Cloud native development presents not only new solutions for architectures, but also potential operational methodologies for infrastructure and operations (I&O) teams. Technology like microservices and containers combined with concepts such as DevSecOps (Development / Security / Operations) and ‘shift left’ security are all efforts to improve the delivery and security of your modernized applications and workloads.
They can also modernize how compliance and monitoring are performed by allowing organizations to achieve a Continuous Authority to Operate (C-ATO).
What is C-ATO?
The process of approving IT systems for use within a federal organization is called Authority to Operate (ATO). In order to obtain an ATO designation, the system owner must implement, certify and maintain appropriate security controls. Two significant challenges in this process are the continual monitoring for deviations of the certified system (a.k.a. “drift”) and the ongoing ownership of security throughout the system’s ATO designation.
Cloud native technologies like containers and microservices, and strategies like DevSecOps and shift-left security enable continuous monitoring and adherence to a system’s approved security posture—hence the term C-ATO.
How Prisma Cloud Helps Your Organization Achieve C-ATO
The underlying ATO methodology is based upon the NIST Risk Management Framework (RMF). The six steps within this framework map closely to the microservice-based development phases of build, deploy and run, as seen in the image below.
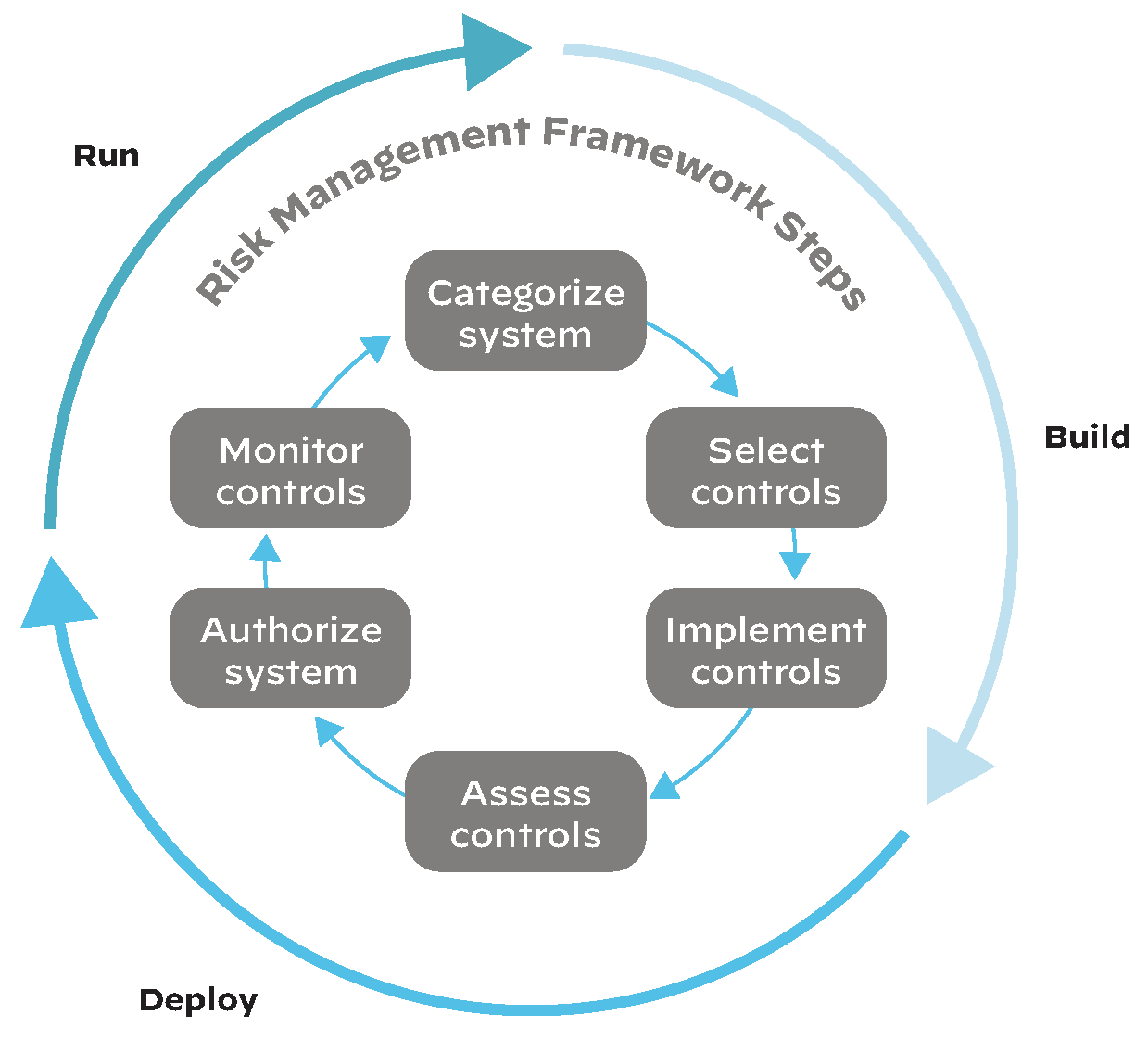
Prisma Cloud is purpose-built for secure containerized development throughout the build, deploy and run lifecycle. It allows teams to operationalize the RMF by helping create and enforce compliance policies while monitoring for vulnerabilities, entirely integrated with DevSecOps principles. Each step can be carefully monitored and controlled from the Prisma Cloud console:
