Executive Summary
The threat landscape for macOS is rapidly evolving, demanding ever-increasing vigilance from users and developers alike. While macOS has a reputation for robust security features, it is by no means immune to cyber threats. In fact, the malware landscape targeting macOS is growing and diversifying, encompassing backdoor spyware, ransomware, stealers, remote access Trojans, and sophisticated surveillance software.
Several specific threats have emerged over the years. AppleJeus, a malware attributed to the Lazarus Group, was first discovered in 2018 and marks a significant shift in the group's tactics from primarily targeting Windows to also including macOS. Another threat, NukeSped, a remote access Trojan (RAT) also linked to the Lazarus APT and was first discovered in 2019. It has a wide array of capabilities, including acting as ransomware, spyware, and stealer malware. In 2022, a new malware known as SquirtDanger surfaced which specifically targets macOS systems with sophisticated evasion techniques to avoid detection.
Apple continues to respond to threats that target its platform with features such as Gatekeeper, Notarization, and Lockdown Mode, demonstrating its ongoing commitment to user security. While Apple's macOS is generally considered secure, it still accounted for 6.2% of all malware detections in 2022, marking a 165% increase from the previous year. The most common types of malware on macOS are adware and potentially unwanted programs (PUPs), with ransomware and other malware types also on the rise. The threats targeting macOS are evolving, particularly with the widespread shift to remote work.
In this blog, we will be covering a novel machine learning (ML) model incorporated into our macOS agent that enables detecting evolving macOS malware with unprecedented accuracy. This marks a significant leap in our ongoing efforts to protect our customers from existing and evolving threats in the macOS landscape.
What’s Wrong With the Existing Ecosystem
Despite robust built-in security measures, macOS is not invincible. Increasing cyber adversary sophistication and persistence pose significant challenges to existing security measures, leading to successful evasion and system compromise.
One of the primary macOS security measures is XProtect, a signature-based malware detection tool. While XProtect has partially proven effective against known threats, its signature-based approach has limitations. It identifies malware based on existing signatures or identifiable characteristics of known threats. This means that novel or modified malware variants that are adept at altering their signatures, especially those from advanced persistent threats (APTs), can bypass XProtect's defenses. Additionally, XProtect lacks dynamic scanning capabilities, which can detect and neutralize threats as they occur, a feature commonly found in third-party EDR solutions.
Gatekeeper is another macOS security feature that prevents the execution of unsigned or malicious applications downloaded from the internet. It verifies the developer's ID and checks for alterations in the application since it was signed. However, cyber adversaries have found ways around this security measure, including using stolen developer IDs to sign their malicious applications or exploiting vulnerabilities in legitimate applications to execute malicious code.
The macOS security landscape also suffers from a visibility problem. Many organizations lack the necessary visibility into macOS endpoints due to a misconception that macOS is immune to threats, thus reducing the effectiveness of threat-hunting and incident-response efforts.
Gathering the Right Data With Cortex XDR Agent for macOS
Cortex XDR utilizes sophisticated machine-learning algorithms to scrutinize patterns and behaviors in two modes: pre-execution and post-execution. This enables the agent to identify and block even zero-day threats and previously unseen malware at the earliest possible stage of the threat, offering protection that adapts to the evolving threat landscape.
The new macOS malware detection model has been trained on an extensive dataset consisting of samples obtained from both public repositories, private samples collected by Palo Alto Networks, and malicious samples of well-known red-team/adversary tools.
This comprehensive collection of samples enables analyzing a wide range of malware families and developing a broad understanding of their characteristics. Our new dataset is comprised of more than 75% new files, ensuring our model stays up-to-date with the latest threats in the wild, while avoiding blocking new legitimate tools that may be used by our customers.
The new model was built using advanced data clean-up and deduplication techniques, and a state-of-the-art gradient boosting algorithm. According to internal evaluations, this enables improving our detection rate by over 25% while also reducing false positives by over 65%.
