Power of Threat Intelligence
The closest thing you get to being a threat precog is probably the ability to harness intel within your threat feeds – to anticipate and prevent future attacks. Unfortunately, just like in the movies, reality falls short of fiction. Today’s management of threat feeds is part automation, part manual and part luck when it comes to identifying the critical and relevant threats specific to one’s environment.
Threat intel teams spend hours sorting through feed data from various sources; correlating that data to incidents; and pushing only the relevant data to enforcement tools for action.
The true power of a Threat Intelligence Platform lies in understanding how to make intelligence actionable and doing so before it is too late. This includes automatically mapping threat information to incidents happening in your network, quickly understanding the connections between threat actors and attack techniques previously unknown in your environment. We are delighted to release the second version of our Threat Intelligence Management (TIM) module that assists customers in making the most of the Intelligence they have at their disposal.
What’s New in Cortex XSOAR TIM 2.0
Cortex XSOAR TIM 2.0 unlocks the power of your threat intelligence. The mission-control platform gives you full intelligence lifecycle management, with unmatched visibility into the global threat landscape; ties threat information to incidents in real-time; and automates the distribution of your threat intelligence at scale.
- Central Threat Intelligence Library for Your Enterprise: We bundle in threat intel from our Unit 42 threat research team, so you have access to a huge repository of high-fidelity threat intel from Palo Alto Networks, in addition to your own collection from open source threat intel feeds.
- Native Correlation Between Indicators, Incidents and Intel: Not only do you see all the atomic indicators related to your incidents, but you also get enriched strategic intelligence, so your team has added insight into threat actors and attack techniques.
- Easily Discover and Add New Threat Intel Sources Via Our Marketplace: Since the launch of TIM last year, we’ve added 165 threat intel specific integrations. With a single click, you can instantly add a new feed integration and subscription.
Batteries Included
When you deploy TIM 2.0, you get access to out-of-the-box, high-fidelity threat intelligence from the industry’s largest footprint of network, endpoint and cloud intelligence sources (tens of millions of malware samples and firewall sessions collected and analyzed daily). This intel is further enriched with context from world-renowned Unit 42 threat researchers at Palo Alto Networks.
Combine this with the ability to correlate third-party intel and incidents happening internally, and you unlock a host of threat use cases previously unknown to your security team.
Self-Service via the Marketplace!
With over 650 content packs in the Cortex XSOAR Marketplace, users can take advantage of threat intel feed automation packs and thousands of pre-built automation scripts for common and unique security-incident response use cases. If you feel your feeds are not covering enough threat territory, it’s easy to peruse and add threat intel subscriptions directly from our marketplace. Our 100+ threat intelligence and data enrichment partner ecosystem includes our launch partners, VirusTotal, Flashpoint and Intel 471. Other key partners include AlienVault, APIvoid, Cisco Umbrella, Cofense, Crowdstrike Falcon, Cybersixgill, DHS, Domaintools, IPInfo, Recorded Future, RiskIQ, SafeBreach, URLScan, FireEye Threat Intelligence and more.
More Details on the New Release
Centralized Threat Intelligence Management:
With Cortex TIM 2.0, you now have a central threat intelligence repository for storing and managing tactical threat intel (indicators of compromise) and strategic intel reporting on actors and attack techniques. The ability to correlate these different sources of intel with incidents happening internally unlocks a host of threat use cases previously unknown to the security team.