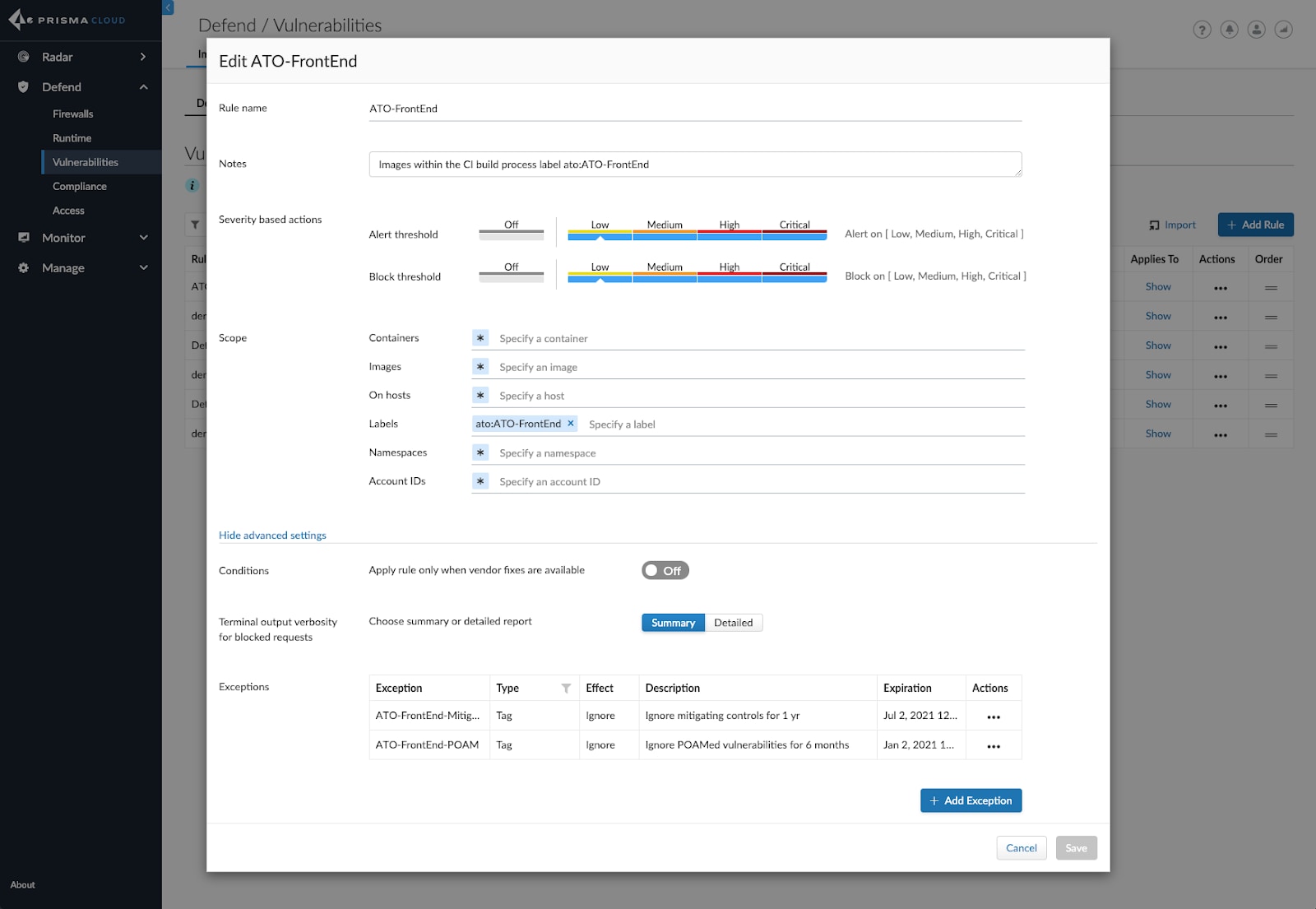
- Create defined filters to create container Collections that fall under the same ATO, making it easy to see related resources and control access.
- Use tags to associate vulnerabilities found in a Collection with approved remediation milestones and mitigating controls.
- Automatically identify new threats across the lifecycle, effectively performing continual assessments.
- Shift security left into development by alerting and/or failing builds that are non-compliant with ATO policies.
- Implement policies to block non-compliant images from instantiating as containers.
What’s next
The rapid adoption of microservices and containers prove that cloud native security is quickly becoming a standard requirement for organizations in the federal space. These concepts are being applied in other programs such as FedRAMP’s vulnerability scanning requirements for the deployment and use of containers. Conversely, the RMF described here is not just applicable to the United States Department of Defense and federal agencies, but to public sector and commercial organizations worldwide.
Palo Alto Networks is committed to offering support for developing frameworks with products and services to address our customers’ ever-changing security and compliance challenges. The functionality presented here represents only our initial support for C-ATO, with more planned for the future.
How to Begin Your C-ATO Process
Check out the data sheet that provides further detail as to how Prisma Cloud can help your organization achieve continuous authority to operate. Or you can see all of the ways Palo Alto Networks supports cybersecurity for federal governments.