Despite their ubiquity, cloud native applications are still not necessarily widely understood, which can create gaps for security teams tasked with protecting them.
These apps are built with newer technologies like containers and microservices, which allow organizations to deploy and iterate faster than ever before. It's that same speed that defies traditional approaches to Zero Trust models: resources are continually shifting, services are in constant communication and hybrid architectures are difficult to map. This creates serious obstacles for identification and validation.
In order to adapt, organizations are "shifting left" and integrating security touchpoints in the development pipeline. As part of those touchpoints, two critical security requirements for cloud native Zero Trust are container images and runtime defense.
Visibility Into Container Images
In a cloud native world, developers move fast. They can do this thanks to things like containers – a standalone file or package of files with components needed to run an application. At rest, it's called a container image. They're handy for DevOps teams, but because they're ephemeral by nature, it can be difficult for an organization to grasp what they're used for and where they originate.
In some cases, developers use public image repositories like Docker Hub to generate the base layer of an application. While these public repositories can be an efficient resource, they sometimes resemble a vending machine without a window, with little to no information provided about what item you're selecting.
Ensuring developers have the tools to secure container images at every stage in the development lifecycle is a great first step to achieving Zero Trust. One-time vulnerability scanning, while useful, isn't a complete solution to this problem. In order to ensure existing container images deployed across the environment don't contain malicious files, teams need the ability to quickly differentiate between what is good and what is not.
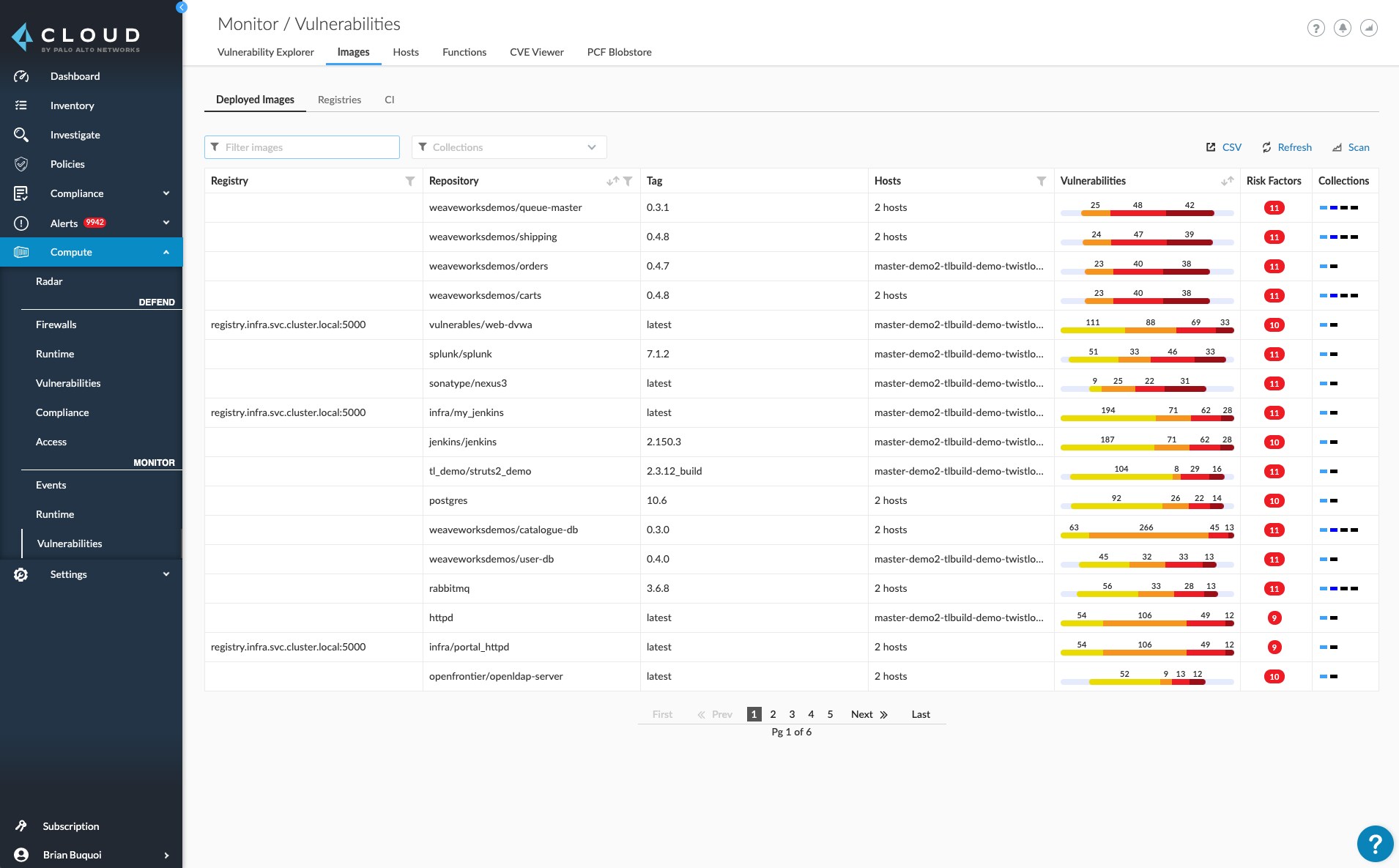
Consistent image vulnerability scanning must be combined with "image trust" to obtain the visibility and control necessary for Zero Trust in cloud native applications. Image trust policies allow users to specify which container images are safe to run within their environment, either by image or by image layers. Prisma Cloud Trust Groups provide a cohesive set of capabilities for image security to achieve Zero Trust.
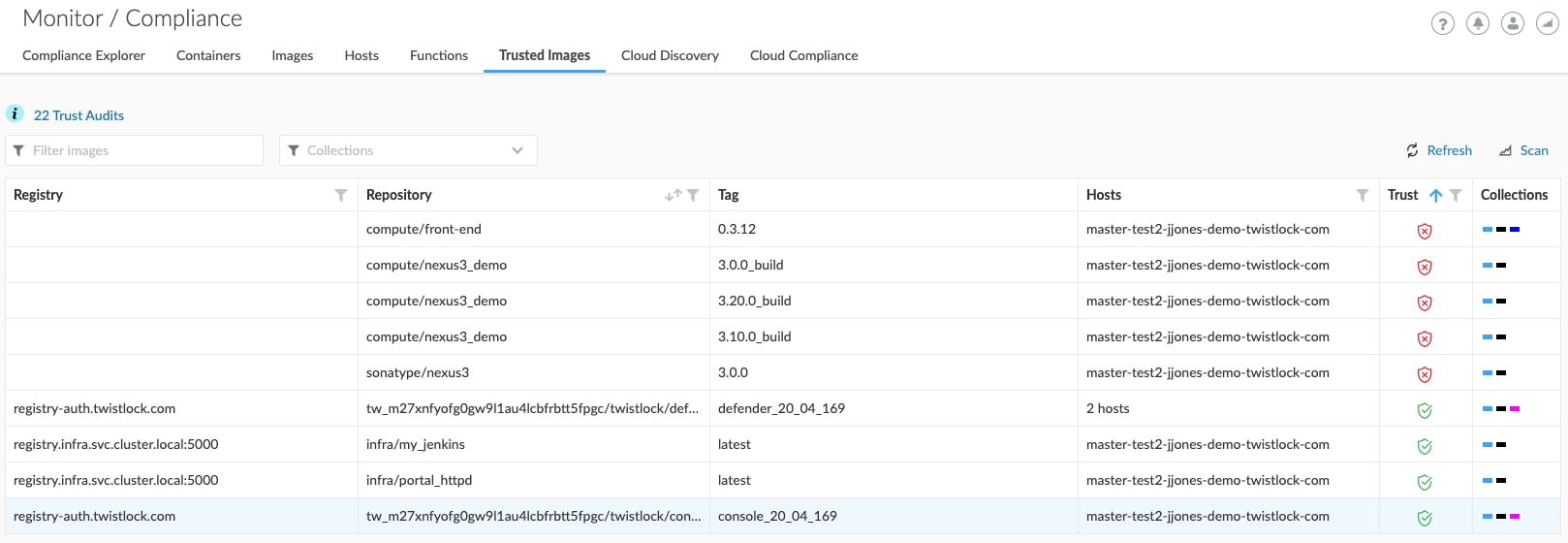
Protecting Running Applications
While continuously scanning images and verifying their trustworthiness is important, protections need to be continued into runtime as well.
