When I hear the term “supply chain” in reference to software development, I immediately think about the interlocking steps linking raw materials, refinement processes and consumption. To oversimplify, the software development supply chain is similar to planting and harvesting wheat, processing the harvested wheat to provide fine-grain flour, and transporting that flour to a warehouse, and then from the warehouse to stores, bakeries or home kitchens.
The supply chain, in this context, is a process that captures the entire movement of wheat from the point of seeding in the field to finished goods like a delicious loaf of bread for consumption by people. And of course, it includes analogues to the addition of modern health and safety standards that guarantee the end-product is fit for end-user consumption.
The software development supply chain is, conceptually, much like the wheat supply chain where bread fit for consumption is the goal. In securing the software development supply chain, you have to understand four things:
- Where do my software components come from? (i.e. How is the wheat planted and nurtured?)
- Do my software components have vulnerabilities or insecure configurations? (i.e. How has the wheat been processed, and what ingredients have been added to flavor the bread?)
- Does the software meet compliance requirements? (i.e. Is the wheat FDA-approved, and is the bread free of dairy product residues?)
- How do I enforce a manageable software governance process without losing speed? (i.e. How can I ensure workers followed FDA regulations in making the bread, without slowing down the entire bread production process?)
Securing the Software Development Supply Chain
Using those same four concepts, we’ll use the example of Prisma Cloud to describe how Palo Alto Networks secures the software development supply chain.
Where do my software components come from?
Prisma Cloud provides packaged information about images so security teams can see what components their developers are using to build applications.
Do my software components have vulnerabilities or insecure configurations?
Prisma Cloud provides vulnerability scanning for container and serverless images in CI/CD and registry, so DevOps can identify and remove vulnerabilities before those images are spun up as containers and serverless in the runtime environment.
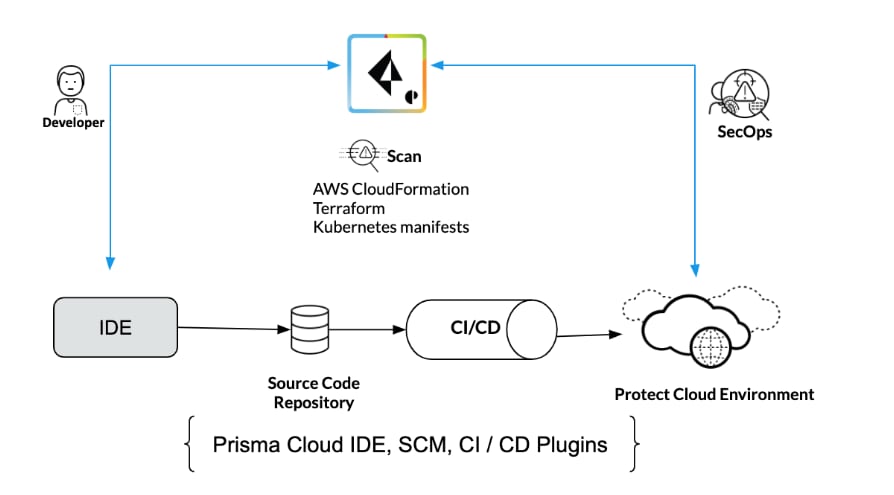
Prisma Cloud also provides configuration scanning for infrastructure as code (IaC) templates (e.g. HashiCorp Terraform, AWS CloudFormationTemplate, Kubernetes app manifest YAML) while they are under development in IDE (e.g. IntelliJ, VSCode), SCM (e.g. GitHub, GitLab) and CI/CD (e.g. AWS CodePipeline, Azure DevOps, GCP Cloud Build/Spinnaker, Jenkins and CircleCI) so developers and DevOps can identify and fix misconfigurations before these infrastructure and Kubernetes applications are deployed in runtime.
Does the software meet compliance requirements?
Embedding security checks using Prisma Cloud early in the CI/CD pipeline is crucial for reducing the attack surface area and reducing the mean time-to-detect and response to events.
IaC templates drive the automation of provisioned cloud resources. Any insecurity in these assets amplifies risk. Detecting threats and remediating them before deployment mitigates the possibility of insecure configurations.
Prisma Cloud can help developers and DevOps detect known vulnerabilities in their OS packages or container image files that violate CIS compliance standards. This improves the overarching security posture of software applications.
How do I enforce a manageable software governance process without losing speed?
Context-rich alerts can be sent to automated incident response and security orchestration tools such as Demisto. And within Demisto, build/use playbooks link to those alerts for an automated response.
Demisto focuses on the most important incidents first so that a manageable software governance process can be enforced without losing speed.
Additional software security protection and enforcement
To circle back to our original supply chain analogy: In order for people to enjoy a delicious loaf of bread, the wheat supply chain needs to be closely monitored, including follow-through to ensure relevant health and safety standards are met. If any contamination should enter the wheat supply chain, modern health and safety regulators will be notified when standards are not met, and resulting notifications will result in severe financial penalties as well as unwanted lawsuits to ensure “safe bread.”
In the case of the software development supply chain, security should be a high priority for all developers, DevOps and security teams. Modern security breaches are sophisticated and can damage or disrupt development operations, resulting in massive financial penalties or unnecessary charges, an inefficient delivery schedule and a potential theft of intellectual property.
Prisma Cloud protects the software development supply chain from cyber threats on-premises or in the cloud. While cyber threats cannot be completely avoided, software development supply chain security can provide a more secure, efficient environment for developing code that can recover rapidly from disruptions.
In the final analogy: the wheat can become bread, without putting any consumers at risk. Not a bad place to be!
To learn more about how Prisma Cloud protects the full software development supply chain watch our free on-demand digital summit, Cloud Native Security Live.