
Faraz Ahsan — AI's Role in Cybersecurity
“AI’s Impact in Cybersecurity” is a blog series based on interviews with a variety of experts at Palo Alto Networks and Unit 42, with roles in AI research, product management, consulting, engineering and more. Our objective is to present different viewpoints and predictions on how artificial intelligence is impacting the current threat landscape, how Palo Alto Networks protects itself and its customers, as well as implications for the future of cybersecurity. Read our interview with Faraz Ahsan.
Recently, I had the privilege of engaging in a thought-provoking conversation with a seasoned Principal Consultant at Unit 42, Faraz Ahsan, specializing in security research. Ahsan provided insights into the integration of artificial intelligence (AI) and machine learning (ML) in combating cyberthreats.
Reactive to Proactive Defense
One of the most significant changes in cybersecurity, with the advent of AI, is the shift from reactive to proactive defense mechanisms. Traditionally, cybersecurity relied heavily on predefined rules and signatures to detect and mitigate threats, often reacting to attacks after they occurred while relying on manual investigation and intervention along the way.
However, with AI, organizations can implement a proactive approach and stay ahead of cyber adversaries with systems that can analyze vast amounts of data in real time, identify patterns, predict potential threats, as well as detect and neutralize malicious activity before they can cause significant damage.
Additionally, AI-powered cybersecurity solutions can adapt and learn from new data and emerging threats, continuously improving their efficacy over time, without requiring manual intervention. This transformative capability represents a paradigm shift in cybersecurity, empowering organizations to anticipate and mitigate threats with unprecedented speed and accuracy.
AI + ML for a Supercharged Defense
AI and ML are increasingly integral to security operations, revolutionizing the ways threats are detected, analyzed and mitigated. These technologies can quickly and accurately identify patterns indicative of cyberattacks, enabling rapid responses to emerging threats. Through advanced algorithms, AI can discern normal behavior from anomalous activities, detecting even subtle deviations that might signify a breach, such as unusual login times or locations, or anomalous network traffic patterns.
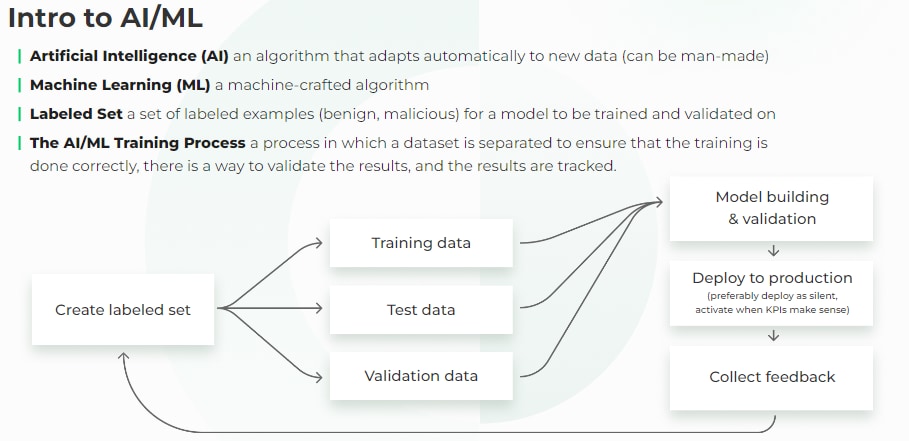
These deviations might be subtle enough to evade traditional rule-based detection methods but can be identified through AI-driven anomaly detection techniques that analyze vast amounts of data and recognize patterns characteristic of malicious activity. Moreover, machine learning algorithms continuously refine their models based on evolving data, enhancing accuracy and adaptability over time.
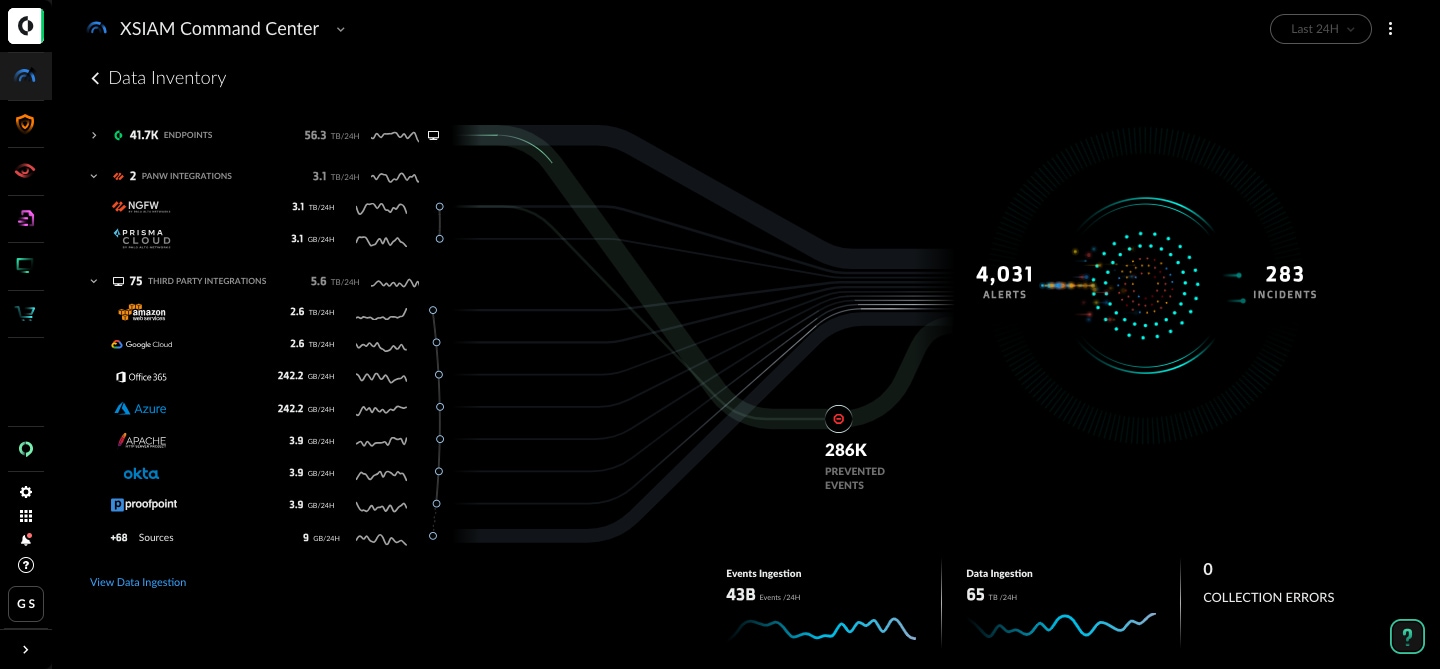
For example, Cortex XSIAM uses AI and ML algorithms to analyze the behavior of endpoints and detect anomalies that may indicate the presence of a threat. Employing predictive analytics, the XSIAM platform leverages ML algorithms to analyze historical data and predict potential threats, helping organizations proactively protect against future attacks. XSIAM continuously learns from new data and adjusts their models, improving the platform’s accuracy and effectiveness over time.