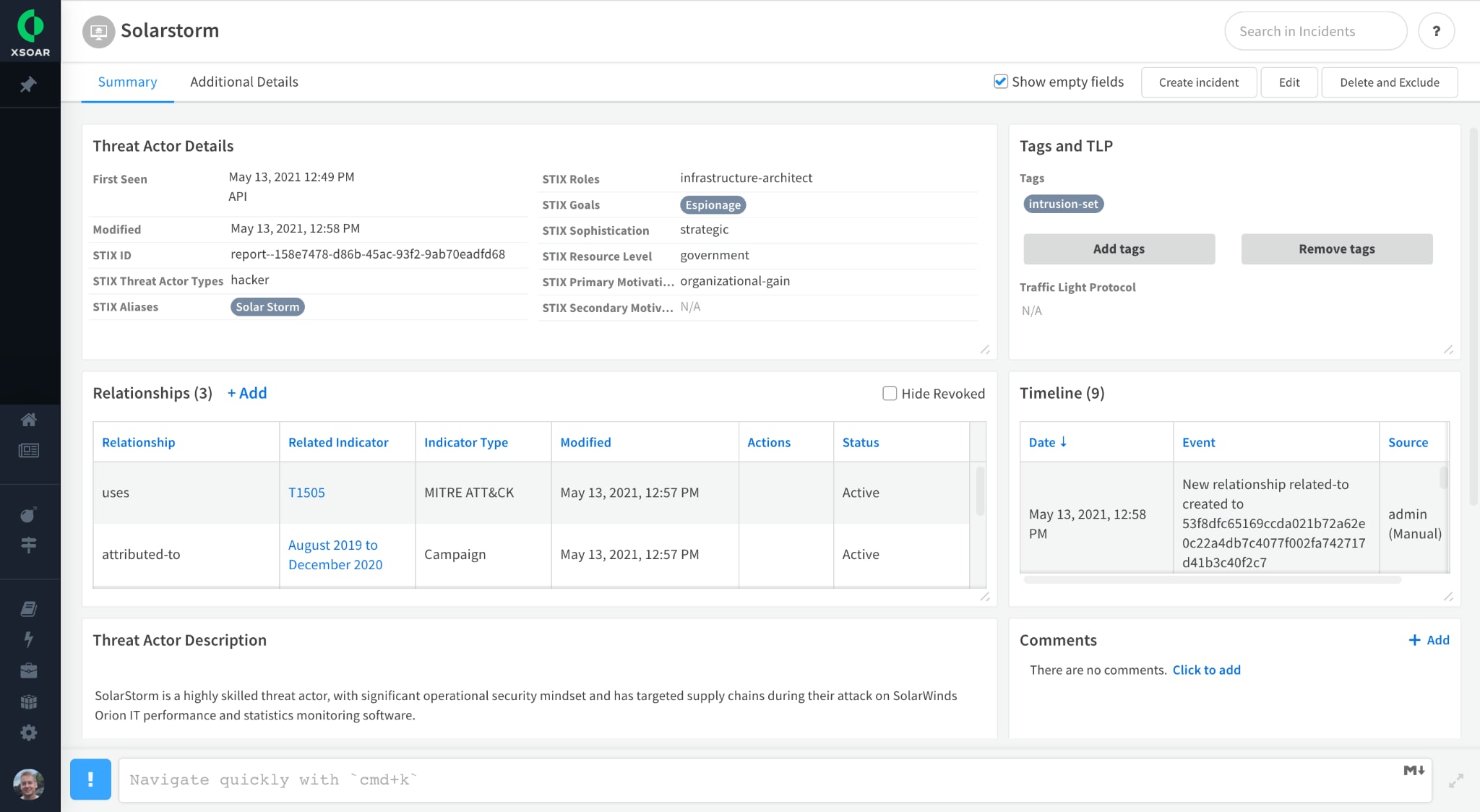
Strategic Threat Intelligence Relationships:
Threat Intel now supports structured relationships, enabling better alerts and context for SOC/IR. Intel analysts will be able to model their external threat landscape. Indicator layouts have been redesigned. Updates to popular threat intel integrations take advantage of the expanded data that includes STIX 2 objects, such as threat actor, tool, report, malware, attack patterns, campaign, course of action, infrastructure and intrusion sets.
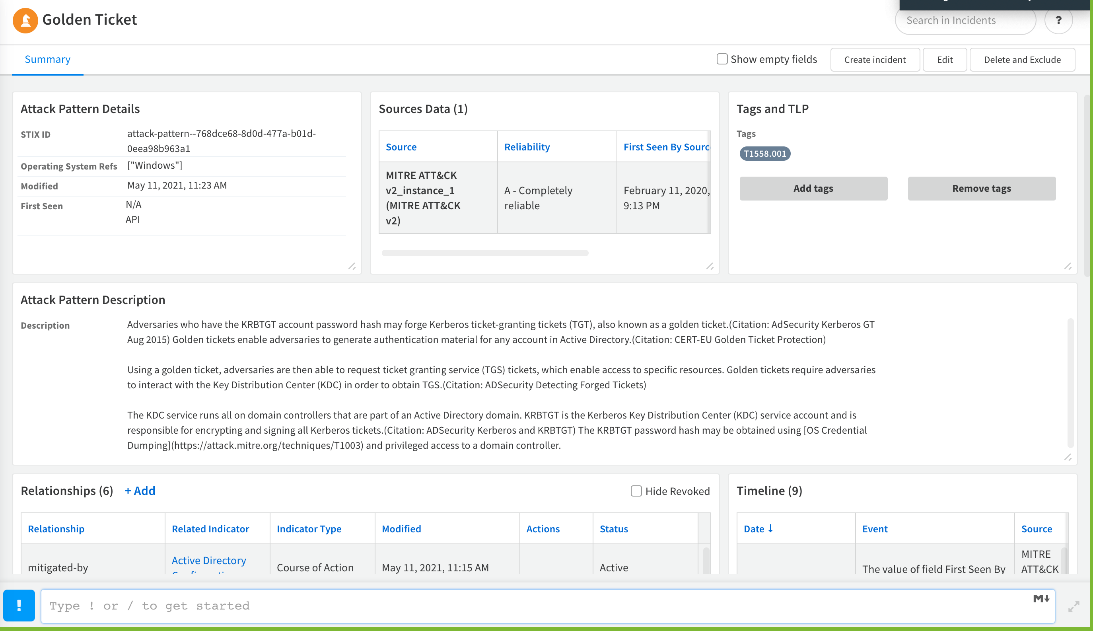
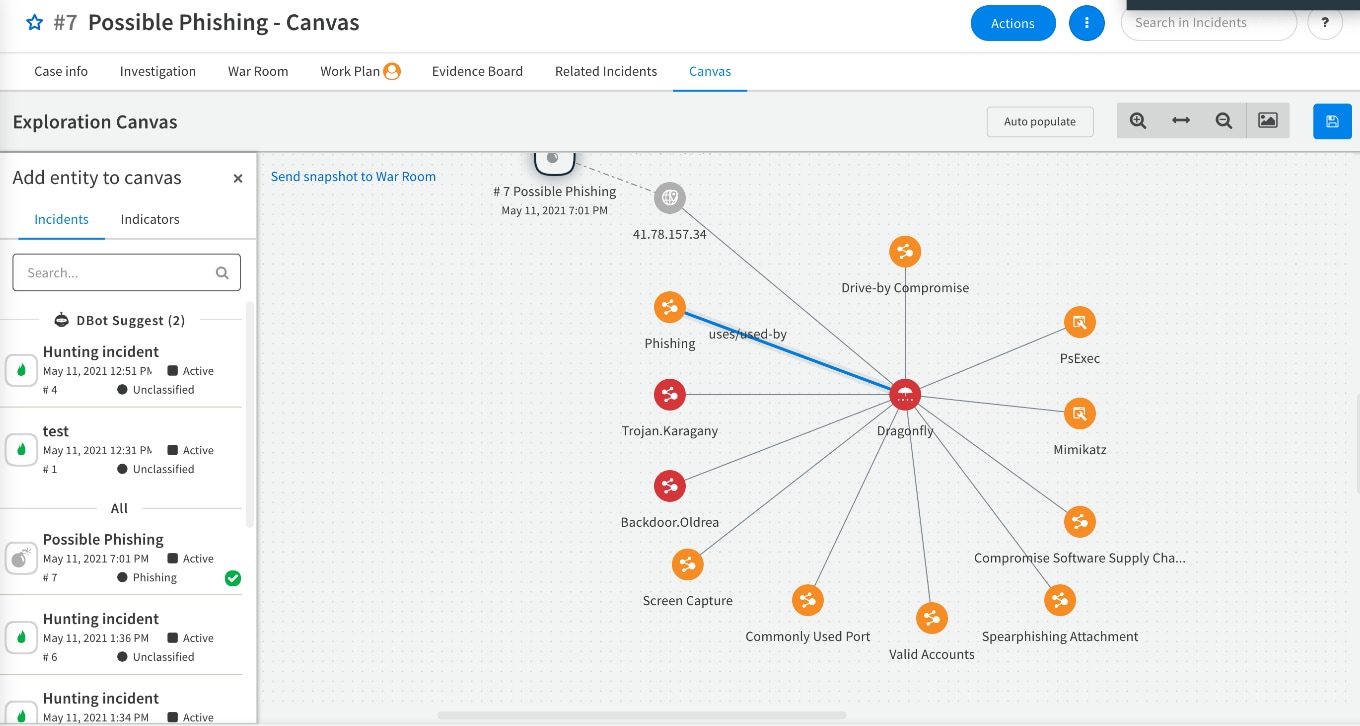
TIP + SOAR = Better Together
From the beginning, we have taken the approach that current threat intel platforms (TIPs), while adept at aggregating, correlating and even sharing or distributing threat data, cannot address a critical piece of the threat intel management lifecycle. And that is how to help threat intel teams act on the data they consume. Marrying TIP to SOAR extends the workflow automation and case management capabilities to the process of managing threat intel. But more importantly, you now have one central repository for both your threat data (aka indicators) and incidents to allow for the correlation of external threats to what is happening in your network. It is this combination that truly allows us to enrich incidents with threat actors and attack campaign intel for a better understanding of impact, so we can fine-tune our defenses to deliver the right response at the right time.
Time for a Deeper Dive

Join us for a LinkedIn Live event to learn how our own Palo Alto Networks threat intel experts and Unit 42 research team approach threat hunting and threat intel management.
For those looking to see the use case in action, join us for the webinar hosted by Threatpost where we will walk you through a threat campaign and how we leverage automation to handle it.
