In just a matter of months during the COVID-19 pandemic, the percentage of employees working remotely jumped alarmingly from 20% to 71%. The World Health Organization (WHO) declared COVID-19 a pandemic in March 2020, and in response enterprises quickly scaled their cloud spend in the third quarter of that same year. Remote work surged, and organizations accelerated their cloud migration plans. Needless to say, Q3 of 2020 saw a massive influx of companies moving to the cloud.
So what does a seismic, unexpected shift to cloud services mean for security?
Our elite cloud threat researchers utilized data pulled from our global array of sensors and found a correlation between the increased cloud spend due to COVID-19 and security incidents: organizations across the world increased their cloud workloads without fully understanding the security implications, leading to an explosion of cloud security breaches. Despite the migration, our research shows that cloud security programs for many organizations are still in their infancy when it comes to automating security controls (i.e. DevSecOps and shifting left). Scaling cloud services without automated security controls embedded across the entire development pipeline is a toxic combination.
Continue reading to discover the top takeaways from the 1H 2021 Unit 42 Cloud Threat Report, learn about COVID-19’s global impact on security posture, and receive a free download of the full report.
COVID-19 Cloud Security Incidents Varied By Industry
The first significant takeaway from the Unit 42 research is that cloud security incidents differed depending on the industry. Additionally, there were significant increases in a wide variety of security risks during the COVID-19 pandemic. Risks included unencrypted cloud data, public exposure of cloud resources, insecure port configurations, and more.
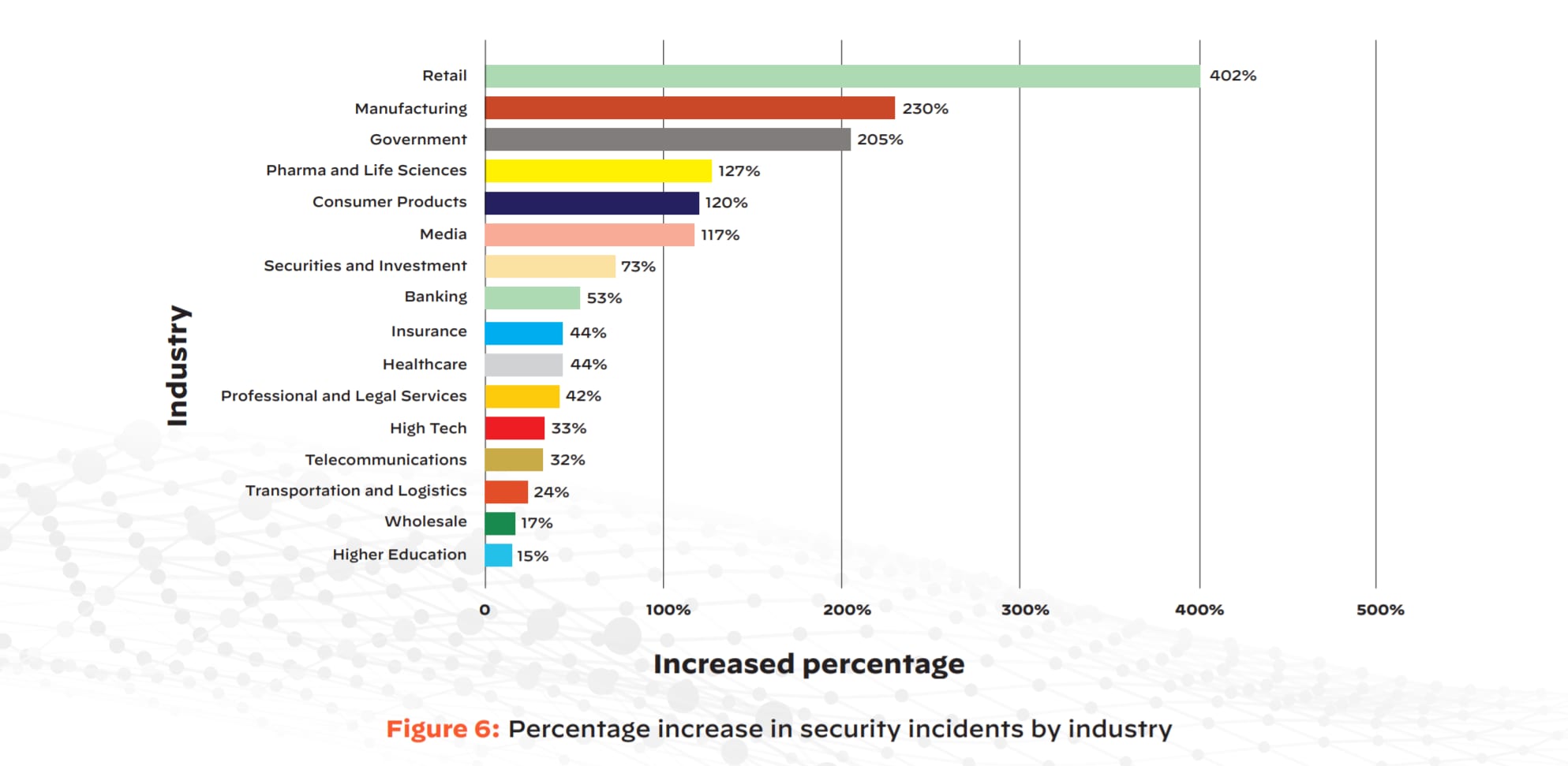
Cloud security incidents for the retail, manufacturing, and government industries rose by 402%, 230%, and 205%, respectively. These industries were among those facing the greatest pressures to adapt and scale in the face of the pandemic — retailers needed new ways to quickly provide basic necessities, while manufacturing and government organizations had to deliver COVID-19 supplies and aid. Industries that play crucial roles in combating the pandemic continue to struggle to secure their cloud workloads, underscoring the danger of underinvesting in cloud security.
