5G has the potential to disrupt traditional business models and create new monetization opportunities for service providers to stay ahead of the curve and succeed in the digital age. To live up to its potential and promise, however, 5G has to address cyber risks. Our work with Singtel focuses on application-layer security, 5G network slice security, intelligent security per 5G subscriber and equipment identities.
The role of cybersecurity has become increasingly important. Cyberthreats are growing more numerous and sophisticated. Criminals consistently introduce and update new attack tools, using automation, exploit toolkits and cloud technology. All organizations, particularly telco service providers, must assume they will be the target of a nation state cyberattack.
The risk of cyberattacks to all organizations will grow with the scale enabled by 5G. This will dramatically increase network capacity and attack surface. The proliferation of devices, vast increase in intelligence at the network edge, and the aggregation of critical functionality at the network core bring challenges that together contribute to a perfect storm of security risk in 5G deployments.
Security for previous generations of mobile technology was not focused on detecting and preventing attacks on all layers, all locations/interfaces, all attack vectors, or all software lifecycle stages. Because 5G finds its way into mission-critical applications that affect every aspect of public and private life, it's imperative to make sure that 5G deployments are protected by pervasive security that looks at all layers of the attack surface and provides controls to help mitigate risks.
For 5G to live up to its promise, you need a Zero Trust approach.
Zero Trust in 5G is defined by Palo Alto Networks as continuous security visibility, detection and prevention with 5G subscriber-ID and equipment-ID granularity across all layers, locations, vectors, etc.:
- All Layers: Application layer, signaling layer, data layer, management layer, 5G slices.
- All Locations: Roaming, peering, RAN, DC, Internet perimeter, open-RAN interfaces, APIs.
- All Attack Vectors: L3/L4, including all threats and vulnerabilities, i.e. malware, ransomware, DNS attacks, C&C, remote code execution, etc.
- All SW Life Cycle Stages: Runtime and shift-left to CI/CD and further left to DevOps.
- Automation, Machine Learning (ML), Artificial Intelligence (AI): Get out of reactive mode to threats, attacks and vulnerabilities by harnessing the power of machine learning and artificial intelligence in real-time.
- Use of In-Line Real-Time Machine Learning Models: Help detect and prevent previously unknown attacks.
Last week Singtel announced that they have selected Palo Alto Networks to supplement their 5G security efforts.
Application-Layer Security
Application-layer security has a few dimensions. Applications must be identified and confirmed if they are what they claim to be, and either allowed or blocked, or, certain applications should only be allowed to be used altogether. Badly written applications can cause damage, such as by using excessive CPU, memory, other resources or even causing network congestion and outages.
