Data is currency for modern businesses. Organizations use data analytics to make decisions about new products and services or to provide better customer experiences. As companies collect, store, transmit, process, and use more data, they increase their use of the cloud. Additionally, cloud-based technologies enable workforce collaboration across geographic regions as well as between internal and external users.
Complex IT environments often use a combination of on-premises, cloud, multicloud, and hybrid infrastructures, meaning that they store vast amounts of sensitive data in multiple locations. Often, organizations lose visibility into where sensitive data resides, who uses it, and whether it remains protected. In response, malicious actors have turned their attention to the cloud, looking to steal sensitive corporate and personally identifiable information (PII).
With an estimated 60% of enterprise data stored in the cloud, understanding cloud data security is fundamental to mitigating data breach, reputation, financial, and compliance risks.
Understanding Data Security
Data security includes the technologies and processes an organization uses to protect sensitive data both on-premises and in the cloud.
Sensitive information includes corporate and non-public personal information (NPI), including:
- Intellectual property
- Names
- Birth dates
- Government identification information, like social security numbers and driver's license information
- Physical address
- IP address
- Biometric information
Further, as legislative bodies respond to ransomware attacks and data breaches by enacting new data protection laws, some best practices have emerged, including:
- Data classification
- Data anonymization and pseudonymization
- Data encryption
- User access controls
What Is Cloud Data Security?
Cloud data security refers to the technologies and controls that discover, classify, and protect all data in the cloud to mitigate risks arising from data loss, misuse, breaches, and unauthorized access. This includes:
- Detecting and classifying structured and unstructured data
- Implementing and monitoring access management controls at the file and field levels
- Identifying storage locations for structured and unstructured data
- Data transmission flows
- Encryption configurations
Data security is a fundamental component of an organization’s cybersecurity strategy.
Why Is Sensitive Data Protection Important in Cloud Computing?
As organizations use more data, they need to protect its confidentiality, integrity, and availability. Cloud computing models enable collaboration and analytics but present unique challenges.
Data Integrity
Cloud computing and analytics enable organizations to make data-driven decisions. According to the global IDC survey data:
- 83% of CEOs want a data-driven organization
- 74% of senior executives require data in decision making
Organizations need to protect sensitive information to ensure the integrity of the data that their analytics models use. To do this, they need to mitigate risks associated with unauthorized access, including internal users who can make changes to data.
Data Availability
As organizations build out their data cultures, breaking down data silos becomes more important. The cloud enables this collaboration, but organizations need to ensure that they protect sensitive information’s availability, like ensuring no one accidentally deletes a data set.
Data Confidentiality
With hybrid and multicloud environments, monitoring data use becomes even more challenging. As data travels between services, organizations need to worry about application programming interface (API) configurations. By protecting sensitive information, organizations prevent data loss and leaks that compromise confidentiality.
What Are the Benefits of Cloud Data Security?
While protecting sensitive data is important, the same practices, controls, and processes benefit companies, too.
Mitigate Data Breach Risk
Data security controls reduce a cyberattack’s success rate. For example, implementing data access controls makes it more difficult for attackers to get to the information. Other data controls, like encryption, make the data unusable and unreadable if attackers succeed.
Protect Brand Reputation
Brand reputation generates customer interest and provides insight into financial performance. The State of Corporate Reputation and Business Performance Report found that 72% of business leaders believe reputation will be a bigger driver of business performance than margin over the next five years. Every data breach that makes the news undermines a company’s brand reputation. By mitigating these risks, organizations protect themselves.
Enhance Customer Trust
Today’s customers consider a company’s data privacy policies and data protections as part of their buying decisions. Customer trust starts with an organization’s privacy policies, but it also incorporates brand reputation.
According to McKinsey, consumers want companies to provide transparency around digital-trust policies finding:
- 85% of respondents said knowing a company’s data privacy policies is important before making a purchase
- 46% of consumers often or always consider another brand if they are unclear about how a company will use their data
- 53% of consumers make online purchases or use digital services only after making sure that the company has a reputation for protecting its customers’ data
Cloud data security enables organizations to implement data privacy controls that ensure safe customer data sharing.
Avoid Fines and Fees
Data privacy and protection law noncompliance leads to costly fines and legal fees. For example, a company that violates the General Data Protection Regulation (GDPR) can face fines up to €10 million, or 2% of its worldwide annual revenue. These fines apply to violations which may not be cybersecurity incidents. For example, one of the first GDPR fines was levied against a Portuguese hospital for allowing too many people to have too much access. Additionally, companies often face expensive lawsuits in a data breach’s aftermath.
Who Is Responsible for Cloud Data Security?
Most cloud service providers follow the shared responsibility model for cloud security. At a high level, the cloud provider is responsible for the security of the cloud while their customer remains responsible for the security of applications and data in the cloud.
