Over the past week, most of the discussion about the Heartbleed vulnerability focused on how to protect public facing servers. Many organizations sought to mitigate the risk using intrusion protection or other measures while they created and installed emergency patches.
There’s no question that the Heartbleed vulnerability introduced a major vector of risk to companies around the world. Given that an attacker could exploit Internet-facing servers and access privileged information, it is clear why these measures were necessary.
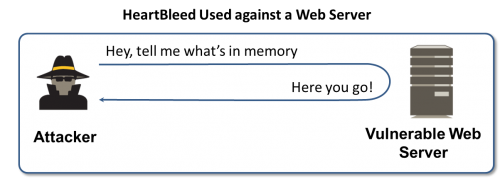
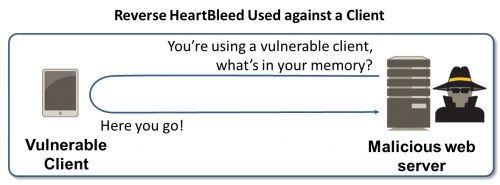
However, with the widespread coverage focusing on the exploitation of web sites, one might be misled into thinking that Heartbleed is solely a server security problem. It’s not. OpenSSL is widely used in a variety of products, and it’s not limited to web servers. In fact, it’s also used as the cryptographic library for clients connecting to a web server, which introduces another set of security issues. Clients that are using affected versions of OpenSSL are vulnerable to reverse-Heartbleed, which reveals the contents of memory on the client rather than the server.
In this scenario, the attacker would set up a malicious web server that would be used to send the exploit against the Heartbleed vulnerability to the client, rather than the other way around. Security teams need to think about a different set of problems, namely how to intercept the exploit while patching applications and operating systems on endpoints and mobile devices.
The attack surface is quite large with these conditions, because OpenSSL is used fairly extensively in many different types of products. With respect to mobile devices, the good news is that Heartbleed does not affect iOS itself, and does not affect the majority of Android versions. The bad news, however, is that Android 4.1.1 is vulnerable, and depending on which set of statistics that you look at, it could affect anywhere from 10% to 34% of Android mobile devices in use today.
Endpoints and mobile devices are considerably different in terms of rolling out patches and updates. Managed endpoints typically have updates pushed out through system management software, and even unmanaged endpoints often receive updates by the software publisher to protect the public at large. However, mobile devices are not updated as frequently and there are questions about whether some of the affected devices will ever be patched, because the device manufacturer is typically responsible for pushing out the patch, and may not be actively doing so.
Heartbleed exposes a set of mobile device security challenges that many organizations had not previously considered: How do you safely provide access to applications using mobile devices that may not be (and may never be) patched?
Determine Platform Use
One of the biggest problems that companies face right now is that they have no idea what types of devices are being used, especially in light of BYOD. Are people using older operating systems that are vulnerable? Being able to firmly establish which devices are being used with company applications, and the ability to exclude ones that are not properly secure, is the first step to dealing with the problem of platform fragmentation and the availability of patches.
Manage Mobile Devices
Managing the mobile device is a critical step for protecting it and understanding what applications are in use. Gauging the use of applications is necessary in order to take the proper steps to secure the traffic from potential threats.
Protect Users with Threat Prevention
Palo Alto Networks next-generation security platform identifies exploits, harmful websites, malware and mobile exploits. GlobalProtect can be used to automatically establish a tunnel to the next-generation security platform and keep users behind a gateway for threat prevention.
Use Device Criteria for Policy
Organizations may want to classify specific mobile devices for use in their organization. For example, if the company decides to phase out the use of older operating systems, the organization might establish policies that govern which platforms can be used with corporate applications.
These principles are critical elements for dealing with a number of mobile security issues, including ones that extend beyond Heartbleed. The main challenge that organizations face is how to be more thorough delivering threat prevention, as well as being more precise over policy and device control. To learn more about how these technologies are delivered, visit our GlobalProtect page.
For more on Heartbleed: