This post is also available in: 日本語 (Japanese)
Government agencies have been stepping up efforts to adopt a Zero Trust architecture since May, when President Biden signed the Executive Order on Improving the Nation’s Cybersecurity. Many of these agencies and other organizations in the public sector were already laying the groundwork for Zero Trust before the Executive Order as part of their digital transformation journey, which includes rebuilding and improving their security approach.
We know that there are still a lot of questions about Zero Trust and that agencies may be wondering what it means to deploy a Zero Trust Enterprise approach with help from Palo Alto Networks. We thought we would lay out a few need-to-know basics about Zero Trust for agencies to keep in mind as they move forward in their cybersecurity journey.
What Is Zero Trust?
By definition, Zero Trust is a strategic approach to cybersecurity that secures an organization by eliminating implicit trust and continuously validating every stage of a digital interaction.
The core idea of Zero Trust is to “never trust, always verify.” Organizations can no longer inherently trust whatever is inside their security perimeter. As the perimeter has evolved and IT environments have become far more complex, organizations must continually authenticate, authorize and verify who and what can access an environment to grant “least privilege” access. Authorization is based on who or what is requesting access, the context of the request and the risk level.
Deployed properly, Zero Trust is a strategic approach to cybersecurity that simplifies risk management to a single use case: the removal of all implicit trust for users, applications and infrastructure.
What Is the Value of Adopting a Zero Trust Strategy?
Zero Trust is a way for government agencies and other organizations to build resilience into their IT networks and environments. With Zero Trust as a strategic framework for guiding the agency’s security approach, the agency can keep moving forward with its mission, even if its environment is compromised.
Zero Trust can also serve as a North Star to guide an organization’s future security investments. Whatever the threat du jour may be, it won’t be the force driving the agency’s decision-making around security spending. By moving to Zero Trust, an organization can lower its costs in several ways:
- Reducing risk by eliminating implicit trust for users, applications and infrastructure.
- Achieving better security outcomes by deploying the most rigorous security checks.
- Adopting a simplified, consistent security posture that is less expensive to manage.
How Does an Organization Become a Zero Trust Enterprise?
Zero Trust starts with determining what you already have and what you need to reduce acute risk and achieve resilience. Government agencies and other organizations in the public and private sector should approach Zero Trust based on the intersection of users, apps and infrastructure with identity, devices/workloads, access and transactions.
Here’s what the approach looks like:
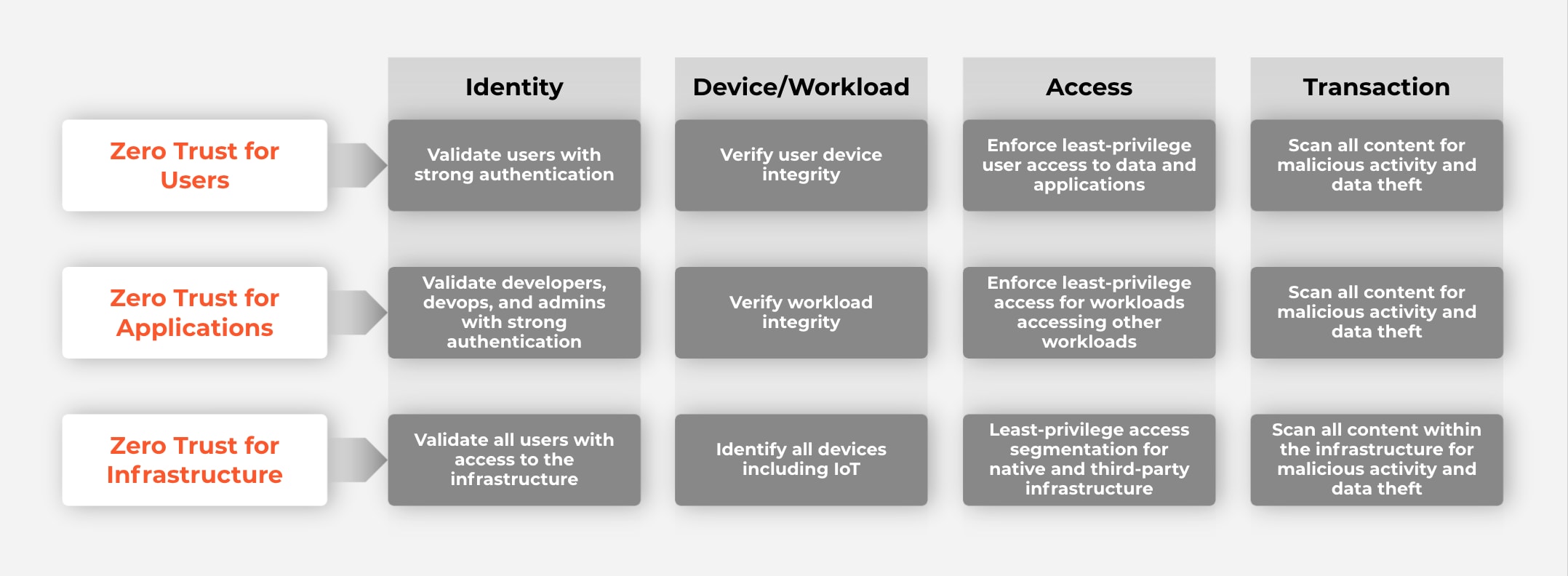
You can begin implementing the Zero Trust process anywhere. Starting points might include Zero Trust Network Access, DevSecOps, microsegmentation or third-party management.
