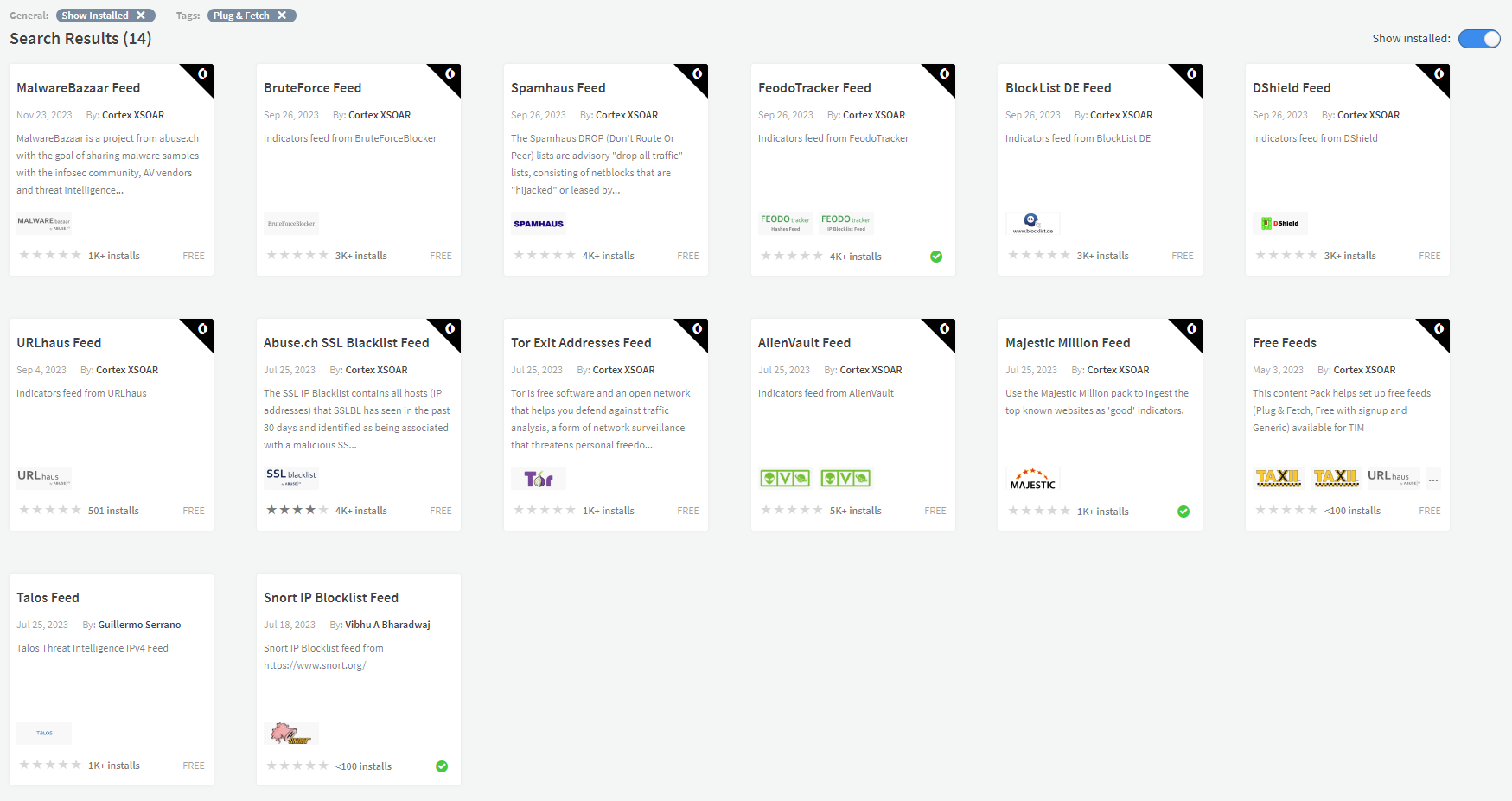
2. Free Feeds - The Free Feed tag is used for feeds that do not require a subscription but do require the user to register in order to obtain the credentials needed to ingest the feed. A good example for such a feed would be the National Vulnerability Database (NVD).
