As the majority of organizations move into a multi-cloud world, new challenges for Zero Trust are emerging.
Organizations are experimenting with different architectures for cloud infrastructure. Research into the state of cloud native security shows that 80% of security professionals feel their cloud environment is constantly shifting. This makes sense given that these environments are inherently ephemeral – developers can spin up new instances and resources in a matter of minutes, and destroy them just as quickly.
Trying to figure out what or who is in your environment, let alone establishing a baseline for what is normal, can feel chaotic. In order to maintain Zero Trust for cloud, compliance and security teams need tools that can help continuously enforce policies.
Multi-cloud Compliance and Visibility
With so many organizations constantly changing their cloud architectures, simply cataloging these different environments and ensuring that they adhere to any industry compliance regulations becomes increasingly time-consuming.
In order to maintain a Zero Trust approach, organizations should look for a cloud native security platform (CNSP) that can provide visibility into all types of workloads and offer policy engines that alert about any misconfigurations across multiple cloud service providers (CSPs). These integrated tools help security, compliance and development teams prevent configuration drift and quickly remediate issues across cloud environments.
Prisma Cloud is one such CNSP that can provide multi-cloud visibility and help manage regulatory compliance across multiple environments. Dashboards show ingested data from multiple sources within a single pane of glass, and alerts are automatically prioritized with context. Prisma cloud then recommends fixes to help users quickly validate workloads and applications.
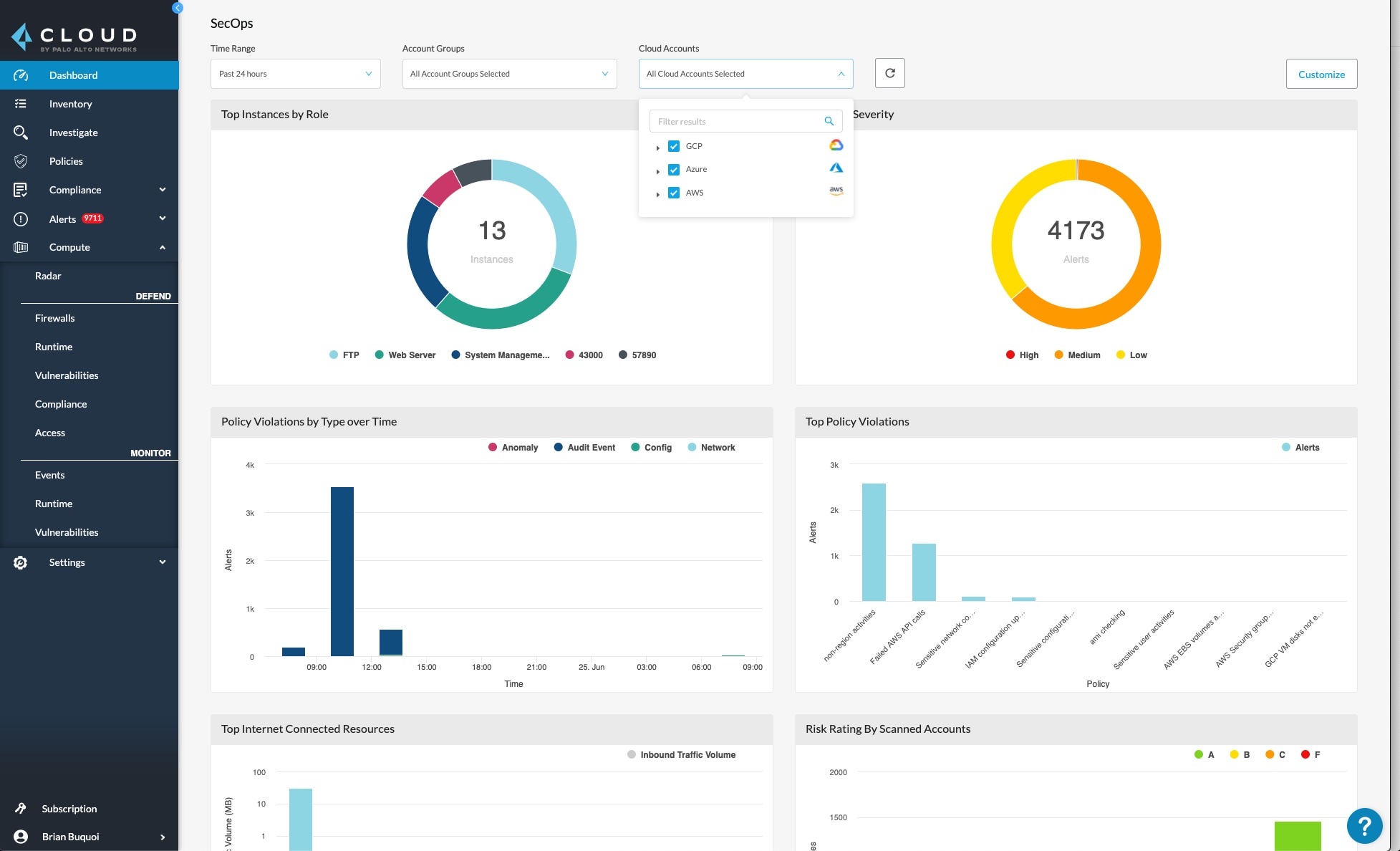
Cloud User Identity
While managing the “multi-everything” nature of the cloud poses security challenges, for many organizations, managing users presents a larger obstacle.
