This post is also available in: 日本語 (Japanese)
An Introduction to Best Practice Assessment Plus (BPA+)
As organizational complexity continues to increase, the attack surface that security teams must address expands parallelly. Customers struggle to configure their firewalls using existing applications and capabilities to properly secure their network, which means a misconfigured firewall offers comparable protection to no firewall at all. 99% of firewall breaches through 2023 will be due to firewall misconfigurations, not firewall flaws, according to Gartner research.
The Best Practice Assessment (BPA) measures usage of your Palo Alto NetworksⓇ Next Generation Firewall, and Panorama™ security management capabilities across your deployment, enabling you to make adjustments to maximize your return on investment and strengthen security. The BPA enables you to obtain context into your security posture from a configuration perspective by generating high-level graphics, heatmaps and reports that compare how your configuration aligns with best practices across your industry. Additionally, more granular metrics are shown along with recommendations on how to take action in order to improve configuration security postures across all devices.
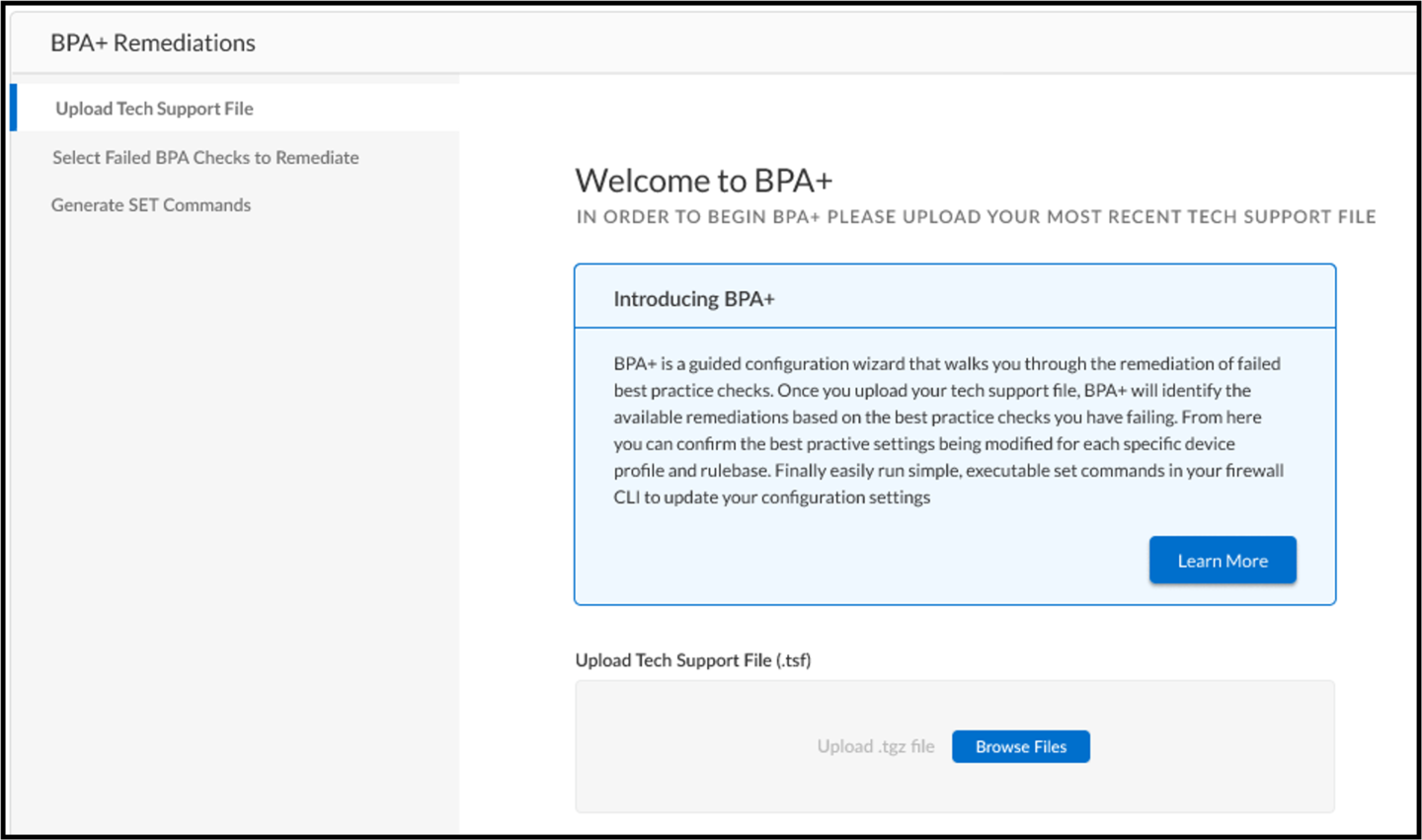
The Palo Alto Networks Best Practice Assessment Plus (BPA+) is a step-by-step configuration wizard that provides an intuitive, easy-to-use interface to configure firewalls to align with best practices. The BPA+ takes the results of the BPA and expedites the remediation process by outputting commands that can be easily pasted into any instance of PAN-OS and committed. This provides a clear call to action on how to remediate failed BPA checks and improve security posture.
