With the growing threat of supply chain attacks, as evidenced by recent high-profile breaches like SolarWinds and Kaseya VSA, Palo Alto Networks Unit 42 cloud threat researchers sought to understand these types of attacks in order to help organizations protect against them.
Unit 42 Cloud Threat Report, 2H 2021 Available Now
For their latest Cloud Threat Report, the Unit 42 team analyzed data from a variety of public data sources and also executed a red team exercise on the software development environment of a large SaaS provider (a customer of Palo Alto Networks) at their request. Their findings indicate that many organizations may have a false sense of security regarding their cloud infrastructure and protection procedures. In reality, many organizations are vastly unprepared for the threats they face.
Here, we’ll detail the report’s biggest takeaways and offer resources to help your organization stay ahead of supply chain security threats in the cloud.
Red Team Exercise Signals Supply Chain Vulnerability
The large SaaS provider tested in the red team exercise has what many would consider a mature cloud security posture. However, during the exercise, Unit 42 researchers were able to leverage misconfigurations in the organization’s software development environment, such as the presence of hardcoded identity and access management (IAM) key pairs, that would have allowed them to control all development processes and thus conduct a successful supply chain attack.
Further, Unit 42 researchers found that 21% of the security scans they ran against the customer’s development environment resulted in misconfigurations or vulnerabilities, highlighting how process gaps and critical security flaws leave an organization exposed and susceptible to a business-halting attack.
