Palo Alto Networks is the leading vendor in preventing Cobalt Strike C2 communication and blocked 99.2% of tested attacks, with the next leading vendor blocking only 17% of attacks, as cited in a recent report here.
The ever-evolving threat landscape makes it challenging for organizations to be confident in their security posture. In fact, we have seen a 100% year-over-year increase in attacks where threat actors leverage a zero-day exploit before vendors can patch them. Our Unit 42 team has reported more than a 73% increase in attackers using white hat hacking tools to perform command and control attacks, with “Cobalt Strike” as the leading attack. All of this makes it even more critical for companies to select cloud-delivered security tools that are easy to scale and provide zero-trust security. SecureIQ Lab published a study comparing three SSE offerings, concluding that Palo Alto Networks is the leading vendor in preventing Cobalt Strike C2 communication and blocked 99.2% of the five attack scenarios, with the next leading vendor blocking 17% of attacks.
Cobalt Strike Explained
While Cobalt Strike is a legitimate piece of software that is sold to white hat hackers to perform penetration tests, cracked versions have recently become easily available and are used by a wide range of threat actors. With an intuitive UI, threat actors can perform command and control attacks such as command line execution, file transfers, keylogging, etc., without sophistication. Researchers have also created and shared tools to generate new randomized Cobalt Strike profiles easily. These profiles are highly configurable, small in memory, emit low and asynchronous traffic, and can be masqueraded as different pieces of software, making them difficult to detect.
The traditional approach taken by some vendors uses static IPS signatures, which fails to address new and evasive variants. Some customers even try to monitor their infrastructure manually to identify irregular network activity. A new approach is needed to effectively block C2 traffic with Cobalt Strike while still avoiding any false positives.
Prisma Access Blocks 99.2% of Cobalt Strike Command-and-Control Profile Categories
Palo Alto Networks’ Advanced Threat Prevention uses ML-based cloud-delivered security not only to help protect against standard C2 network activity from Cobalt Strike but also to evaluate the relative resiliency of the protection provided by each product when modifications are made to evade detection.
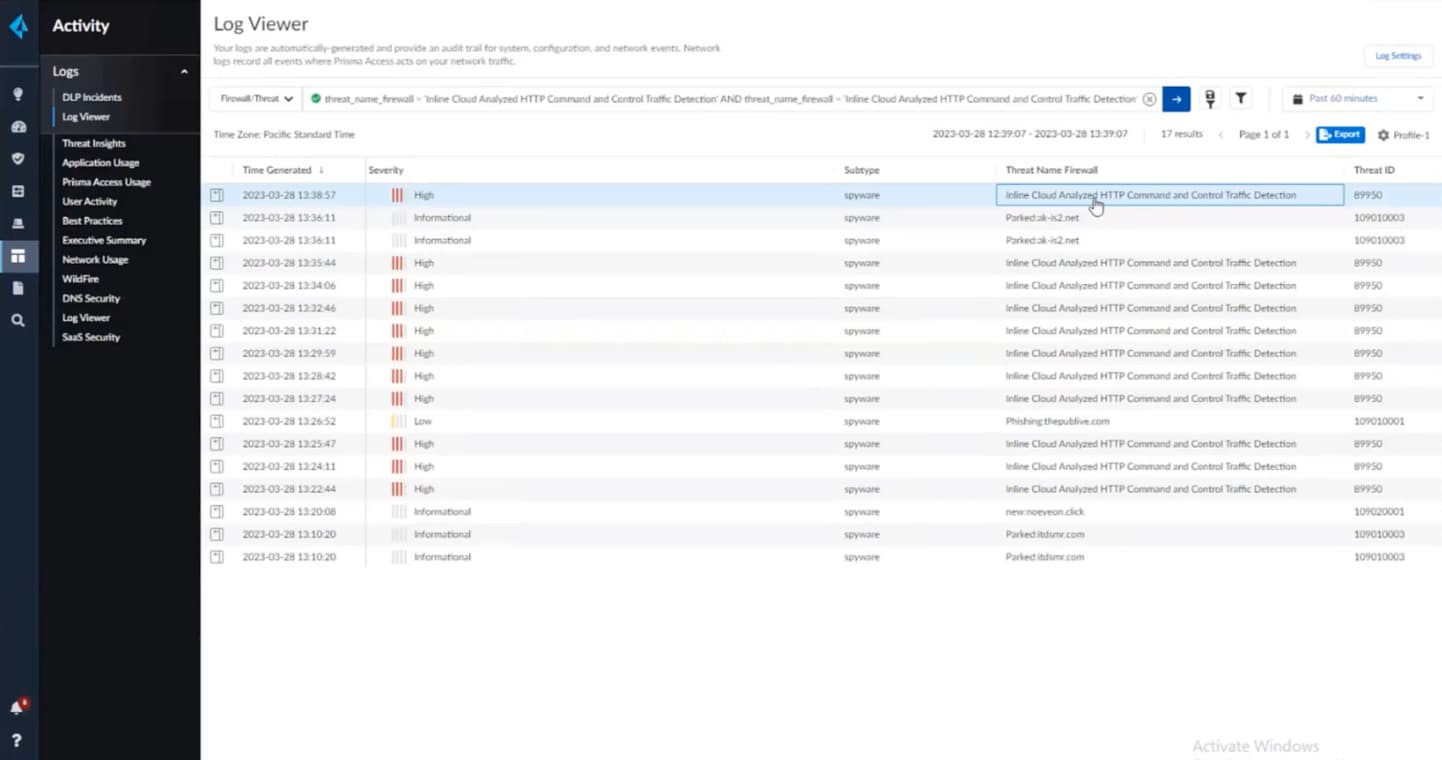
With the cloud-delivered security of Prisma Access, a customer can view the logs of an attempted command and control attack, which can be automatically blocked through configurable settings, while our competitors may allow the traffic.
SecureIQ Lab tested the ability of cloud-delivered security solutions to block the command-and-control capabilities of the Cobalt Strike attack suite. The test measured the block rate of each vendor in five attack scenarios: basic attack, random attack, custom attack, nonstandard ports-based attack, HTTPS attack, and hostname change attack.
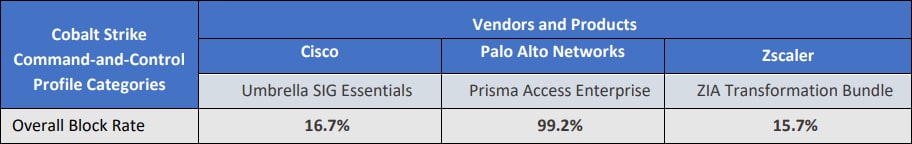
To summarize, Palo Alto Networks leads other security vendors in preventing Cobalt Strike C2 communication. When analyzing other competitors, Cisco failed all HTTPS-based attack scenarios as their solution cannot decrypt IPS traffic in the current version of their SSE solution, and Zscaler missed several attack scenarios when non-standard ports for hosting the Cobalt Strike profile were used. The full report can be found here. For a similar test on next-generation firewalls, please click here.
Conclusion
Continuous security inspection is a fundamental component of a Zero Trust framework and an essential component of ZTNA 2.0. Simplifying identity security across hybrid identity stores enables a unified security product to deliver Zero Trust outcomes with Zero Exceptions. Learn more about how Prisma Access transforms security and networking to deliver the infrastructure and support that today’s hybrid enterprises need here and get started exploring how ZTNA 2.0 on Prisma Access can help secure today’s hybrid enterprises and workforces.