New Dataset Cleanup and Tuning Approach
It’s important to have a lot of data to train an accurate and effective ML model, but it’s not enough on its own. You also need good and accurate labels, balanced proportions between the different clusters in the dataset, and diversity in the collected samples. When training this model we introduced two new approaches to dramatically improve the quality and diversity of our datasets.
First, for each sample, we collected threat intelligence data from both internal sources (such as WildFire) and external sources. Knowing that no data source is 100% accurate, we created a sophisticated labeling logic that uses these sources to generate a more accurate verdict, which we used for training. Then, to balance our dataset and avoid focusing only on the most common malicious or benign sample families, we applied an in-house ML-based deduplication algorithm.
This approach uses common attributes such as locality-sensitive hashing, combined with a clustering algorithm that is based on our extracted features set which can detect similarities in files even when locality-sensitive hashing fails.
Extensive and Custom Feature Extraction and Analysis
At the core of our malware detection engine lies a custom feature extraction mechanism. Built by cyber security experts, the feature extractor effectively and efficiently summarizes each file into thousands of features that are then fed into our machine learning model.
Information about the maliciousness of a file may be hidden in various places throughout the file, so our feature extractor extracts the most important parts such as headers, segments, sections, libraries symbols, and strings. In addition, we use a disassembler and extract features that can describe different behaviors of the code.
A disassembler is a specialized tool that translates binary code into human-readable assembly instructions, providing insight into the functionality and behavior of the analyzed software. By disassembling Mac files, we gain visibility into the underlying logic, control flow, and potential malicious patterns encoded within the malware. Our model then processes all these extracted features from millions of samples and is able to detect subtle patterns in malicious files.