5G Network Slice Security
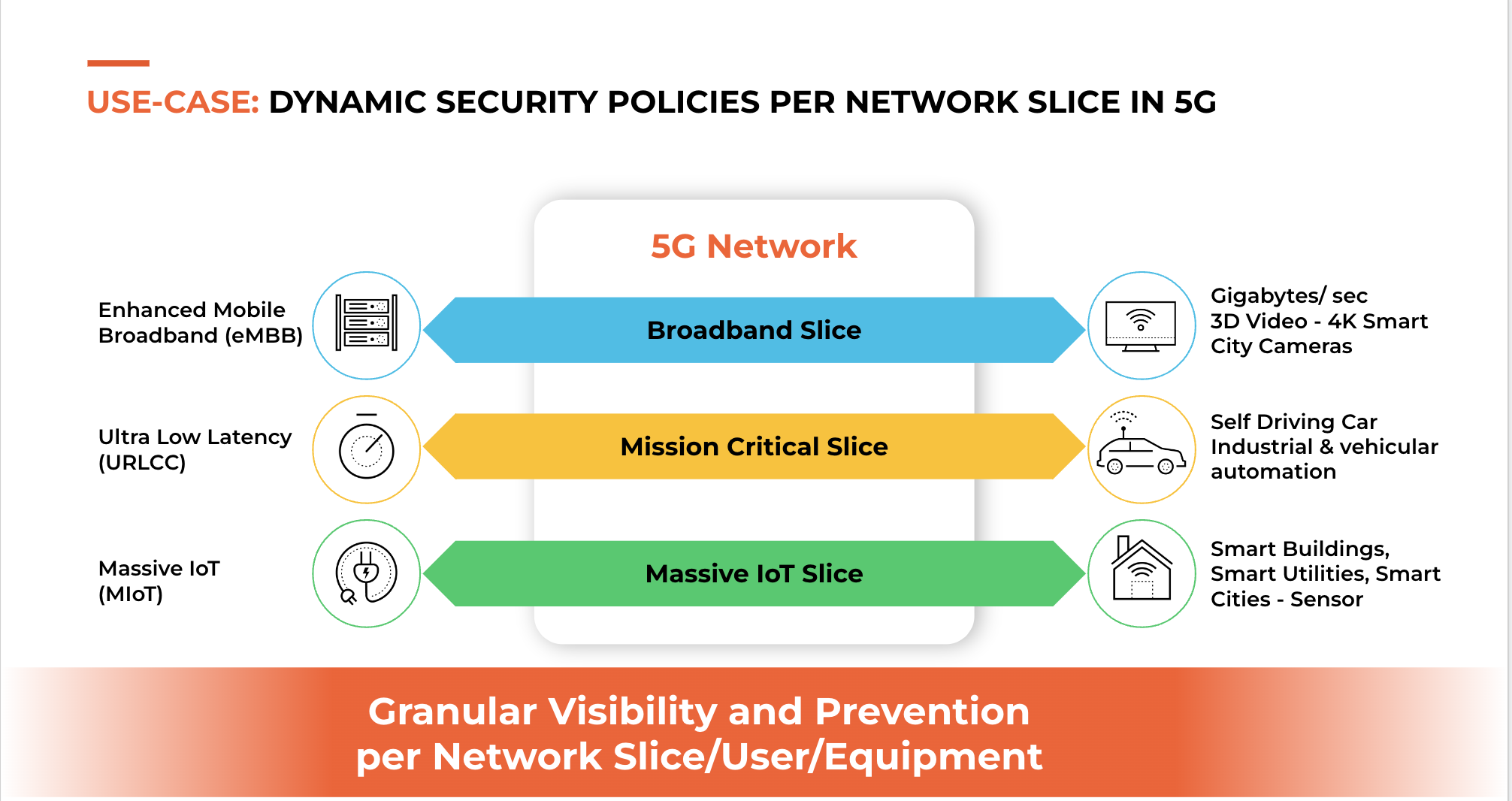
An additional aspect of Zero-Trust security for 5G is network slice security. Network slicing is a fundamental 5G differentiation compared to all previous generations of mobile networks. 5G allows service providers the ability to offer different, dedicated, end-to-end network slices with different bandwidth and quality of service (QoS) to different enterprises, vertical industries and government agencies on the same 5G network simultaneously. New slices can be launched and modified dynamically, using 5G Network Slice-IDs (NSSAI) running on the 5G signaling layer.
In addition to bandwidth and QoS, each slice’s security level can be tailored to its specific requirements. Different network slices can also run side by side for different purposes and have their own security requirements applied to meet their respective needs. For example, different security policies can apply application controls, anti-virus, anti-spyware, URL filtering and intrusion prevention services by network slice or group of slices. As real-time threat detection and prevention is paramount, this should be done dynamically in real time, so traffic can be correlated to specific slices, and security can be applied in real time.
Intelligent Security, Based on 5G Subscriber and Equipment Identities
Zero Trust 5G security should be intelligent, as well as pervasive, flexible and as simple as possible.
Security visibility and prevention should be intelligent and must be able to correlate attacks, threats and vulnerabilities to the real 5G subscriber and equipment identities: SUPI (5G globally unique Subscription Permanent Identifier) and PEI (Permanent Equipment Identifier). With this intelligence it would be possible to automatically identify threats and attacks while granularly enforcing security mechanisms based on the SUPI and/or PEI.
In addition, intelligent security should allow for rules and security policies to change as required per business needs. Some examples include options to apply application control, anti-virus, anti-spyware, URL filtering, intrusion prevention and advanced threat prevention per 5G subscriber and equipment identities. Examples of 5G subscriber-ID security flexibility include being able to provide security policies per 5G subscription identifier, including Subscription Permanent Identifier (SUPI) or a group of SUPIs. Options can also add single or multiple SUPIs or PEI in a security policy, or select various SUPI or PEI ranges in a security policy.
While there are many more examples, the key point is that Service Providers are able to choose from a range of security policies that work for them.
Palo Alto Networks is proud to help partner with Singtel in their 5G security efforts. Network service providers have a critical role in delivering enterprise-grade security for their enterprise customers. Read Monetizing 5G Security: Moving from Cost Center to Profit Center and learn more about Palo Alto Networks 5G-Native Security for protecting 5G interfaces, user traffic, network function workloads and more.