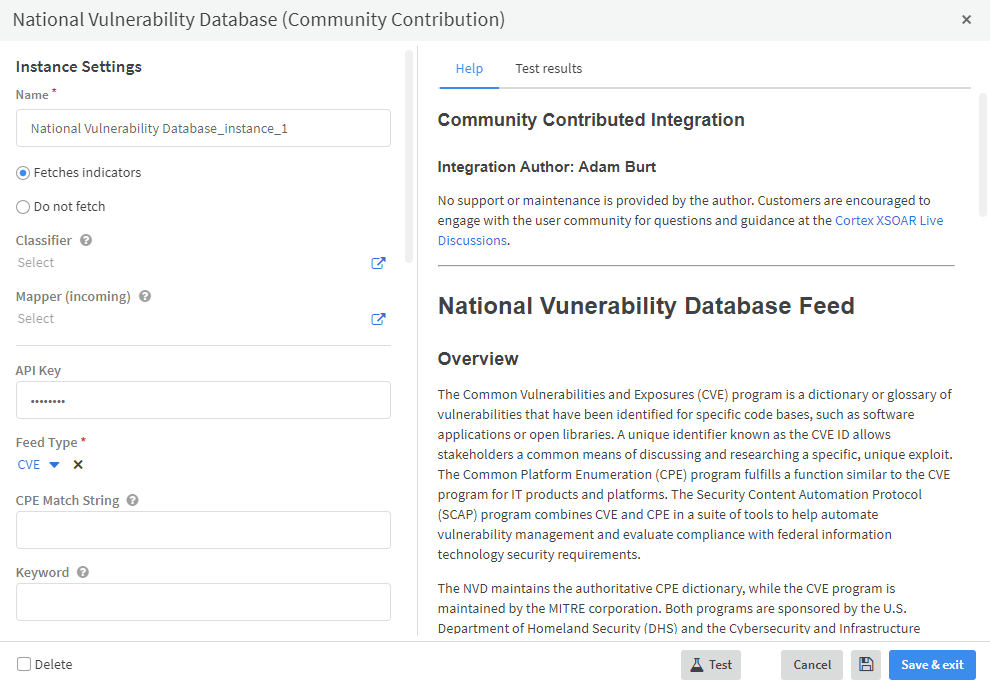
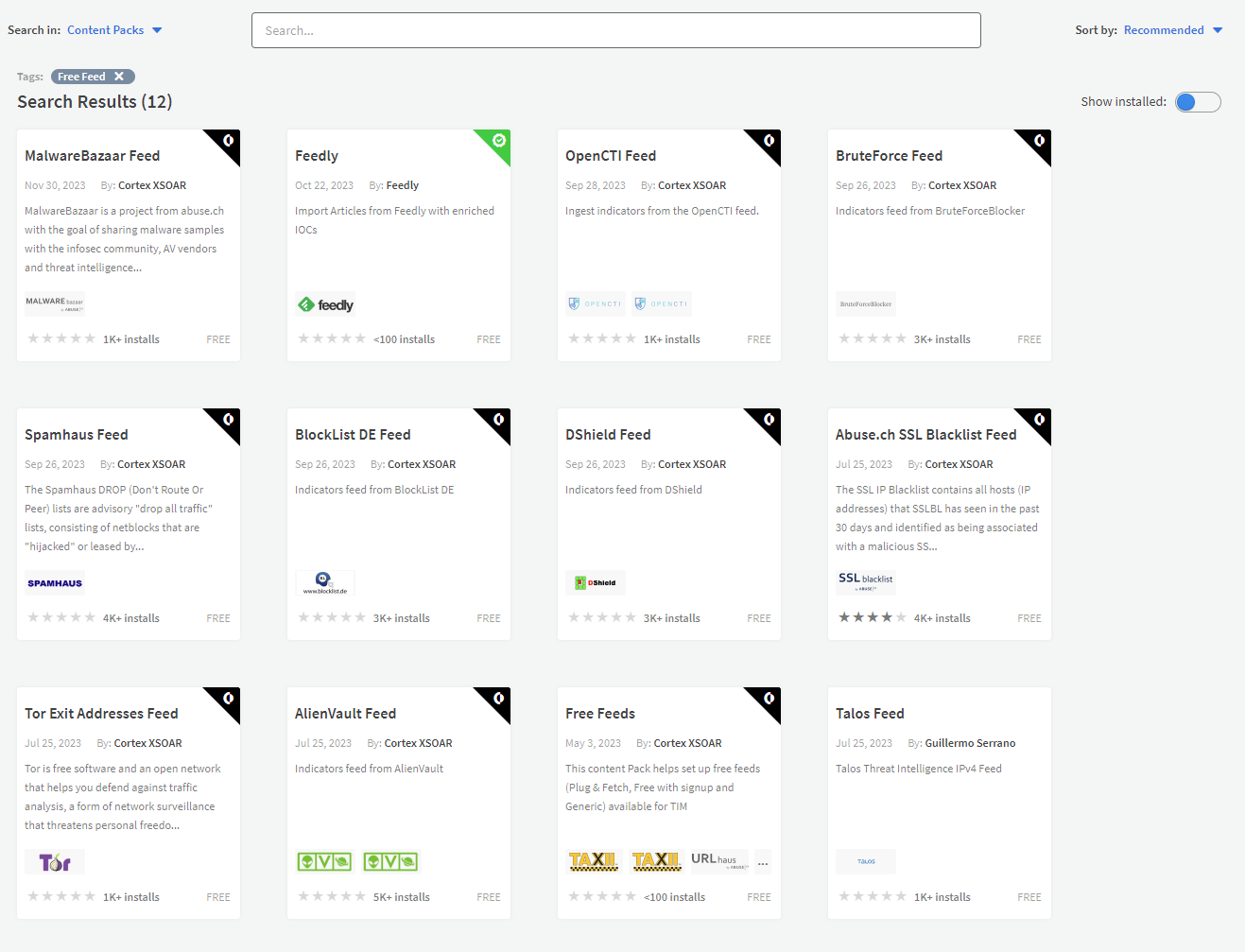
As before, you can use the “Free Feed” tag.
3. Generic Feeds - The Generic Feed integrations are used when XSOAR does not have a pre-built integration for a specific feed. As most feeds usually use common data formats such as TAXII, JSON, CSV, etc, the user can use these Generic Feed integrations to fetch the data without building a custom integration from scratch. These can also aid as a skeleton structure for building an integration for a feed using these common frameworks.