In many machine learning algorithms, model generalization is often tied with a smaller number of features that contribute to the model and capture the essence of the data. To support that, tools and methods were developed to reduce the number of features a model uses, such as feature selection and regularization. However, we actually prefer a model that is diverse and robust and can detect malicious files using many features.
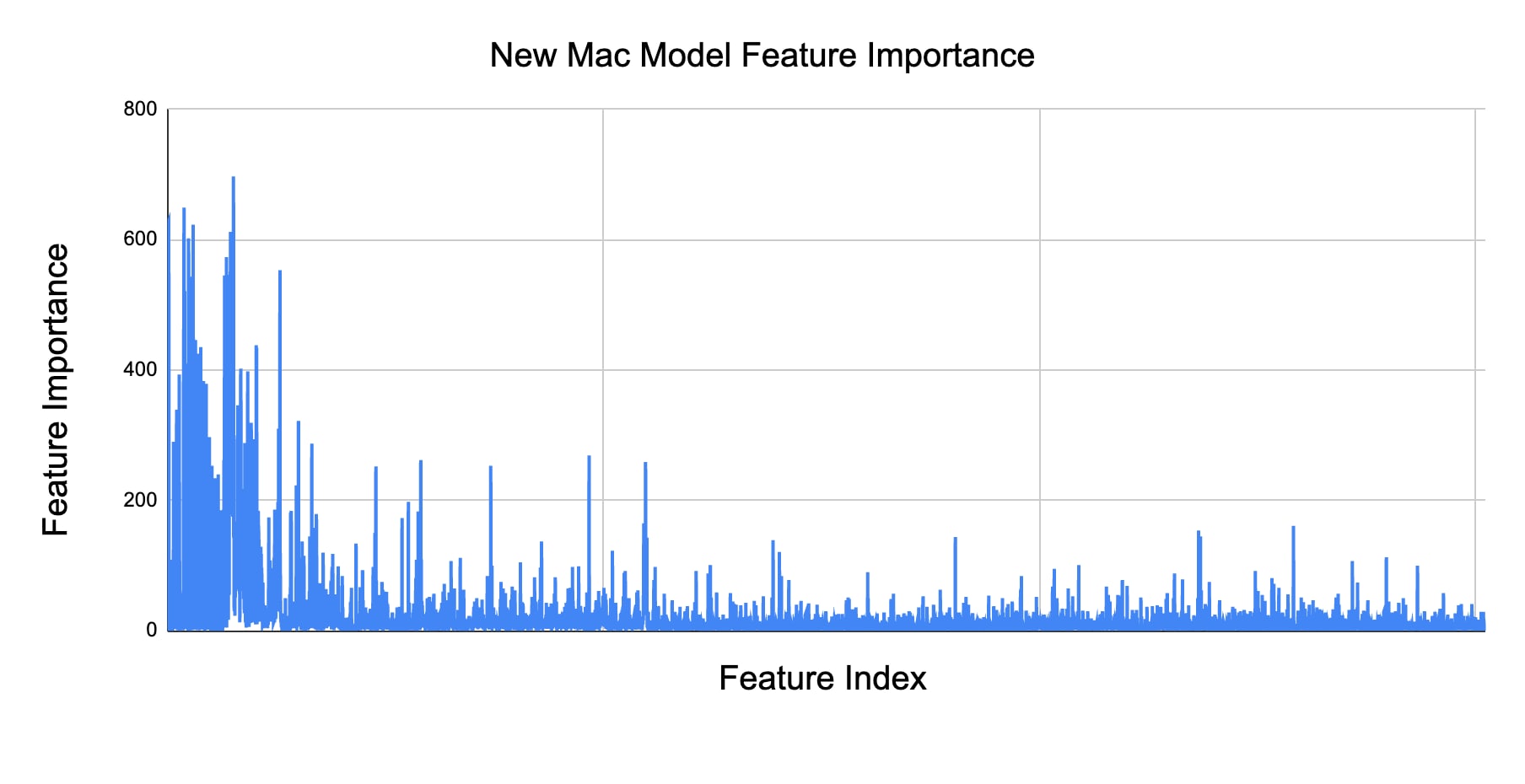
One tool to evaluate the robustness of a machine learning model is feature importance analysis. Feature importance refers to the measure of the impact or relevance of each feature in an ML model. It helps determine which features have a stronger influence on the model's predictions. The X-axis in the graph below is ordered by the different types of features. This indicates the new model takes into account a broad spectrum of features and a diverse ability to detect malicious files.
Improved Sliver Framework Detection
The new model was tuned and validated using a set of key performance indicators (KPIs) to ensure its accuracy over a wide range of samples. In addition, we manually tested selected sample groups that had higher importance or sensitivity. One example is the Sliver framework, where the new model achieved over 98% detection rate based on our internal evaluations.
Sliver is a popular open-source adversary emulation framework used by both red teams and threat actors. The Sliver framework enables the operator to generate implants for macOS as a macOS executable or dynamic library (dylib). These implants communicate back to the command and control (C2) server using one of the available protocols, such as HTTP, DNS, or WireGuard.
Each Sliver implant is different in size, hash, and ssdeep, which makes it harder to catch. It also uses compile time obfuscation, which generates randomization and causes the same configuration to generate different-looking samples every time.
While Sliver is gaining traction among attackers, many malicious Sliver samples are undetected by existing malware detection products. For example, we tested a random batch of private Sliver samples, and more than 50% of the samples had five detections or less when checking them against threat intelligence providers.
