The Australian Cyber Security Centre (ACSC), led by the Australian Signals Directorate (ASD), has developed a comprehensive list of strategies for mitigating cybersecurity incidents, known as Strategies to Mitigate Cyber Security Incidents.
Among these strategies, the most effective are encapsulated in the Essential Eight, a set of prioritized mitigation measures designed to help organizations protect themselves from cyberthreats.
In today’s post, we outline the Essential Eight and explain how Prisma Cloud can help users achieve compliance w.r.t Essential Eight.
The Essential Eight Defined
The Essential Eight Maturity Model, published in June 2017 and updated regularly, supports the implementation of the Essential Eight. The model is based on ASD’s experience in producing cyberthreat intelligence, responding to cybersecurity incidents, conducting penetration testing and assisting organizations to implement the Essential Eight.
The Essential Eight is a cybersecurity framework developed by the ACSC, designed to provide organizations with a comprehensive strategy for safeguarding digital assets. It comprises eight mitigation strategies formulated to strengthen layers of security and provide a solid defense against a range of cyberthreats.
Essential Eight Security Controls
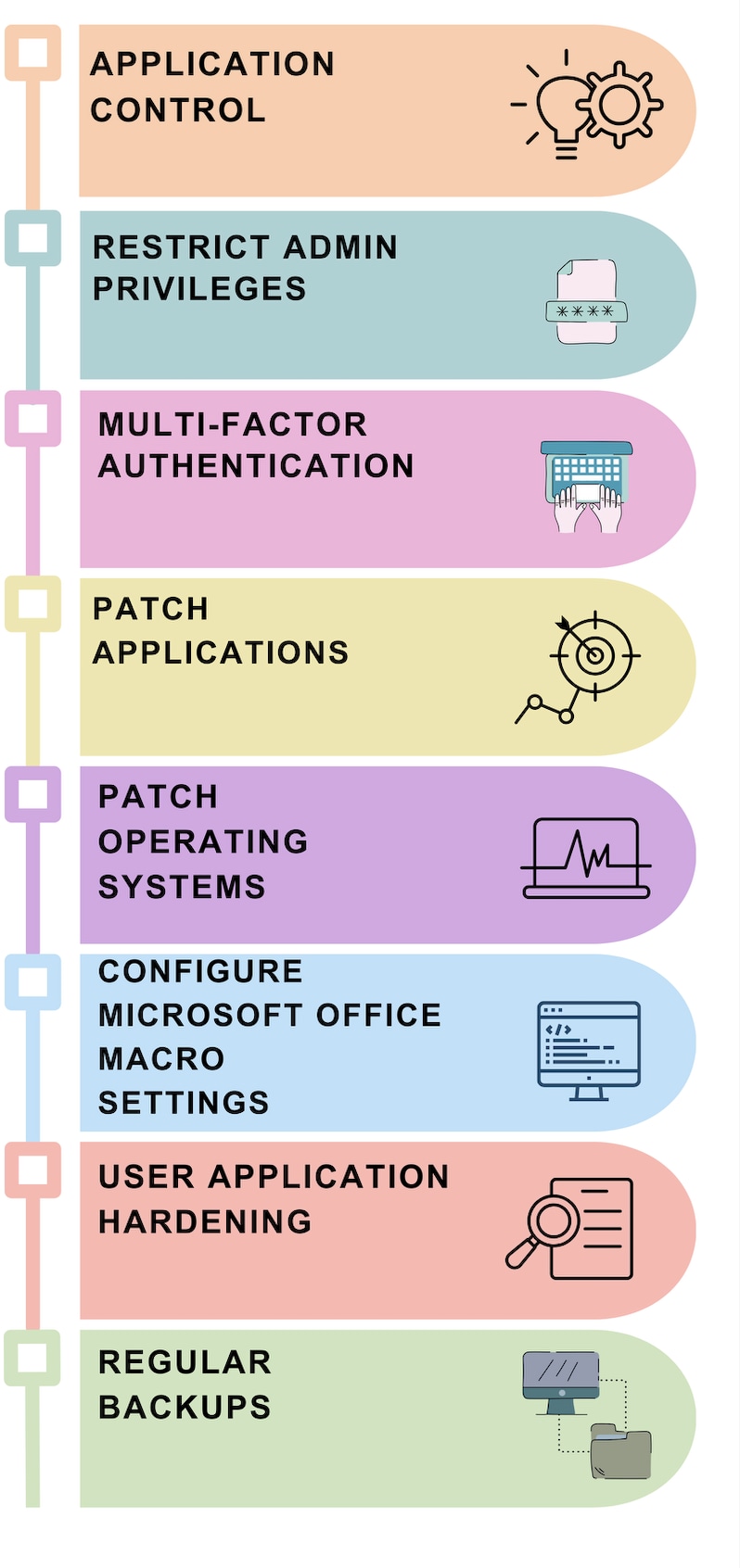
- Application Control: to control the execution of unauthorized applications and software.