Although cloud infrastructure allows businesses to quickly expand their remote work capabilities, automated security controls around DevOps and continuous integration/continuous delivery (CI/CD) pipelines often lag behind this rapid movement.
Cryptomining Increased While Cryptojacking Decreased
Another takeaway was the discovery of some unexpected trends in regards to cryptomining and cryptojacking. The cryptocurrency industry has always been a popular target for attackers, even before the pandemic. However, Unit 42 research revealed the increase of cryptomining and the decrease of cryptojacking during the outbreak of COVID-19.
Cryptomining is the process of contributing computer processing power to validating blockchain transactions for the reward of getting paid in cryptocurrency. Cryptojacking is a type of cyberattack in which the attackers attempt to stay undetected for as long as possible while hijacking a computer system’s resources to mine cryptocurrency for their own gain.
During the COVID-19 pandemic, cryptocurrencies such as Bitcoin (BTC), Ethereum (ETH), and Monero (XMR) grew in popularity and market value. While 23% of organizations showed signs of cryptojacking from July through September of 2020, this number decreased to 17% from December 2020 through February 2021. This is the first recorded drop since Unit 42 began tracking cryptojacking trends in 2018.
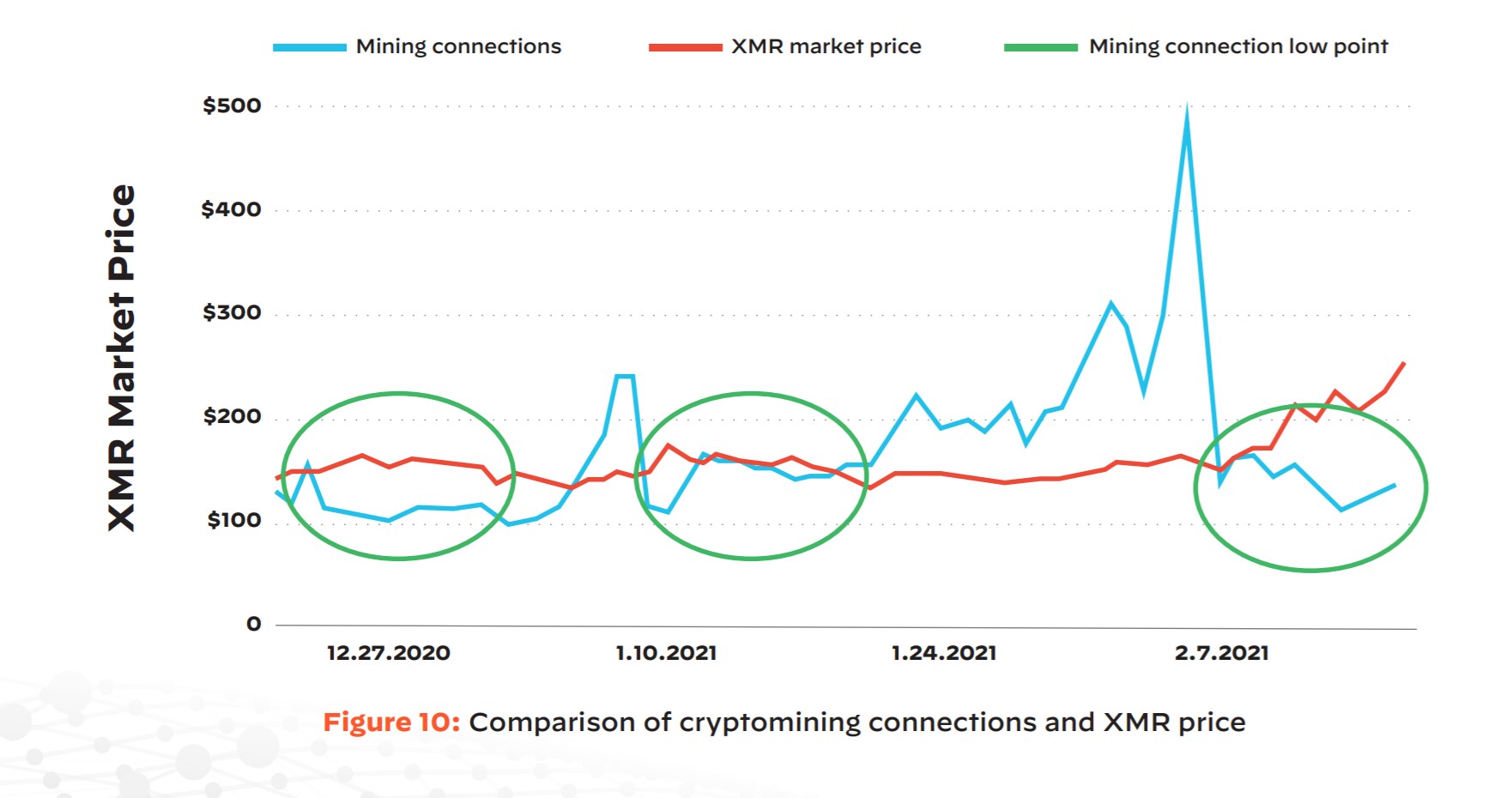
Unit 42 researchers focused on data associated with Monero (XMR), a cryptocurrency popular with hackers due to its strong anonymity protections and the fact that it can be easily mined in the cloud. The research took place between December 2020 and February 2021. Although the amount of data available does not make it possible to draw definitive conclusions, it appears likely that political and health-related events exert a clear impact on malicious cryptomining operations, at least for some cryptocurrency (such as XMR).
Sensitive Data in the Cloud Remains Publicly Exposed
