DevSecOps, or shift left security, is top of mind for many cloud-native teams today. And as the term has grown exponentially, so too has the number of DevSecOps tools and use cases. But all these new additions to the market make it challenging to decide which DevSecOps tools you need to empower your team with frictionless, consolidated code security.
Related Article: Anatomy of a Cloud Supply Pipeline Attack
To answer this question, let’s walk through the top five DevSecOps tools your team will need to ship secure code fast.
Software Supply Chain Security
The challenge of maintaining security across the development lifecycle is getting “increasingly difficult as security extends into production environments and software supply chain attacks are on the rise,” according to Gartner®.
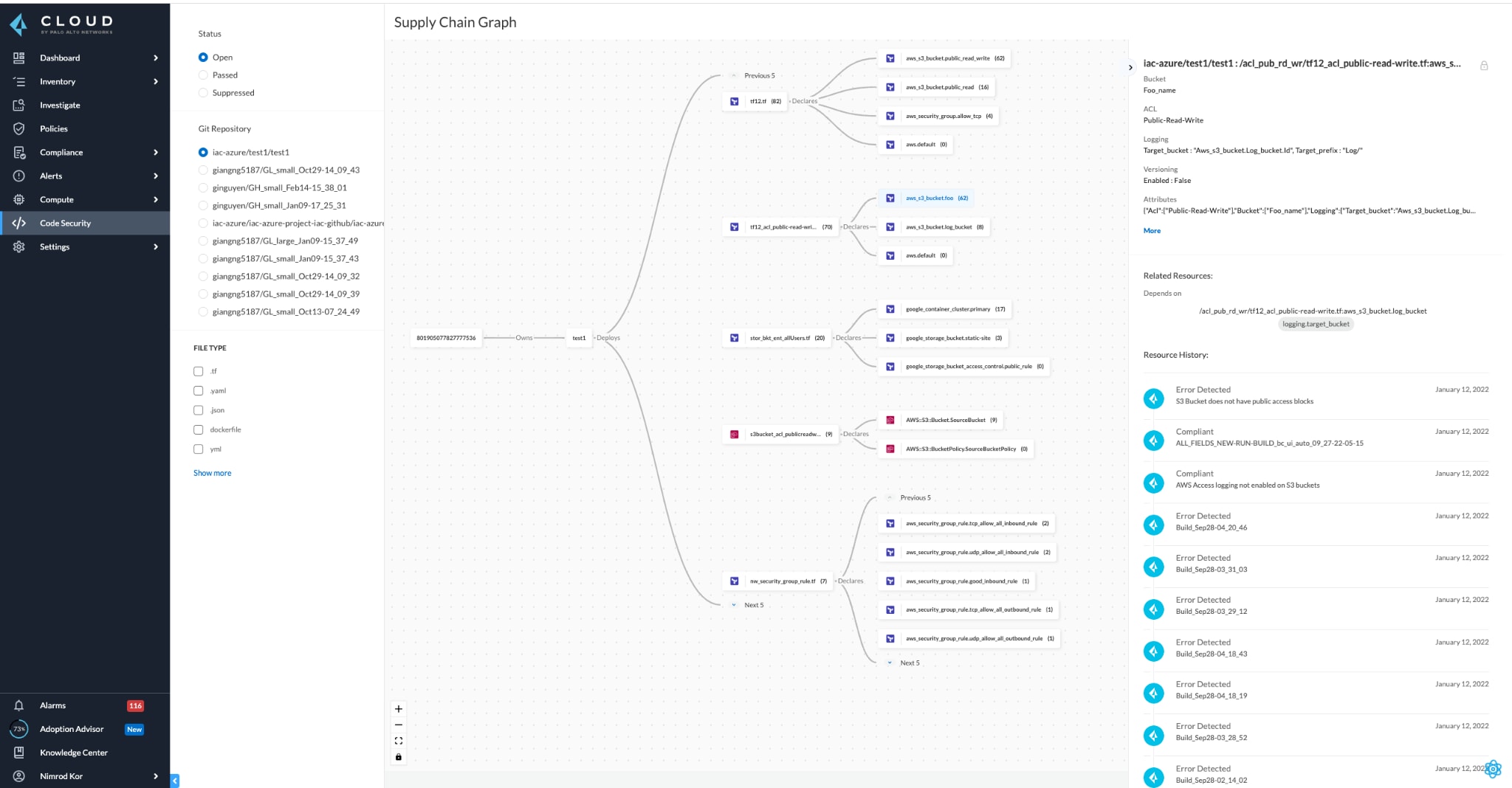
To get ahead of supply chain attacks and clearly visualize your sources of supply chain risks, you’ll need a graph-based solution that visualizes your entire software supply chain. An ideal supply chain security solution also provides complete visibility across your DevSecOps pipeline, giving you visibility into everything from code to resources to delivery pipelines — such as version control systems (VCS) and continuous integration/continuous delivery (CI/CD) pipelines.