- Restrict Admin Privileges: Restricting administrative permissions and access to only specific users to perform their job functions.
- Multifactor authentication (MFA): MFA ensures that even if a password is compromised, the additional layer of security will prevent attackers from gaining access to the system.
- Patch Applications: Regularly updating and patching applications to remediate security vulnerabilities and known security risks.
- Patch Operating Systems: Regularly updating and patching operating systems to remediate vulnerabilities and security risks.
- Configure Microsoft Office Macrosettings: Disabling macros by default in Office, only enabling them when necessary, can significantly reduce this risk of embedded malware.
- User Application Hardening: Restrict web browsers and email clients to core features to safeguard against vulnerable functionalities attackers can exploit.
- Regular Backups: Data backups offer a reliable method for recovering data lost or compromised due to security incidents.
Essential Eight Maturity Model
To help organizations implement the Essential Eight, four maturity levels have been established, ranging from Maturity Level Zero to Maturity Level Three. Each level, except for Maturity Level Zero, is designed to address progressively sophisticated cyberthreats, including advanced tools, tactics, techniques and targeting strategies.
When adopting the Essential Eight, organizations should determine a target maturity level that fits their needs. They should then gradually implement each level until they reach the desired level of cybersecurity maturity.
Maturity Level Zero
Level Zero indicates significant weaknesses in an organization's security measures, making them highly susceptible to attacks. At this level, the risk of data breaches or compromises in system integrity and availability is high. It highlights critical vulnerabilities in the organization's overall cybersecurity posture, leaving them exposed to potential threats.
Maturity Level One
The entry-level stage known as Maturity Level One refers to the status of organizations that have partially rolled out security measures but are not yet comprehensive or consistent. Basic defenses are in place, but they likely won’t hold up against complex cyberthreats. The primary focus at this level is countering attackers exploiting common tactics to access and control systems.
Maturity Level Two
At this intermediate level, most security strategies have been thoroughly implemented, offering improved protection over Maturity Level One. There’s still potential for enhancing consistency and effectiveness throughout the organization, though. Here, the focus shifts to combating more sophisticated attackers who invest time and resources into their attempts,including more effective tools.
Maturity Level Three
This top maturity level signifies that an organization has thoroughly implemented all Essential Eight strategies. The security measures are rigorous, consistently applied, and well-managed. At this level, the focus shifts to dealing with advanced, highly adaptable attackers with less dependency on publicly available tools and techniques. These attackers take advantage of vulnerabilities such as outdated software and inadequate monitoring to establish a foothold. They rapidly use new exploits and advanced tactics to avoid detection and deepen their access.
The Australian Signals Directorate (ASD) recommends that all Australian businesses achieve Maturity Level Three for the optimal malware threat and cyberattack protection.
How Prisma Cloud Helps with Essential Eight Compliance
As a cloud-native application protection platform (CNAPP), Prisma Cloud secures applications from code to cloud, offering comprehensive protection tailored to modern development environments. Prisma Cloud helps users navigate compliance by providing automated configuration checks that align with critical frameworks like the Essential Eight. This integration ensures that organizations not only safeguard their applications but also adhere to stringent compliance requirements, fortifying their cybersecurity defenses.
Prisma Cloud offers ACSC Essential Eight as an out-of-the-box compliance standard for all the maturity levels.
