In the book Hitchhiker's Guide to the Galaxy, the answer to the ultimate question of life, the universe, and everything is “42”. Back in 2014, a group of threat researchers at Palo Alto Networks were given the charter to make sense of all the telemetry, indicators of compromise (IOC’s), and other data being gathered about the threats our customers were seeing— just looking at the data wasn’t enough. Our customers needed to understand who was executing these attacks, what were their objectives, what were their specific TTPs to identify the group, and how to truly operationalize the threat intelligence they were being given.
It was at that point Unit 42 was born with the charter to help customers by providing threat research that enables security teams to understand adversary intent and attribution, while enhancing product protections offered by our products and services to identify and stop advanced attacks. Since then, Unit 42 has published hundreds of blogs, Actionable Threat Objects and Mitigations ATOMs, and Threat Briefs providing detailed analysis of the threat landscape while building a reputation as an authority on the threats we face daily.
Fast forward to 2016, when Unit 42 published a detailed analysis of the Shamoon 2 attack on Saudi Aramco gaining global attention and continuing to bolster its reputation as a threat intelligence authority. Unit 42 has provided expert testimony to the United States Senate Homeland Security and Governmental Affairs Committee and was named as one of just 8 founding partners of CISA’s Joint Cyber Defense Collaborative.
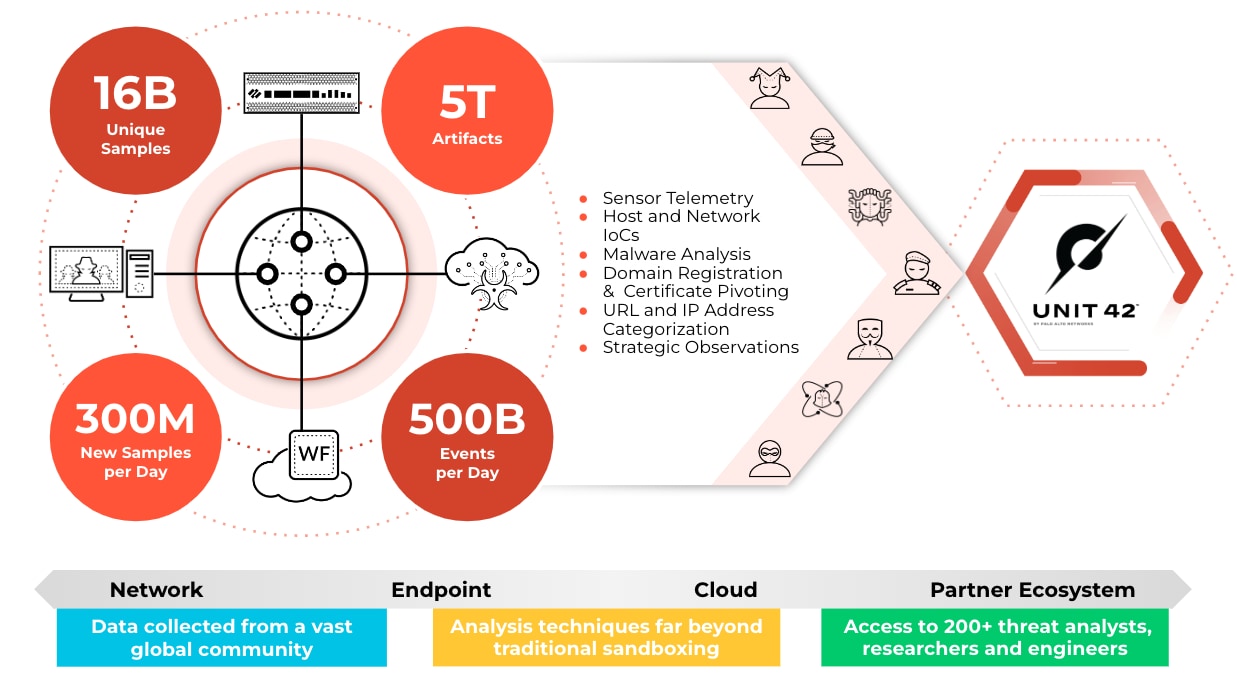
Unit 42 fields one of the largest and most experienced threat intelligence teams in the world with over 200 cyber threat researchers, consisting of threat hunters as well as experts in reverse engineering, malware analysis, and threat modeling. We have 10+ years of historical malware analysis growing by over 300 million samples per day. We have won multiple awards and industry recognition for our contributions to vulnerability research and continue to tap into our threat intelligence to assess and test your security controls against the right threats, transform your security strategy with a threat-informed approach, and respond to incidents in record time. Unit 42 services like Unit 42 Incident Response, Unit 42 Cyber Risk Management, Unit 42 Managed Threat Hunting (MTH), and Unit 42 Managed Detection and Response (MDR); were all built around our threat-informed approach.
And that brings us to today. MITRE Engenuity has just published the results of their first ever evaluation of security services focused on managed detection and response delivered by managed service providers. Palo Alto Networks and Unit 42 were thrilled to be invited to participate in this inaugural evaluation. We were even more thrilled to find out the evaluation would be based on the threat group OilRig.
Why, you ask? It goes back to our original charter; to understand adversary intent and monitor their actions to ensure our customers are protected. Unit 42 assigned APT 34 the attributed name of OilRig and published the OilRig Adversary Playbook in 2016. We’ve continued tracking them, writing over 15 Articles about OilRig since that initial analysis and playbook.
When Unit 42 issues a report, our goal is to provide a clear understanding of the threat and actionable details to communicate to your organization. As a Unit 42 MDR or MTH customer, you will receive
- Threat Reports that provide detailed information about cyberthreats identified in your organization. You get a complete account of each security incident, including the scope of the attack, the probable source, the attack tools, and recommended guidance.
- Impact Reports contain the details needed to stay ahead of emerging threats affecting multiple organizations and allow you to answer critical questions about exposure to high-profile attack campaigns from your executives or board before they even ask.
- Threat Hunting Alerts integrated into Cortex XDR, allowing analysts to review and triage reports using their standard investigation workflows. Threat hunting alerts are automatically grouped with related alerts into incidents, providing a complete picture of an attack.
There is quite often voluminous information and telemetry available which can be read and reviewed in detail later, but when the clock is ticking it is important to have the information at your fingertips rather than be sifting through raw data, allowing you to focus on informing key stakeholders and taking steps to defend your organization.
Doing so requires a deep understanding of the latest threats and applying that knowledge to our products and services, so our customers have the latest prevention and detection tools and threat information. Unit 42 continues to have a long-standing commitment to partnering with governments and international intelligence communities, providing innovative security technology, lending our expertise on cybersecurity best practices and policies, and providing early warnings and threat intelligence to law enforcement and CERTs on emerging threats long before the world is aware of them.
From the beginning, Palo Alto Networks’ vision has been to ensure each day is safer and more secure than the one before, and Unit 42 continues to be a cornerstone of that mission.
For more information about Unit 42 services, please visit https://www.paloaltonetworks.com/unit42