Third-Party Code Is Rarely Trustworthy
In their research, Unit 42 researchers discovered that 63% of third-party code templates used in building cloud infrastructure contained insecure configurations, and 96% of third-party container applications deployed in cloud infrastructure contain known vulnerabilities. With this level of risk, if an organization uses third-party code without vetting and verifying it, chances are high that it could contain vulnerabilities and insecure configurations that could allow an attacker to easily gain access to sensitive data in the cloud and even take control of the organization’s software development environment.
Based on the Unit 42 team’s findings, it’s evident that unvetted code can quickly snowball into a security breach, especially as infrastructure flaws can directly impact thousands of cloud workloads. For that reason, it is critical that organizations understand where their code is coming from since third-party code can come from anyone – even an Advanced Persistent Threat (APT).
How to Protect Your Organization From Software Supply Chain Insecurity
Here, we outlined the biggest takeaways from the latest Cloud Threat Report, but there is still a lot left to unpack. While the report goes into granular detail about software supply chain attacks and how they occur, Unit 42 cloud threat researchers aim to help teams understand these attacks in order to help them stay protected.
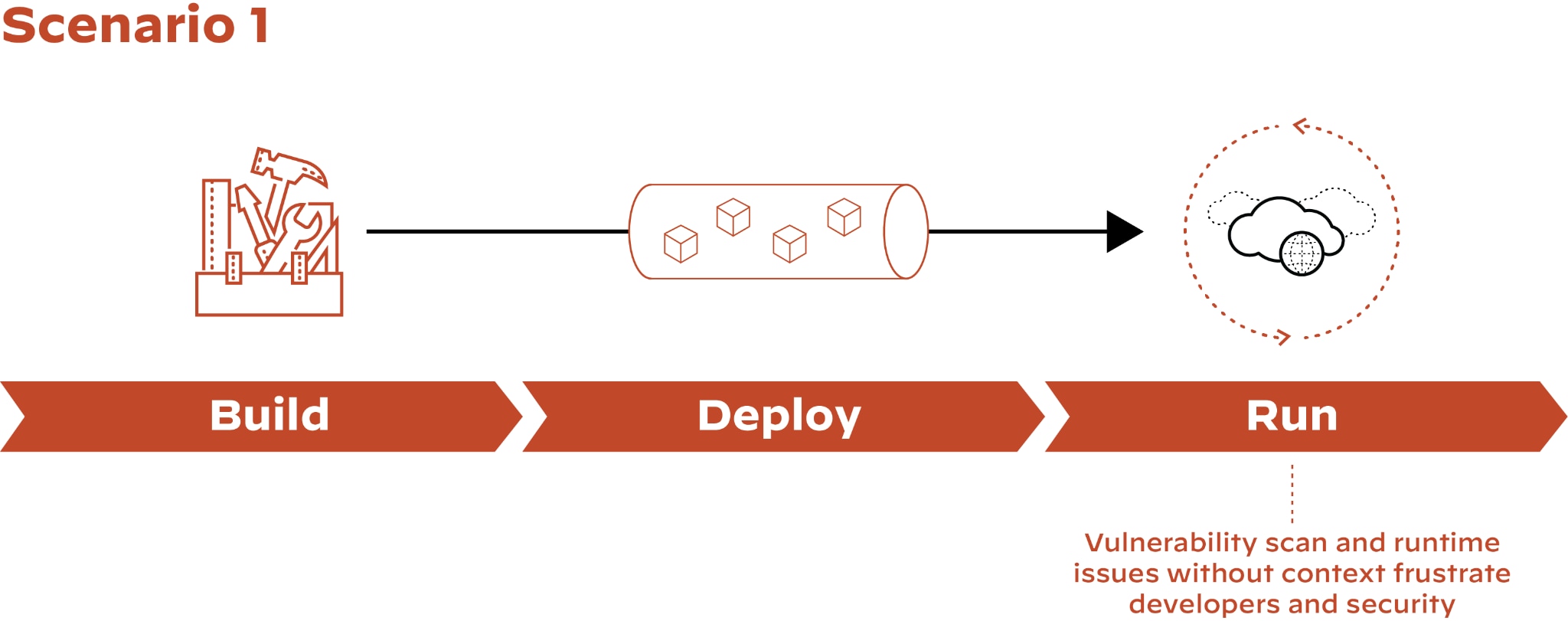
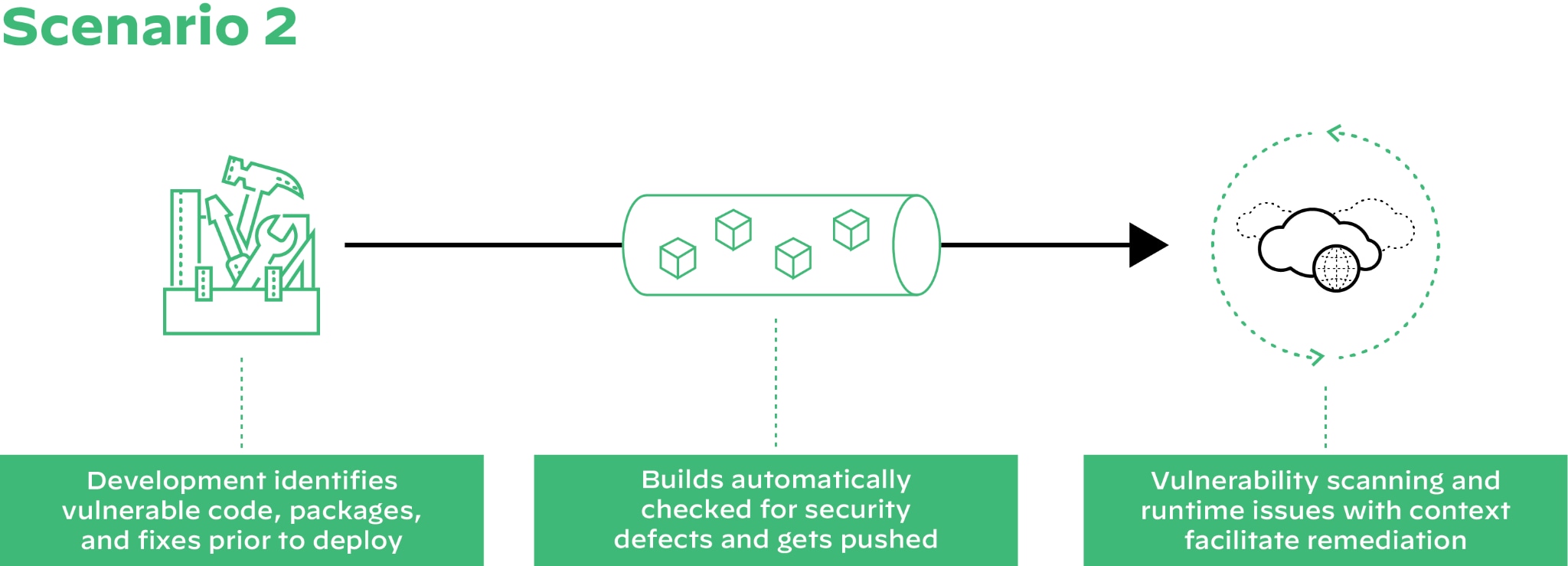
In the report, you’ll find step-by-step recommendations that you can begin implementing for your organization immediately, as well as gain valuable insight into how this growing threat continues to evolve. Download your free copy of the Unit 42 Cloud Threat Report, 2H 2021, today!