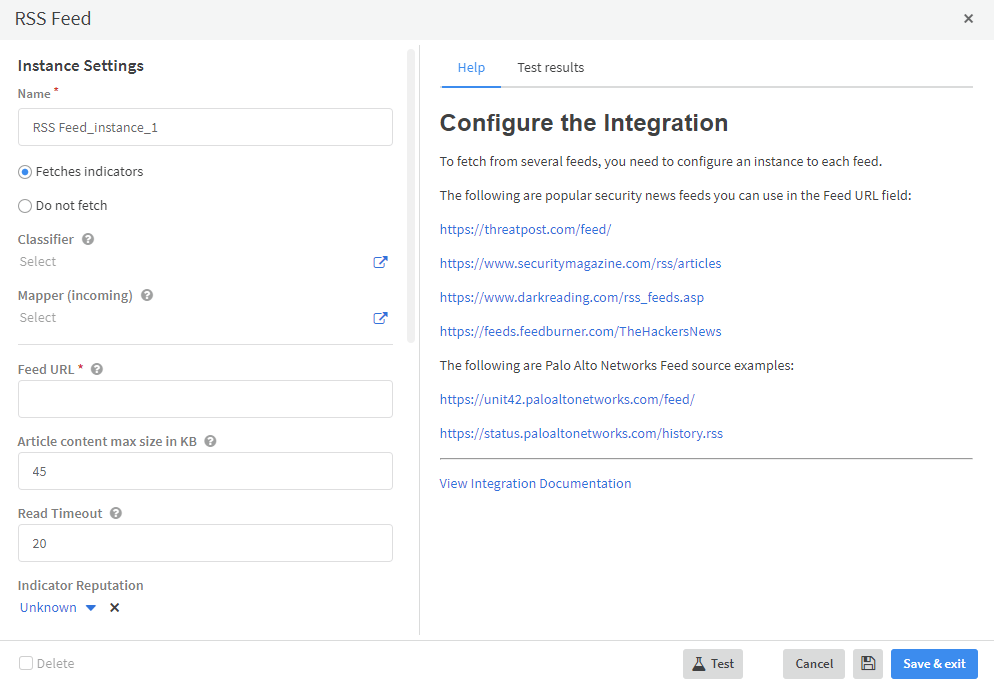
An easy setup for an RSS based feed:
4. Allow lists (previously known as whitelists) - Unlike other feeds that are meant to provide us with indicators for blocking and keeping our environment safe, these are meant to help us keep it organized and to prevent inadvertent lockouts to applications or services used by the organization. The “Allow list” tag feeds include assets from well known companies such as AWS, Azure, Cisco, Google, Cloudflare, etc.
