Version 3.0 of Checkov — Prisma Cloud’s open-source infrastructure-as-code (IaC) security scanner — is now available. Checkov 3.0 is a result of over 11 thousand new commits since we released Checkov 2.0 and includes upgrades, such as improved graph policies, deeper Terraform scanning and support for new frameworks.
Checkov enables developers to identify and remediate misconfigurations in infrastructure-as-code files across platforms, such as Terraform, Kubernetes, CloudFormation and Ansible. Since its launch in late 2019, Checkov has been downloaded over 80 million times, making it one of the most popular open-source IaC security scanners.
Let’s dive into the latest upgrades to Checkov.
Expanded Graph Policies
Checkov was the first infrastructure-as-code security tool to introduce graph policies, emphasizing the importance of context between objects when considering security posture. Checkov 3.0 builds on that initial investment in a graph-based approach and includes over 800 new graph policies on top of the 1,000 policies we added 2 years ago.
Checkov now has over 3 thousand total policies customizable with inline suppressions. You can also create custom policies and leverage Checkov’s new baseline feature, which enables you to set a baseline for a directory — not an individual file — so that future runs skip all existing misconfigurations.
To use the baseline feature, first use checkov -d path/to/directory --create-baseline to set a baseline file .checkov.baseline in the scanned directory. For later runs, use checkov -d path/to/directory --baseline path/to/directory/.checkov.baseline so that you’re only checking for newly identified misconfigurations.
Power to the Policy Definitions
Along with the new out-of-the-box policies, we’ve improved the power and usability of Checkov’s policy language with new operators — 36, in fact — to make policies simpler to write. Let’s look at a few of these operators in more detail.
“SUBSET” allows for a huge reduction in nested and logic. Additionally, all operators now support JSON paths by appending jsonpath_ to the operator to get even more complex in your patterns.
Here's an example of a YAML-based policy in Checkov:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
metadata: id: "CKV2_AWS_49" name: "Ensure AWS Database Migration Service endpoints have SSL configured" category: "NETWORKING" definition: or: - and: - cond_type: "attribute" resource_types: - "aws_dms_endpoint" attribute: "endpoint_type" operator: "equals" value: "source" - or: - cond_type: "attribute" resource_types: - "aws_dms_endpoint" attribute: "engine_name" operator: "subset" value: - "s3" - "azuredb" - cond_type: "attribute" resource_types: - "aws_dms_endpoint" attribute: "ssl_mode" operator: "not_equals" value: "none" |
‘Jsonpath_’ is powerful because the attributes can also be expressions that allow a single policy to cover the complexity of cloud environment objects. Let's look at an example policy that uses ‘jsonpath_’:
|
1 2 3 4 5 6 |
- cond_type: "attribute" resource_types: - "aws_security_group" attribute: "ingress[?(@.to_port == 443 & @.from_port == 443)].cidr_blocks[?(@ == '8.0.4.19/92')]" operator: "jsonpath_equals" value: 8.0.4.19/92 |
Read Checkov’s documentation to learn more about the new operators.
Deep Terraform Scanning
Checkov started out as a Terraform security scanner, and while it now supports a wide range of infrastructure-as-code frameworks, we’ve continued to improve its Terraform security capabilities based on community feedback.
Checkov now provides the deepest level of Terraform security scanning available. With Checkov 3.0, you get:
- Terraform JSON scanning across all Terraform policies
- Deep analysis and resolution of Terraform for_each and dynamic code blocks
- Fetching and scanning of dependent Terraform modules
- Terraform plan scanning
Checkov also has a new deep analysis mode that works with all the above features. With deep-analysis, you can use a plan file and the original Terraform to fully resolve any possible variable, block or complex configurations.
Upgraded Secrets Scanning
Checkov helps you identify and remove exposed credentials — such as API keys and access tokens — early in the software development lifecycle.
With our upgrades to its secrets security capabilities, Checkov now supports a wider range of known-format secrets. Checkov also features improved “random secret” detection and includes valid key testing with an API key to ensure it only alerts on valid credentials.
Expanded Support for IaC Frameworks
In this latest upgrade to Checkov, we also sought to extend support for a variety of infrastructure-as-code frameworks. This includes some you probably wouldn’t even call infrastructure as code (we’re looking at you, Ansible).