And to ensure that your supply chain solution is developer-friendly and aligns with DevSecOps principles, you’ll want to ensure your solution embeds into existing DevOps workflows.
Software Bill of Materials (SBOM) Generation
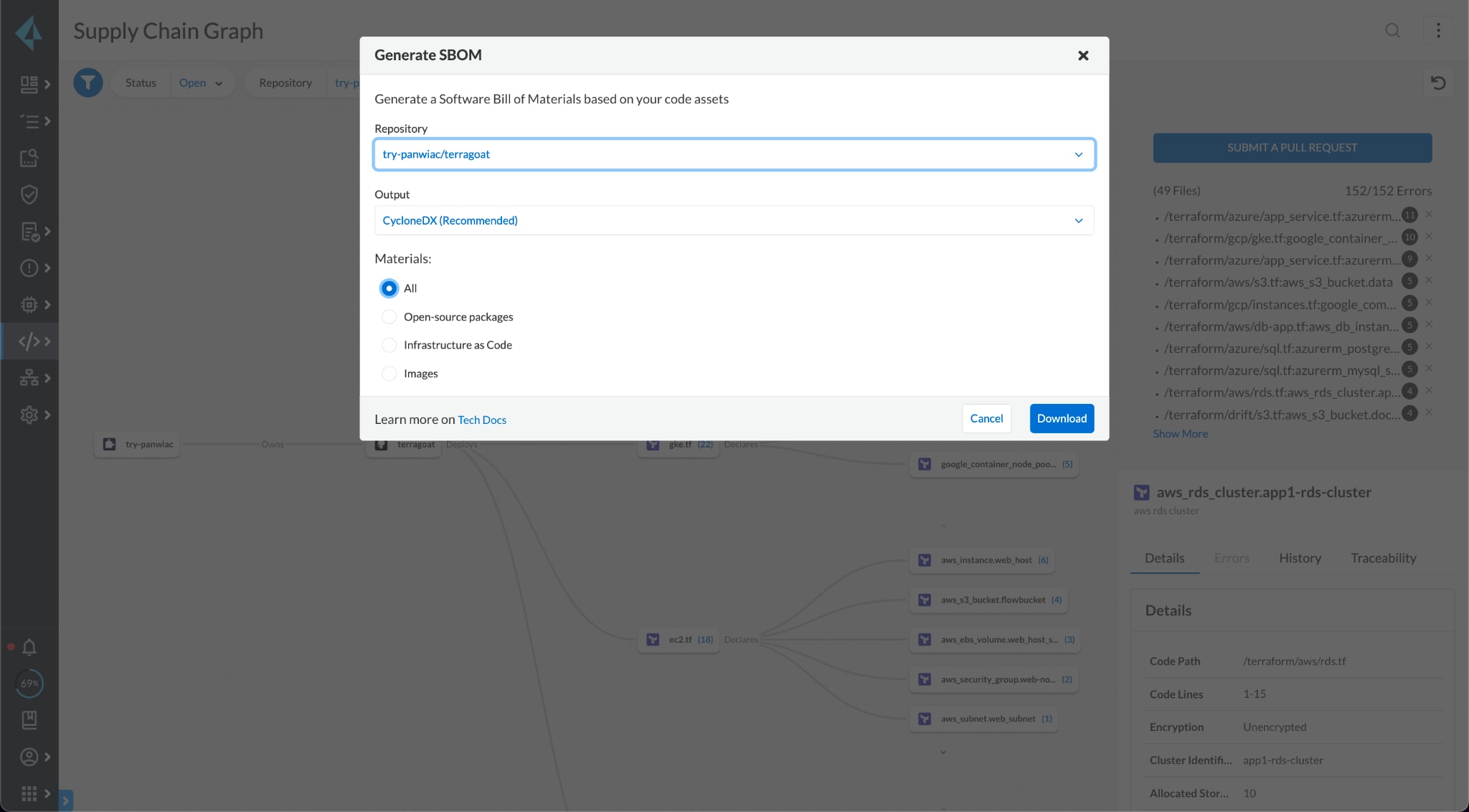
With your graph-based supply chain security solution, you can easily get the visibility you need to fully understand all sources of your supply chain-related risks. Generating a software bill of materials (SBOM) will augment that visibility and give you the comprehensive reporting and inventory management you need to remain compliant and secure in the cloud.
As you adopt DevSecOps tools in your organization, we highly recommend you implement a solution that supports SBOM generation because SBOMs are now a critical component of maintaining compliance, as outlined in the recent executive order to improve the nation’s cybersecurity.