With a Zero Trust approach, access control must be handled with a least-privileged strategy and logs must be continuously monitored for any anomalous behaviors. When users are spread among different cloud service providers and accounts, the complexity involved in establishing a Zero Trust architecture rises further.
While the threats of unusual user activity, account hijacking attempts and excessive login failures exist in any environment, managing them is paramount in a successful Zero Trust model for cloud. The implementation of a user and entity behavior analytics (UEBA) engine can help provide a clearer picture of user activities. Machine learning can be leveraged to monitor the logs coming in from multiple sources, creating a baseline of normal activity and triggering alerts on any deviations from this baseline.
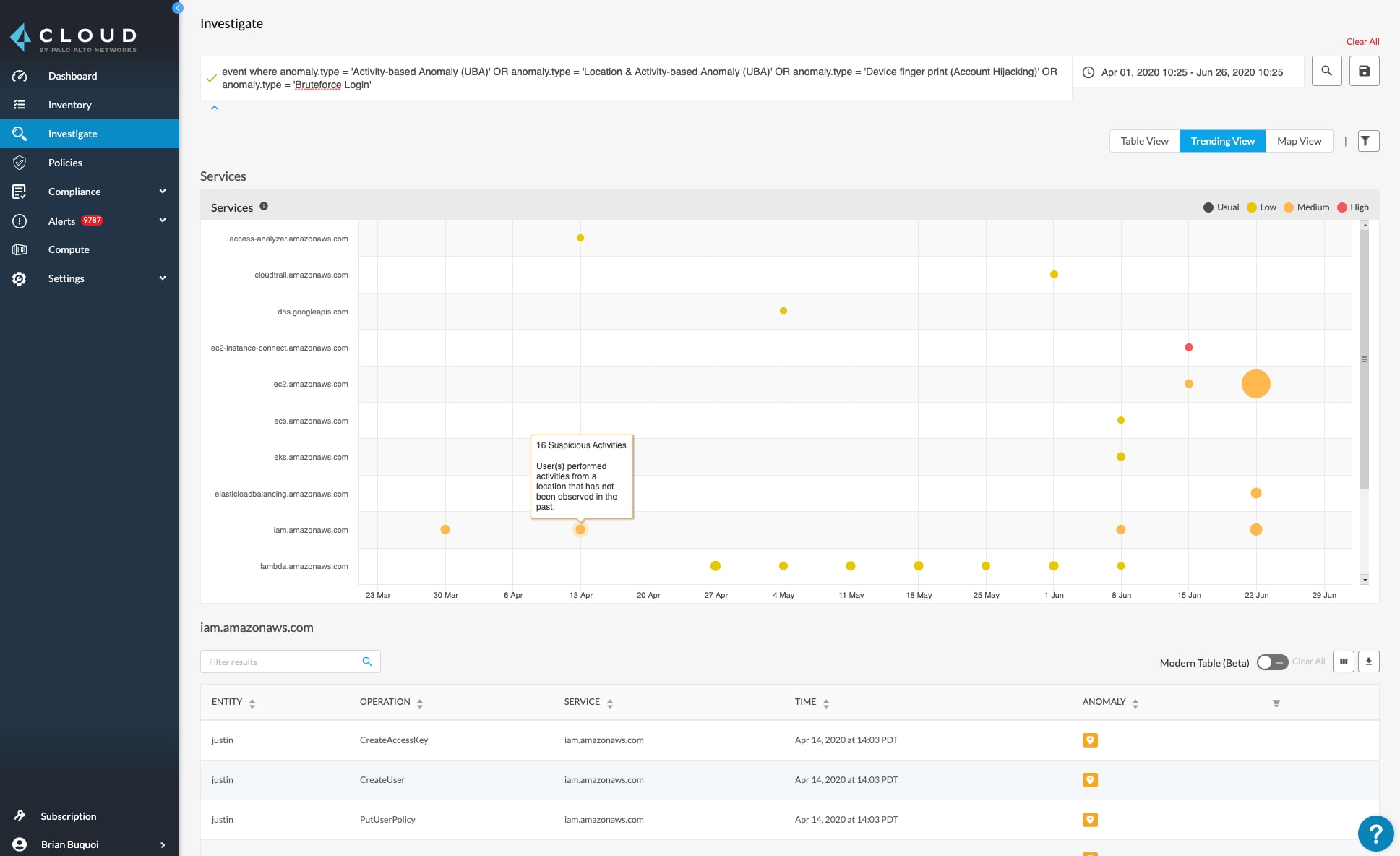
Prisma Cloud provides the UEBA functionalities needed for managing users with Zero Trust across multiple cloud platforms. It can alert on threats mentioned above as well as other malicious activities. In addition, Prisma Cloud performs continuous monitoring of cloud account roles, password policies and multi-factor authentication (MFA) use through a customizable policy engine.