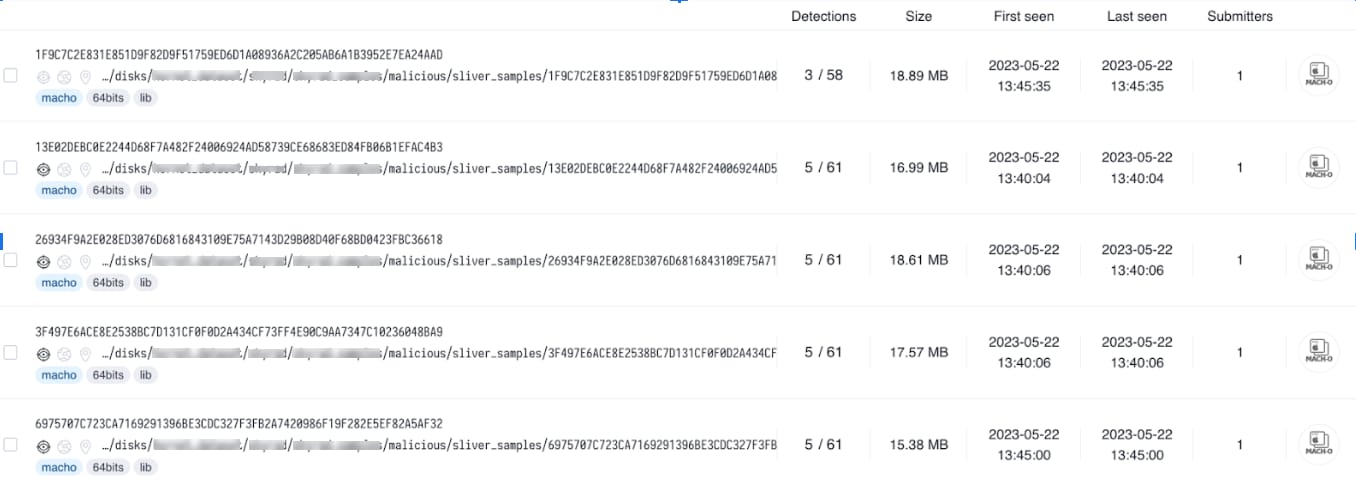
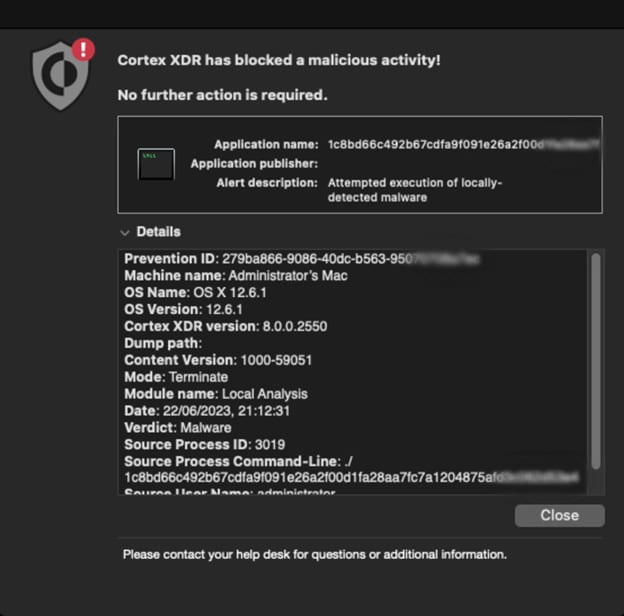
To detect the Sliver framework, we collected external samples found in the wild as well as private samples found by our internal research teams and enriched them with numerous samples we simulated in our lab. We then used our custom-made feature extraction to add these samples to our malicious datasets for training and evaluation. Finally, we fine-tuned our ML model to detect the malicious samples, dramatically increasing the model’s coverage without causing an increase in false positives.
Conclusion
The new ML-based detection model for macOS provides a powerful layer of protection against existing and new malware. It uses top-notch techniques to reliably predict the maliciousness of a file using dynamic models that continuously learn and adapt, based on real-time threats derived from our extensive customer base.
This model is a great addition to our multilayer defense strategy for macOS, which analyzes both static and dynamic artifacts taking place on the endpoint. These combined efforts provide comprehensive protection for macOS users, no matter the complexity or sophistication of the threats they face.
The new ML model is available to all Cortex customers running XDR agent version 8.1.0 and above. This rollout will be backported to older versions as well in the upcoming weeks.