A Holistic Approach to Zero Trust
As the urgency and focus around adopting Zero Trust has accelerated, many security professionals are working to assess their organization’s readiness and maturity. Despite many vendor’s claims that Zero Trust is a product, Zero Trust requires a comprehensive approach that spans both tools and processes in order to be successful. Today, many Palo Alto Networks customers are using our Zero Trust framework and platform to evolve their Zero Trust journey. Recently, we have expanded our Zero Trust services offering with a Zero Trust Advisory Service to provide high levels of support on the process side of Zero Trust and accelerate our customers’ move to a Zero Trust approach.
Securing Your Digital Transformation
Major digital transformation initiatives, such as hybrid workforce and cloud transformation, have further accelerated the need for a Zero Trust approach. As an example, the move to SD-WAN on the network side of the house maps well to modern security models, like ZTNA and SASE within a broader Zero Trust strategy. These factors informed our approach to the creation of our Zero Trust Advisory Service, where we leveraged our broad security expertise and capabilities to figure out how to deliver Zero Trust everywhere, not just in a single security domain, such as endpoint or network security. The Zero Trust Advisory Service is our way of partnering with our customers for an aligned vision that ultimately enables us to succeed together. As a trusted partner, we seek to protect all users, applications and infrastructure by using a consistent set of capabilities and validation criteria, ensuring that blind spots are reduced within each environment. The process starts with high-level technical and business discovery, which moves through strategy, design and implementation phases to reach a more mature level of Zero Trust adoption and continuous improvement. There are key steps in this process:
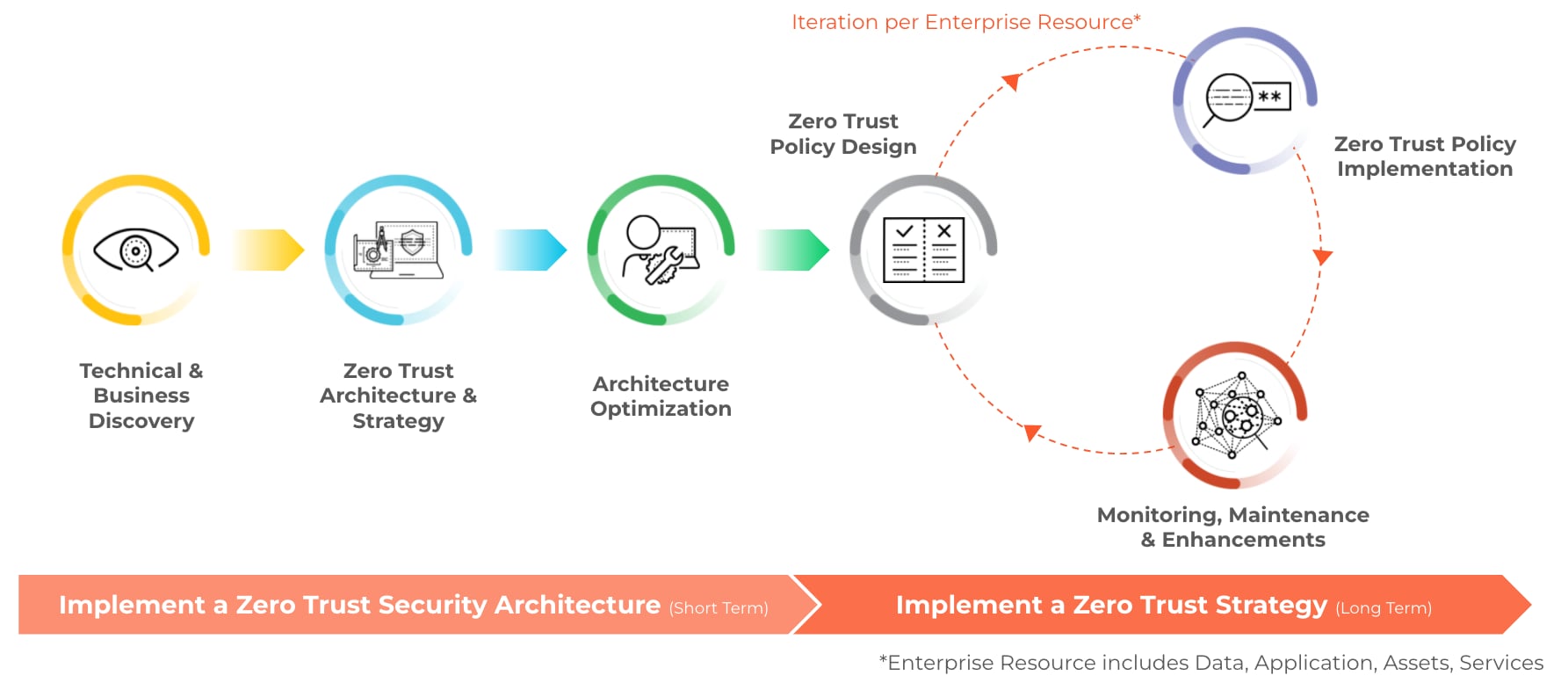
Technical and Business Discovery
Visibility and an intimate understanding of which users and devices are connected, what applications are deployed and where critical resources reside is a critical “step 0” in any successful Zero Trust journey. In this phase, the objective is to create a baseline of the existing security posture by collecting data from key stakeholders, as well as understanding the organization’s operational priorities and critical assets.
Architecture and Strategy
In this phase, we work to design a vendor-agnostic security architecture and roadmap. We utilize key data points from the previous phase to optimize the architecture and close any gaps discovered in your security posture. This ideal future state will address current cybersecurity challenges, support future cybersecurity needs, and offer all the required controls to implement a Zero Trust strategy going forward. This stage includes the creation of a holistic Zero Trust maturity baseline for the organization and a Zero Trust strategy specific for your use cases.
Architecture Optimization
In this phase, we leverage an organization's existing infrastructure alongside the newly proposed architecture to guarantee the required security capabilities are present. The optimization of the architecture will ensure all identified security gaps have been closed. Prior to implementation, a detailed roadmap and timeline will be provided to the customer, allowing feedback and proper planning. Once final approval is achieved, the optimized architecture will be implemented to make sure the security capabilities align with the Zero Trust strategy.
Policy Design & Implementation
In this phase, the objective is to design and implement a Zero Trust security policy. The optimized security architecture will be utilized to identify legitimate traffic flows for the enterprise resources, based on the collected data. Next to the technical information, the organization needs to provide input for who can access what resource, when and where. The combination of the technical and business input allows us to design a least-privilege security policy. This policy will be translated into a configuration for specific technical controls that will then be applied to the associated policy enforcement points applicable for a specific use case.
Monitoring, Maintenance & Enhancements
In this phase, the objective is to continuously evaluate if the implemented Zero Trust security policies still meet the technical and business requirements. Over time, enterprise resource access requirements may change. That’s why it’s essential for your organization to implement the processes to continuously monitor and validate your Zero Trust security posture. This iterative process will be used to ensure the best possible Zero Trust policy is implemented, based on available security controls, technical and business information for an enterprise resource.
Contact us to learn more about the Zero Trust Advisory Service and how we can help you become a Zero Trust Enterprise.