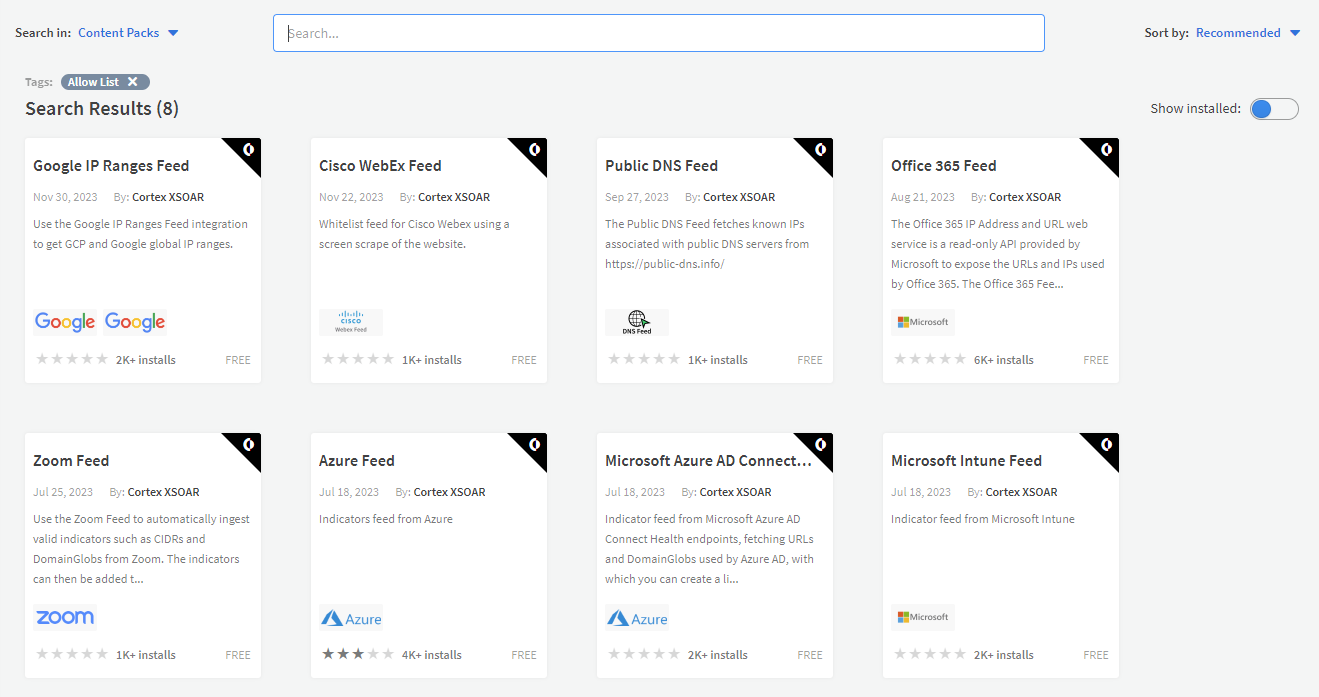
These feeds are almost always Plug & Fetch but as they are different in nature, we decided to give them a distinctive tag to enhance searchability.