BPA+ User
We have designed BPA+ to help our Strata ™ and Panorama customers to automagically expedite expert-driven changes by identifying failed BPA checks and provide a clear call to action on how to remediate those failed BPA checks. This will help our Strata and Panorama customers to reduce misconfigurations across their network security resulting in greater security posture.
BPA+ Customer Benefits
- Save time and automatically remediate to security best practices.
- Lower risk and reduce configuration errors.
- Quickly deploy configurations across your entire firewall infrastructure.
- Maximize your return on your security investment.
Our goal is to provide you with a customized recommendation to remediate failed BPA checks that improve overall security posture. A step-by-step guided configuration wizard will provide an intuitive, easy-to-use interface to configure your Palo Alto Networks Next Generation Firewall that aligns with best practices. This involves tech support file (TSF) upload, completing the numbered steps and then executing the commands generated by the BPA+ on to your firewall.
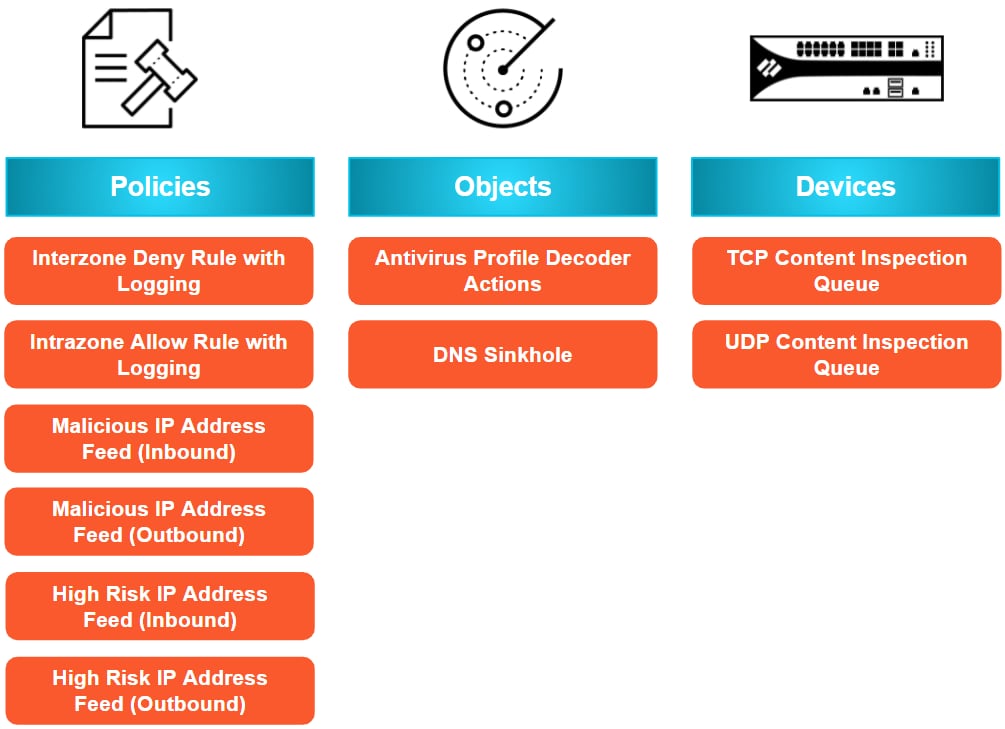
As part of its initial release, BPA+ will analyze the ten most prevalent Best Practice Assessment checks.
How to Access Best Practice Assessment Plus?
There are two different ways to access the Best Practice Assessment Plus.
1. Login to your account in Customer Support Portal and click tools, then Best Practice Assessment to generate an assessment of your current configuration.