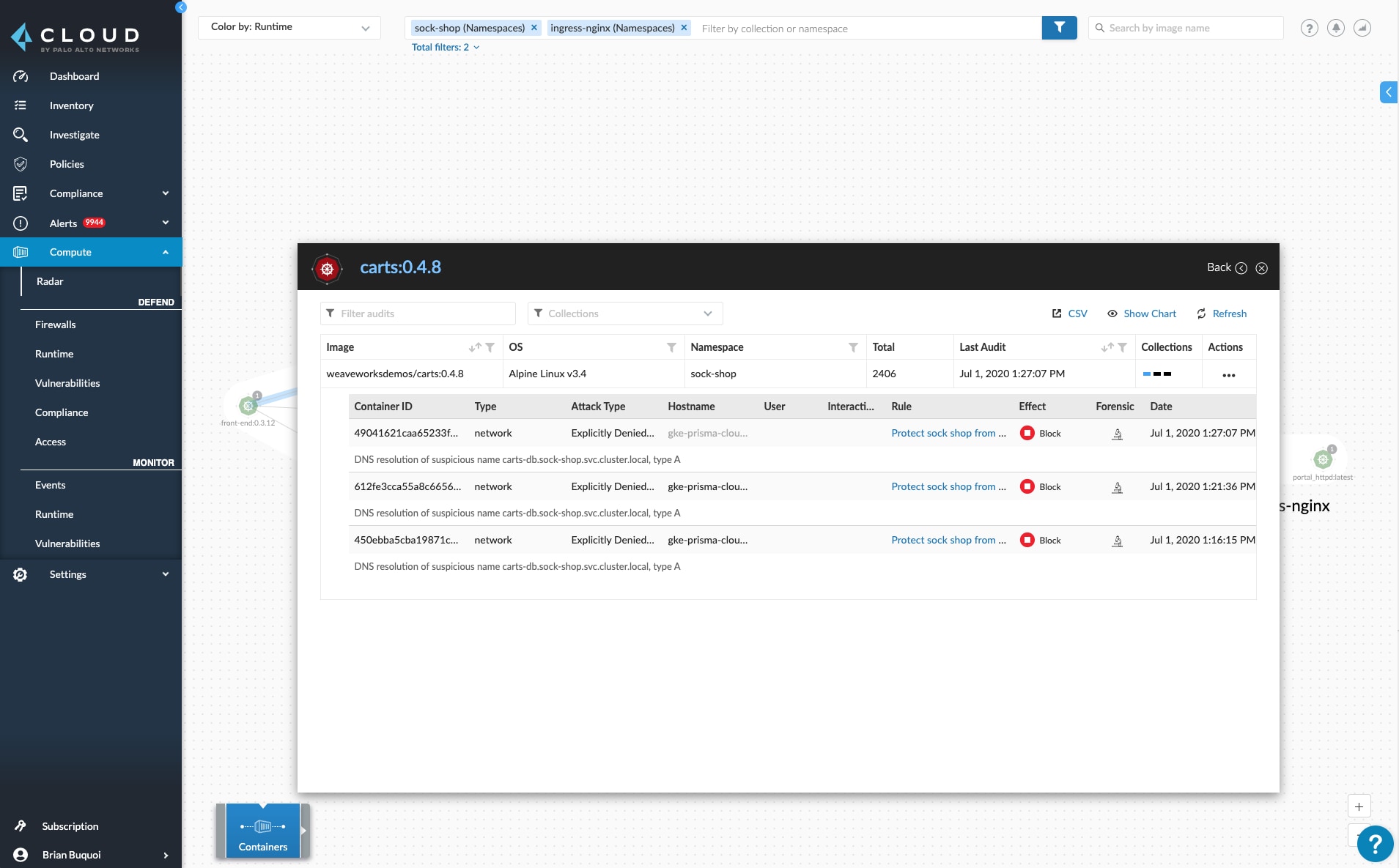
Having continuous visibility into running applications becomes of the utmost importance to validate that they are operating within defined specifications and ensure that they are only communicating with relevant entities.
Creating a model of known-good processes and network connections, then alerting on or blocking any deviations from this model, helps give organizations full control over how an application performs.