Infrastructure-as-Code (IaC) Scanning
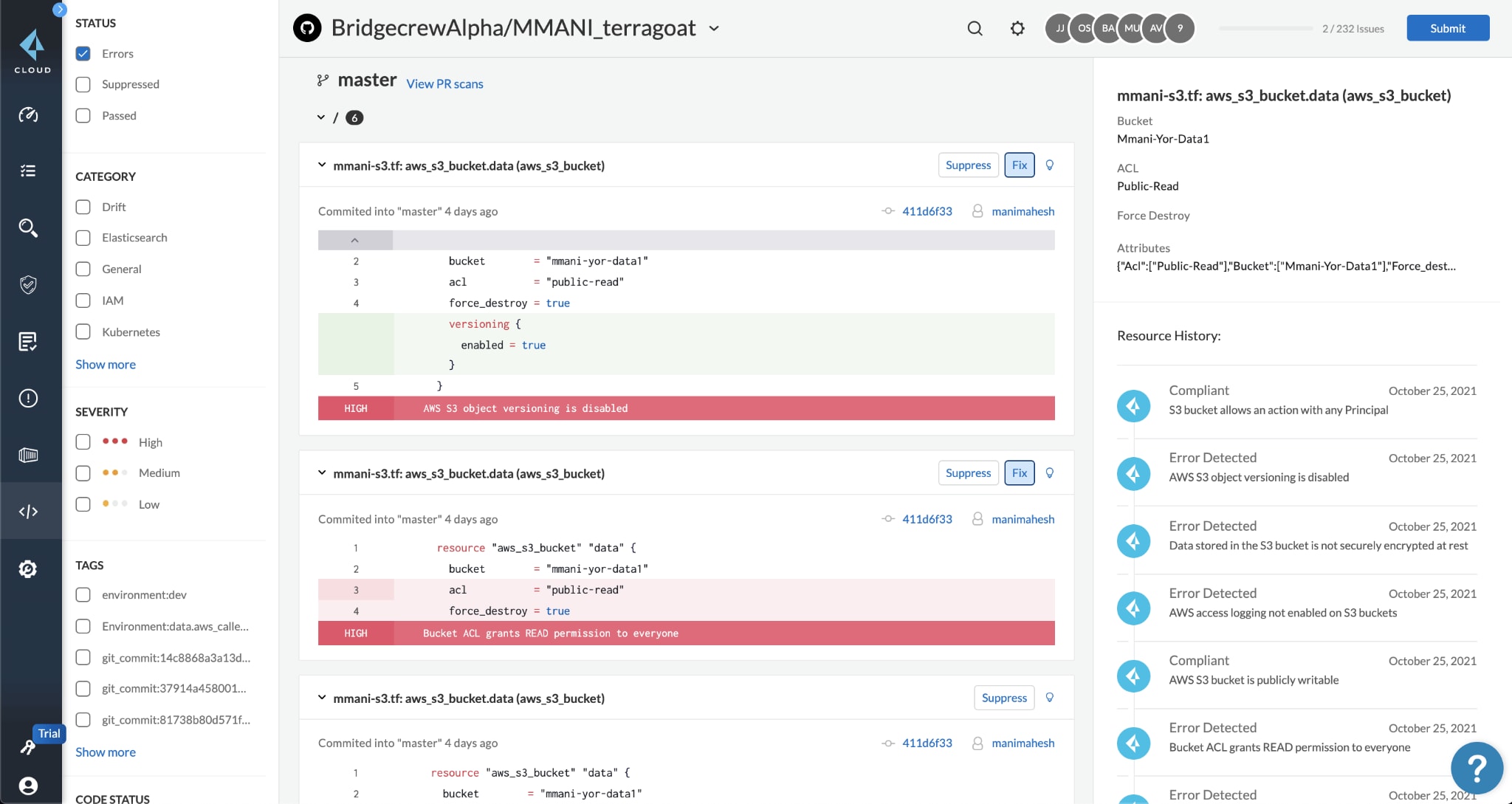
With IaC, your team no longer needs to manually configure cloud resources. Instead, IaC automates this process by enabling you to write resource configurations in code so that you can later use that code to automatically spin up exact replicas of those same resources across instances and environments.
While IaC introduces significant efficiencies, it can also introduce risk unless you scan your IaC templates across the development lifecycle. With proactive IaC security, you can catch misconfigurations before they turn into thousands of duplicative alerts.
To ensure that your IaC scanner aligns with DevSecOps principles, you’ll want to ensure your solution natively integrates into existing developer tools so that your team can benefit from streamlined security that’s embedded into their IDEs, CI/CD pipelines, repos and runtime environments.