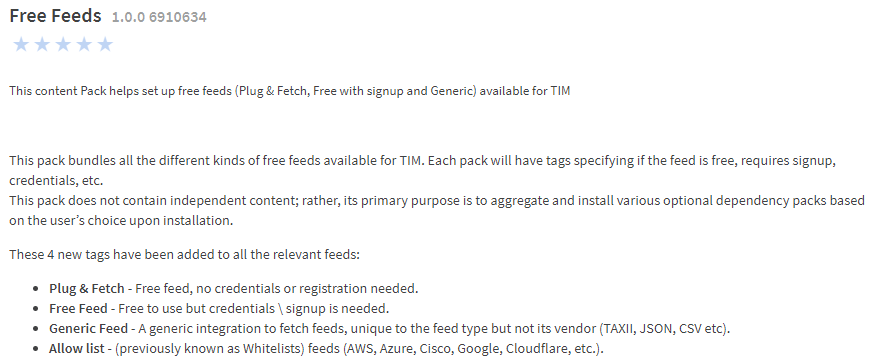
To make life even easier for our users, we have also created a new XSOAR pack called “Free Feeds”. This new pack has all the data presented above and lists all the available new feeds within XSOAR, and any optional dependencies, in one single location. We will update this pack with every new free feed that is added to XSOAR.
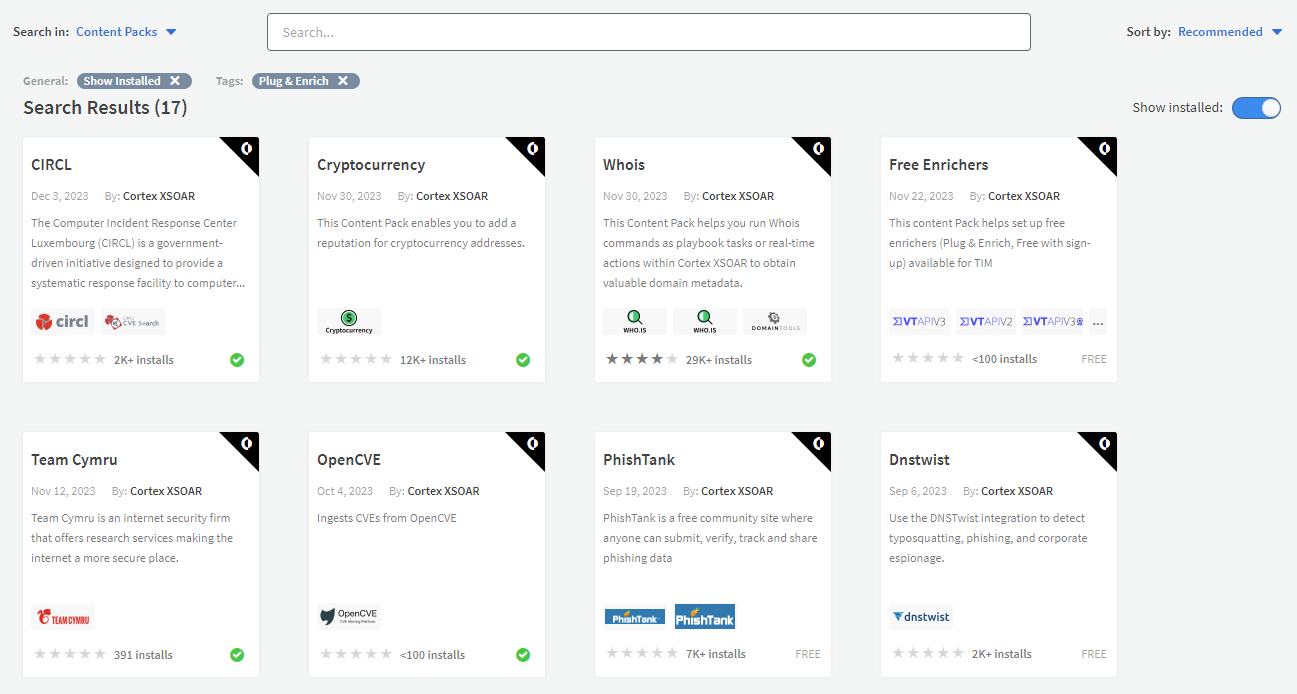
Just like with feeds we have also added two new tags to indicators of compromise (IOC) enrichers within XSOAR:
5. Plug & Enrich - like the Plug & Fetch tag this new tag lists any integration within XSOAR that allows the user to enrich IOCs without prior registration. These integrations can be set up in little time to provide rich context to your incident investigations at no additional cost.
