This post is also available in: 日本語 (Japanese)
The adoption of cloud-based identity providers (IdPs) has grown exponentially in the past several years. The reason for this level of growth is largely due to the desire of most businesses to migrate from on-prem to the cloud to manage user identities.
Enterprises are adopting cloud-based identity providers (IdPs) for their ability to tightly control access and centrally increase security with password complexity management, multi-factor authentication (MFA), and single sign-on (SSO) without negatively impacting availability, reliability, or scalability.
However, migrating from on-prem authentication methods (such as RADIUS, LDAP, and Kerberos) to cloud authentication methods (e.g. SAML with Azure AD, Okta, Google Identity) can be a time-consuming and resource-intensive effort that can lead to delayed projects. Organizations need ways to navigate the complexity of hybrid and distributed identity stores without compromising end user security.
Prisma Access, our flagship cloud-delivered security platform, now provides organizations two key solutions to help navigate deployment complexity and gradually migrate users to cloud authentication:
- Multiple Portal Authentication Support allows organizations to configure cloud authentication and on-prem authentication within a single Prisma Access instance. The co-existence of on-prem and cloud authentication within Prisma Access helps enable the gradual migration of user authentication from on-prem to cloud.
- Cloud Authentication Service with Cloud Identity Engine integrates with multiple identity providers from a single interface and simplifies authentication with cloud IdPs to help solve operational challenges.
Multiple Portal Authentication Support
Multiple Portal Authentication Support enables IT administrators to configure two mobile user GlobalProtect portals on the same Prisma Access tenant. For example, a customer who wants to migrate from RADIUS to SAML can enable Multiple Portal Authentication Support to activate an additional portal on their Prisma Access instance.
Portal 1 can service existing RADIUS-authenticated users without service disruption while Portal 2 can be enabled for SAML authentication.
The customer can use Portal 2 to test SAML authentication for a subset of its users, gradually rolling it out to other uses with a simple portal change on the GlobalProtect agent.
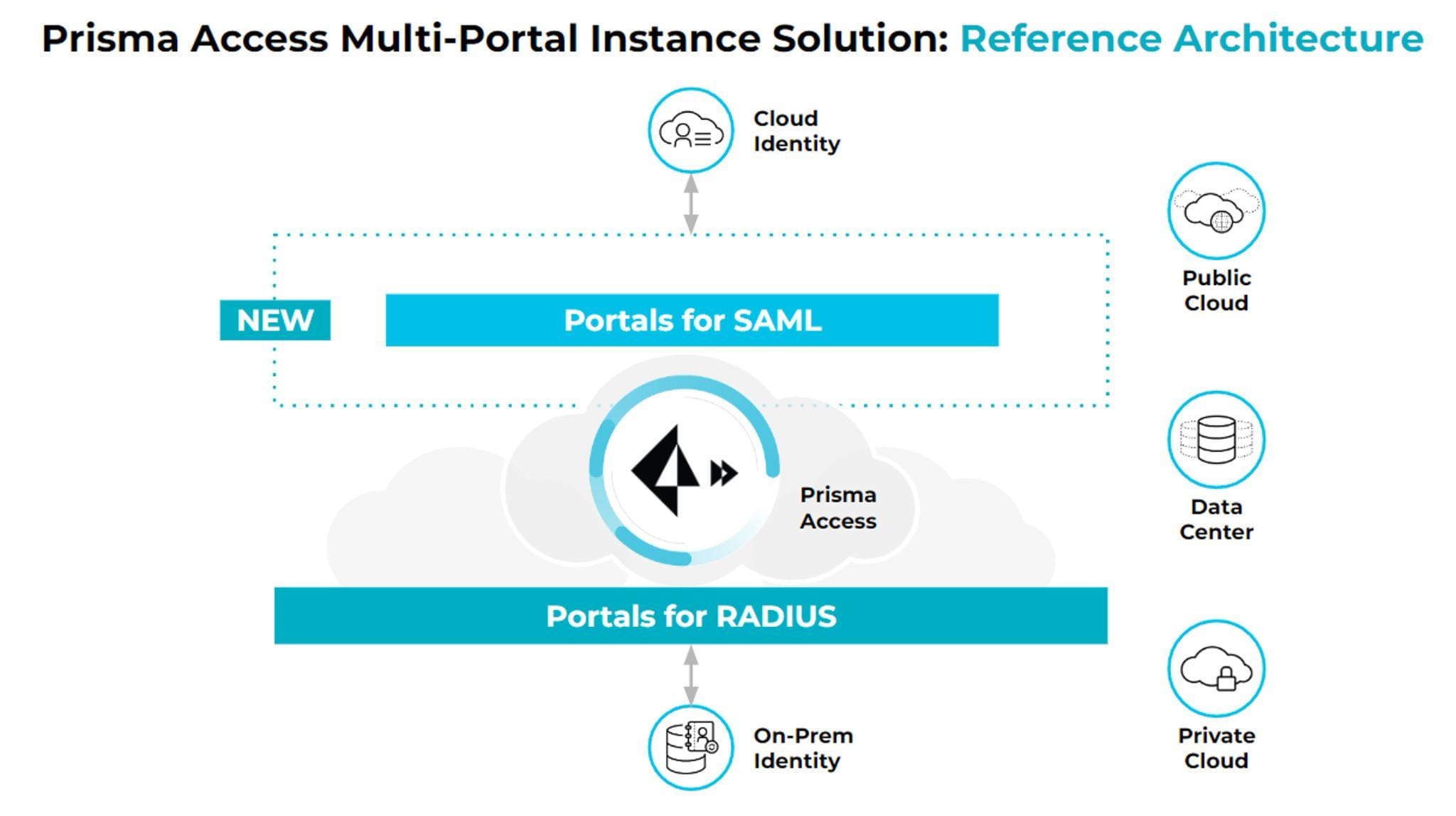
Fig 1: Both RADIUS and SAML portals are active within a singular Prisma Access instance.
