Executive Summary
On Monday, January 13, 2021, the Kubernetes security team announced a vulnerability in the Kubernetes Java client that affects programs using its copy functionality.
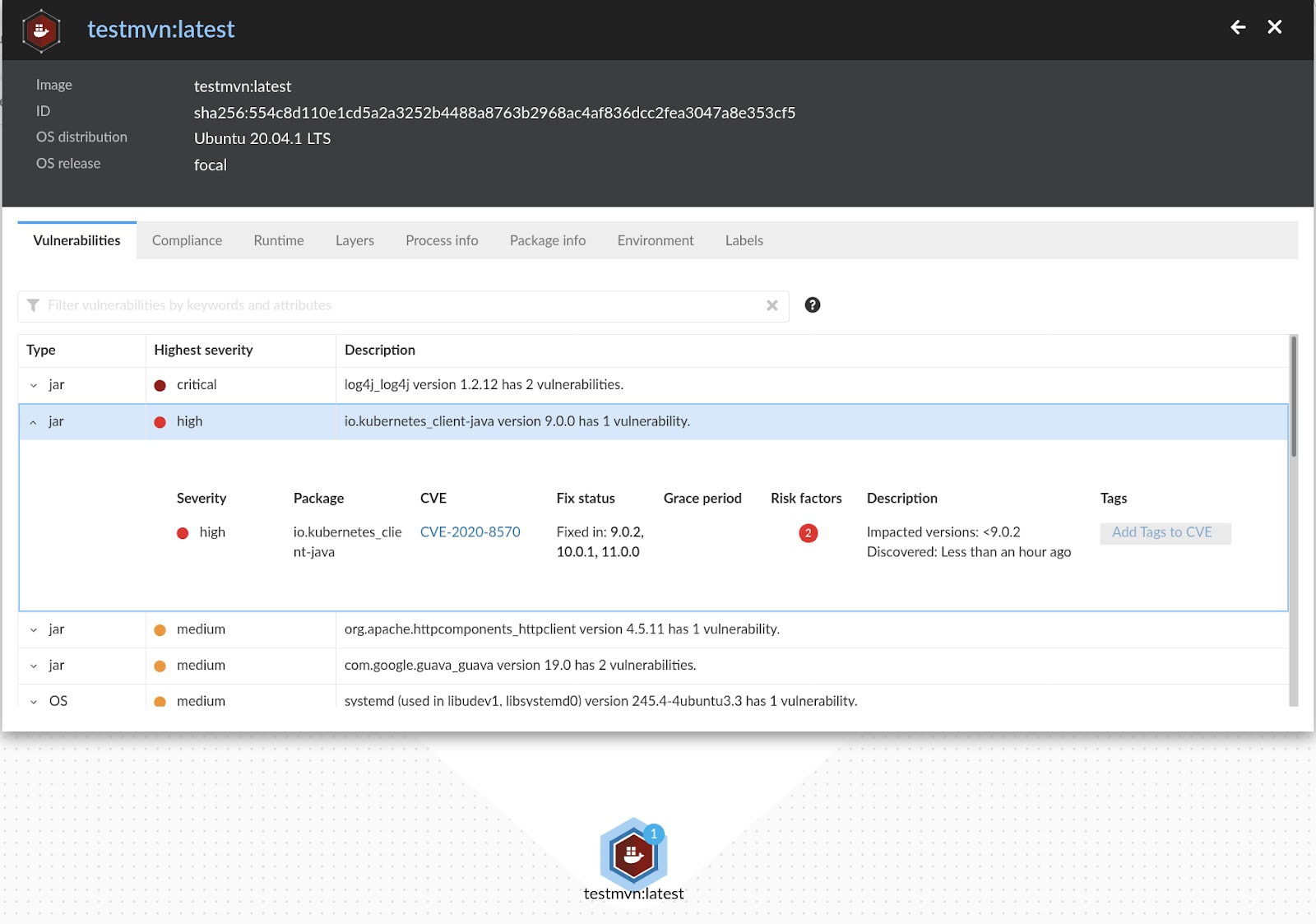
Prisma Cloud provides comprehensive vulnerability scanning capabilities to detect components vulnerable to the issue.
Same Old Trick
If you have been closely monitoring Kubernetes security for a while, you might remember multiple copy vulnerabilities in kubectl that were disclosed throughout the last couple of years. I previously wrote about CVE-2019-1002101, where attackers could use symbolic links to subvert kubectl to copy attacker-controlled files from the target pod. Additional CVEs were later assigned to further issues discovered in the same piece of kubectl code.
The vulnerability discovered in the Java client is similar to the first problem found in kubectl cp. When copying files from a container, the Java client would create a tar archive with the files, and unpack it without sanitizing file names. As a result, an attacker who has control of a pod could produce a malicious tar that would unpack malicious payload on any location in the target’s filesystem under the client’s permissions.
In other words, if the Java client would run the copy operation on a malicious or breached container, the attacker could trick it into moving any file they want to the client's filesystem. The exploitation scenario is identical to that of CVE-2019-1002101, for which I created a video proof of concept.
The Fix
If you are using the Java client and running copy with it, remedying the problem should be your priority. The vulnerability was fixed in versions 9.0.2, 10.0.1 and 11.0.0. Upgrading your Java package to one of those releases in your Project Object Model (POM) should resolve the problem.
Prisma Cloud
The Prisma Cloud team highly prioritizes accurate and timely vulnerability detection. Prisma Cloud detects vulnerabilities in Java packages. With it, you could check if you are using the vulnerable Kubernetes Java Client and which versions you are relying upon in your code. It can also produce alerts on the usage of any Java modules with high severity vulnerabilities.
Although CVE-2020-8570 is still under analysis and investigation by both the National Vulnerability Database (NVD) and Linux distribution maintainers at the time of writing, Prisma Cloud users will find that this vulnerability has already been detected by our Java vulnerability scanner.
Summary
This Java vulnerability is one of a series related to copying files from Kubernetes containers using tar. Keeping track of new vulnerabilities is a difficult task that can only be properly executed using tools that continuously scan all code components. Patching these vulnerabilities in a timely manner is a fundamental security task, and the ability to detect them before official analysis is released is a service that we work hard to provide.