A good example of a Plug & Enrich integration is Team Cymru which provides data about IP addresses:
6. Free Enricher - Like “Free Feed” this tag is there to inform you that the enricher is free to use (or have a free \ community tier) but it does require the user to register in order to acquire some sort of credentials to access the data. The “Free Enricher” tag also includes within it all of the Plug & Enrich integrations.
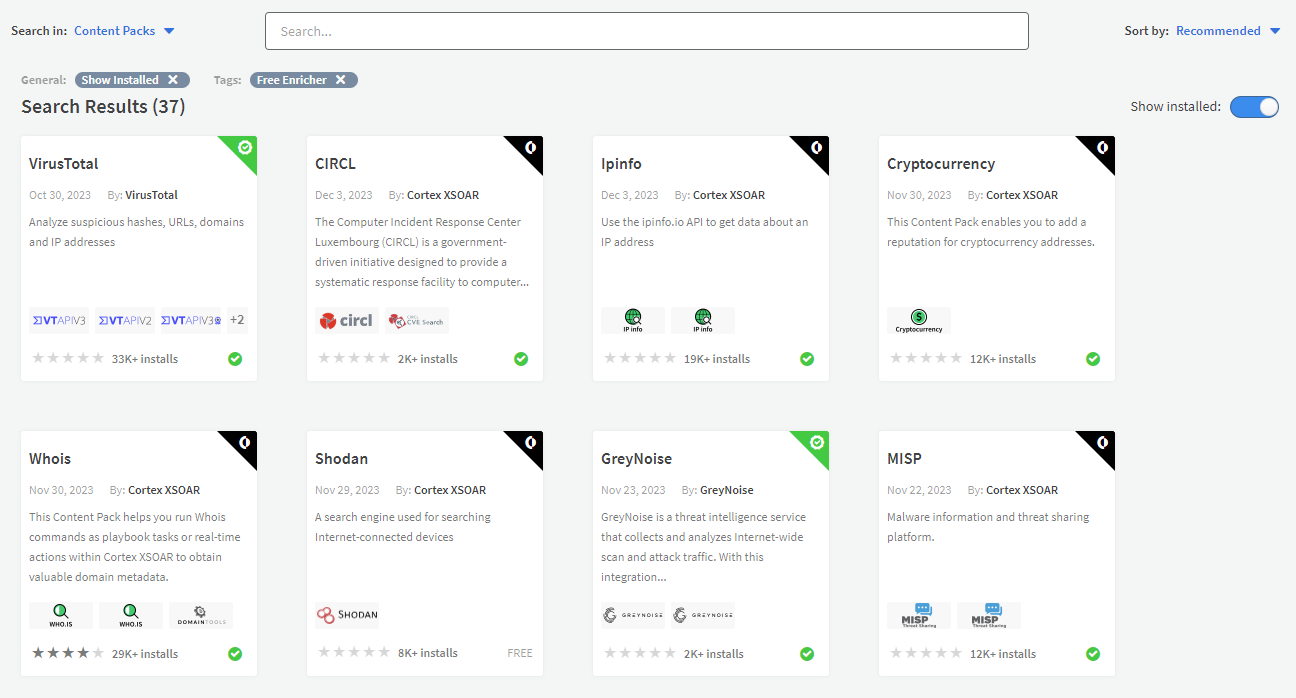
A nice example of such an enricher is AbuseIPDB which requires an API key in order to install an instance in XSOAR.
