Unit 42 has published a number of articles over the last six months discussing the malicious campaigns, pseudo-Darkleech and EITest. These long-running campaigns have gone through many evolutions since their initial discovery, employing different exploit kits and techniques to avoid detection and improve attack success rates. In their most recent forms, both campaigns utilize the RIG exploit kit for the delivery of Cerber ransomware.
HOW DOES IT WORK?
Attackers running a pseudo-Darkleech campaign use a collection of legitimate websites hosting malicious scripts secretly inserted in their source code. With no particular target in mind, the attackers select random users accessing the compromised websites and load hidden iframes in the backgrounds of their pages.
Similar to pseudo-Darkleech, attackers running an EITest campaign have no specific target in mind, and attempt to use a compromised website injected with malicious script to exploit anyone running out-of-date Windows operating systems or applications.
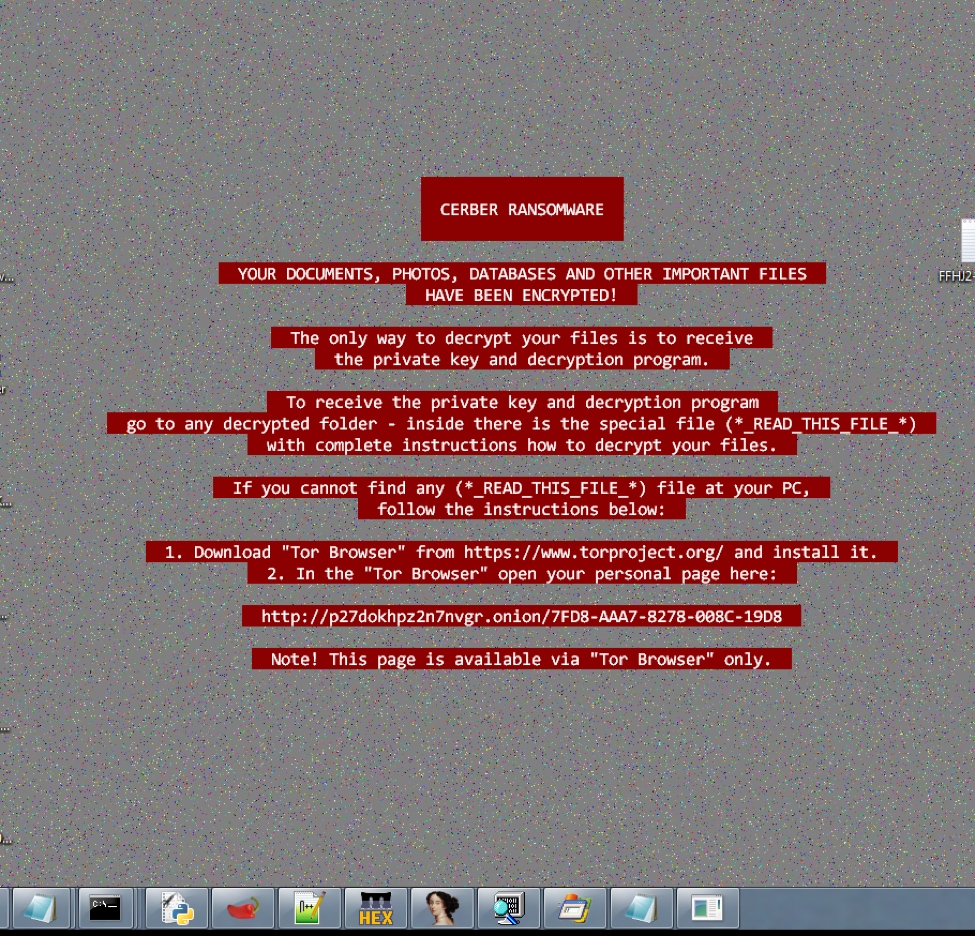
When victims visit one of these compromised websites, they are forwarded to the RIG landing page, where the exploit kit fingerprints the target to determine which exploit can be served for their system. If successful, Cerber ransomware is deployed and the victim’s host is infected.
WHY IS IT UNIQUE?
Cerber has proven to be a powerful threat with advanced encryption and evasion capabilities. The encryption tasks can be done offline, without C2 communication; executables are continuously reloaded; and different stages of the malware are separated into multiple files, making Cerber extremely difficult to detect for most malware analysis tools.
The longevity of these campaigns – pseudo-Darkleech since 2012 and EITest since 2014 – shows that they are reliable for attackers. Domains, IP addresses and other indicators are continuously changing, allowing them to survive the changing exploit kit landscape and remain undetected by most security solutions.
HOW DO YOU STOP IT?
Palo Alto Networks Traps uses a multi-method approach, focusing on the core techniques used by all exploit-based attacks to prevent successful exploit campaigns.
Traps stops exploit techniques that work to manipulate memory management mechanisms and redirect applications normal execution flow before they have a chance to subvert an application. It recognizes weaponized files in the exploit attempt and stops them before they can successfully perform any malicious activity. Additionally, Traps prevents malicious code from being deployed following the exploitation stage.
By focusing on these core exploit techniques used by attackers, Traps is able to prevent never-before-seen attacks.
Learn more about how Traps can stop exploit campaigns like pseudo-Darkleech and EITest.
Ignite ’17 Security Conference: Vancouver, BC June 12–15, 2017
Ignite ’17 Security Conference is a live, four-day conference designed for today’s security professionals. Hear from innovators and experts, gain real-world skills through hands-on sessions and interactive workshops, and find out how breach prevention is changing the security industry. Visit the Ignite website for more information on tracks, workshops and marquee sessions.