This post is also available in: 日本語 (Japanese)
When we created the 2022 Unit 42 Incident Response Report, our goal was simple: to gather insights from our incident response cases and our security consultants’ experience so organizations can benefit from them.
By examining what we’ve learned about attackers from helping organizations in hundreds of cases, you can prioritize your resources and focus your efforts to mitigate the risks that you deem most significant. The goal is to understand:
- What attackers are doing (or trying to do).
- How attackers are doing it.
- What contributes to attackers’ success.
- What you can do to protect your organization.
To answer these questions, Unit 42 analyzed hundreds of incident response (IR) cases over the past year to extract critical details and insights. We also conducted in-depth interviews with experienced consultants to learn what they believe organizations most need to know to be more resilient and prepared.
The 2022 Unit 42 Incident Response Report provides our findings, shedding light on key attack tactics and trends that reveal how the threat landscape is evolving, so you can adapt your defenses to protect your organization’s assets and operations.
What Attackers Are Doing (or Trying to Do)
Most attacks seem to be motivated by money. Commonly affected organizations are in industries that store, transmit and process high volumes of monetizable information. The finance, professional and legal services, manufacturing, healthcare, high tech, and wholesale and retail industries accounted for 63% of our IR cases.
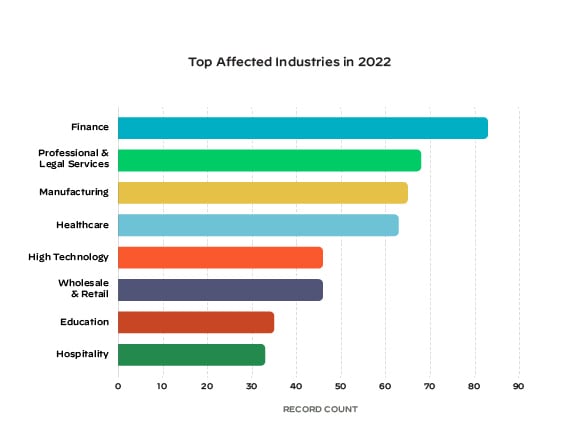
Hackers can sell the data or hold it hostage to extract a payout because they know the organizations in these industries rely on the integrity and privacy of their information to operate and compete.
How Attackers Are Operating
Ransomware and business email compromises (BEC) were the top incident types observed in our cases over the past year, accounting for approximately 70%.
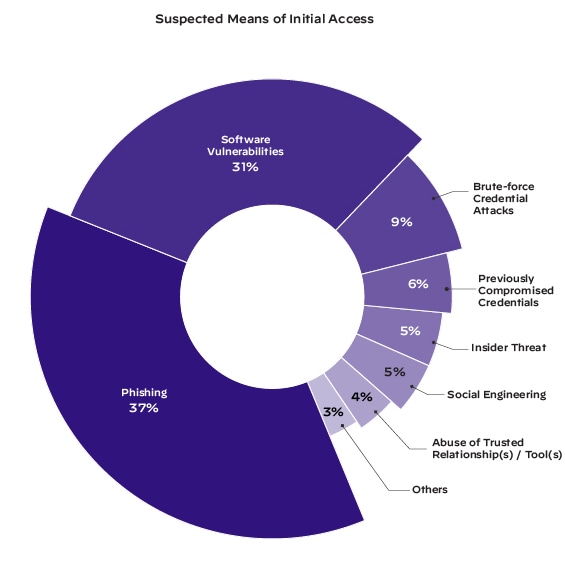
The top three access vectors that threat actors used to get into an organization’s environment were phishing, the exploitation of known software vulnerabilities and brute-force credential attacks, primarily focused on remote desktop protocol (RDP) where victim’s systems were directly exposed to the internet. These three were the suspected initial entry vectors of more than 77% of intrusions.
What Contributes to Attackers’ Success
When investigating why breaches were successful, our team identified seven common contributing factors to successful attacks.
- Lack of multi-factor authentication – 50% of cases
- No endpoint detection and response (EDR) security solution to detect and respond to malicious network activities – 44% of cases
- No or poor patch management procedures – 28% of cases
- No mitigations in place to ensure account lockout for brute-force credential attacks – 13% of cases
- A failure to review/action security alerts – 11% of cases
- Weak password security practices – 7% of cases
- System misconfigurations – 7% of cases
In many cases, organizations we worked with had been taking the right steps most of the time – but attackers only need to find one gap to be successful. We saw cases where a bit of “shadow IT” – unauthorized devices – or a half-forgotten legacy system wound up putting the entire organization at risk.
We see this list as a guide you can use to double-check that your key protections are in place.
What You Can Do to Protect Your Organization
Based on the themes that come up again and again in our IR cases, our consultants highlighted the top six things you can do to improve your organization’s security posture and make it harder for attackers to succeed:
- Conduct phishing prevention and recurring employee and contractor security training.
- Disable any direct external RDP access. Ensure all external remote administration is conducted through an enterprise-grade virtual private network (VPN) with multi-factor authentication (MFA) required.
- Patch internet-exposed systems as quickly as possible (given leading practices for testing and responsible deployment) to prevent vulnerability exploitation.
- Implement MFA as a technical control and security policy for all users.
- Require that payment verification takes place outside of email to ensure a multi-step verification process.
- Consider a credential breach detection service and/or attack surface management solution to help track vulnerable systems and potential breaches.
Other Insights You’ll Find in the 2022 Unit 42 Incident Response Report
In addition to the findings outlined here, the report includes in-depth spotlights on ransomware, BEC and cloud incidents – three types of incidents that we believe all organizations should prepare to defend against. We share actionable information on what attackers do once they’ve breached a network. Our consultants predict how attackers may shift their tactics and goals in the coming year.
Finally, our security experts take you far beyond the six fundamentals described above. We offer in-depth recommendations for how to improve your security posture, grouped so you can focus on the risks you most want to mitigate.
Download the full 2022 Unit 42 Incident Response Report to learn more, and register to attend the 2022 Incident Response Report webinar to hear our security experts discuss the key findings in the report and answer your questions live.
Get in Touch
Want help to prepare for or respond to a cyber incident? Call in the experts.
If you think you may have been impacted by a cyber incident or have specific concerns about any of the incident types discussed here, please contact Unit 42 to connect with a team member. The Unit 42 Incident Response team is available 24/7/365. If you have cyber insurance, you can request Unit 42 by name. You can also take preventative steps by requesting any of our cyber risk management services.