This playbook is part of the Cortex Response and Remediation Pack, which delivers a powerful collection of automated playbooks designed to streamline incident response and remediation processes, built to support an autonomous SOC vision.
The playbooks in this pack are tightly coupled to analytics alerts, leveraging detector logic to provide highly accurate and context-aware responses. This ensures seamless integration with Cortex XSIAM®, enabling SOC teams to focus on high-priority threats while automating repetitive tasks.
What is Tor?
Tor is a decentralized network designed to enhance privacy and anonymity online. It routes internet traffic through a series of relays, encrypting data at each step to obscure its origin and destination. While Tor can be used for legitimate purposes such as protecting privacy, bypassing censorship, and enabling secure communication, it is also exploited by threat actors to mask malicious activities. This dual-use nature of Tor makes it a critical focus area for security monitoring and automated response mechanisms.
In enterprise environments, Tor has almost no legitimate use cases. Its anonymity features conflict with enterprise security policies that prioritize traceability, accountability, and compliance. Therefore, any activity involving Tor in an enterprise context is often treated as suspicious and warrants thorough investigation.
Single sign-on (SSO) is a cornerstone of modern enterprise security, offering streamlined access to applications and reducing password management complexities. However, it also presents a significant risk vector if not monitored carefully. Two analytics alerts related to SSO that often indicate potential threats are:
- A successful SSO sign-in from Tor.
- A successful SSO sign-in from Tor via a mobile device.
These alerts, specifically tied to Cortex XSIAM, flag potential unauthorized or suspicious access attempts. This blog introduces a robust Cortex XSIAM® playbook designed to handle these alerts effectively, ensuring security gaps are mitigated promptly.
Purpose of the Playbook
The primary purpose of this playbook is to mitigate security risks by:
- Containing potential threats as early as possible.
- Investigating the context of the alert thoroughly.
- Executing remediation actions if malicious activity is detected.
Stages of the Playbook
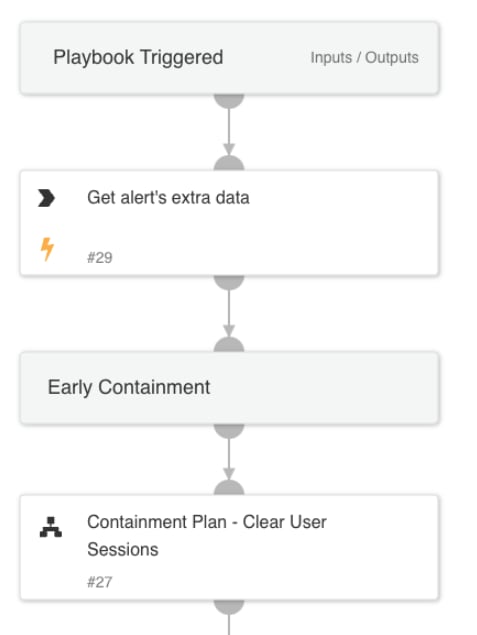
1. Early Containment
Upon receiving an alert of a successful SSO sign-in from a Tor exit node, the playbook initiates early containment actions to disrupt any potential malicious activity. Key steps include:
- Clearing or revoking user sessions: This action terminates the connection originating from the Tor exit node, keeping the attacker outside of the network.
- Enforcing re-authentication: Ensures that the user’s identity is verified before they regain access.
The playbook executes these actions using integrations with either Microsoft Graph User (Azure Active Directory Users) or Okta v2, ensuring compatibility across common enterprise authentication platforms.