Checkov 3.0 now supports:
- Continuous integration (CI) pipeline tools, such as Bitbucket Cloud Pipelines and Jenkins
- Bicep in Azure
- Kustomize
- Ansible
- Kubernetes graph checks
AI and Checkov
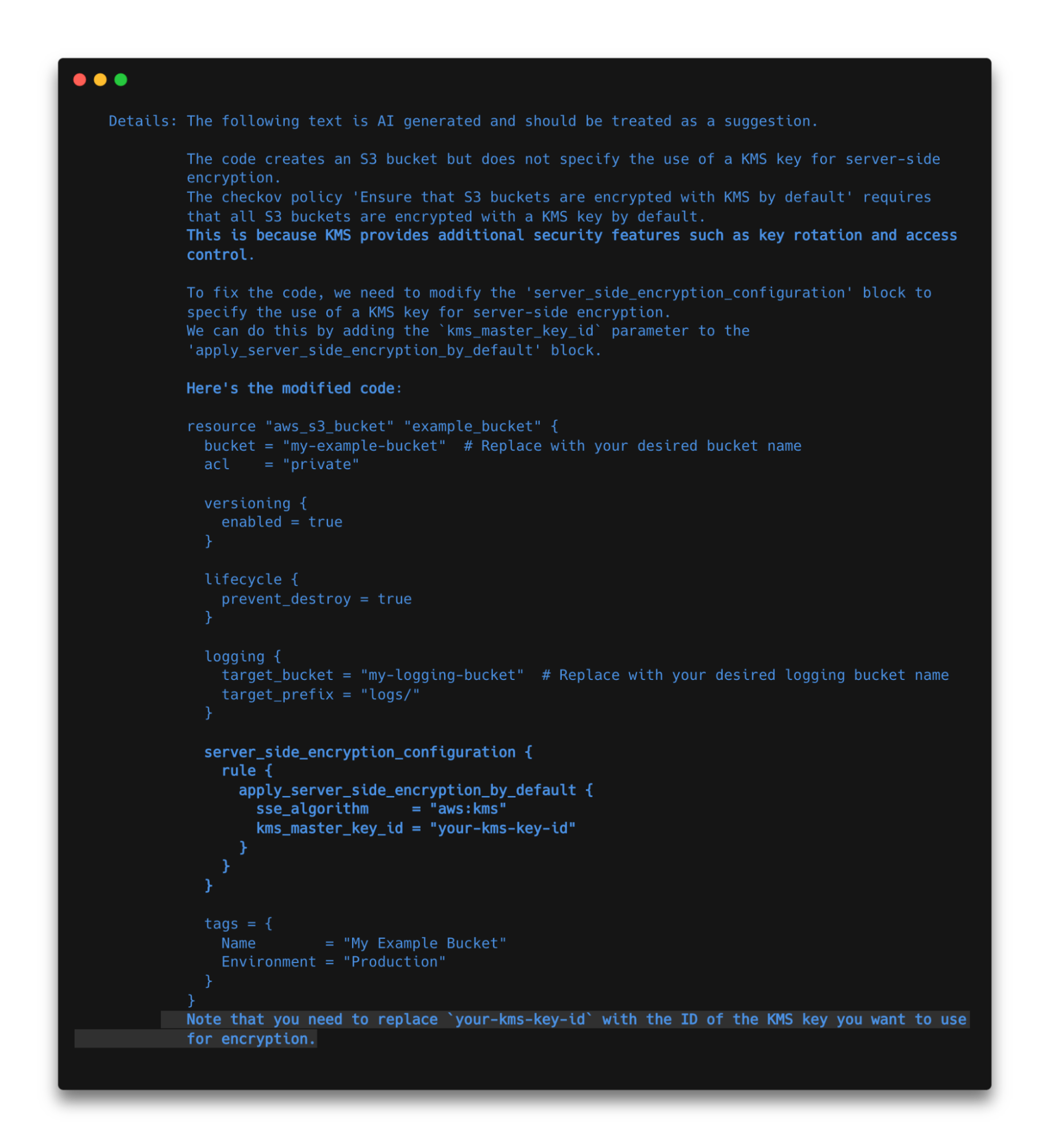
It’s 2023, so we obviously had to upgrade Checkov with AI. When you use Checkov and ChatGPT — via an API token — Checkov provides detailed CLI output with suggested code fixes to help streamline your workflow.
Getting Involved in the Community
We’re excited to see how far Checkov has come since 2019, and we can’t wait to see what the future of infrastructure-as-code security will bring. As you explore Checkov, please join our #CodifiedSecurity Slack channel to ask questions, share ideas and connect with our awesome dev team.
And if you’re looking for more information on how to adopt infrastructure-as-code security in your organization, download the step-by-step guide: Operationalize Your Infrastructure-as-Code Security Program. In it, you’ll learn how to get started with IaC security, roll out your program and iterate for success.