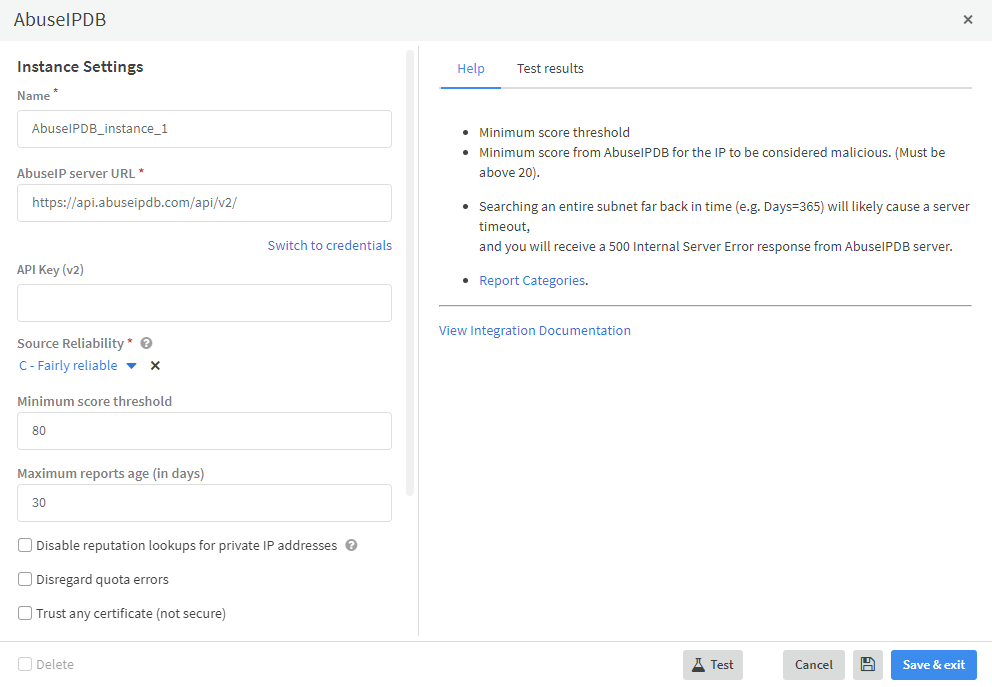
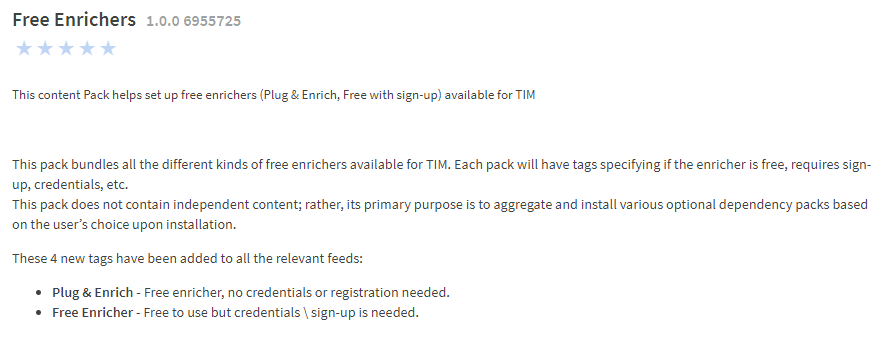
Just like with our Free Feeds we also created a new XSOAR pack called “Free Enrichers” which lists all of the free enrichers available in the Marketplace and provides details about the tags used to define them.
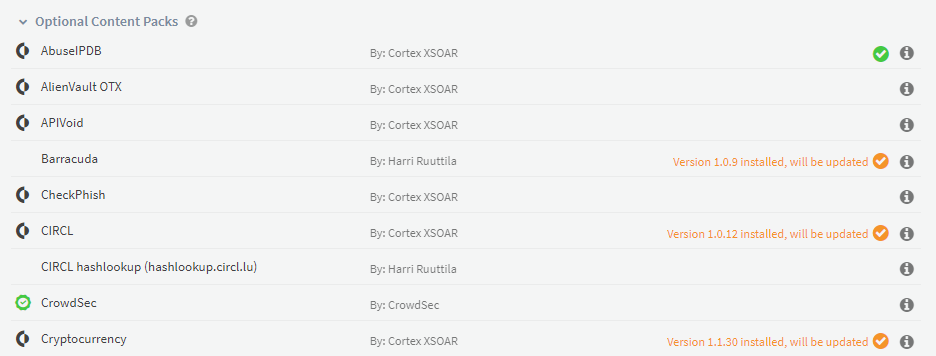
These content packs, as well as hundreds of other packs covering a myriad of incident types and use cases can be discovered in the Cortex Marketplace. In order to run these packs, you will need an instance of Cortex XSOAR.
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.
Read about how you can transform your Threat Intel Management with XSOAR.