Cloud Authentication Service with CIE
Cloud Identity Engine (CIE) provides network security teams a single implementation point to manage MFA for both on-premises and cloud IdP. CIE integrates with one or more IdPs in a few clicks, eliminating the frustration of configuring IdPs on individual security devices.
Prisma Access now supports CIE multi-authentication. CIE Multi Authentication allows companies to configure a single authentication profile with SAML 2.0 and multiple certificate authentication methods or identity providers.
For example, a single GlobalProtect authentication flow can be completed with Okta, Azure Active Directory, or certificate-based authentication, depending on which user is trying to gain access. This is essential when multiple IdPs with multiple authentication types are present on a network.
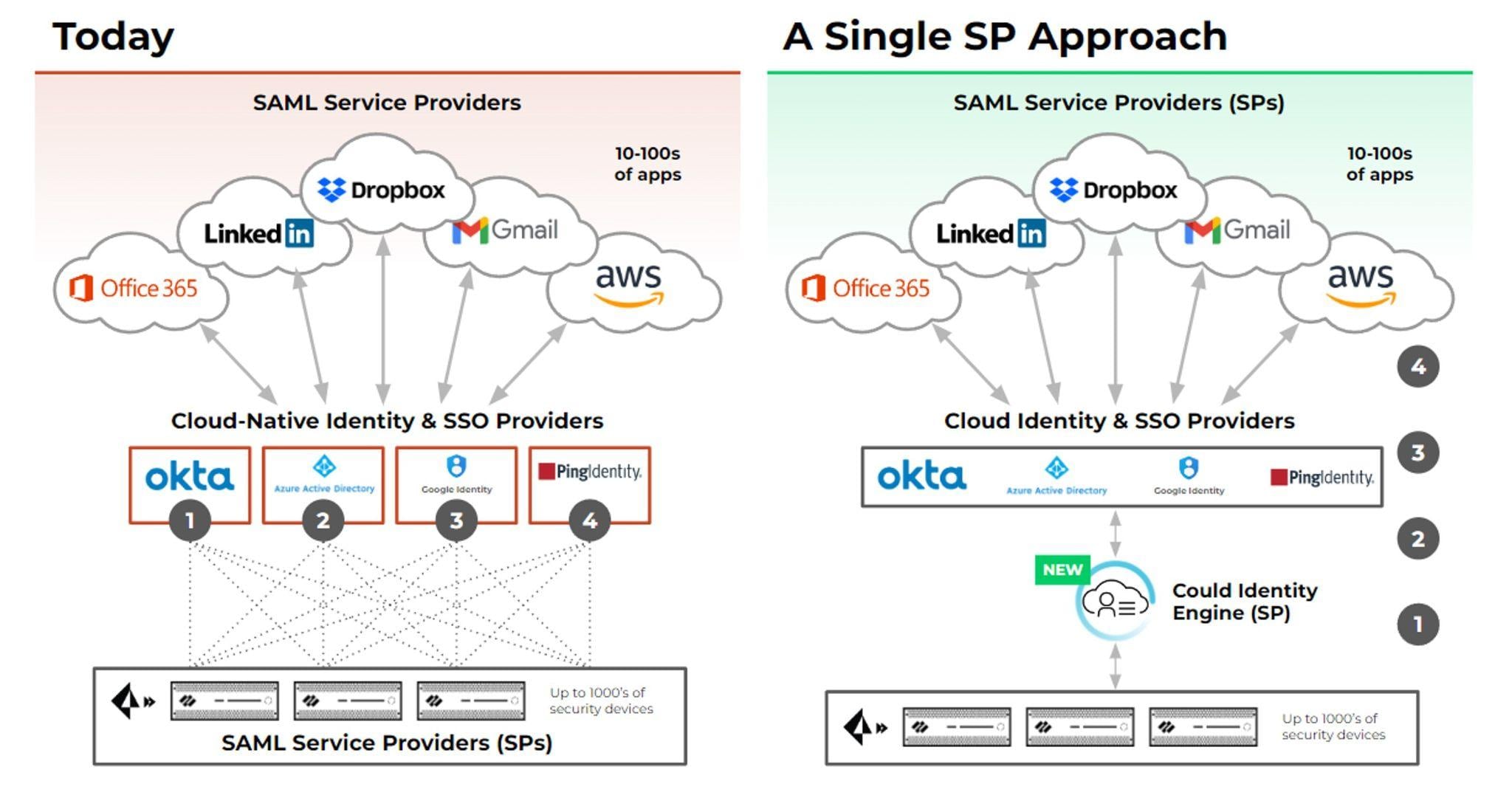
Fig 2: Cloud Identity Engine simplifies cloud authentication setup and management for multiple IdPs.
Identity Security and ZTNA 2.0
Check out the latest Prisma Access and Cloud Identity Engine release notes to learn more about the innovations we are driving around identity on Prisma Access. Identity is a fundamental component of a Zero Trust framework and an essential component of ZTNA 2.0. Simplifying identity security across hybrid identity stores enables a unified security product to deliver Zero Trust outcomes with Zero Exceptions.
Cloud Identity Engine aligns with principles of least privilege access by allowing customers to associate each group in their directory with the appropriate authentication type for that group. For example, customers can have their product management employee group authenticate with SAML through Okta, a contractor group authenticate with SAML through PingID, and another group authenticate via certificate-based authentication—all under one authentication profile. This approach greatly simplifies identity security while ensuring consistent security across hybrid organizations with hybrid workforces.
Get started exploring how ZTNA 2.0 on Prisma Access can help secure today’s hybrid enterprises and workforces.