In the last five years, most organizations have begun to move at least some operations away from traditional data centers in favor of adopting cloud infrastructure-as-a-service (IaaS) from major cloud service providers (CSPs). As this adoption increases, securing these services has become a focal point, especially as organizations determine how to internally manage the shared responsibility model between CSPs and users.
One of the most prevalent services to experience breaches has been cloud object storage. Object storage is used to store and retrieve data, using a web interface or programmatically through APIs. The good news is that these breaches are often preventable. Let's look at some of the top breaches that have happened in the last few years, and how to prevent similar incidents.
Popular Cloud Storage Services
First, we should note that there are several popular cloud storage services available. Amazon Web Services (AWS) calls its service Simple Storage Service (S3). Microsoft Azure has Azure Blob Storage. And Google Cloud simply calls its product Cloud Storage.
In this article, most of the examples of data breaches are related to Amazon S3, though the logic behind the breach and the reasons that cause them are equally applicable to other CSP storage services.
Newsworthy Breaches of Cloud Storage
Cloud storage services have been a common target for bad actors over the past several years. Here are examples of well-known incidents across industries.
Financial Services
In mid-2019, an outside individual gained unauthorized access to a large financial services company's storage and obtained personally identifiable information (PII) of individuals who had applied for credit cards. According to the company, the individual accessed applications from consumers and small businesses, which included data like names, addresses, zip codes/postal codes, phone numbers, email addresses, dates of birth and self-reported income.
The breach happened because the company had misconfigured its AWS servers, identity access management (IAM) services and S3 services; which allowed privilege access to attackers.
Social Networking/Media Services
A social networking site also had its data exposed through an S3 bucket, one that was configured to allow anyone from the public to download files. The database backup contained columns with user information and passwords. As a result, the company faced intense public scrutiny over its data handling practices, and have reduced third-party access as a result.
Payment Services
A third-party working for a well-known payment vendor also misconfigured an S3 bucket, exposing millions of US-based customers’ names, addresses, account details, and PINs. The bucket was again configured to allow public access, and the data was freely downloadable. Even though there was no theft and data was less sensitive, the noteworthy event still caused reputational damage.
Consulting Services
A technology consulting firm performed a security assessment on both its internal and external computer systems. The assessment discovered that over 60,000 files were publicly accessible on AWS S3, and many of the files contained unencrypted passwords and credentials of US Government systems. Luckily the firm found that no data had been compromised, and quickly corrected the misconfiguration. But again, the reputational damage had been done.
Professional Services