Cloud Infrastructure Drift Detection
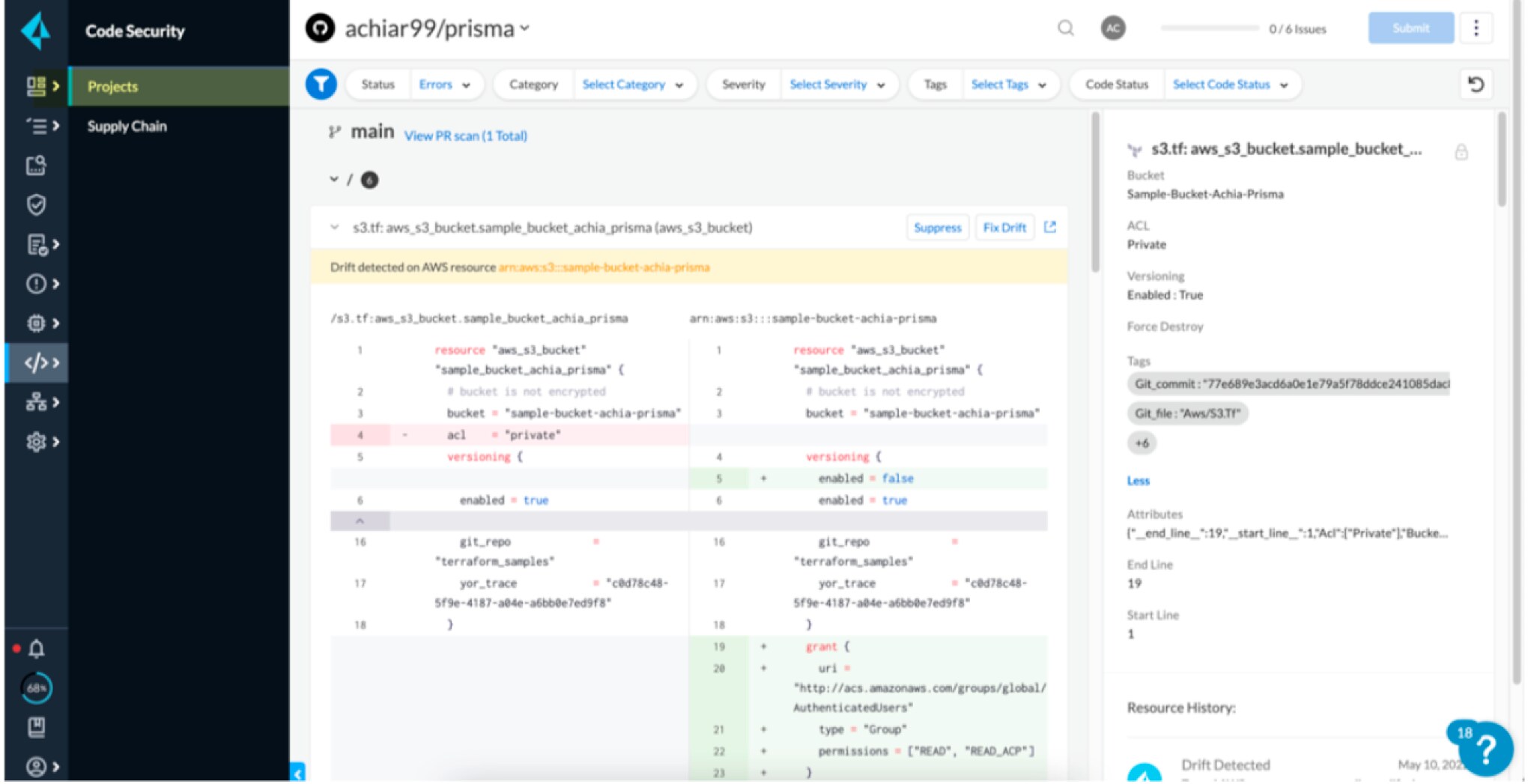
Drift happens when the configurations outlined in your IaC templates don’t perfectly match the configurations of running cloud resources. And while it negates the full benefits of IaC, drift isn’t always a bad thing.
For example, your team may need to introduce drift by making changes to running resources during a “break glass” moment, such as an in-progress security incident. However, it’s a GitOps best practice to ensure that your configuration files are the single source of truth regarding your cloud configurations. To maintain GitOps in your team, you’ll want to ensure that your DevSecOps toolbag includes a drift detection solution.
Secrets Scanning
Secrets — such as usernames and passwords — help applications communicate with other services, and developers frequently hardcode credentials to speed up development. But version control systems are not secure, so when developers commit that code to a repo, those credentials can become publicly exposed and leave your organization vulnerable to attack. That’s where secrets scanning solutions come in.
With a secrets scanner that identifies complex strings, supports custom secrets policies, includes rich context for faster risk prioritization and embeds feedback into developer tools, your team will be empowered to identify and remediate exposed credentials before they become major security issues.
Why a Consolidated Approach to DevSecOps Tools Is Key
As Gartner calls out, it’s key for leaders to recognize that only an integrated approach — one that consolidates many DevSecOps tools into one complete solution — will provide the frictionless and developer-friendly security that cloud-native organizations need to maintain their speed in the cloud.
