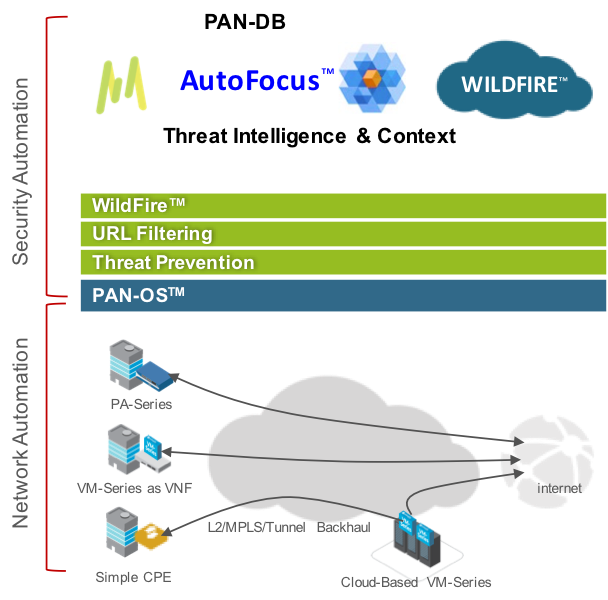
In cybersecurity, the concept of automation is provided in two distinct yet complementary areas: network automation and security automation. Network automation simplifies the workflow to deploy and manage security devices. Security automation provides the needed interactions and intelligence to learn, adapt and prevent successful attacks.
There are times in service provider cybersecurity conversations when the descriptors are dropped, and the topic just becomes “automation.” However, based on the audience’s perspective and focus with only the network or security aspects, this may limit complete understanding of the benefits provided when both types of automation are used in tandem.
Network automation and virtualization are coupled to allow for rapid deployment and configuration of devices and applications without slow, error-prone human intervention or purpose-built hardware deployments. Network automation drives the rapid scalability that enables operational benefits from virtualization.
The networking industry continues to transform from purpose-built hardware like routers, switches and firewalls to software-centric models that can leverage general-purpose or mass-market hardware. Network automation is often tossed around in conversations accompanied by acronyms such as SDN (Software-Defined Networking) and NFV (Network Function Virtualization). The key with automation in this environment is the ability to instantiate a virtual system as a piece of the network – that is, to get the system up and running, connected to peers, and ready to move packets – without direct human intervention. Network automation could be applied to internal private networks using VMware, or in public cloud environments such as Amazon Web Services or Microsoft Azure, or with platforms used across public and private deployments, such as OpenStack.
While rapid instantiation of a virtual network function is often good enough for network automation of routing and switching functions, it is only the beginning for security.
Security is a dynamic ecosystem of enforcement, threat analysis, threat feeds and signature updates that allow it to adapt as adversaries leverage previously unknown exploits and malware techniques. This is a world that never sleeps and keeps evolving.
Security automation is the engine that drives this ecosystem. Effective security automation includes automated data collection, analysis, enforcement and feedback.
- Data collection: Security automation starts in learning mode by pulling files and links from the network for malware indicator analysis, crawling websites, and receiving third-party information about potential threats.
- Analysis and enforcement: Once indicators of compromise are known, they can be converted to threat signatures, URL categorization and threat feeds. This information can be pushed into enforcement points in the network, primarily next-generation firewalls or endpoint protection applications. All of this is done moment by moment, day after day, with little to no human intervention.
- Feedback: As enforcement points see attempted attacks, the ecosystem can send alerts, perform dynamic policy updates, quarantine users and devices leveraging network automation, and push out notifications to affected users. The endless feedback loop is only effective when highly automated, without the bottleneck of limited or nonexistent human resources.
Rick Howard, our Chief Security Officer, gives a great perspective on security automation in a March 2017 interview on Federal News Radio. Rick reinforces the idea that manual security techniques will always stay behind automated adversaries and provides insight into how to move to automated security.
As you can see, cybersecurity automation is really “automation squared” for modern preventive security in a virtualized world: network automation to easily instantiate and bring a firewall online and ready for action anywhere in the world; security automation to work against adversaries and continuously try to prevent successful cyberattacks.
Palo Alto Networks partners with managed security service providers to provide effective and differentiated security services that reduce cost and increase average revenue per customer. For more information, visit our Nextwave Managed Security Service Provider Program.