What Are the Key Elements of the Zero Trust Enterprise Approach?
Palo Alto Networks is uniquely positioned to deliver Zero Trust Enterprises because, unlike other vendors, we offer a broad, high-quality and integrated set of capabilities. We help enable and ensure Zero Trust by eliminating all implicit trust across users, applications and infrastructure. These important elements help distinguish our approach:
- Comprehensive: Zero Trust should never focus on a narrow technology. It must instead consider the full ecosystem of controls – network, endpoint, cloud, application, the Internet of Things, identity and more – which organizations rely on for protection.
- Actionable: Comprehensive Zero Trust isn’t easy; however, getting started shouldn’t be hard.
- Intelligible: A Zero Trust approach should be concise and easy for nontechnical executives to understand.
- Ecosystem Friendly: In addition to having one of the most comprehensive portfolios in the market, we work with a broad ecosystem of partners to help enable all aspects of the Zero Trust Enterprise.
Here’s what our Zero Trust Enterprise framework looks like, and how various technology products help to support it:
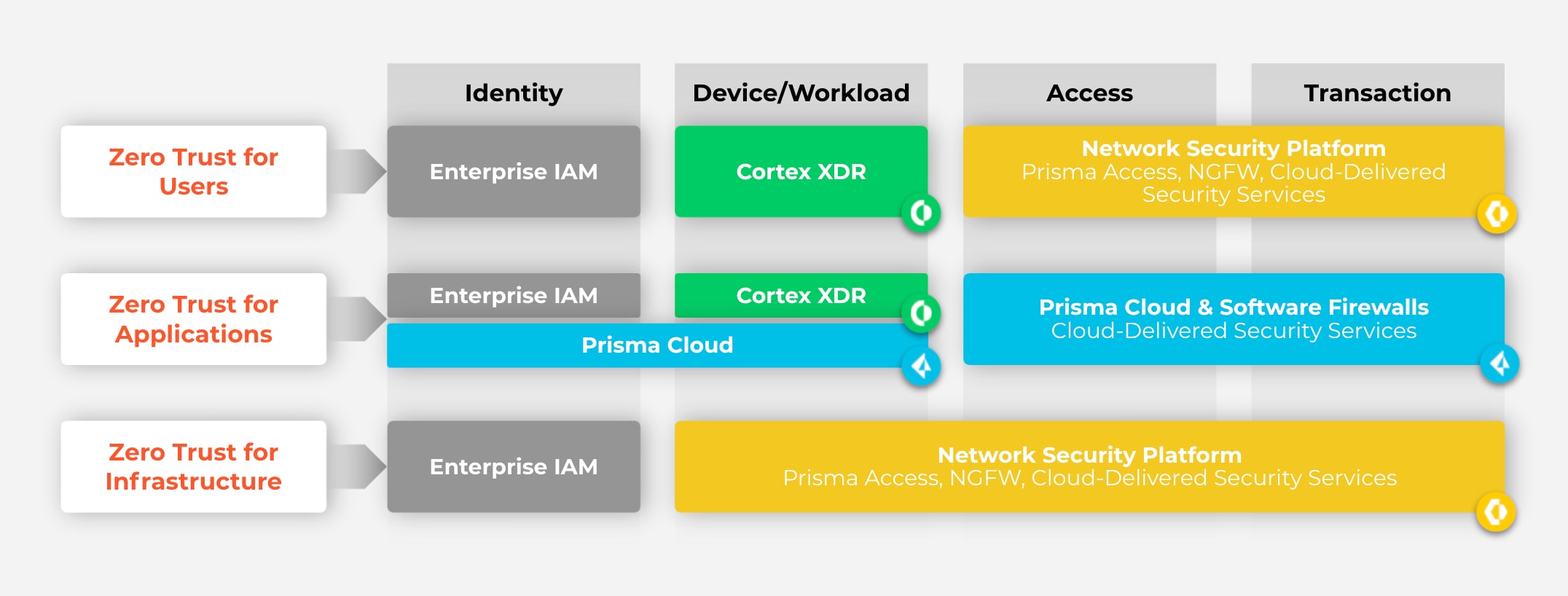
What About Taking Zero Trust to the Cloud?
Hopefully, the information presented above helps to answer some basic questions you might have about Zero Trust and how Palo Alto Networks can help support your journey. One final question we’ll cover here is one we’re hearing often from government agencies: “How challenging is it to extend Zero Trust policies to the cloud?”
The challenge is that today, the majority of apps are now directly delivered from the cloud, public or private, with direct-to-app and rapid development models fundamentally disrupting app delivery and consumption models for your users. This creates a rift with the legacy, castle-and-moat approach in a traditional data center; bringing with it new risks as a consequence of the implied trust granted to IaaS, PaaS and app delivery platforms. A new mindset and a disruptive approach is needed to discover and eliminate implied trust in this ecosystem.
Recently, the Palo Alto Networks federal team worked with a federal agency to extend its segmentation program for critical data from an on-premises environment to the cloud. The agency is taking advantage of the single policy engine in our unified policy management platform, Panorama, to apply the same Zero Trust policies in both environments without the need to design anything new.
Visit our website for more information on how Zero Trust architecture fuels digital transformation. If you’d like to learn more about how we can help your agency become a Zero Trust Enterprise, our Professional Services team can assist you with Zero Trust architecture design, implementation or both, depending on your organization’s needs.