The final takeaway from our research was that organizations have neglected to invest in the cloud governance and automated security controls necessary to protect their workloads as they move to the cloud. 30% of organizations exposed some form of sensitive content to the internet, such as personally identifiable information (PII), intellectual property, or healthcare and financial data. For reference, anyone who knows or can guess the organization’s URLs can access this data.
When this data is exposed directly to the internet, organizations face significant risks associated with unauthorized access and regulatory compliance violations. This degree of exposure suggests that organizations continue to struggle to enforce proper access controls for the hundreds of data storage buckets that may operate in the cloud, especially when those buckets are spread across multiple cloud providers and accounts.
In turn, organizations have created serious business risks, such as inviting breaches through sensitive open ports. Organizations must now build a cloud security program focused evenly around all phases of the software development lifecycle to avoid this threat. Doing so will enable them to not only win in the market, but also to establish sustainable cloud security programs that can expand and contract, no matter what types of unpredictable events take place in the future.
Cloud Spend Must Match Cloud Security Investment
While our previous Unit 42 Cloud Threat Report identified similar problems, the numerous crises unleashed by the COVID-19 pandemic have further amplified the need for a strong cloud security strategy.
For organizations that are ready to identify the threats in their cloud environment, Prisma Cloud analyzes more than 10 billion incidents every month. As the industry’s only comprehensive Cloud Native Security Platform, Prisma Cloud proactively detects security and compliance misconfigurations, as well as triggers automated workflow responses.
Download the full Unit 42 Cloud Threat Report (2021) to continue reading about how you can continuously and securely meet the demands of your dynamic cloud workloads, and visit Prisma Cloud to find out how you can get started on securing your organization’s cloud today.