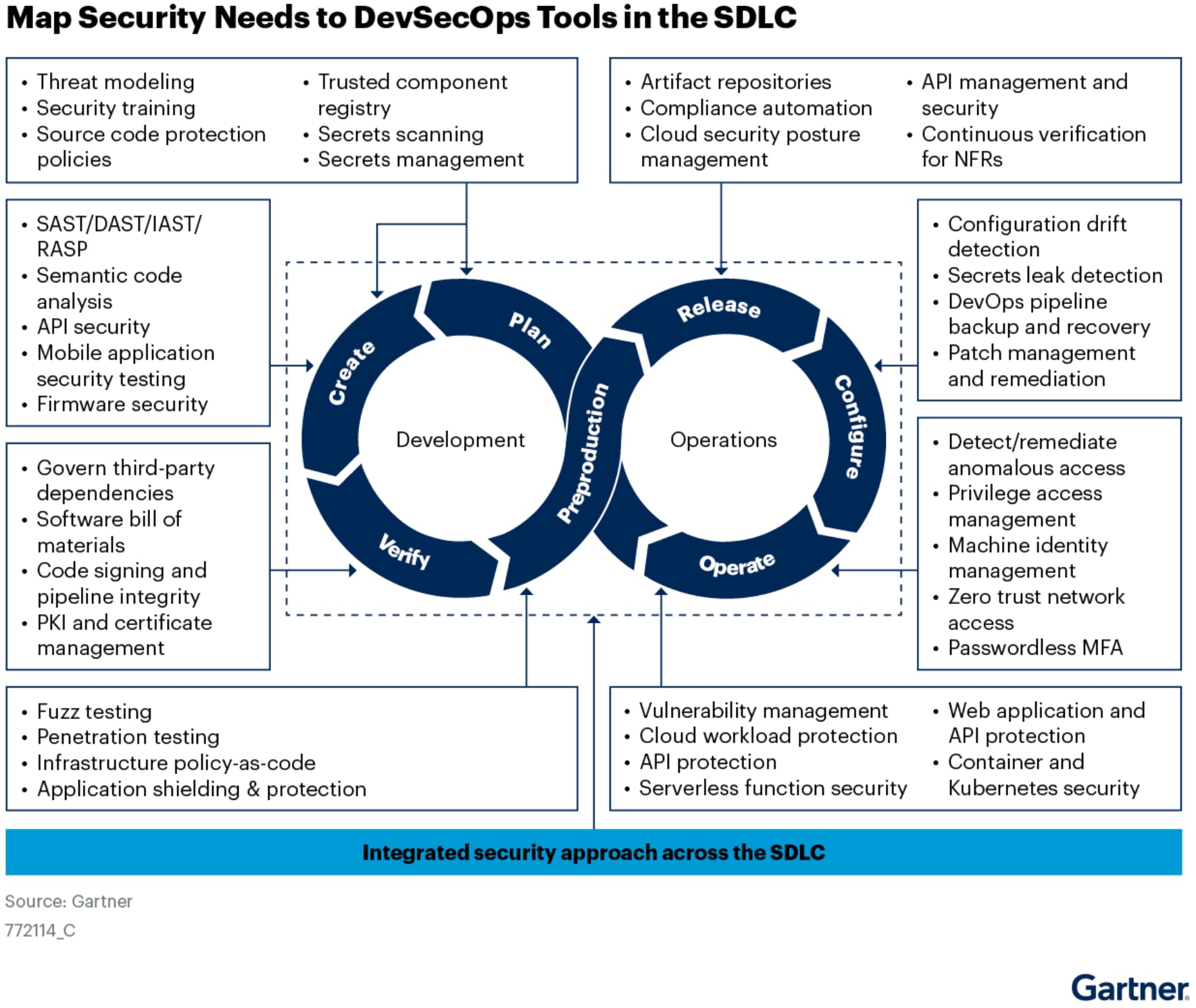
By adopting a single solution — one that consolidates all the top DevSecOps tools we discussed earlier — your organization can minimize coverage gaps and reduce the all-too-common noisy alerts when employing multiple point solutions. With an integrated and consolidated approach that leverages developer-friendly integrations, you can also empower your team with the comprehensive security and improved risk prioritization they need to streamline security and maintain their release velocity.
Learn More About DevSecOps Tools
As agile development has introduced more security use cases, the pressure is on software engineering leaders to find the best DevSecOps tools for their teams. But how do you get started with this process?
Gartner new report, How to Select DevSecOps Tools for Secure Software Delivery, provides an excellent overview of the DevSecOps market while offering practical guidance for engineering leaders to help you kickstart your vendor research.
Gartner, How to Select DevSecOps Tools for Secure Software Delivery, 16 January 2023, Manjunath Bhat Et Al.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.