Prisma Cloud customers often use Harbor, an open source registry, to store their container images as part of the application continuous delivery pipeline. In addition to storing images, Harbor also supports image vulnerability scanning via pluggable scanners, so users have full visibility into image components and can mitigate risks before deployment.
We are excited to share that Prisma Cloud, in collaboration with the Harbor community, has released an easy-to-integrate, pluggable vulnerability scanner, allowing DevOps teams to view image vulnerability results within the Harbor UI.
Here are four of the top reasons why you should consider integrating the Prisma Cloud pluggable scanner with your Harbor registry today!
1. Scan Before You Deploy
If ‘shift-left’ is not on your radar yet, it most definitely should be. It simply means adding security checks as early as feasible in application development. This gives application owners visibility into any known vulnerabilities before deployment and helps ensure that only secure and trusted images are deployed to production.
With the Prisma Cloud Harbor integration, users can easily identify vulnerable images in the Harbor registry itself, without having to log into a different console or UI. All data is available for automated security reports directly in your registry.
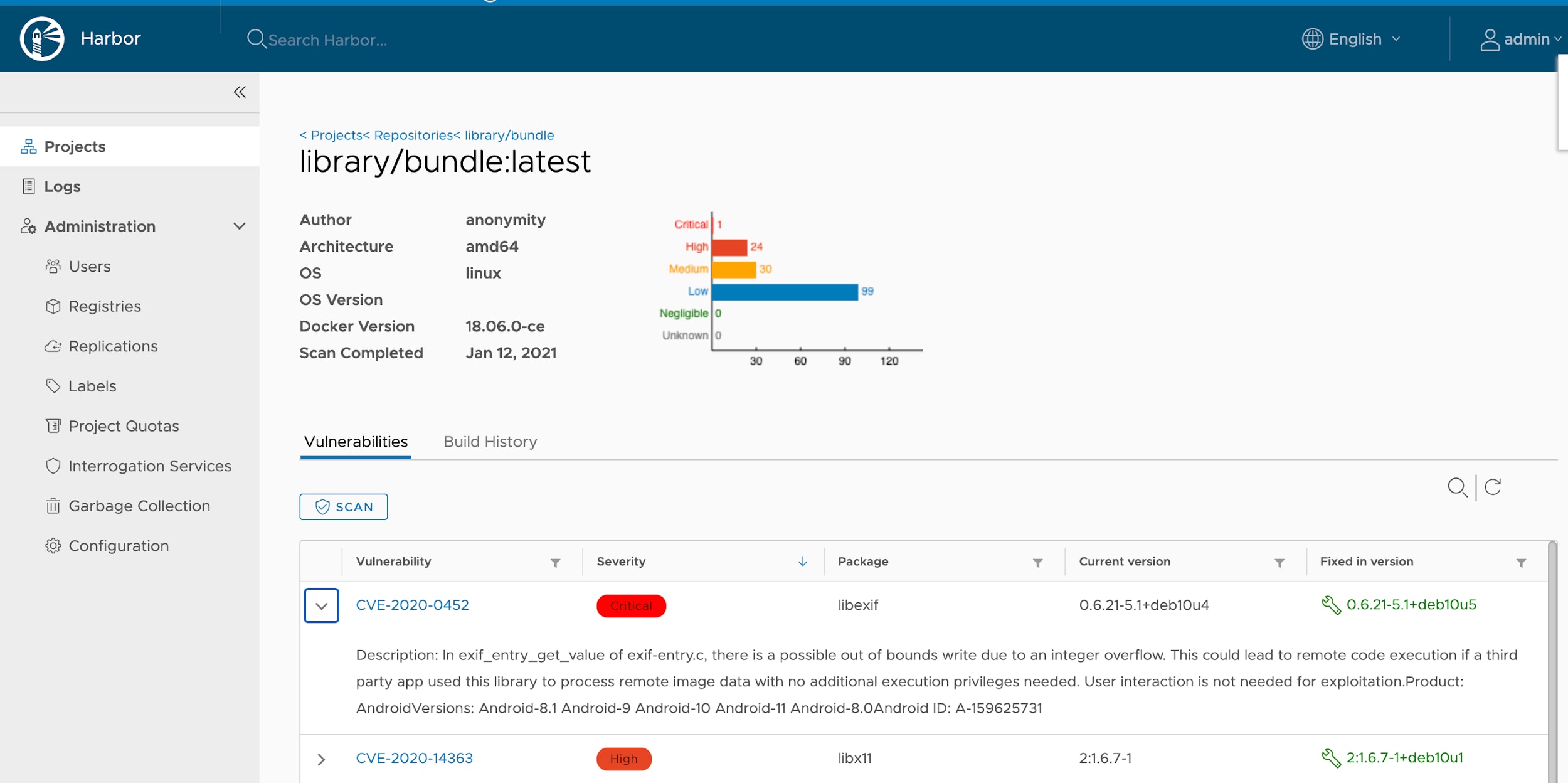
2. Continuously Updated Threat Data
Prisma Cloud image scans are powered by Intelligence Stream, a real-time threat feed that contains vulnerability data and threat intelligence from commercial providers, our Unit 42 threat research team, and the open source community. With new vulnerabilities discovered each day, this stream is continuously updated so that you automatically have the latest thread feed available for your image scans.
