IBM Cloud VPC now supports the industry leading Palo Alto Networks VM-Series Virtual Firewalls in single availability zone, high-availability configuration, allowing customers to easily deploy Advanced Threat Prevention, cloud-delivered security and ML-Powered Next-Generation Firewalls (NGFWs) with higher resiliency.
IBM Cloud VNF Program
Network functions virtualization (NFV) offers a new way to design, deploy and manage networking services known as virtual network functions (VNFs). IBM has introduced the VNF program for customers who need greater control over network-based capabilities. In conjunction with the IBM Marketplace and Partner Center, our enterprise customers can make the IBM Cloud platform more agile and reflective of their networking, security and routing policies.
Palo Alto Networks is a key IBM Cloud Partner in its NFV Program. In partnering with Palo Alto Networks, IBM can wrap cloud services around industry-leading and effective security solutions delivering the best value. Palo Alto Networks and IBM Cloud are proud to announce the highly available deployment architecture of the VM-Series NGFW on IBM Cloud. The Palo Alto Networks VM-Series in HA option on IBM Cloud ensures that the network and its services are always on, accessible (service accessibility) and active sessions are always maintained without disruption (service continuity).
About the VM-Series Virtual Firewall on IBM Cloud
Palo Alto Networks VM-Series Virtual NGFWs protect your IBM Cloud workloads with next-generation security features that allow you to confidently and quickly migrate your business-critical applications to the cloud. Embed the VM-Series in your automated infrastructure provisioning workflows to protect applications deployed in the IBM Cloud.
VM-Series NGFWs allow you to migrate your business-critical applications to the cloud and protect the increased public cloud footprint from threats, data loss and business disruption. The many benefits offered by VM-Series on IBM Cloud include the following:
- Offering industry leading application visibility and precise control.
- Preventing threats from moving laterally between workloads and stopping data exfiltration.
- Eliminating security-induced application development bottlenecks with automation and centralized management.
Palo Alto Networks NGFW HA Deployment Architecture in IBM Cloud
Legacy on-prem deployments of network services are usually implemented utilizing highly-reliable hardware built explicitly for a single-purpose middlebox. VNFs move such services to a virtualized environment, named NFV Infrastructure, based on IBM Cloud’s VPC general-purpose hardware. One of the open issues for NFV Infrastructure design is to guarantee high-availability levels on their VNF images, (i.e., the probability that the network function is working at a given time). In other words, a higher availability corresponds to a minor downtime of the system, and it is required to satisfy stringent Service Level Agreements (SLA), which is a critical requirement of VNF-based workloads on IBM Cloud.
Networks have always needed high availability and resiliency. With NFV, the need is even more significant. Still, there are challenges to ensuring high availability and resiliency in an NFV-based system due to the complexities of virtualization, cloud computing and the various network functions.
You can deploy the VM-Series Virtual Firewalls on IBM Cloud to ensure redundancy in the network by using the active/active high availability (HA) configuration. The Network Load Balancer (NLB) Route Mode feature is used to support the VM-Series HA and is currently supported only with private IP and TCP data traffic.
The ingress routing capability allows you to associate route tables with the IBM Internet gateway and add route rules to redirect the application traffic through the VM-Series Virtual Firewall. This redirection ensures that all internet traffic passes through the firewall without reconfiguring the application endpoints.
Following is the example of Palo Alto deployment as a highly available active/active VNF. The client VSI (source) makes a TCP request to the target VSI (destination) IP at 10.241.66.5 instead of the firewall IP.