Beyond Buzzwords
Ahsan leads a dynamic team at Unit 42 tasked with implementing AI and ML policies to combat web scraping – a prevalent technique used by adversaries to extract valuable data from websites, perform reconnaissance, commit ad fraud and conduct general data theft. His responsibilities include influencing policies, monitoring performance and ensuring a seamless user experience. According to Ahsan, AI and ML are poised to become indispensable components of enterprise security platforms, reshaping the future of cybersecurity. Faraz said, "AI and ML are not just buzzwords; they are becoming integral to the fabric of cybersecurity. We must embrace these technologies to stay ahead of evolving threats."
During our discussion, Ahsan offered compelling predictions regarding the future landscape of cybersecurity. He underscored the significance of integrating AI-driven solutions into security operations to drive a fundamental change toward proactive threat hunting and incident response strategies. Ahsan remarked:
The integration of AI into security operations is akin to a revolution. It streamlines processes, reduces alert fatigue and enhances the overall efficacy of threat detection and remediation. Incorporating AI into security systems enables organizations to mitigate risks more effectively and respond to threats with unprecedented speed and accuracy.
Ahsan likened the transformative impact of AI on security operations to a groundbreaking shift, much like the advent of assembly lines in the early 1900s – a radical idea at the time. Just as Henry Ford revolutionized manufacturing by introducing automation and streamlining production processes, the AI revolution we're witnessing today is transforming various industries by automating tasks and enhancing efficiency through intelligent systems. Similarly, in SecOps, centralizing data and automating processes, AI empowers organizations to proactively identify and mitigate threats in real-time, significantly enhancing their cyber resilience.
Metrics, Proactive Measures and Future Trends
When evaluating AI-powered security solutions, Ahsan suggested focusing on key performance metrics, such as the average time from alert to remediation, reduction in false positives and automated incident closure rates. While AI systems will learn to counter evolving threats, Ahsan noted that the performance of AI models needs to be monitored. Monitoring performance is critical for ensuring new or changing threats aren't overlooked and that existing predictions are not drifting away from where they should be. Metrics like skew and drift can be monitored automatically and raise alerts, but actual debugging or assessments will require analyst intervention.
In addition to monitoring AI model performance, Ahsan noted that AI models will be the target of attacks. SecOps teams will need to employ proactive measures to safeguard AI models from adversarial attacks, including robust access control policies, automated user behavior monitoring, and real-time anomaly detection. These measures mitigate risks posed by insider threats and adversarial evasion techniques, bolstering organizations' cyber defenses.
Looking ahead, Ahsan predicted a heightened focus on data privacy and classification in response to the growing volume of data and sophisticated AI-driven attacks. From the adversarial AI perspective, Ahsan noted two examples that highlight this focus. The first is one we already see in the wild where malicious actors aggregate data from a multitude of internet sources to craft a fairly convincing phishing attack. The other concern is in the massive amount of user data that can be exfiltrated in a successful attack as data is centralized for use by AI systems.
Both of these issues will necessitate a deeper look into an organization’s data classification policy. This means understanding the data you hold, how sensitive each kind is, and whether each classification of data has the proper controls surrounding it. Effectively managing this can limit an organization’s exposure from an AI driven attack.
From the organization’s perspective, effective classification and privacy policies need to be maintained to ensure user data is effectively segmented from any potential AI model training or AI model leakage. This is especially crucial in an LLM context where the right prompt could return data that should have been inaccessible.
AI has the potential to revolutionize cybersecurity practices. Embracing AI-driven solutions is imperative for effectively mitigating cyberthreats and safeguarding critical assets. By harnessing the power of AI to automate processes, enhance threat detection and mitigate risks, organizations can fortify their security posture in an ever-evolving digital landscape.
Ahsan believes AI will have a pivotal role in cybersecurity. As organizations strive to stay ahead of adversaries, leveraging AI-driven solutions will be paramount for maintaining cyber resilience and safeguarding digital assets in an increasingly interconnected world.
Learn More on AI’s impact in Cybersecurity
Register for Symphony 2024, April 17-18, to explore the latest advancements in AI-driven security, where machine learning algorithms predict, detect and respond to threats faster and more effectively than ever.