Each service provider and “as-a-Service'' model defines the shared responsibility differently. However, customers are typically responsible for:
- Information and data
- Application logic and code
- Identity and access
- Platform resource configuration
Infrastructure as a service (IaaS) and platform as a service (PaaS) implementations assign each party additional responsibilities, and these are dictated by the contract.
6 Cloud Data Security Challenges
For every benefit that cloud environments provide, they add a data security challenge. Cloud environments are inherently code-based, creating different risks.
Expanded Attack Surface
Cloud environments are naturally flexible and scalable, meaning that organizations can add new applications or workloads easily. Often, people deploy cloud assets outside of the organization’s security policies, creating misconfiguration risks. Further, IT and security teams may not know that these assets exist since traditional asset management tools lack real-time detection capabilities.
Complex Environments
Modern IT environments may include:
- One or more public cloud provider
- On-premises servers
- SaaS applications
- Virtual machines
- Containers
- Instances
As data travels between these assets, organizations find discovering all sensitive data and mapping data flows challenging.
Virtual machines, containers, and cloud instances pose new and unique challenges. As IT environments add more layers of abstraction, data security protections evolve, requiring security teams to focus on discovering these assets and maintaining secure configurations.
Divergent Permissions
The majority of organizations have multicloud environments. Maintaining situational awareness and proper security practices poses a challenge because they lack data normalization across logs. Although vendors provide monitoring tools, each provider uses different field names and varies the number of fields in the logs. Without data normalization in a centralized location, organizations struggle to gain visibility across disparate:
- Permissions
- Log formats
- Network configurations
- Encryption configurations
Dynamic Environment
IT departments can create and delete volumes of cloud assets rapidly. While the cloud’s flexibility and scalability enables organizations to save money, consistently applying security policies becomes difficult. Security tools built for traditional environments lack real-time policy enforcement capabilities. Cloud asset configurations can fall out of compliance, weakening the organization’s data security posture.
Shadow Data
As engineering teams leverage cloud database technologies, they duplicate data. For example, they may have DB backups generated with sensitive information that were moved to the cloud and never deleted. Since most tools fail to discover this data, organizations are left with shadow data that can lead to a data breach.
Regulatory Compliance
Implementing data security controls is challenging. All the same, increased regulatory focus on data privacy means that organizations have to maintain their data security posture and document their activities. Inconsistent access permissions, configuration drift, and visibility issues lead to compliance violations and audit failures.
Best Practices for Implementing Cloud Data Security
By following best practices for data detection and classification, you can implement controls and technologies that help secure data.
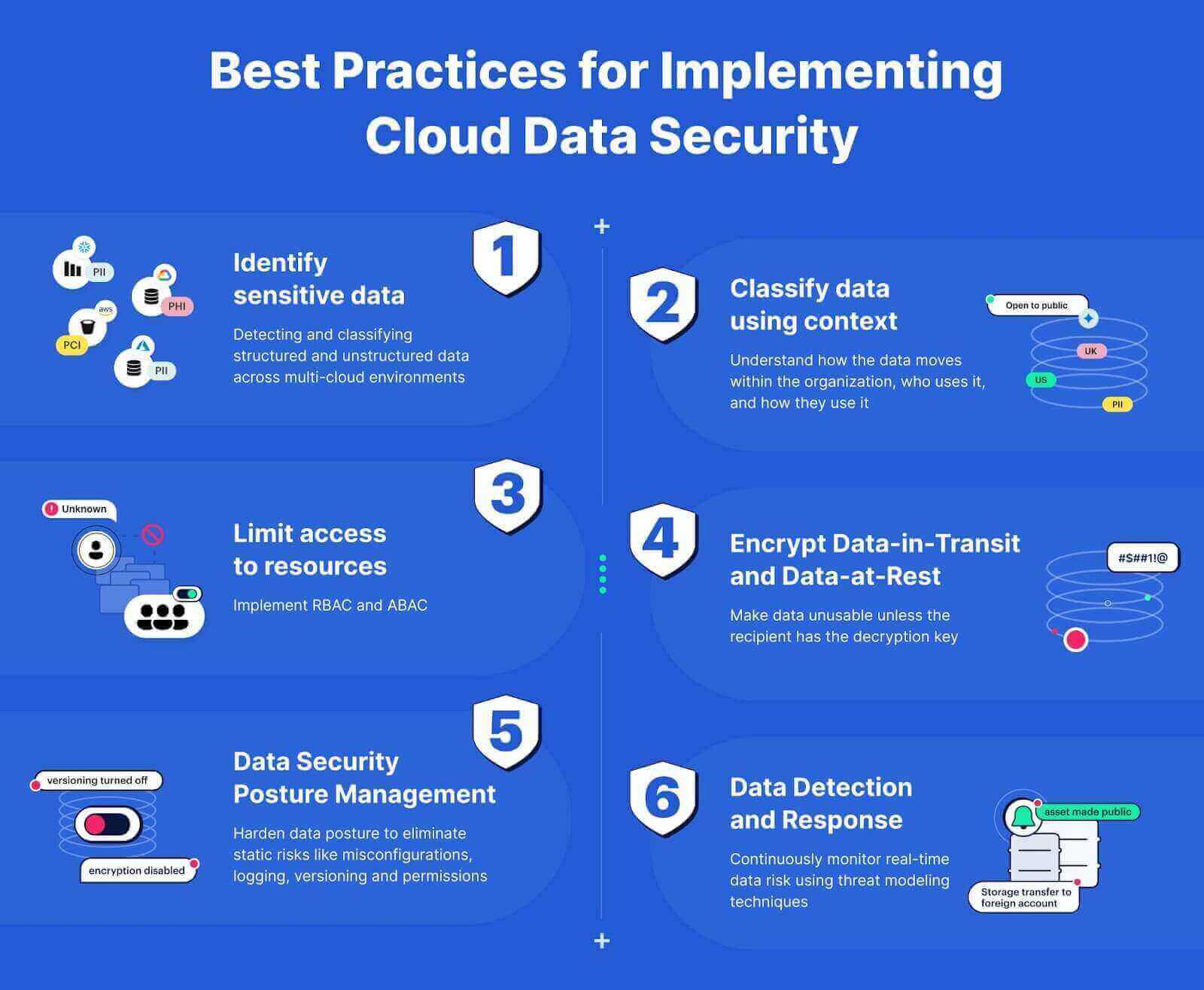
Identify Sensitive Data
Before you can secure data, you need to identify what sensitive information you have and where it resides. To gain visibility into critical data and static data risk, you need to discover and classify structured and unstructured sensitive data across:
- Public cloud platforms, including storage like S3 buckets, RDS, and EFS
- Virtualization environments
- Data analytics platforms, like Redshift
- Databases as a Service, like Snowflake
- Shadow data
Classify Data Using Context