The scanner connects to the Prisma Cloud Console, which uses this intelligence feed to match images in your registry against the latest vulnerability data..
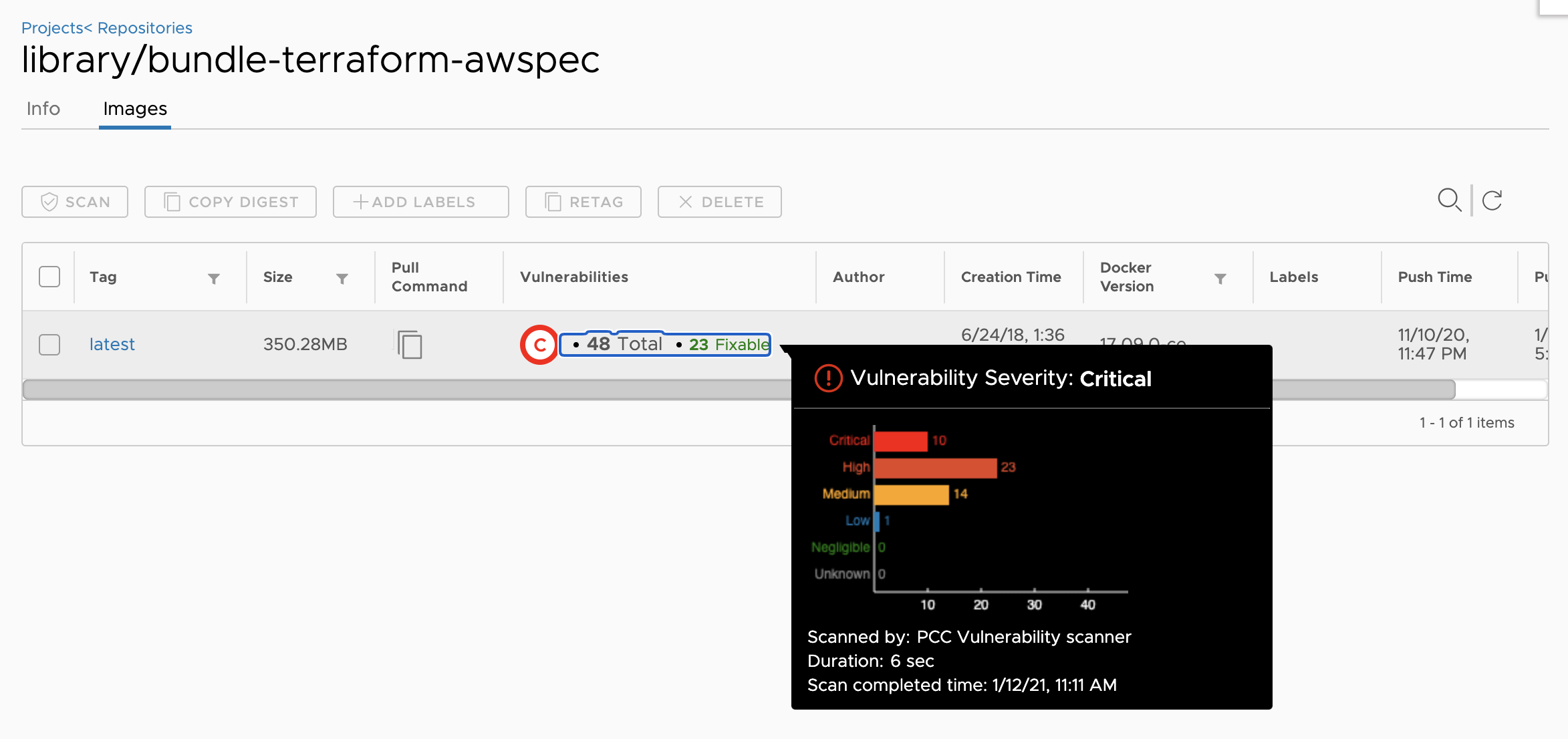
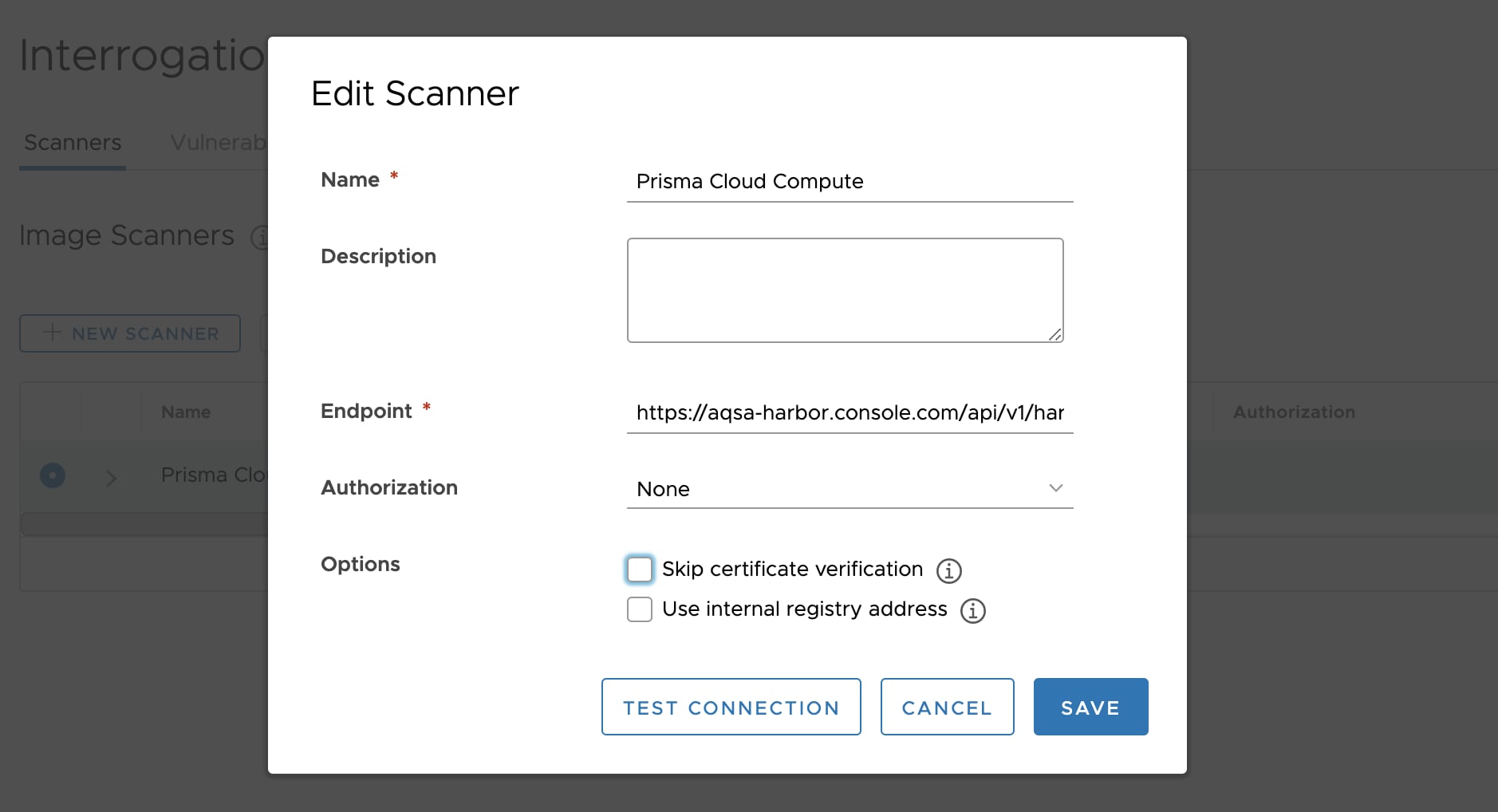
3. Ease of Integration
To integrate with the pluggable scanner, it's as easy as Ctrl+C and Ctrl+V.
Simply take these three steps -
- Add Harbor registry to your Compute Console as part of your initial setup.
- Copy the URL for the pluggable scanner
- Add it as an Interrogation service in your Harbor registry.
Your scanner is now ready to scan any and all of your repositories. You can choose to scan either specific images or all of the images in your registry.
4. End-to-End Security
Combining the capabilities from Harbor with extensive runtime capabilities in Prisma Cloud, such as blocking ‘untrusted’ images from initializing in your hosts, can provide a full end-to-end security model for your organization.
Begin Using Prisma Cloud with Harbor
For detailed set up instructions, you can check out our technical documentation for existing users. Or if you're not using Prisma Cloud yet, take a look at our product page for cloud workload protection.