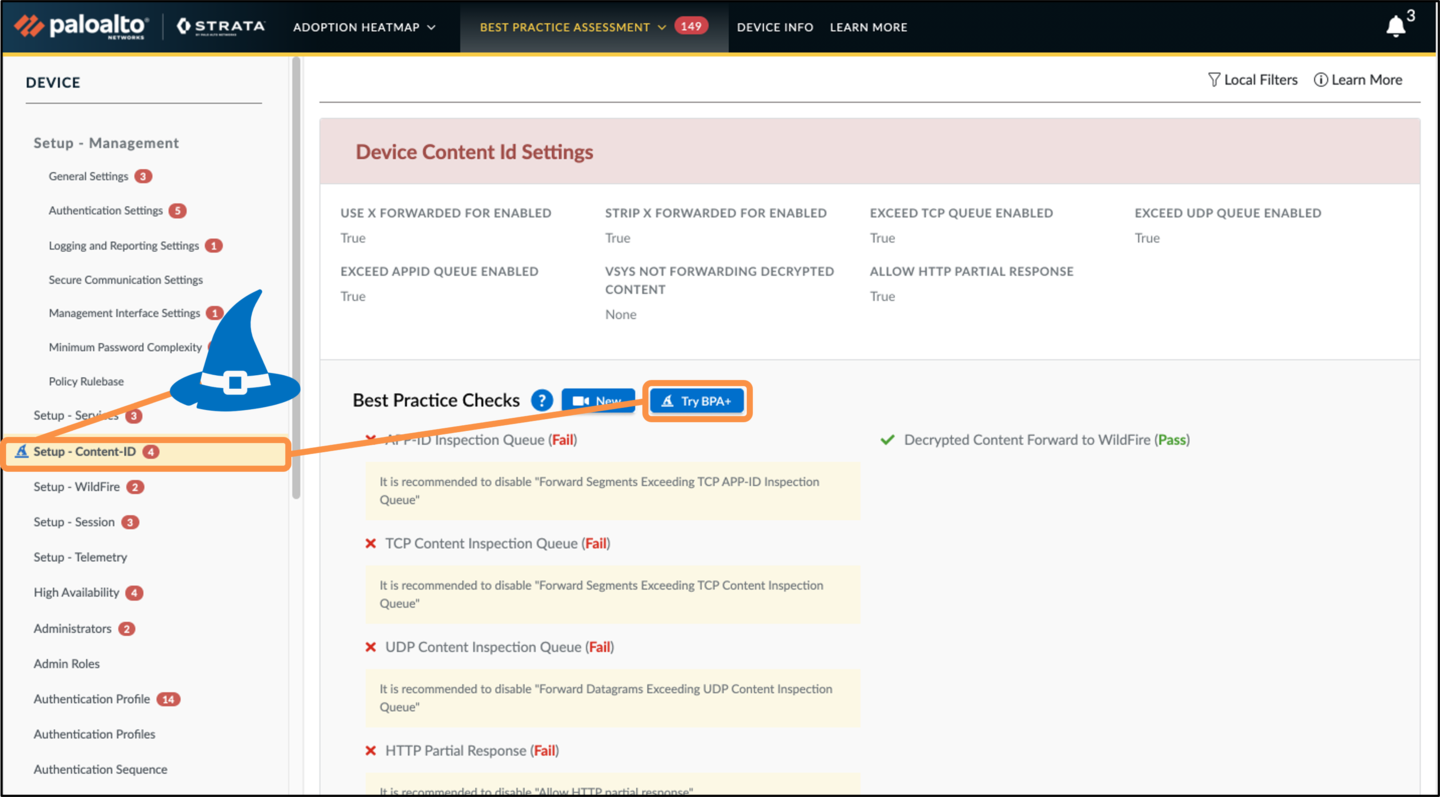
Then upload a tech support file to check for failed BPA checks. After the file is analyzed, the BPA report will be generated with the results. You can view these in the tool or download the report. Once you open your report, click “Try BPA+” tab to launch BPA+ wizard.
2. You can also access BPA+ from the Get Help location of the Customer Support Portal. Click the “Get Help” button and when entering the problem description, the system will determine you may be having a configuration issue based on your problem category choice. A “Launch BPA+” button will appear in the recommended solutions.
Once a tech support file is uploaded, BPA+ will identify available remediations based on the failed best practice checks. You can confirm the best practice settings being modified for each specific profile and rulebase. After review, you can run simple, executable commands in your firewall CLI to update your configuration settings to adhere to best practices.