Once you know where sensitive data resides, you need to classify it according to:
- Type
- Sensitivity level
- Governing regulation
Your classification process should include how the data moves within your organization, who uses it, and how they use it.
Limit Access to Resources
With all your data identified and classified, you can set user access permissions. You should limit access as precisely as possible, granting each user the least amount of access necessary to complete their job function. You should use a combination of:
- Role-based access controls (RBAC): permissions assigned to someone based on their role in the organization, like job function or department
- Attribute-based access controls (ABAC): permissions that incorporate context, like user device security, geographic location, or time of day
Encrypt Data-in-Transit and Data-at-Rest
Nearly every compliance mandate requires organizations to encrypt data-at-rest and in-transit. Encryption makes data unusable unless the recipient has the decryption key. If someone gains unauthorized access to it, they won’t be able to read it.
Implement Data Loss Prevention (DLP)
As users collaborate, you can experience data leakage or loss, meaning that someone shares data outside the organization when they shouldn’t have. Data loss can be a result of:
- Accidental sharing during collaboration
- Threat actors compromising systems and networks to steal data
- Malicious insiders downloading information
You should look for DLP solutions that implement near real-time data risk detection across multicloud environments as information travels between clouds and applications.
Harden Data Posture
As people use data, you need visibility into how they access different datasets so that you understand the evolving nature of data flows.
You can use data security posture management (DSPM) to identify static risks like:
- Misconfigurations, including disabled logging
- Encryption being disabled
- Versioning issues
- Permissions
Continuously Monitor Real-Time Data Risk
Since cloud environments are dynamic, your data risk posture continuously changes.
Additionally, you need to use threat modeling and threat intelligence for real-time risk detection that includes:
- Newly created data assets
- Newly discovered threats
- New attack methodologies impacting your cloud services providers
Create a Single Source for Continuous Monitoring, Remediation, and Documentation
For comprehensive visibility that documents your data security posture, you should aggregate all monitoring and remediation in a single location. With a comprehensive data security posture management (DSPM) and data detection and response (DDR) platform, you gain:
- A data-centric view of your cloud data assets, including content, identities and access, and data vulnerabilities and exposures
- Alerts that prioritize risk based on real-world attack methods for visibility into exploitability
- Automated remediation of data access violations connected to business workflows
- Audit documentation based on cloud, geographic region, and compliance standard
Learn More: Cloud Data Security
While complex and challenging, securing data stored in the cloud is critical. To remain competitive, companies need to use cloud technologies. But they need to mitigate data breach risks to protect brand reputation, customer loyalty, and financial stability.
Leveraging technologies that move at the speed of the cloud, enhance security while reducing the operational burdens that IT and security teams face. Prisma Cloud is the first vendor offering both data security posture management (DSPM) with data detection and response (DDR) capabilities to meet today’s organizations’ needs around multicloud data security. Our ability to improve existing security controls is a game changer in reducing the impact of data breach.
Don't miss the insights from the State of Cloud Data Security 2023 report. Uncover key findings from our analysis of over 13 billion files and 8 petabytes of data stored in public cloud environments.