A large professional service company suffered a breach of client data due to a misconfigured AWS server. It was using unsecured S3 storage buckets where the data was easily available for download. The largest exposed server contained more than 137 GB of data, including databases of credentials and other customer data. The server was misconfigured in a way that anyone who knew or could guess the individual bucket addresses could download the data without a password. It was revealed that some of the data were posted on the dark web by hackers.
Common Causes of Cloud Storage Breaches
Knowing that breaches, even unintentional, are somewhat common, let's explore the reasons why cloud storage services are breached and data is exfiltrated.
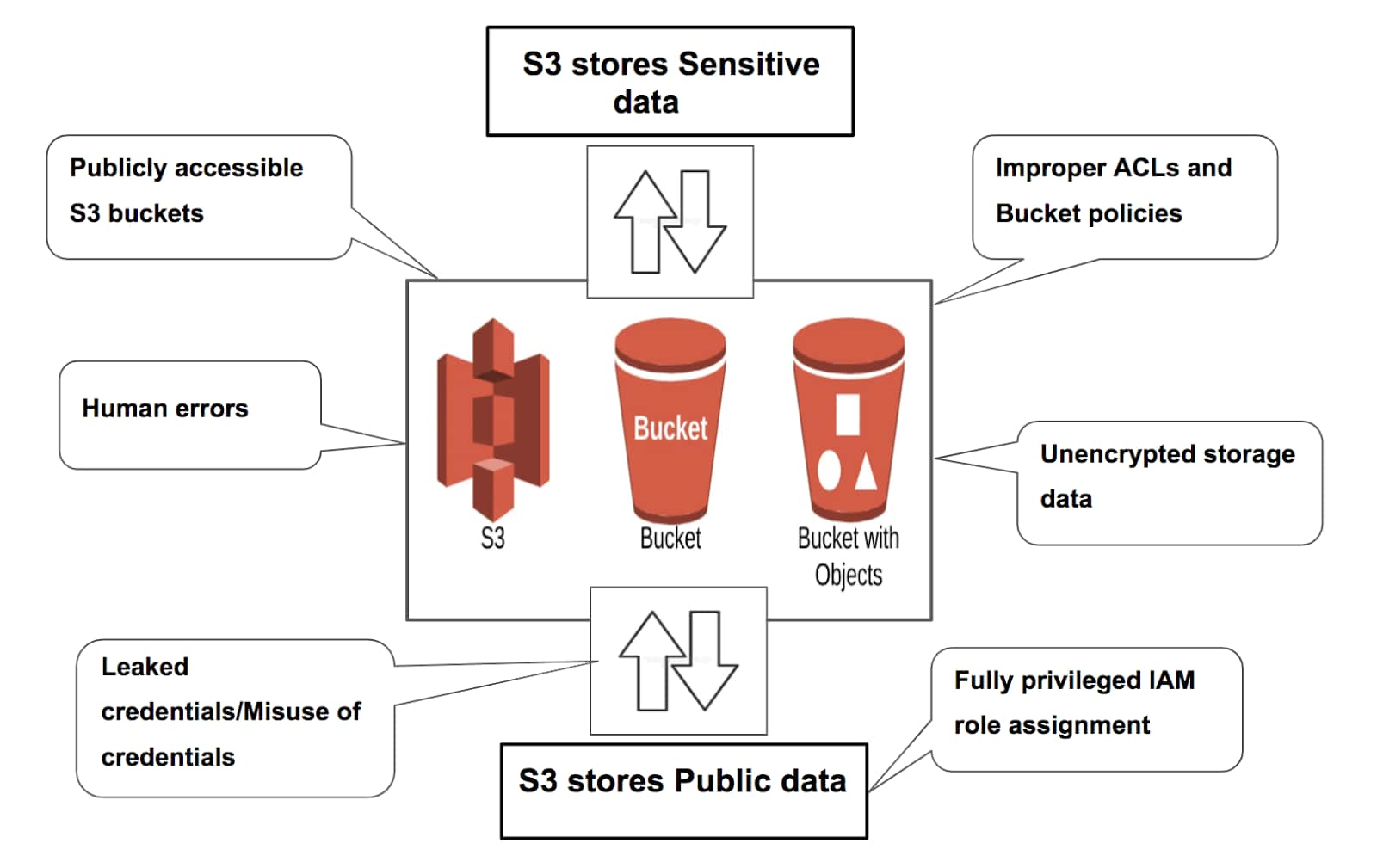
1. Publicly Accessible Buckets
S3 users can misconfigure buckets to make them publicly accessible over the Internet. When a bucket is made ‘public’, everyone has access to list or write objects and read or write permissions. Any user can access and download data stored in the S3 buckets.
2. Misconfigured ACLs and Bucket Policies
Amazon S3 buckets and objects are private and protected by default, with the option to use Access Control Lists (ACLs) and bucket policies to grant access to other AWS accounts or to public (anonymous) requests. Understanding how the S3 bucket access model, ACLs, and bucket policy settings work together is very important. Misconfiguring any one among these might lead to public access.
3. Unencrypted Storage Data
AWS provides encryption of data at rest as well as in transit; not configuring encryption either way can lead to a data breach. Then, even if a data breach happens, if it is encrypted by client-side encryption, which attackers might not have a key to decrypt, your data is still safe.
4. Improper Handling of Identity and Access Management Permissions
AWS Identity and Access Management (IAM) enables you to manage access to AWS services and resources securely. Using IAM, you can create and manage AWS users and groups, and use permissions to allow and deny their access to AWS resources. If a breach happens, it could extend to other cloud services and compromise workloads; IAM could prevent further access and restrict to perform further exploit operations.
5. Human errors
Human errors like unintentionally providing public access, placing sensitive information in wrong storage or public buckets, or incorrectly setting bucket and object permissions are usually the primary cause of breaches. These errors may be compounded by not understanding security features and ways to implement them. Educating yourself and your team should always be your first layer of security.
Conclusion
While customer trust takes years to build, a data breach can erase that trust almost immediately. From fixing compliance issues and mitigating future risk to repairing a broken reputation, breaches are expensive. A single data breach can cost an organization millions of dollars, comprising investigation expenses, damage control cost and repairs, notification costs, regulatory fines, compensation fees, lawsuits – the list goes on.
Moving to cloud storage platforms can help increase organizational productivity and product reliability. But it also requires a strong cloud security strategy – choosing the best tools, processes, policies, best practices, and standard guidelines for your organization. Choosing a comprehensive CSPM tool will improve your security posture, reduce your risks, and provide you protection against such breaches.