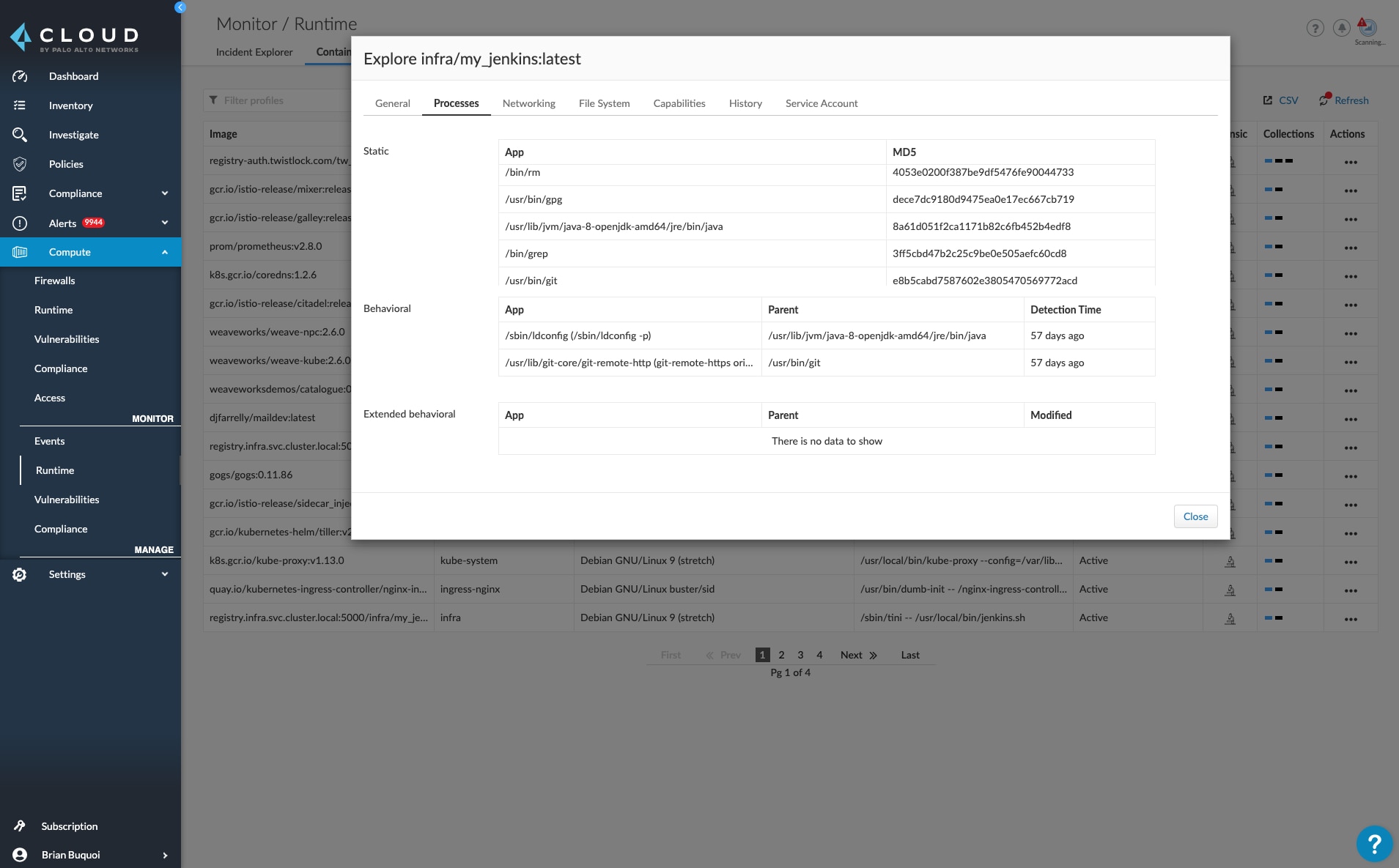
Prisma Cloud provides a comprehensive solution of runtime protections – including process, networking and file system modeling – to ensure that cloud native applications, including any combination of VMs, containers, applications on Kubernetes, or serverless applications, stay within spec and in line with any Zero Trust best practices put in place.
Putting It Together
Securing cloud native applications should be an integral part of your Zero Trust infrastructure. These applications play an integral role in how an organization interfaces with the world and should be protected as such.
Container image and runtime protections are components of an enterprise Zero Trust strategy. Watch as Palo Alto Networks Founder and CTO Nir Zuk explains how it all fits together. And be sure to check out the rest of the blogs in our Zero Trust series.