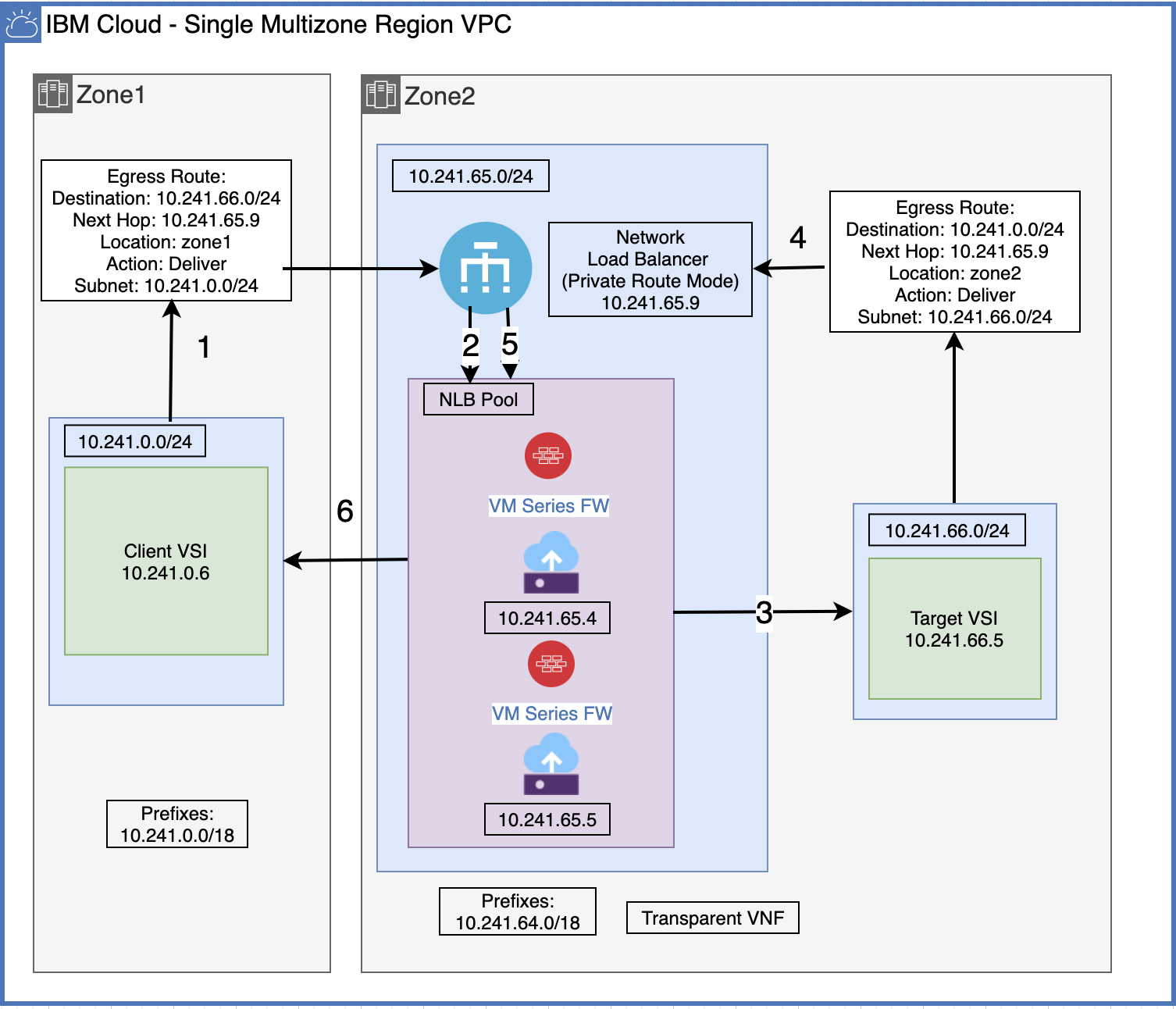
In the example above:
- An egress custom route was created to ensure client (10.241.0.6) data packets destined for the target (10.241.66.5) will "hop" through the NLB.
- Since the NLB is configured in "Route Mode," TCP requests on all ports will be automatically forwarded to their destination. Since the VNFs are in the NLB pool, they will be the next hop after the NLB.
- In this active/active single region example, an egress route is also needed to ensure the return packet from the target will "hop" through the NLB on the return trip, then through the same VNF it was sent through and finally back to the client.
- In this example, the client is in a different zone than the target, but the target is in the same zone as the NLB/VNF.
Next Steps
The example above showed the Palo Alto Networks VM-Series Virtual Firewall HA option used in a single region. However, the HA VNF can also leverage the IBM Cloud Transit gateway and be used in multiple regions in a hub and spoke architecture.
Discover more about the Palo Alto Networks VM-Series Next-Generation Firewalls on IBM Cloud and how they can transform your IBM Cloud Deployments by visiting the IBM Cloud web page.
Visit the Palo Alto Networks website for details about provisioning Palo Alto Networks VM-Series NGFW on standalone and HA configurations.