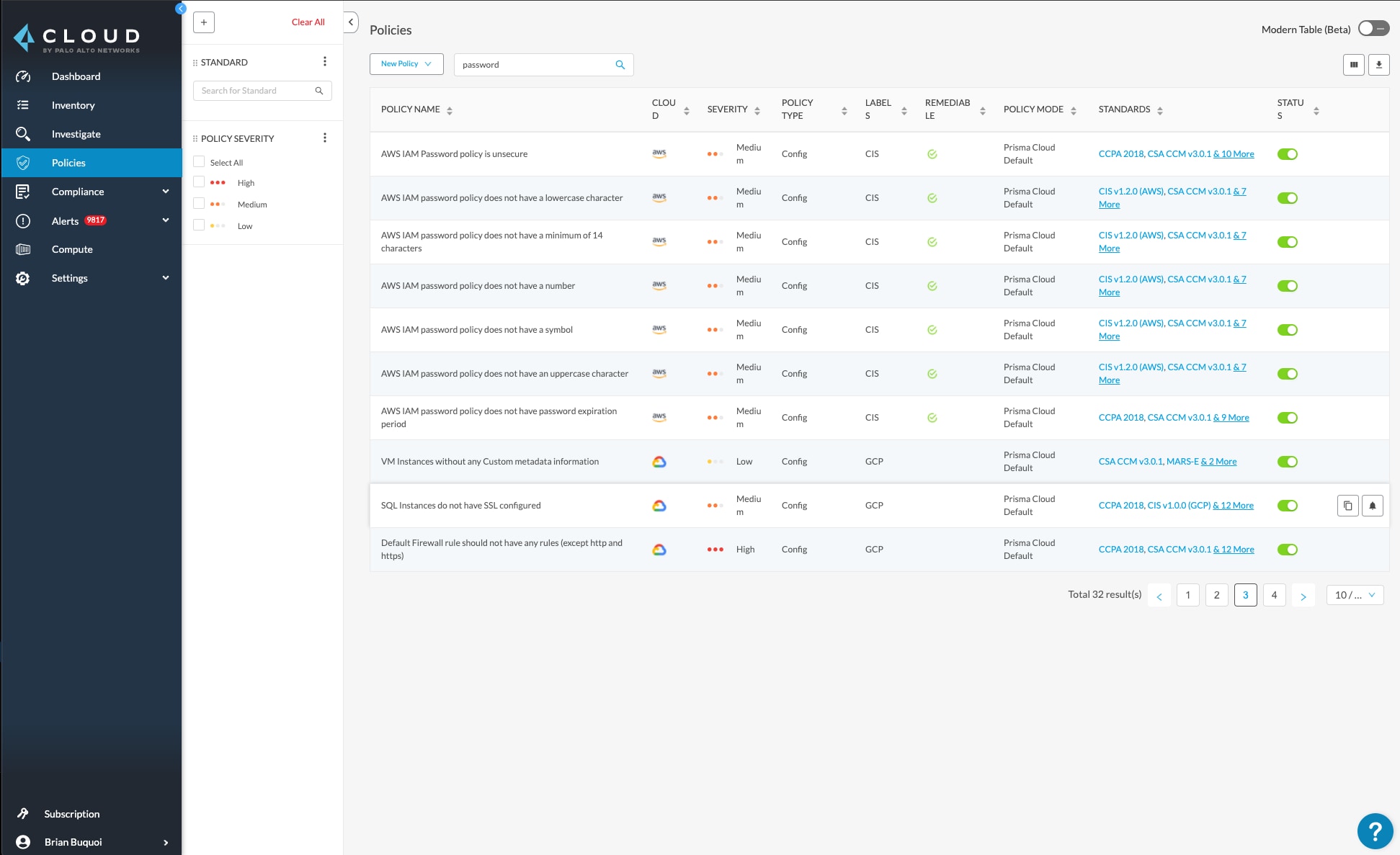
Cloud Native Zero Trust
No matter the size of the organization, the multi-everything approach to cloud is here to stay. While working with a mix of different CSPs and private clouds adds a level of complexity for Zero Trust, maintaining visibility and control can be made simpler with cloud native tools built for the job.
Identity and compliance policies are one component of an enterprise Zero Trust strategy. Be sure to check out the rest of the blogs in our Zero Trust Throughout Your Infrastructure series. Or you can watch as Palo Alto Networks Founder and CTO Nir Zuk explains how it all fits together in this video.