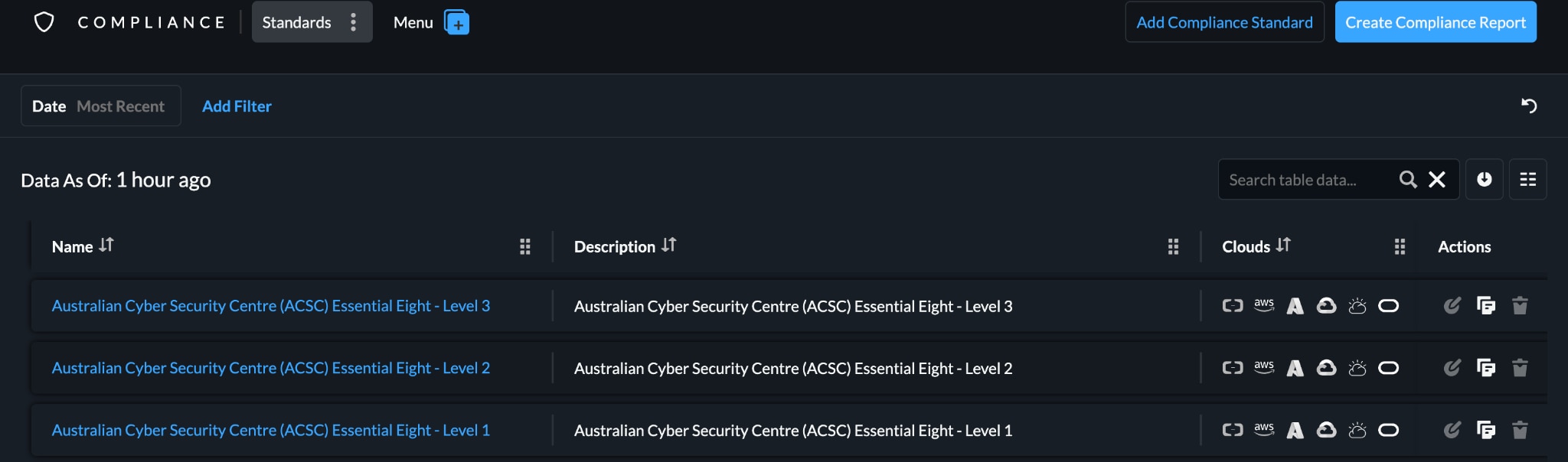
Regarding multifactor authentication guidelines from the Essential Eight, for example, Prisma Cloud provides ready-made policies that evaluate your cloud setup for potential vulnerabilities. These assessments cover accounts on all major cloud platforms, giving you thorough and reliable protection.
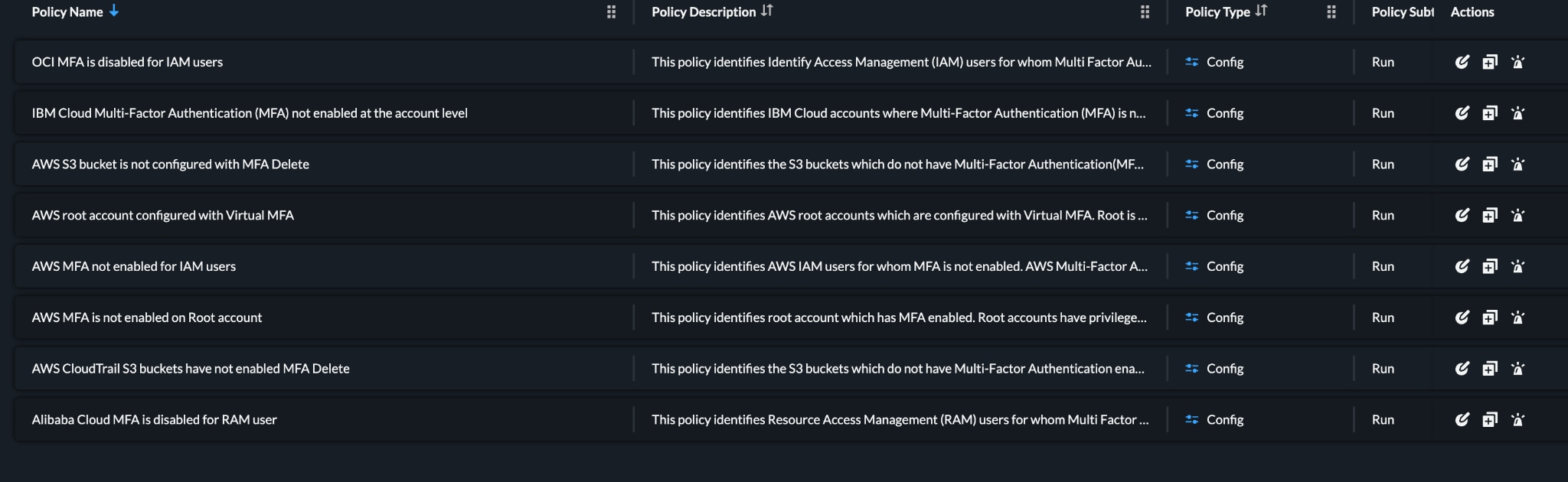
In addition to performing automated checks, Prisma Cloud offers remediation steps to resolve identified security problems. Figure 4, for example, demonstrates how to configure MFA on an AWS root account that doesn’t have it. Recommendations allow users to promptly fix issues and bolster their security defenses.
Continuous compliance doesn’t end with detection and remediation. Prisma Cloud enables security teams to generate compliance reports with a single click. The reports contain compliance posture details for frameworks supported by Prisma Cloud and are ready to handoff to stakeholders, executives and auditors.
Learn More
Prisma Cloud enables organizations to maintain strong security against diverse cyberthreats, all while streamlining cloud security management by merging multiple tools into a single Code to CloudTM platform.
Interested in seeing how Prisma Cloud can elevate your cloud security? Schedule a personalized demo.