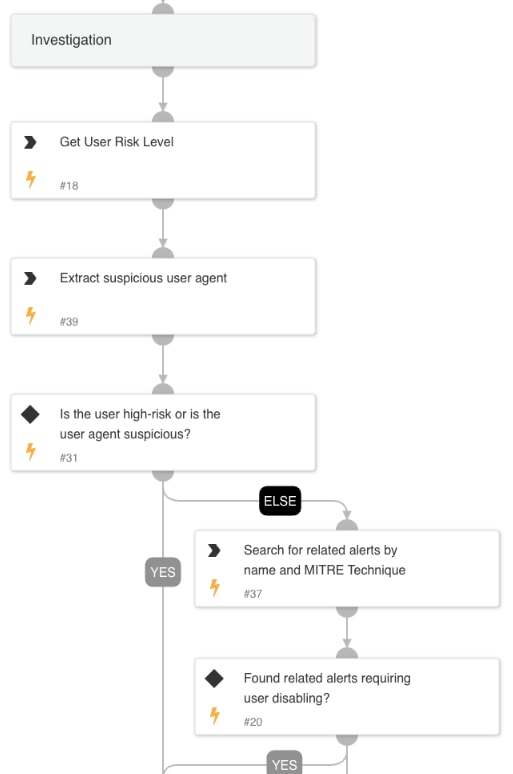
2. Investigation
In the investigation phase, the playbook dives deeper into the context of the alert, performing the following checks:
- User’s risk score: Evaluate the user’s activity to identify abnormal patterns. User risk score is evaluated based on Cortex AI capabilities with a dedicated ML model that evaluates the risk score.
- Suspicious user agent usage: Identifies anomalies in the browser or device details used for the sign-in.
- Cross-referencing related Cortex XSIAM alerts: Uses the MITRE ATT&CK framework to search for:
- T1566: Phishing
- T1621: Multi-Factor Authentication Request Generation
- T1110: Brute Force
- T1556: Modify Authentication Process
When these techniques are observed alongside a successful SSO login from a Tor exit node within a short time frame, it strongly indicates that an attacker is leveraging stolen credentials, bypassing MFA, and securing unauthorized access—hallmarks of advanced malicious campaigns.
These steps provide a holistic view of the user’s activity, helping to differentiate between legitimate and malicious access attempts.
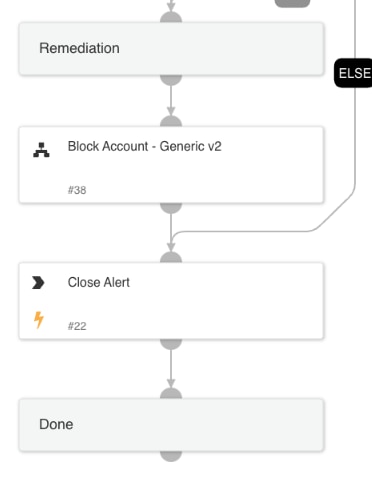
3. Remediation
If the investigation uncovers:
- A high-risk score.
- Suspicious user agent activity.
- Related malicious Cortex XSIAM alerts.
The playbook suggests the analyst disable the user’s account to prevent further access. This action requires analyst approval, ensuring human oversight before taking significant steps like disabling an account.
Integration Requirements
To execute the response actions, the playbook requires one of the following integrations:
- Microsoft Graph User (Azure Active Directory Users)
- Okta v2
These integrations ensure seamless execution of containment, investigation, and remediation actions, aligning with enterprise authentication standards.
Addressing Security Challenges
The alerts tied to successful SSO sign-ins from Tor indicate potential security gaps that can lead to:
- Unauthorized access: Malicious actors may exploit anonymity to access sensitive data.
- Account compromise: Tor’s obfuscation can hide credential stuffing or brute-force attacks.
- Data exfiltration: Once access is gained, sensitive information can be extracted.
This playbook provides an automated, structured response to mitigate these risks, ensuring:
- Threats are contained before causing damage.
- Investigations provide actionable insights.
- Remediation actions prevent recurring access attempts.
Learn More
For detailed documentation and implementation guidance, visit the Cortex XSIAM Playbooks Documentation.
Stay ahead of evolving threats and protect your enterprise with Cortex XSIAM’s automated playbooks.